This post has been republished via RSS; it originally appeared at: Intune Customer Success articles.
Hello everyone, today we have a fantastic article from Intune Sr. Support Engineer and resident Jamf expert Shonda Hodge. Shonda walks through the entire process of configuring integration of Microsoft Intune and Jamf Pro, creating and deploying policies and profiles, as well as enrolling and registering your Mac computers. As always, if you have any feedback for us please leave a comment below.
=====
Introduction
This article discusses the integration of Microsoft Intune and Jamf Pro. Topics covered include the following:
- Architecture and requirements
- Configuration steps for Jamf and Intune
- Creating and deploying device compliance policies in Intune
- Creating and deploying configuration profiles via Jamf
- Registering user devices with Azure Active Directory (AAD)
- Enrolling into Jamf and registering with Intune
- Information on the inventory attributes shared from Jamf to Intune
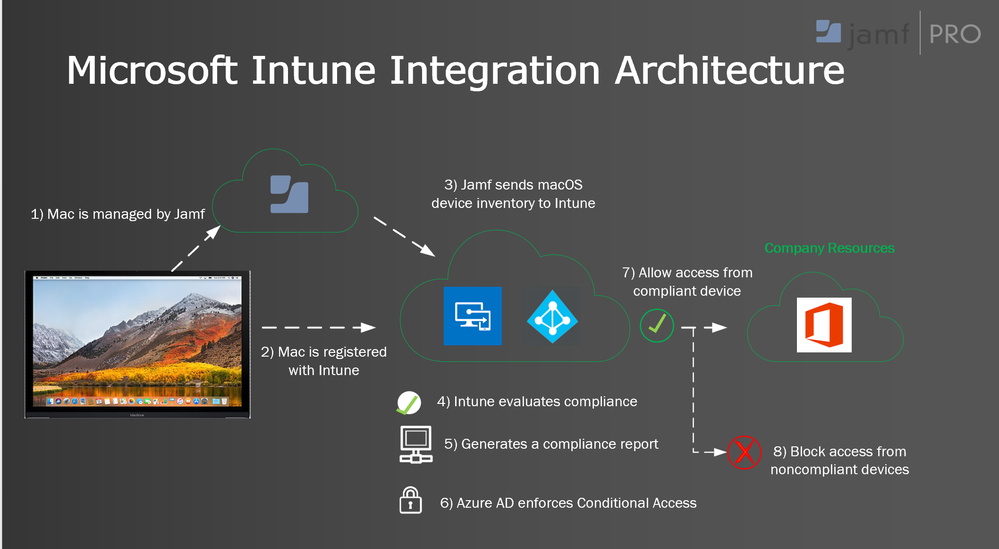
Architectural Overview
- Jamf delivers information about the management state and health of Apple’s Mac computers to Microsoft Intune’s device compliance engine.
- Intune’s device compliance engine integrates with Azure Active Directory and allows you to identify unmanaged and non-compliant Mac computers in your environment.
- You can then remediate the identified machines in Jamf’s Self Service for macOS.
Integration Requirements
You will need the following to configure Microsoft Intune integration with Jamf Pro:
- The latest version of Jamf Pro
- Microsoft Intune and Microsoft AAD Premium P1 licenses (recommended Microsoft Enterprise Mobility + Security license bundle)
- A user with Microsoft Intune Integration privileges in Jamf Pro
- The latest version of the Microsoft Intune Company Portal app
- End user computers with macOS 10.11 or later
Reference: http://docs.jamf.com/technical-papers/jamf-pro/microsoft-intune/10.9.0/Requirements.html
Configuration steps for Jamf and Intune
To enable the connection between Intune and Jamf, configuration is required for both Microsoft Intune and Jamf Pro. When the connection between Microsoft Intune and Jamf Pro is successfully established, Jamf Pro sends the computer inventory state of each managed computer that has checked in with Jamf Pro within the last 24 hours. For a list of the computer attributes that Jamf Pro sends to Microsoft Intune, see Inventory information shared with Microsoft Intune at the end of this post.
Configuring the connection between Jamf Pro and Microsoft Intune involves the following steps:
1. Creating a new application for Jamf Pro in Microsoft Azure
2. Configuring Microsoft Intune Integration settings in Jamf Pro
3. Configuring Microsoft Intune to allow the Jamf Pro integration
NOTE Information is sent to Microsoft Intune only for computers that have completed the device registration process with Azure Active Directory.
Creating a new application for Jamf Pro in Microsoft Azure
NOTE When configuring a conditional access policy to work with Jamf and Intune DO NOT target the Jamf Native macOS Connector app. This will break registration.
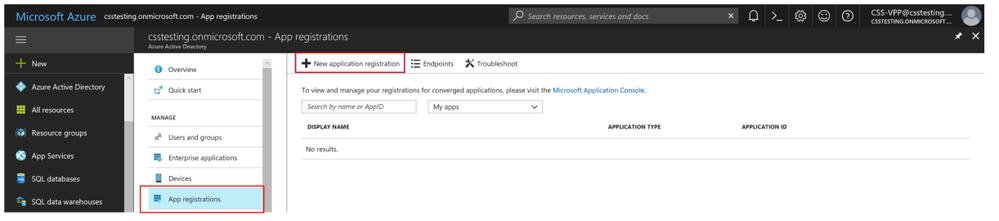
1. Log onto portal.azure.com.
2. Navigate to Azure Active Directory -> Manage -> App registrations.
3. Click +New application registration.
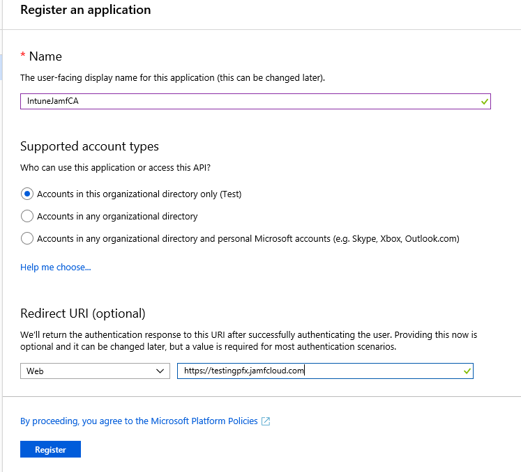
4. Enter a display name (e.g. IntuneJamfCA)
Supported account types – leave default option selected
Sign-on URL: Enter your Jamf Pro instance URL
5. Click Register.
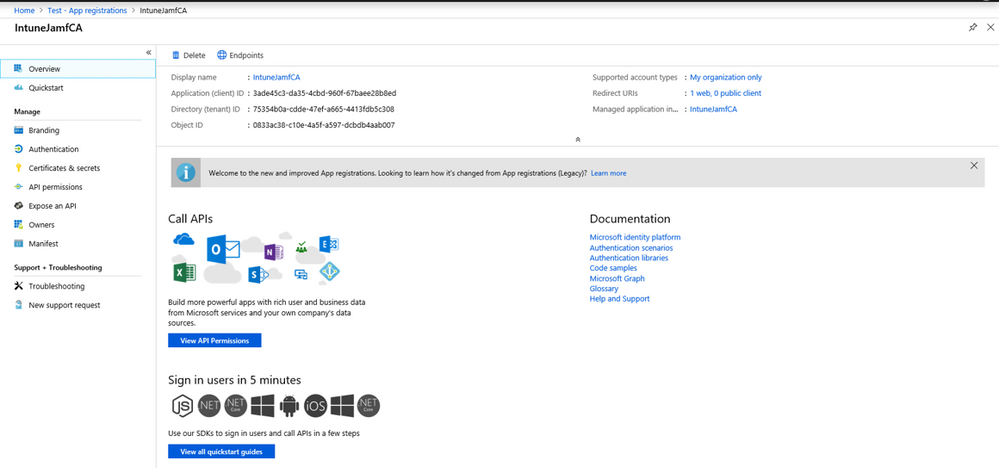
6. Copy the Application ID field. The Application ID is required to configure the Compliance Connector in Intune and the Microsoft Intune integration settings in Jamf Pro.
