This post has been republished via RSS; it originally appeared at: Core Infrastructure and Security Blog articles.
Your organization may be interested to block access to corporate resources (Like E-Mail, SharePoint, etc.) based on Software Updates compliance of the device.
What does it mean for the end user? Simply put, they should have the most recent patches installed on their devices. This eventually helps organizations to meet/increase their compliance goals they have set as the end-users of those non-compliant devices will contact the helpdesk to access corporate resources by remediating their devices.
Overview
Organizations today are looking for an integrated endpoint management platform which can ensure all devices whether owned by the business or personally owned stay secure, are managed and always up to date.
This demands the most secure desktop and mobile experiences without compromising user flexibility. Configuration Manager Co-Management opens the gateway to interconnect the investments made on-premise while attaching it with the power of modern cloud-based solutions like Microsoft 365 & unlock its full potential.
A co-managed device gives you the flexibility to use the solution that works best for your organization by allowing it to be managed concurrently with both Configuration Manager and Intune.
Lean more about co-management here: http://aka.ms/comanagement
Solution
In this scenario, you continue to use ConfigMgr for deploying Software Updates however you use Intune to validate the Compliance of the Device and eventually use Conditional Access to block access to Corporate Resources depending on the compliance of the device.
Here’s a high-level view:
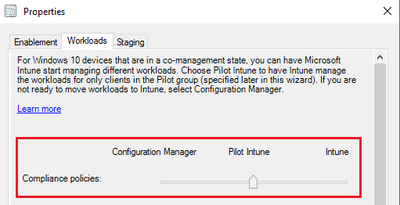
- Enable Co-Management & move Compliance policies workload to Intune.
- Create and deploy a ConfigMgr Compliance Policy.
- Create and deploy an Intune Compliance Policy
- (Optional) – Create a Conditional Access policy to block access to corporate resources.
Prerequisite
You must have Co-Management configured with the Compliance policies Slider moved to Intune/Pilot.
In this post I do not intend to walk you through its configuration/setup. Please refer to this Tutorial to Enable Co-Management.
Additionally, a CMG (Cloud Management Gateway) would allow the management of devices outside corporate network.
ConfigMgr
We will create a Compliance Policy to validate the installation of the required updates.
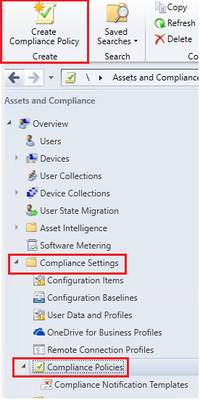
- Launch ConfigMgr console, under Assets and Compliance expand Compliance Settings click on Compliance Polices.
- Click Create Compliance Policy
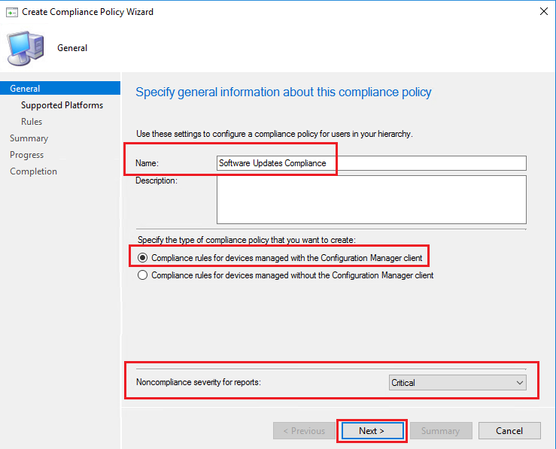
- Give a name to your Compliance Policy and leave the default setting of “Compliance rules for devices managed with the Configuration Manager client”.
- Additionally, you may want to change the Noncompliance severity for reports to Critical.
- Click Next to proceed.