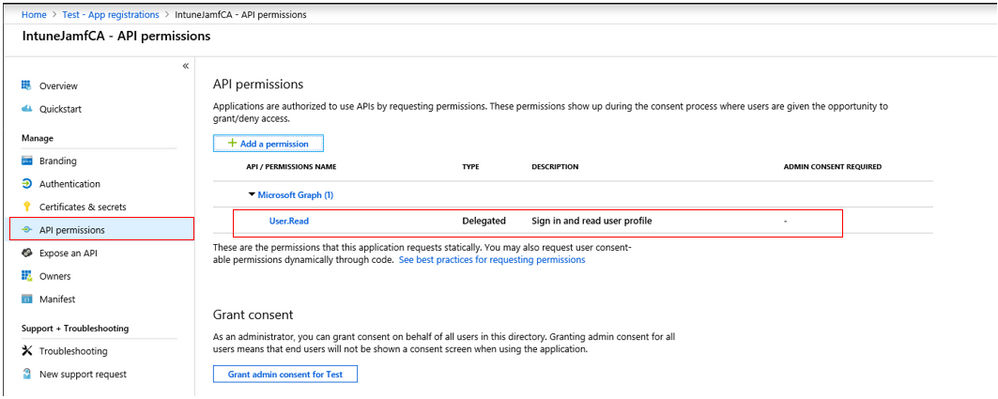
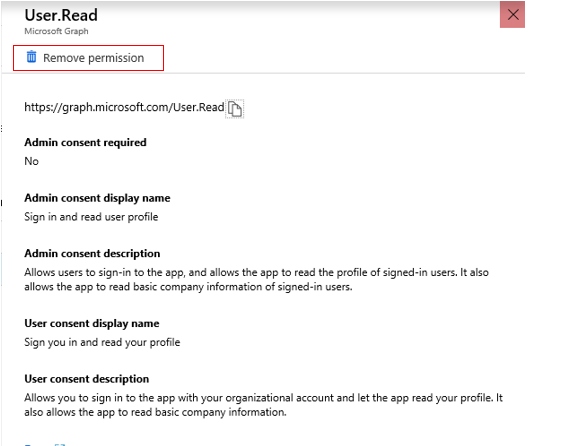
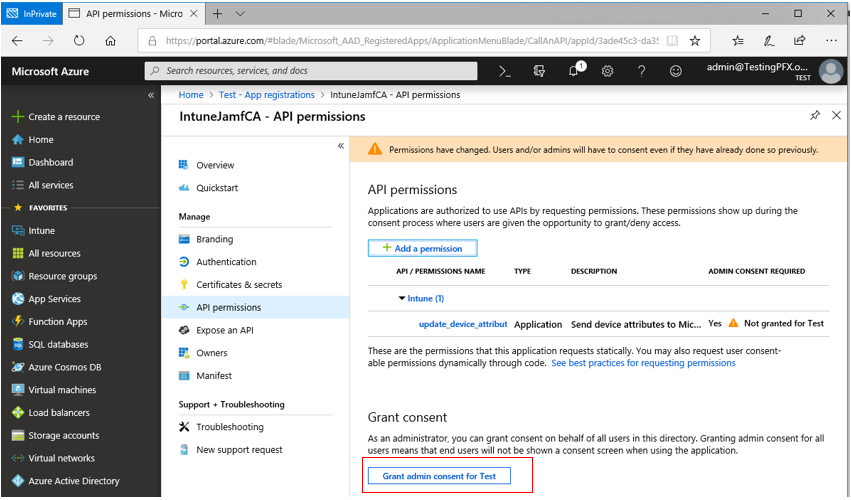
7. Under Manage, select API permissions. Click on the permission itself (nested), not the API.
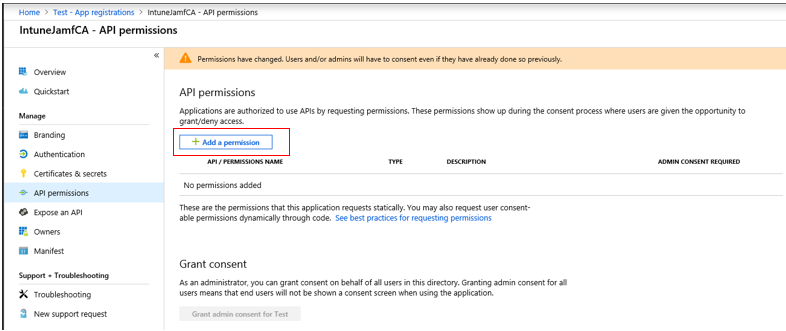
8. Click Remove permission. Once gone, the API itself will disappear from the menu.
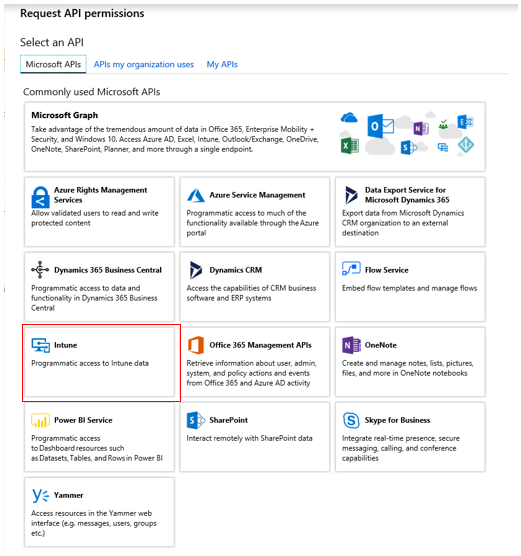
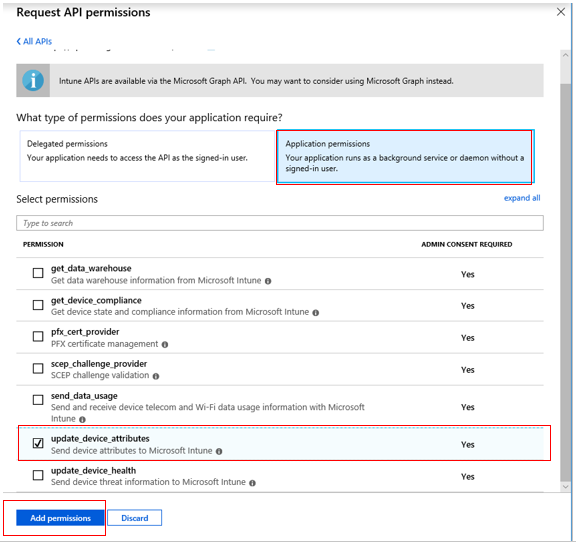
9. Click +Add a permission.
10. Select Intune.
11. Check the box for update_device_attributes (send device attributes to Microsoft Intune). Click Add permissions.
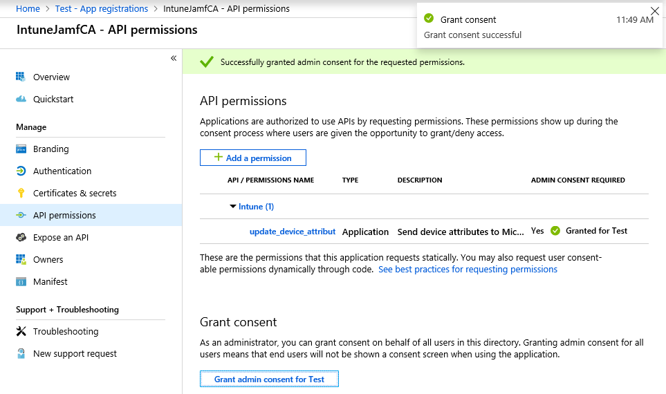
12. Under Grant consent, click on “Grant admin consent for <name of tenant>”
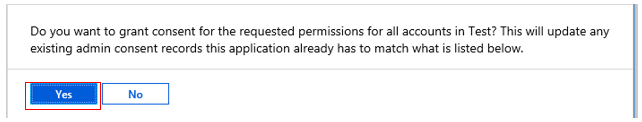
13. Click Yes on the “Do you want to grant consent for the requested permissions for all accounts in <tenant name>?”
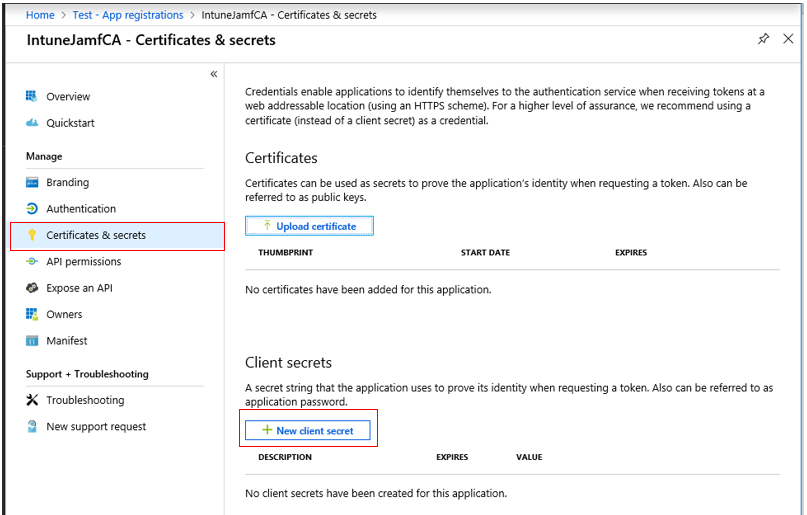
14. Select the Certificates & secrets blade. Select "New client secret".
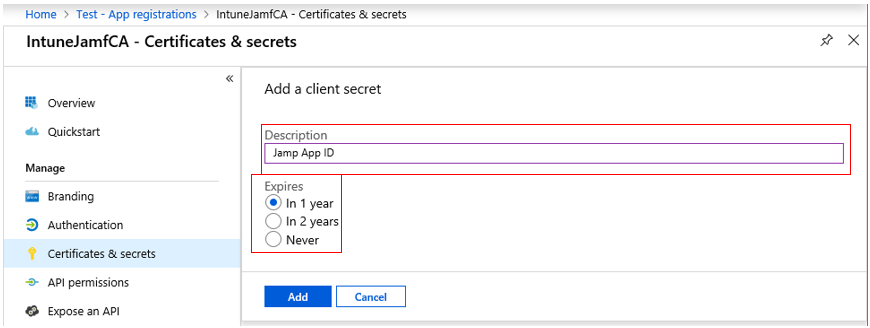
15. Enter a Description (EX: JSS Key) and select an expiration date. Click Add.
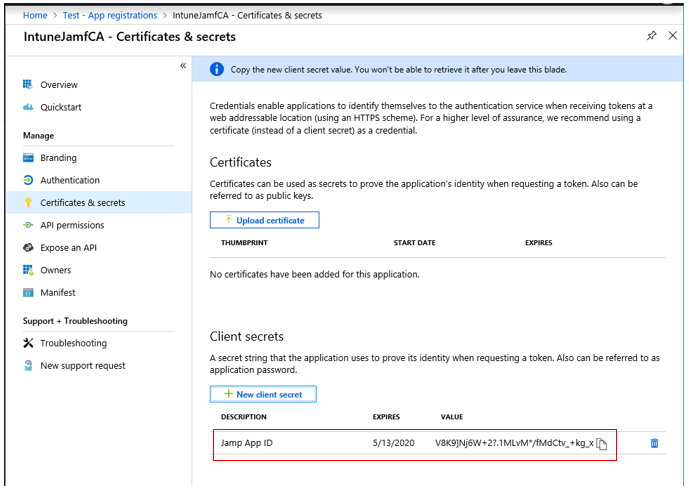
16. Copy the Client secret ID.
NOTE You won't be able to see it again once you leave so make a safe copy of it.
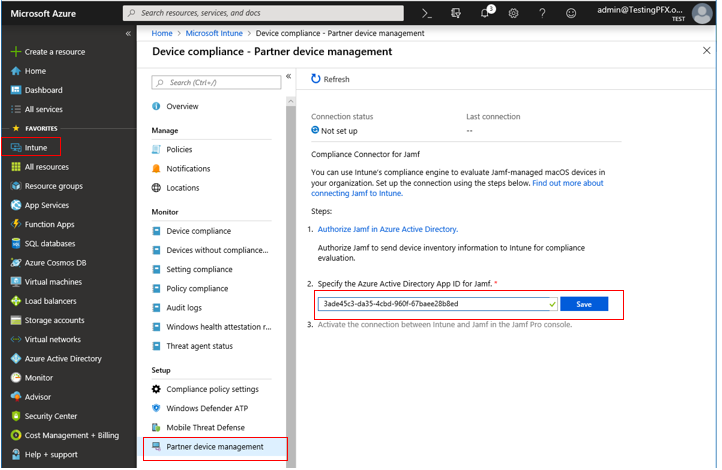
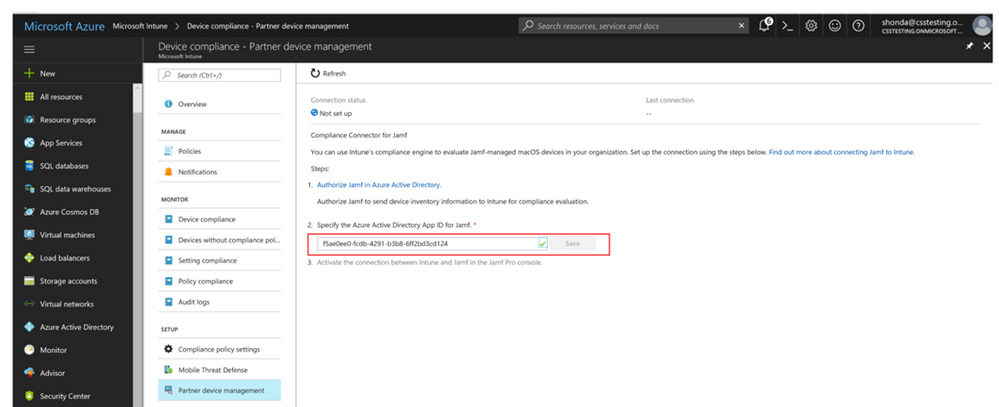
17. Select the Intune service from the far left of portal.azure.com. Select the Device Compliance blade. Click on "Partner device management". Put in the application ID for the enterprise app that was just created and click Save.