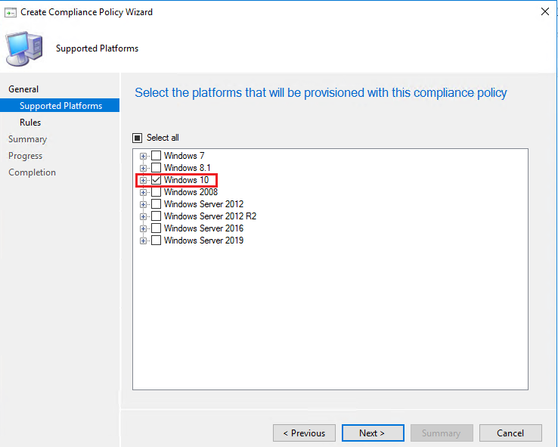
- In Supported Platforms page select Windows 10 Operating System.
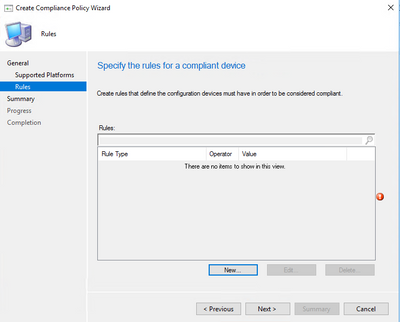
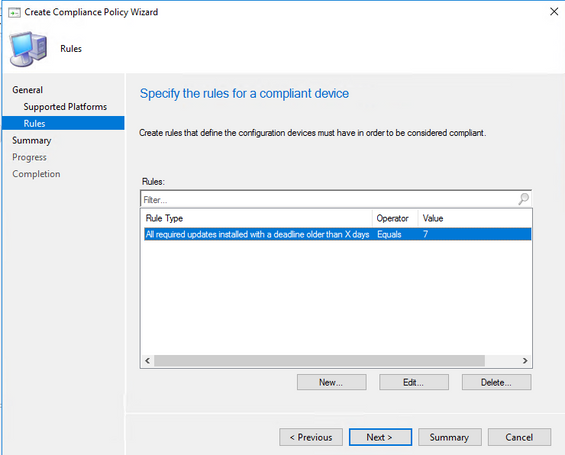
- In the Rules page click New
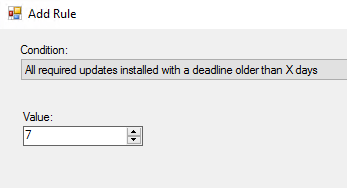
- From Conditions drop down choose “All required updates installed with a deadline older than X days” and specify a Value
In my case I chose 7 days.
- Click OK and Next to finish the wizard.
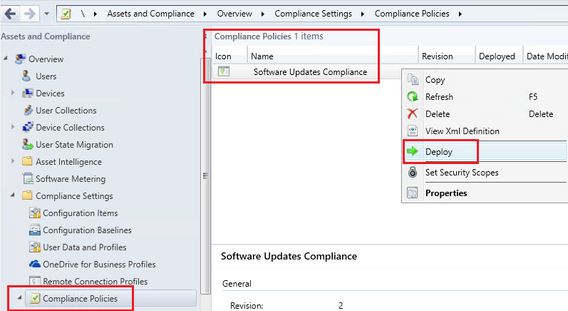
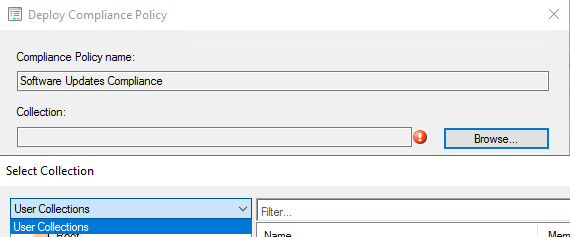
Deploy the Compliance Policy
- Right click on the Policy and choose Deploy.
Note: This can be only deployed to a User Collection. Make sure the target users have an Intune license.