Configuring Microsoft Intune Integration settings in Jamf Pro
NOTE Jamf documentation on configuring Microsoft’s Intune Integration settings in Jamf Pro can be found here.
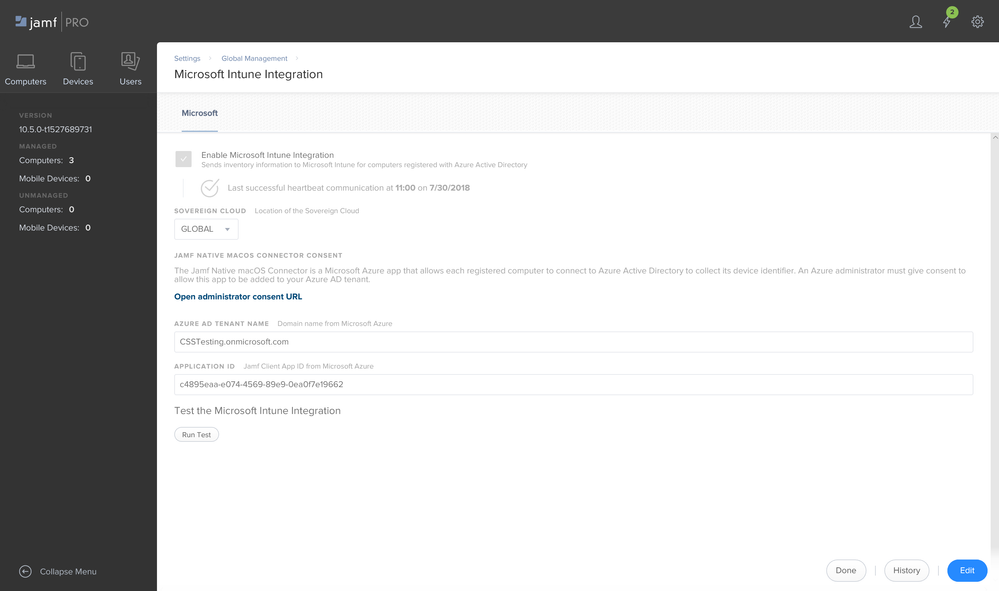
1. Log onto the Jamf admin console, click on the gear icon in the upper right-hand corner, then under Global Management select Microsoft Intune Integration and click Edit.
2. Select Enable Microsoft Intune Integration.
- Sovereign Cloud – Select Public Cloud
- Azure AD Tenant Name – <Enter your tenant name>
- Application ID – <Enter app ID from Azure web app>
- Application Key - < Enter app key from Azure web app>
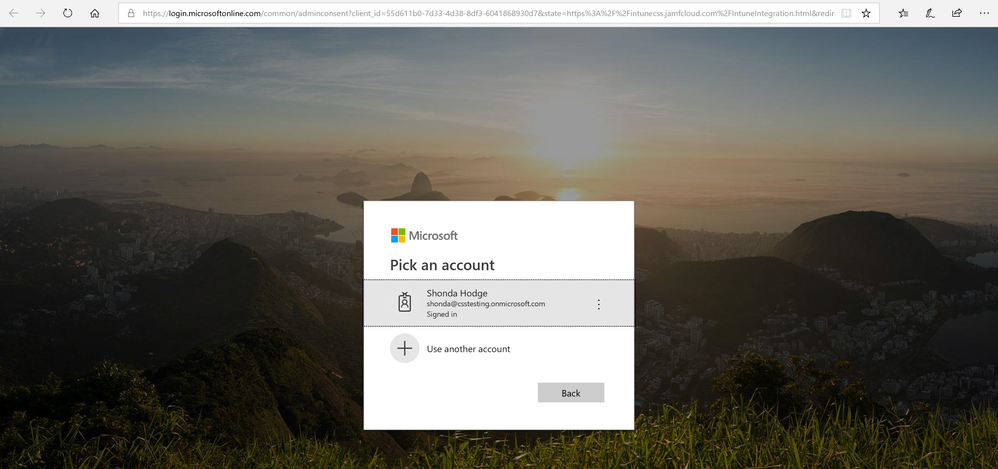
3. Click Open administrator consent URL.
4. Pick an account and enter your password.
Configuring Microsoft Intune to allow Jamf Pro integration
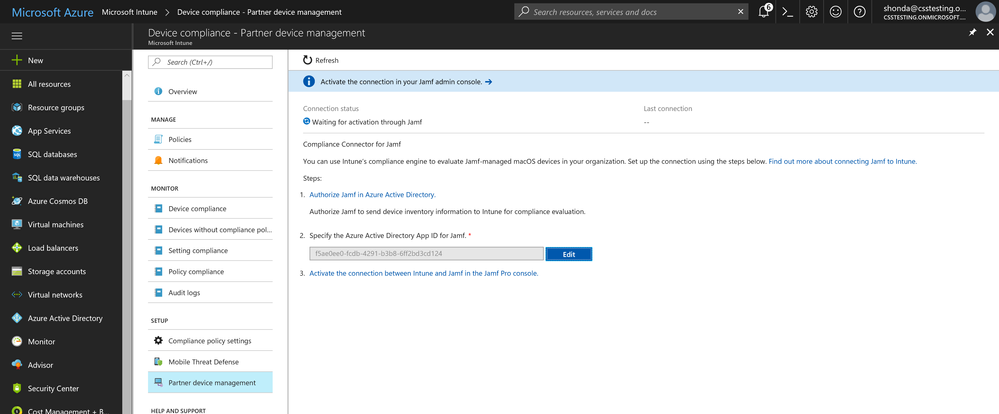
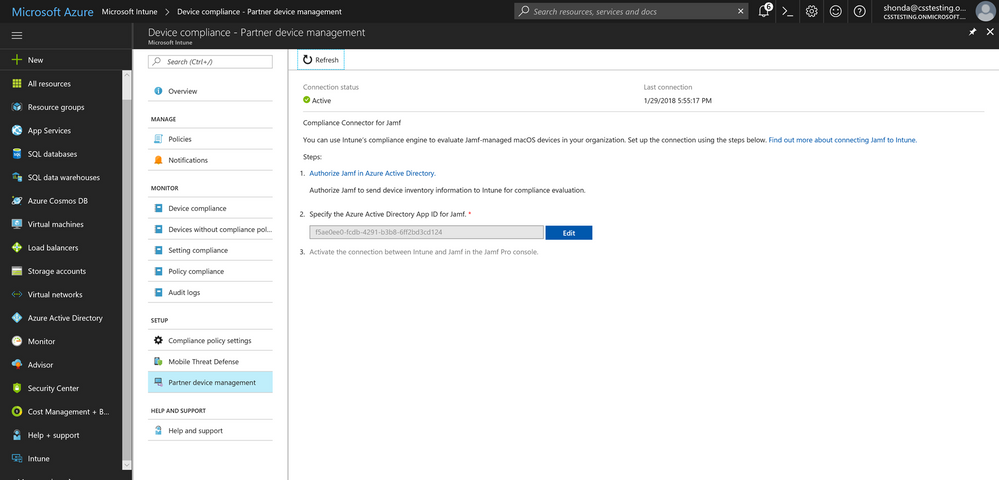
1. In the Azure portal, navigate to the Intune blade -> Device Compliance -> Partner device management.
2. Enable the Compliance Connector for Jamf by pasting the Application ID into the Jamf Azure Active Directory App ID field.
NOTE Click Refresh to get the Save option.
Creating device compliance policies in Microsoft Intune
Now that the connection between Jamf Pro and Microsoft Intune has been established, you can start applying compliance policies to end user computers in Microsoft Intune.
1. Open the Microsoft Azure portal, navigate to Intune > Device Compliance > Policies and create policies for macOS. You can also select a series of actions (e.g., sending warning emails) that should be applied to non-compliant users and groups.
2. Once you create all required compliance policies, simply create Assignments for the compliance policies to apply them to specific users or groups.
IMPORTANT Due to a known issue that sometimes prevents alphanumeric passwords from being reported correctly from Jamf Pro, the alphanumeric password type should not be used when creating compliance policies in Microsoft Intune.
Reference: https://docs.microsoft.com/en-us/intune/conditional-access-assign-jamf; http://docs.jamf.com/technical-papers/jamf-pro/microsoft-intune/10.9.0/Apply_Device_Compliance_Policies_to_Mac_Computers.html
Deploying a configuration profile in Jamf Pro
To register user computers with Jamf Pro and Azure Active Directory, you must first create a policy in Jamf Pro that installs the Company Portal app for macOS on those computers. Deploying the Company Portal app from Microsoft to computers involves the following steps:
1. Downloading the Company Portal app from Microsoft.
2. Uploading the Company Portal app to Jamf Pro as a package.
3. Deploying the Company Portal app to computers.
Downloading the Company Portal app from Microsoft
On a Mac computer, download the current version of the Company Portal app for macOS from the Microsoft website. Do not install it; you just need a copy of the app to upload to Jamf Pro.
Navigate to https://go.microsoft.com/fwlink/?linkid=862280 to download the CompanyPortal_Installer.pkg file.
Upload the Company Portal app to Jamf Pro as a package
1. Upload the Company Portal app to a distribution point in Jamf Pro.
2. In Jamf Pro, navigate to Settings -> Computer Management -> Packages.
3. Create a new package with the Company Portal app for macOS and click Save.
Deploy the Company Portal app to computers
1. In Jamf Pro, navigate to Computers -> Policies and create a policy that deploys the Company Portal app to users.
a. Use the General payload to configure policy settings.
- For Trigger select "Enrollment Complete" and "Recurring Check-in",
- For Execution Frequency, select "Once per computer".
b. Select the Packages payload and click Configure.
c. Click Add for the package with the Company Portal app.
d. Configure the settings for the package.
e. Specify a distribution point for computers to download the package from.
2. Click the Scope tab to specify the computers on which the Company Portal app should be installed.
3. Click Save.
NOTE The policy runs on computers in the scope the next time they check in with Jamf Pro and meet the criteria in the General payload.
Creating a policy in Jamf to have users register their devices with Azure Active Directory
Before directing users or groups to register their computers with Azure AD, you must deploy the Company Portal app to user computers. In Jamf Pro, there are a couple different methods to identify users who do not have the Company Portal app installed on their computers.
Method 1
1. In Jamf Pro, create a smart computer group to identify computers that do not have the Microsoft Company Portal app installed.
2. In Jamf Pro, create a policy that deploys the Company Portal app to the smart group created in Step 1.
For Trigger select "Login" or "Recurring Check-in“
For Execution Frequency, select "Ongoing".
The policy is used to update computer inventory, and if the Company portal app is known to be installed on a computer, a computer will fall out of the smart group created in Step 1 and Jamf Pro will no longer try to install it.
Method 2
1. In Jamf Pro, create a smart computer group to identify computers that do not have the Azure Active Directory ID attribute.
2. (Optional) You an add a second criteria to this group of not being a member of the smart group you created in Step 1 to ensure that only computers with the Company Portal app are included in this group.
NOTE: For steps on how to create a Smart Group, see the following: http://docs.jamf.com/10.9.0/jamf-pro/administrator-guide/Smart_Computer_Groups.html
Directing users to register their computers with Azure Active Directory
End users need to launch the Company Portal app through Jamf Self Service to register the device with Azure AD as a device managed by Jamf Pro. This will require action on the part of end users. The recommendation is to contact end users through email, Jamf Pro notifications, or any other method that will notify end users telling them to click the button in Jamf Self Service.
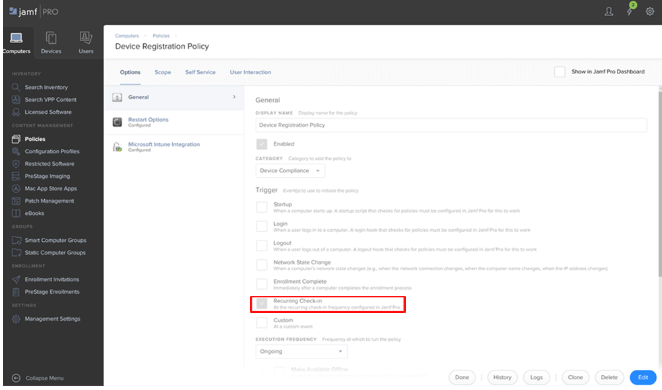
1. In Jamf Pro, navigate to Computers -> Policies and create a new policy for device registration.
2. Use the General payload to specify policy settings, including trigger and execution frequency.
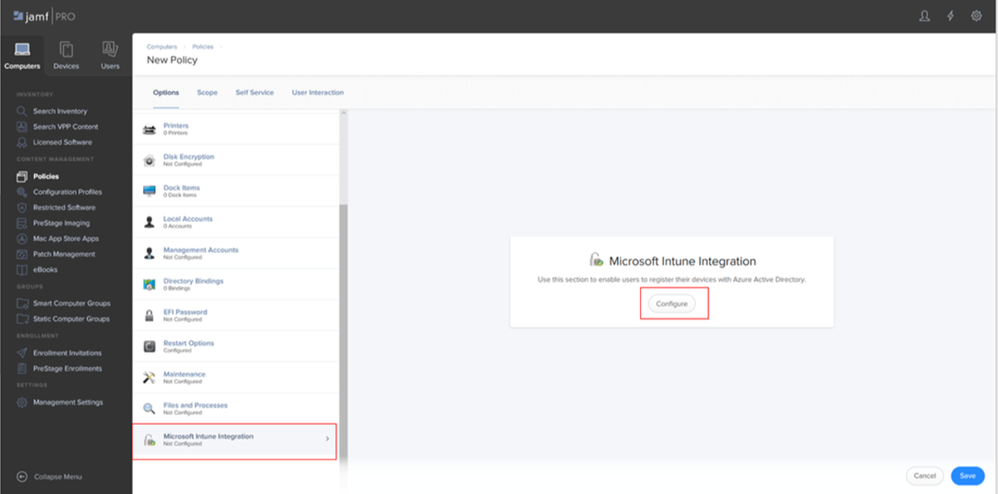
3. Configure the Microsoft Intune Integration payload.
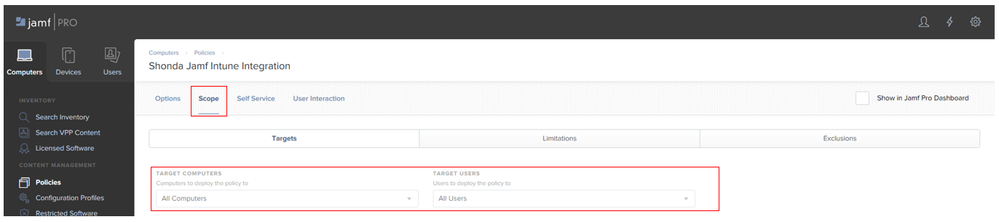
4. Click the Scope tab and scope the policy to all targeted devices.
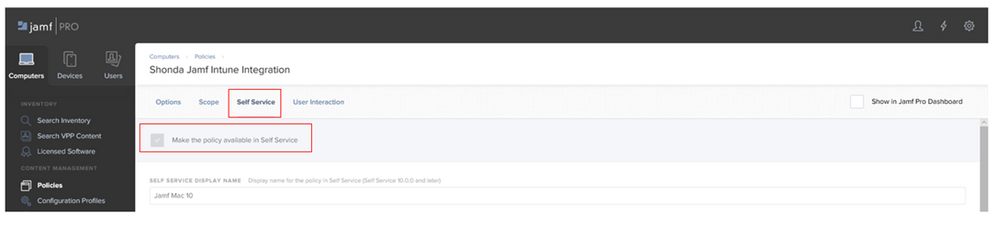
5. Click the Self-Service tab to make the policy available in Jamf Self Service.
6. (Optional) Include the policy in the Device Compliance category.
7. Click Save.
IMPORTANT: The Company Portal app must be launched from Jamf Self Service to begin device registration. Launching the Company Portal app manually (e.g., from the Applications or Downloads folder) will not register the device. If an end user launches the Company Portal app manually they will see a warning, 'AccountNotOnboarded'.
Enrolling into Jamf and registering with Intune
There are two ways to enroll into Jamf:
- Standard enrollment.
- Enrollment using the Quick Add package.