Learn more about AD User Discovery: https://docs.microsoft.com/en-us/sccm/core/servers/deploy/configure/configure-discovery-methods#bkmk_config-adud
Learn more about Azure AD User Discovery: https://docs.microsoft.com/en-us/sccm/core/servers/deploy/configure/configure-discovery-methods#azureaadisc
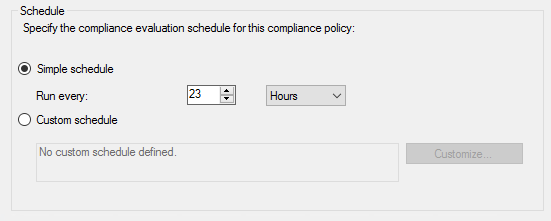
Note: The default compliance evaluation schedule is every 23 hours.
Intune
Next we create an Intune Device Compliance policy to honor ConfigMgr Compliance rule.
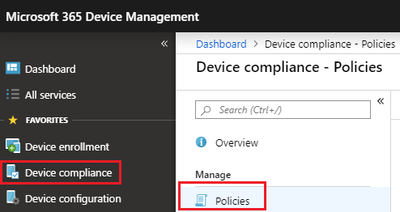
- Login to https://devicemanagement.microsoft.com
- Click Device compliance > Policies
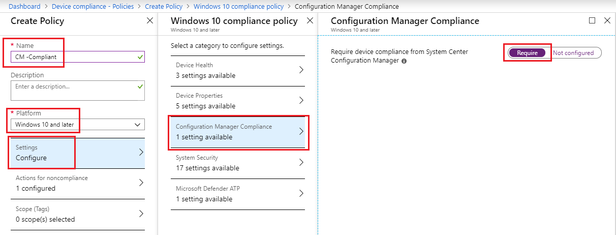
- Click Create Policy give it a Name.
- Under Platforms choose Windows 10 and Later
- Click Settings > Configuration Manager Compliance and click Require for “Require device compliance from System Center Configuration Manager”
- Click OK to close the blades
- Click Assignments tab to deploy this to a user group. Matching what you targeted in ConfigMgr.
Device Validation
Login to a Windows 10 device which is Co-Managed with Intune. For validation you may push newer updates or remove an existing update.
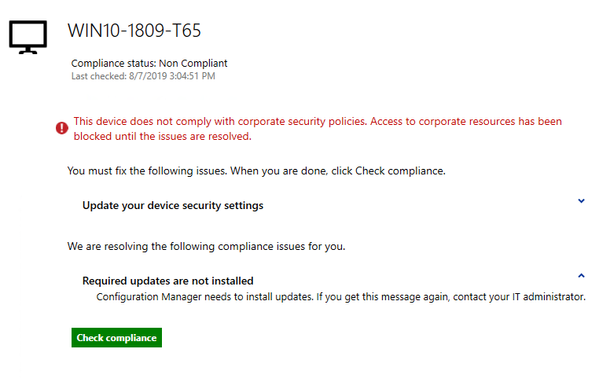
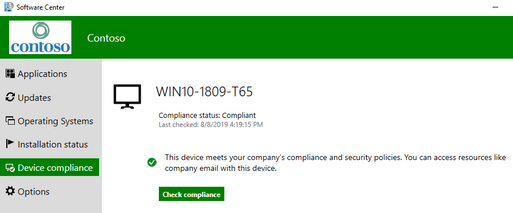
- Launch Software Center > Device Compliance
- Click Check Compliance
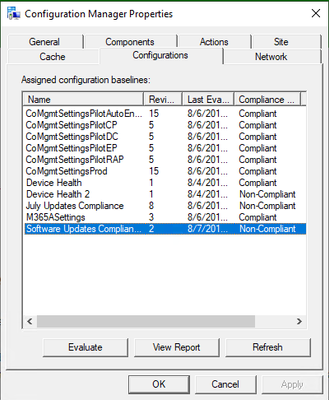
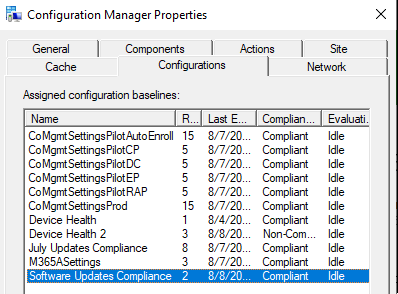
- Launch the ConfigMgr control panel applet. Under Configurations you will see the Compliance Rule as Non-Compliant