Enrollment using the Quick Add package
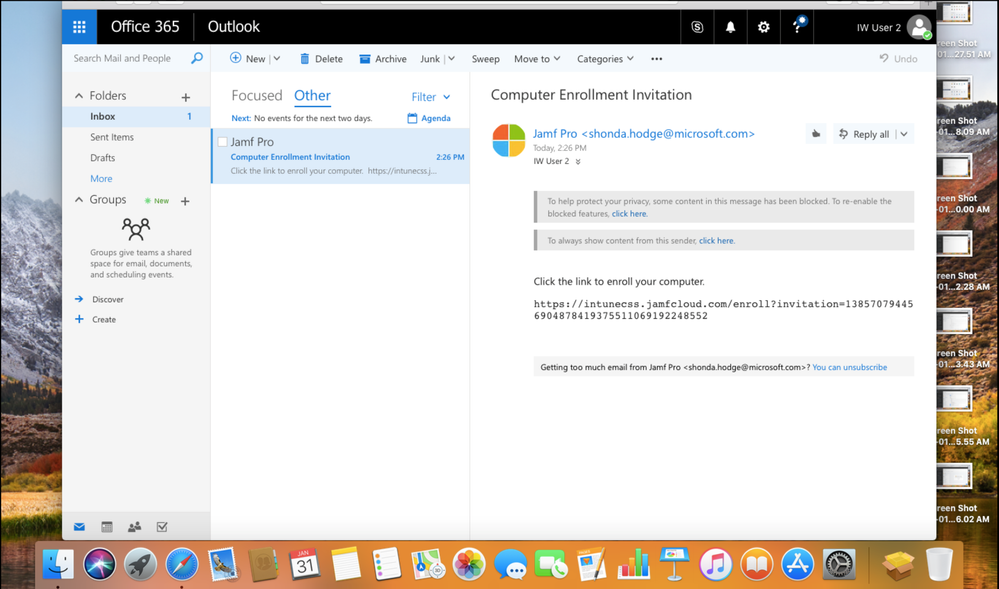
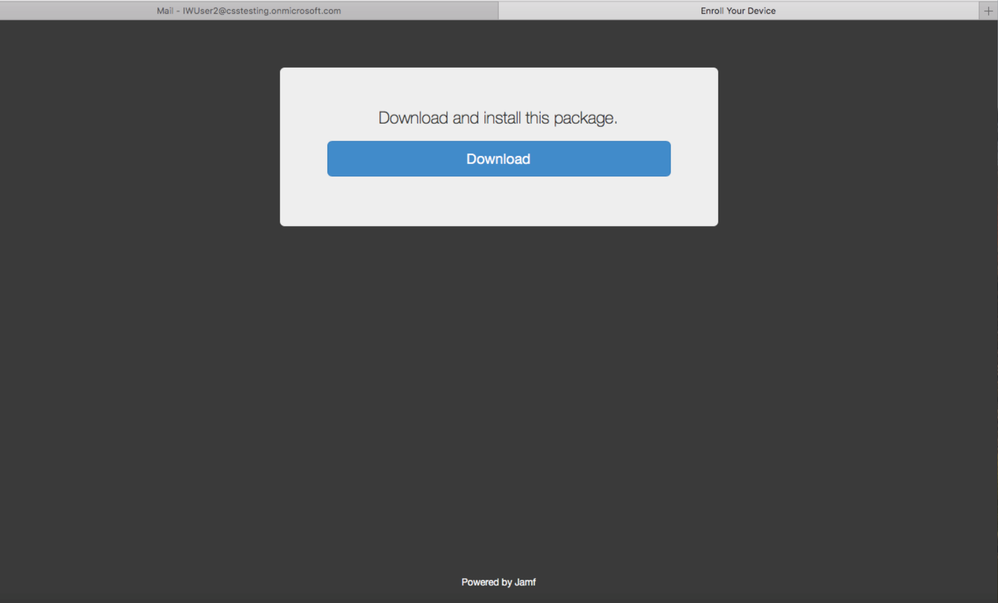
1. The user receives the enrollment email and they copy and paste the link into a web browser.
2. Click Download to begin enrollment.
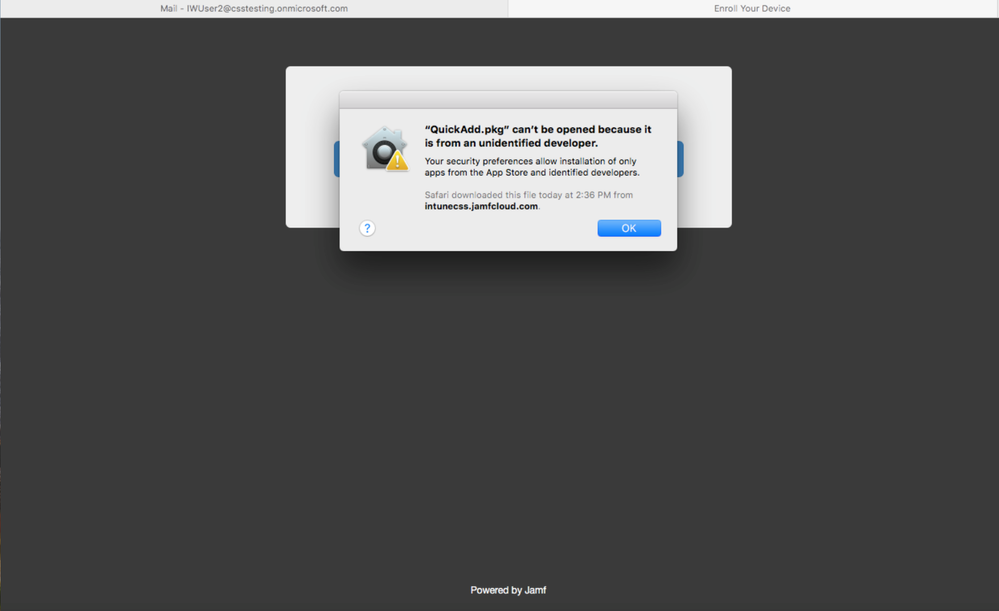
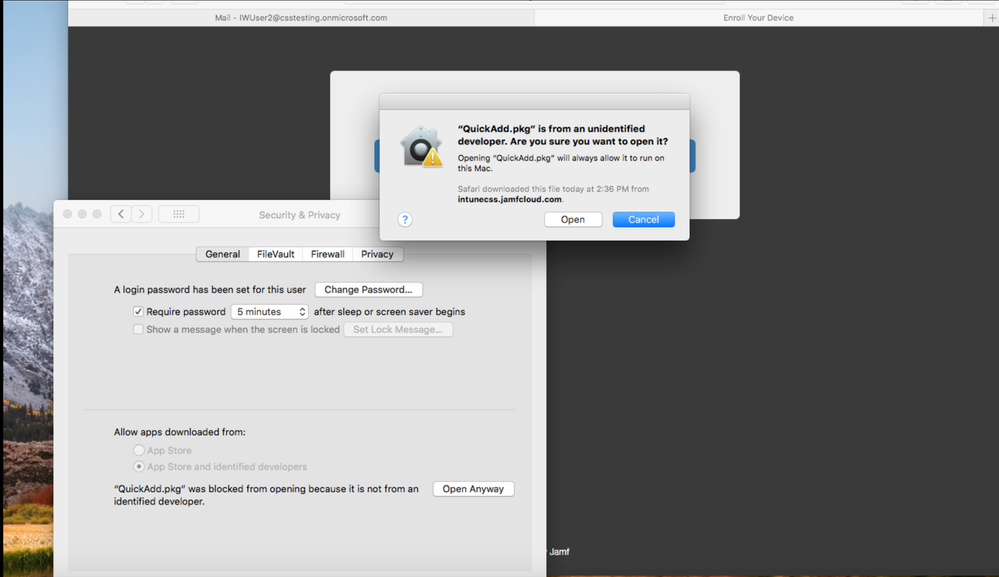
NOTE If the message below pops up, click OK. Open System Preferences to allow the package to be installed.
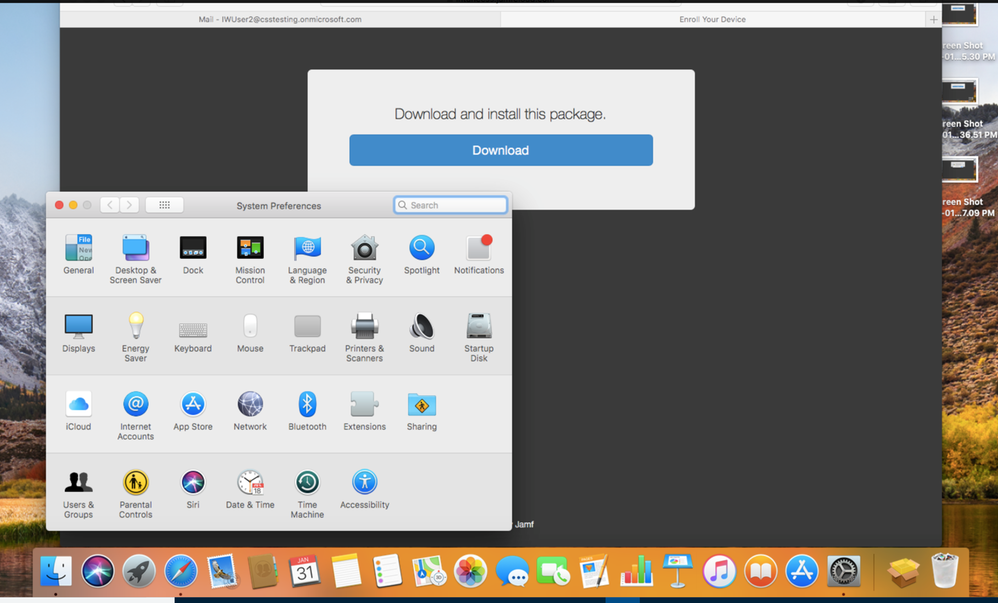
3. Click Launchpad ->System Preferences – Show All -> Security & Privacy
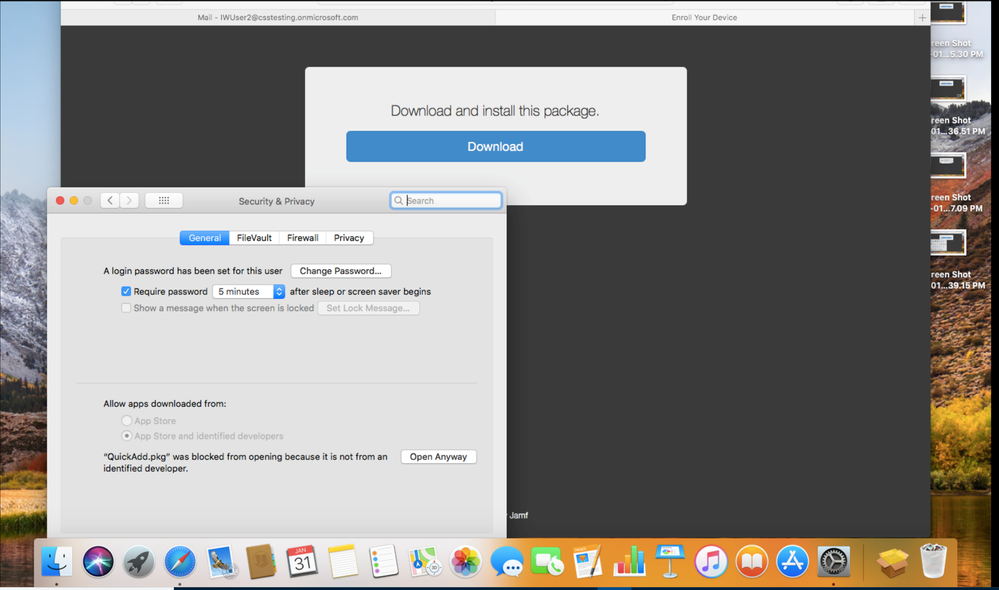
4. Under “Allow apps downloaded from” choose Open Anyway.
5. Select Open.
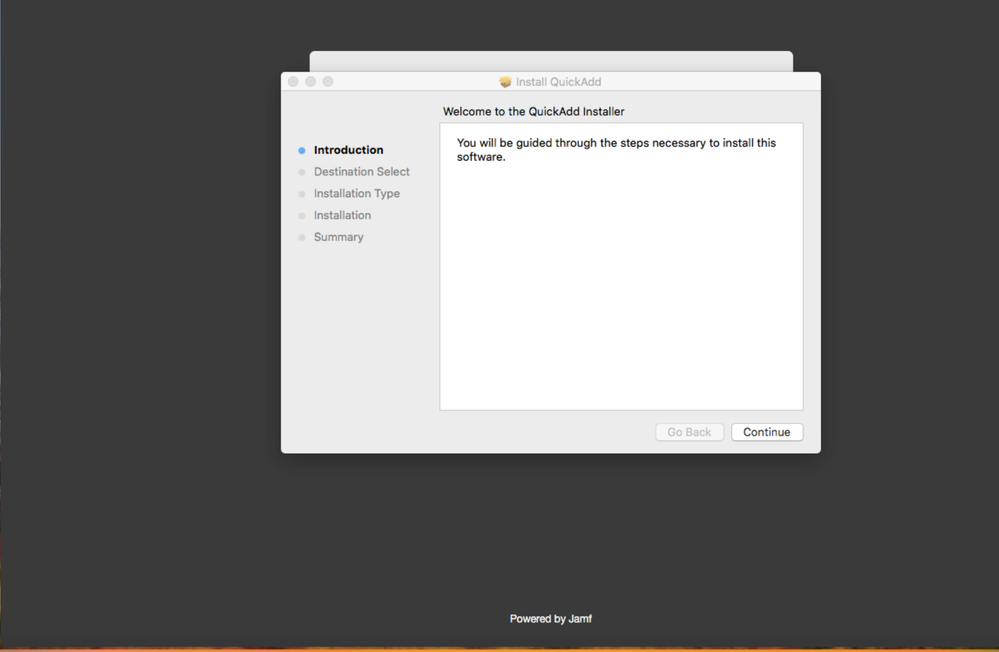
6. Select Continue.
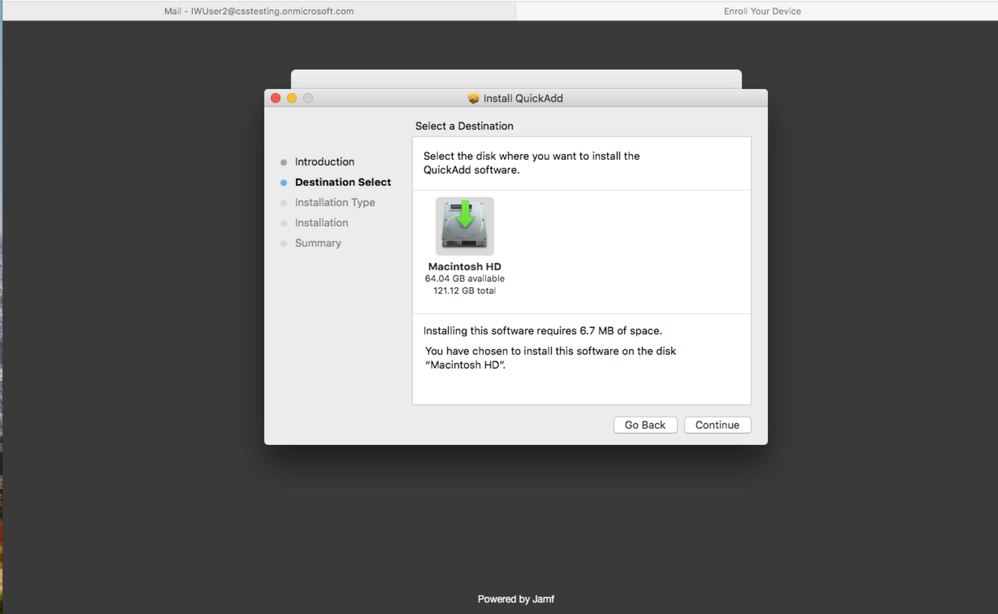
7. Select Continue.
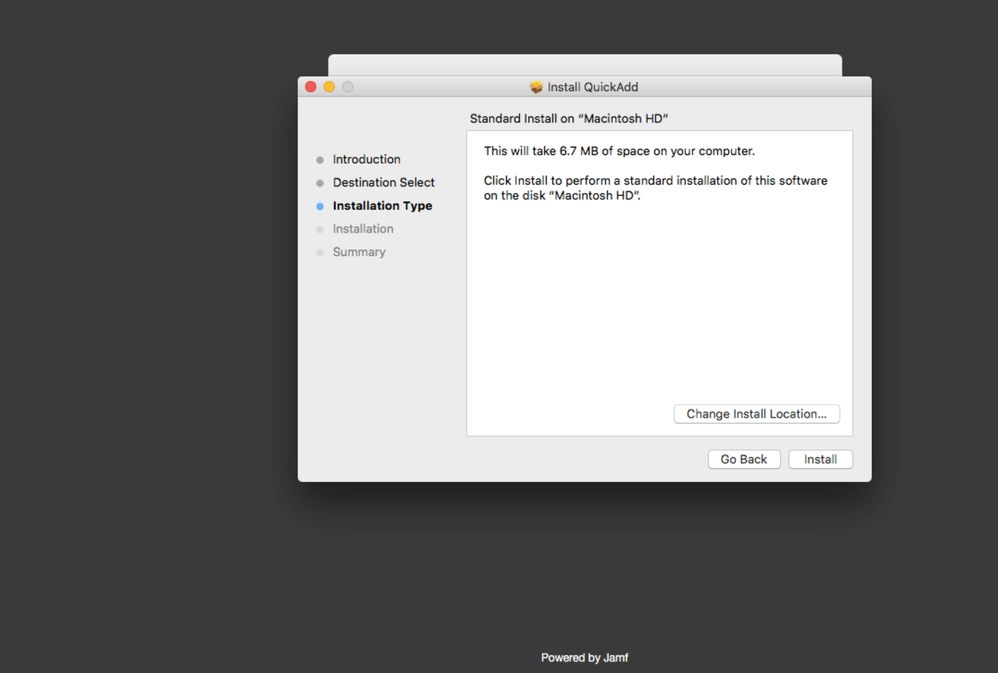
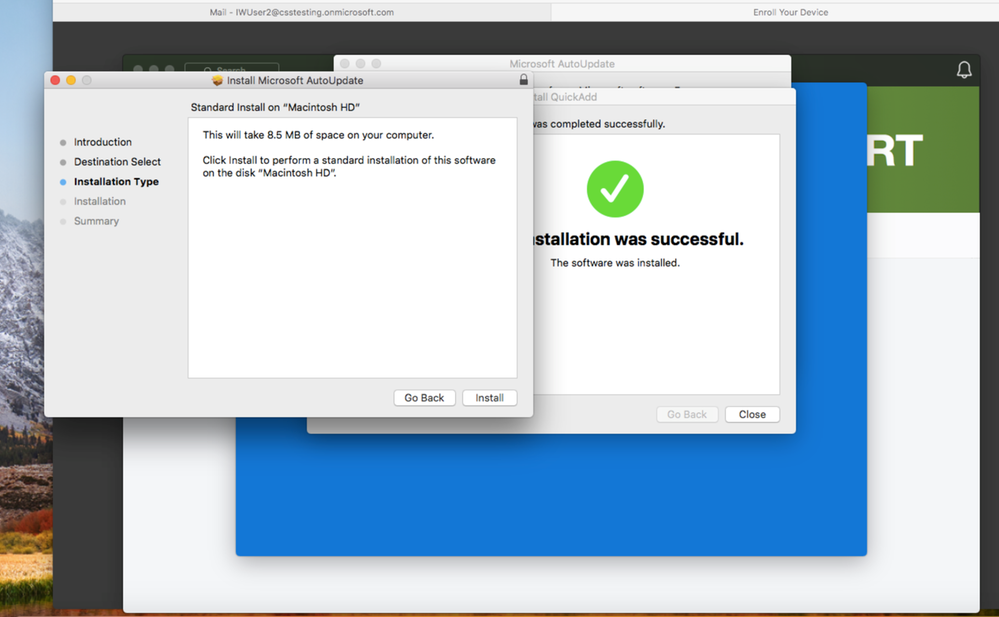
8. Select Install.
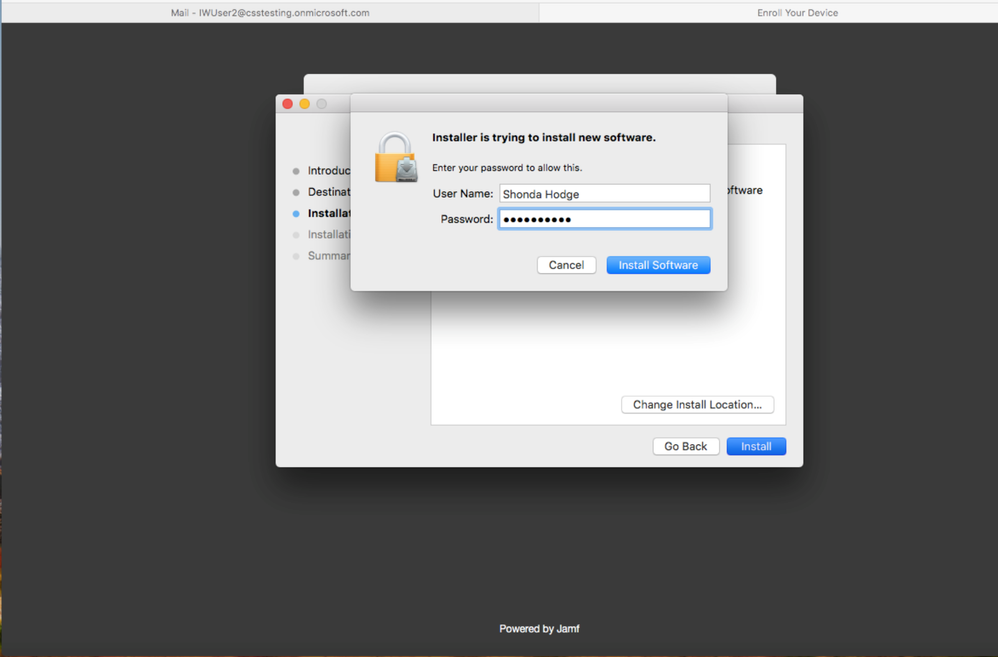
9. Enter your password and click Install Software.
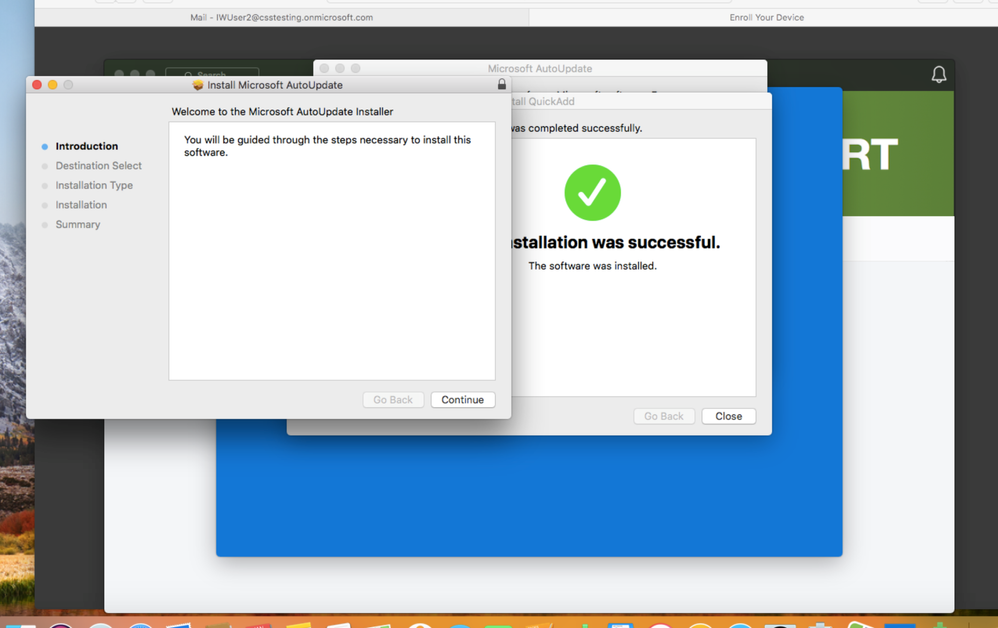
10. Click Install to enroll the device into Jamf, install the Company Portal app, and to register the device with Intune.