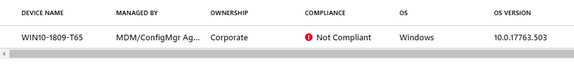
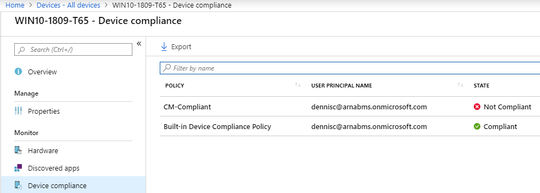
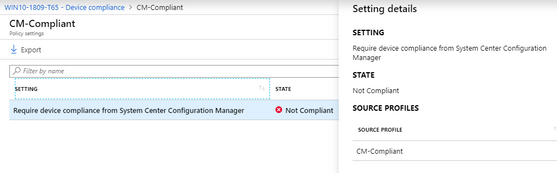
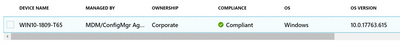
- View the state of the device in Intune Console
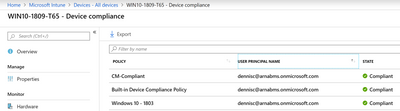
- Click on the device to view more details and find the reason for Non-Compliance.
Conditional Access
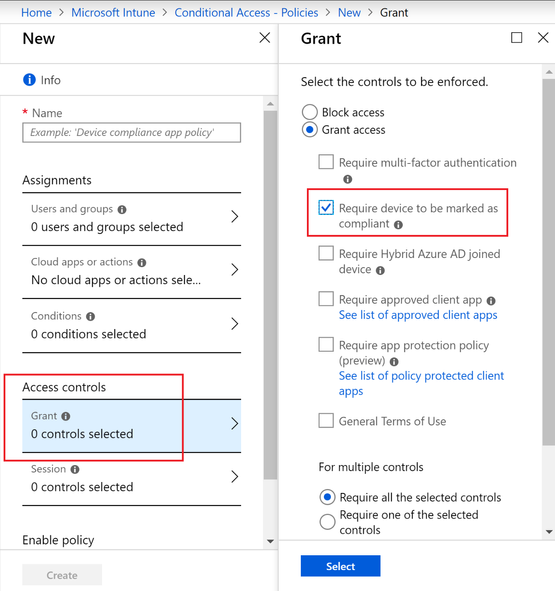
From here you can create a Conditional Access policy to block access to the corporate resources of your choice.
Choose the desired users, cloud apps and conditions.
- Under Access Controls > Grant > Select “Require device to be marked as compliant”.
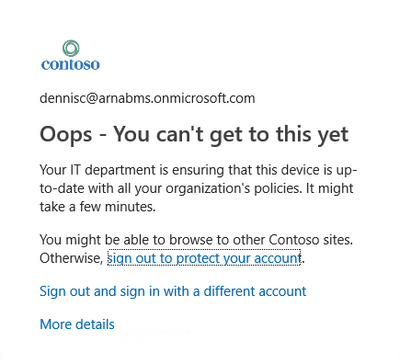
When you try to access one of the Cloud resources (example corporate email), you will be denied access.
Remediation
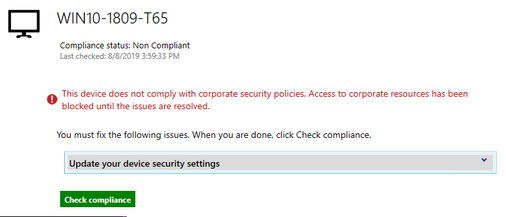
Typically, you will check the device under Intune Portal to identify the offending Device Compliance policies. In this case we already know the cause, ensure the required updates are installed.
Once the updates are installed, when you check the Compliance button in Software Center, you may temporarily see the screen below.
If you look at the corresponding Compliance policy, it will show Compliant.
All you need is to close the Software Center and Reopen.
Click Check Compliance button one more time and the device should appear Compliant
Intune Portal will also reflect compliance and will restore access to corporate resources.
Thanks,
Arnab Mitra