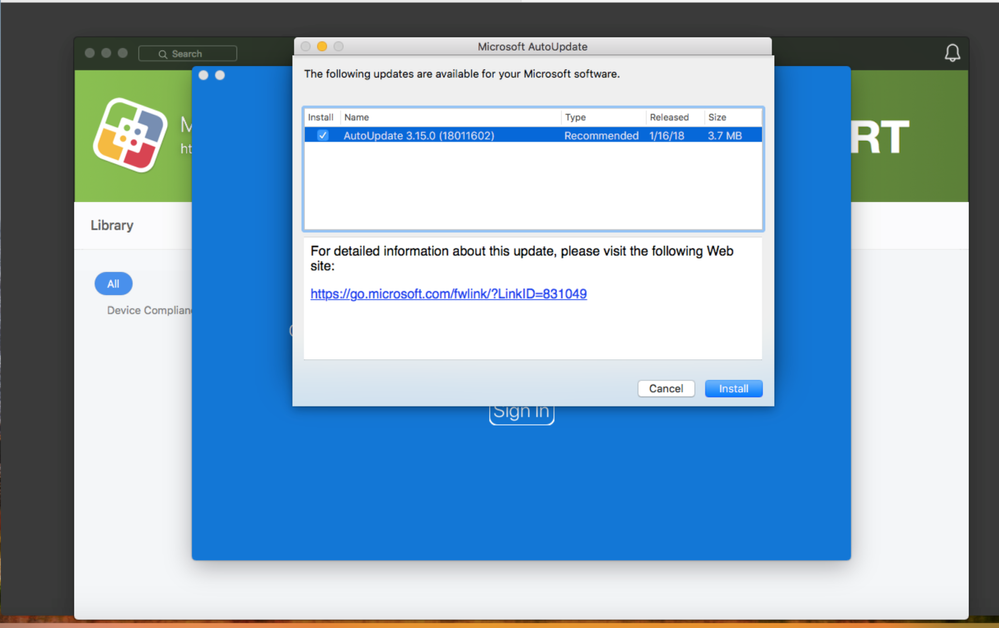
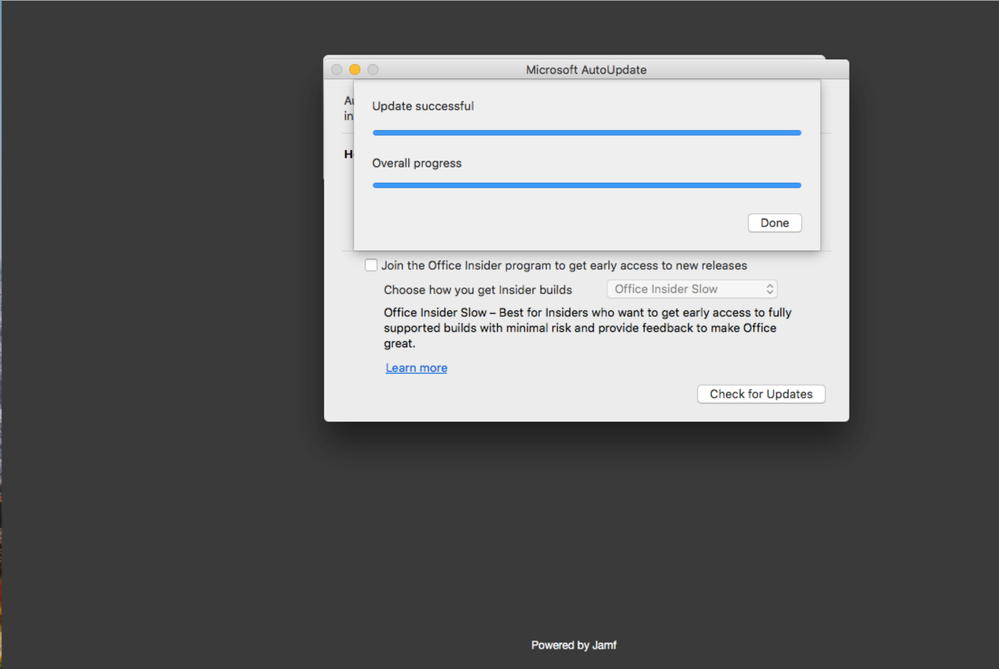
11. If there are Microsoft updates, a notification will popup. Click Install to get the latest Company Portal app.
12. Click Continue.
13. Click Install.
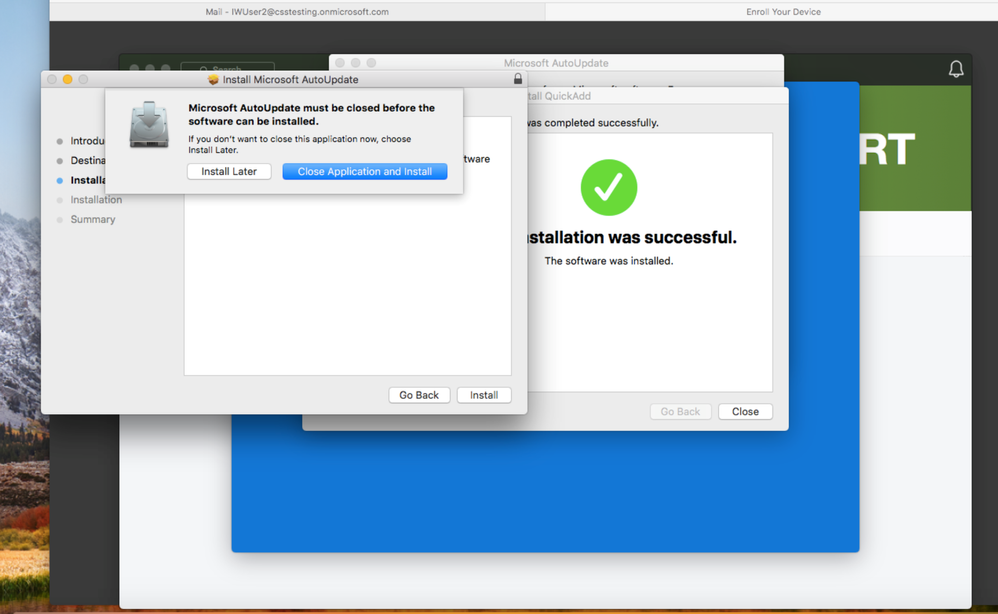
14. Click Close Application and Install.
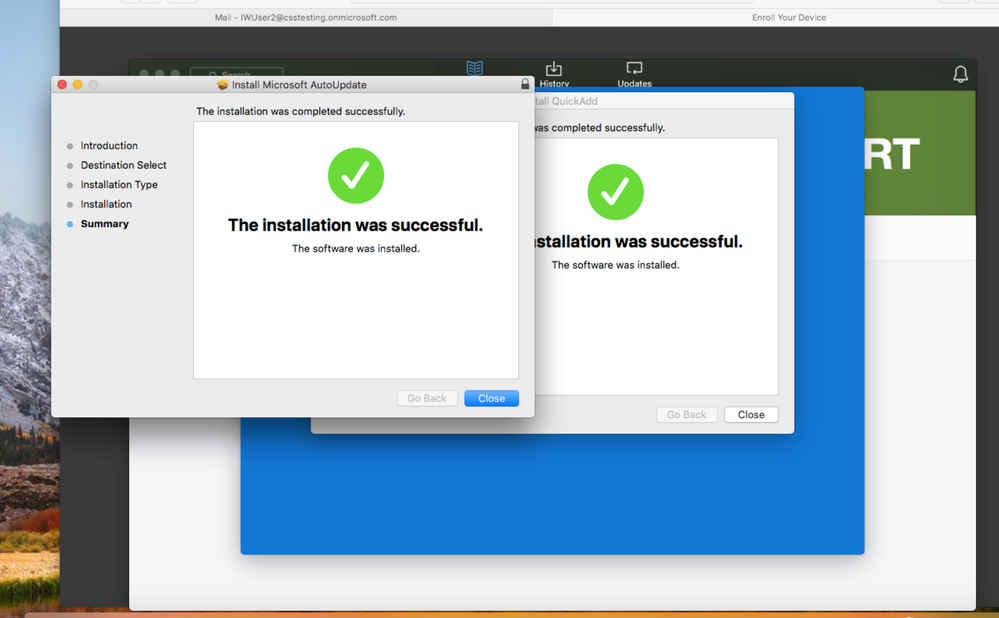
15. Click Close.
16. Click Close.
NOTE You can bypass a Company Portal app (CP app) update if necessary after enrollment, then come back and update the Company Portal app normally.
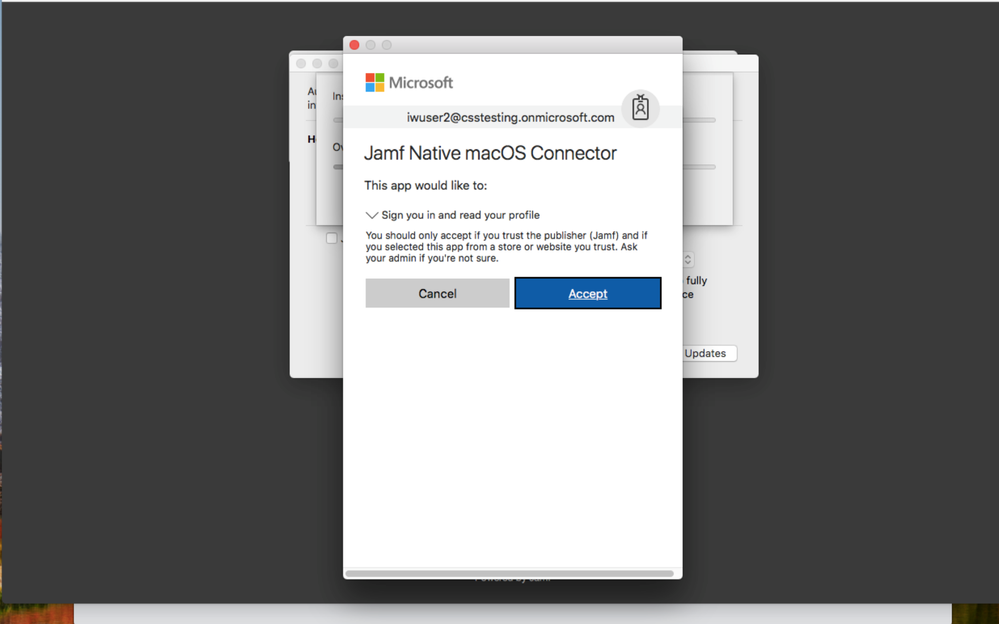
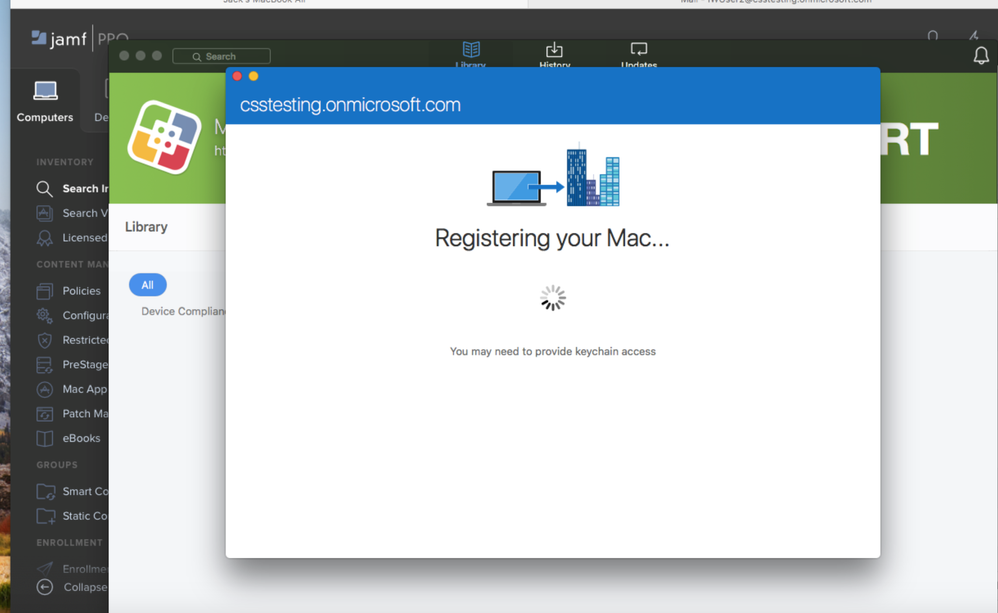
17. Sign-in to register the Mac computer with Intune and create an Azure Active Directory ID.
18. Click to Accept.
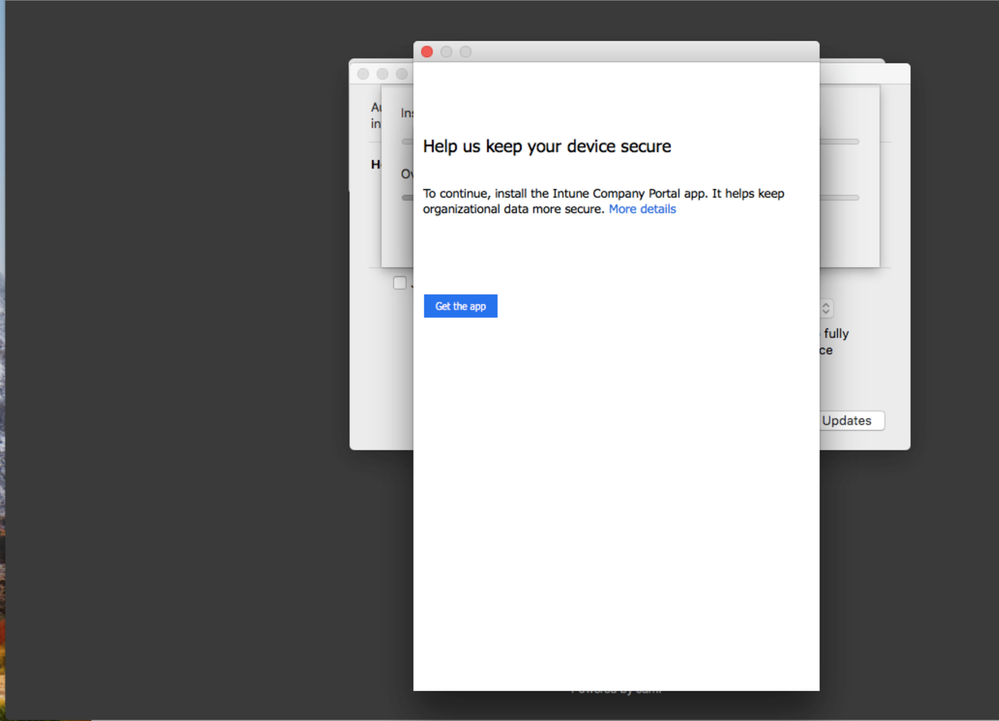
19. Click Get the app to install the Company Portal.
20. Click Done.
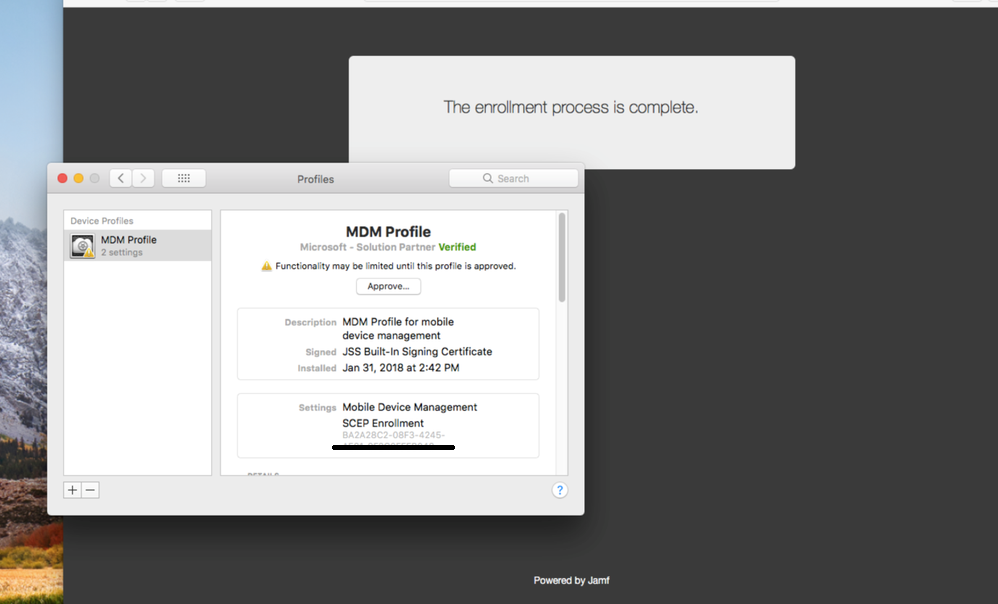
21. Approve the MDM profile.
22. Close out of these screens.
23. Click Done.
24. Enter your password and select “Always Allow”
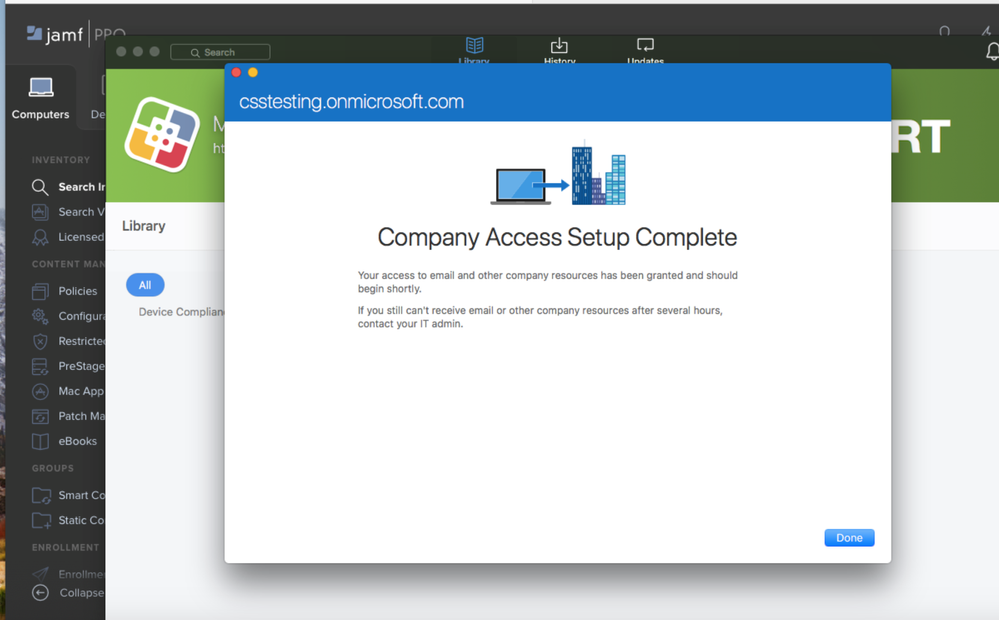
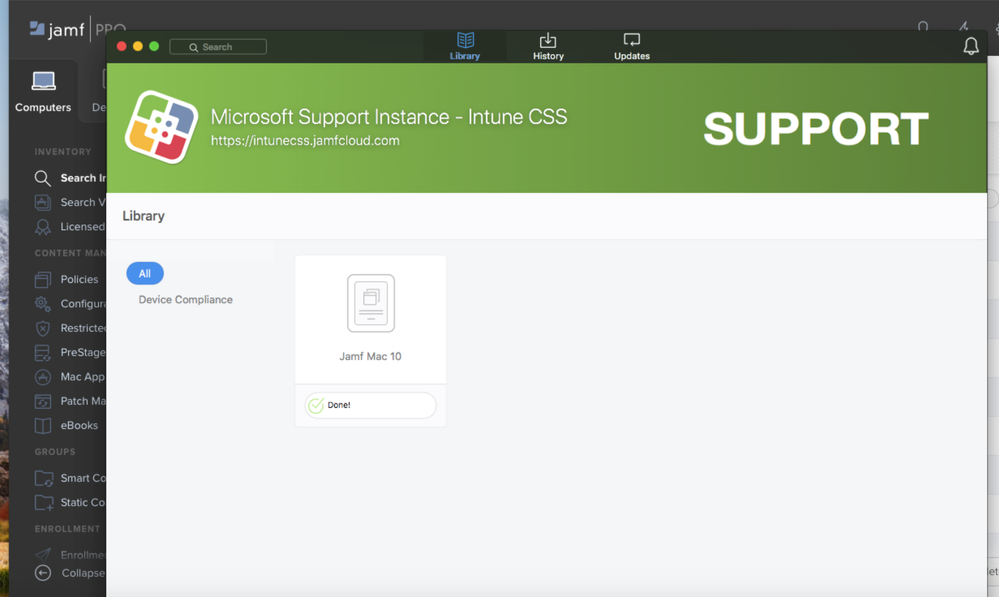
Congratulations! The device is now successfully managed by Jamf and registered with Intune.
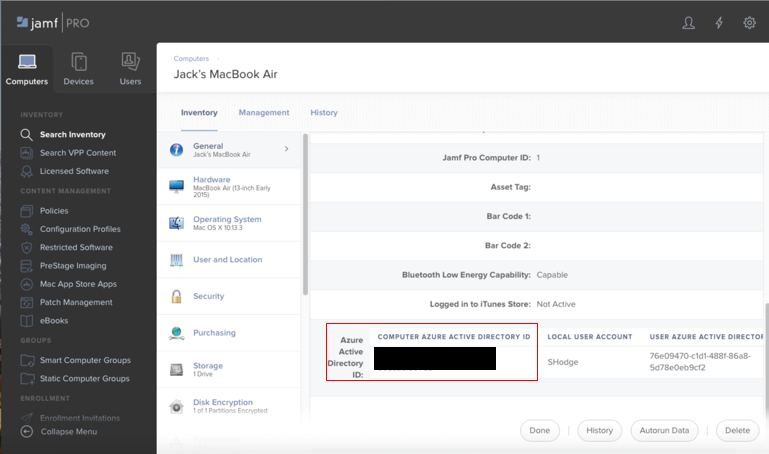
From the Jamf console, the device is enrolled into Jamf and registered with Intune. Note the computer’s Azure Active Directory ID.
Inventory information shared with Microsoft Intune
For a list of inventory attributes shared from Jamf to Microsoft Intune; click here.
Resources
- https://cloudblogs.microsoft.com/enterprisemobility/2017/12/14/microsoft-intune-and-jamf-pro-better-together-to-manage-and-secure-macs/
- https://docs.microsoft.com/en-us/intune/conditional-access-integrate-jamf
- https://www.jamf.com/resources/white-papers/conditional-access-going-beyond-perimeter-based-security/
- https://resources.jamf.com/documents/technical-papers/integrating-with-microsoft-intune-to-enforce-compliance-on-macs-managed-by-jamf-pro-10.1.0-or-later.pdf
- https://docs.microsoft.com/en-us/intune/conditional-access-assign-jamf
- https://www.jamf.com/products/jamf-pro/microsoft/
- http://docs.jamf.com/technical-papers/jamf-pro/microsoft-intune/10.9.0/Introduction.html