This blog was written as a collaboration between
As the severity and frequency of attacks rise, there is even more need for proactive threat hunting. This is becoming increasingly important as organizations seek to stay ahead of the latest cyber threats. Your systems and security appliances generate mountains of data that can be difficult to parse and filter into meaningful events.
Over the last several months, we’ve been able to help our customers use Azure Sentinel’s hunting capabilities to hunt down for signs of intrusions and stay on top of suspicious activities that went undetected by their security systems. These customers have cited measuring improvement in both the speed and accuracy of response, reduction in time for investigation and in attack surface exposure.
If you’re an investigator who wants to be proactive about looking for security threats, Azure Sentinel has powerful hunting search and query tools to hunt for security threats across your organization’s data sources. To help security analysts look proactively for new anomalies that weren’t detected by your security apps, Azure Sentinel’s built-in hunting queries guide you into asking the right questions to find issues in the data you already have on your network.
In this blog post, we will cover the tactical details of Azure Sentinel’s new Livestream hunting capability and how you can use this to help your SOC analysts proactively identify emerging threats.
What is Azure Sentinel Livestream?
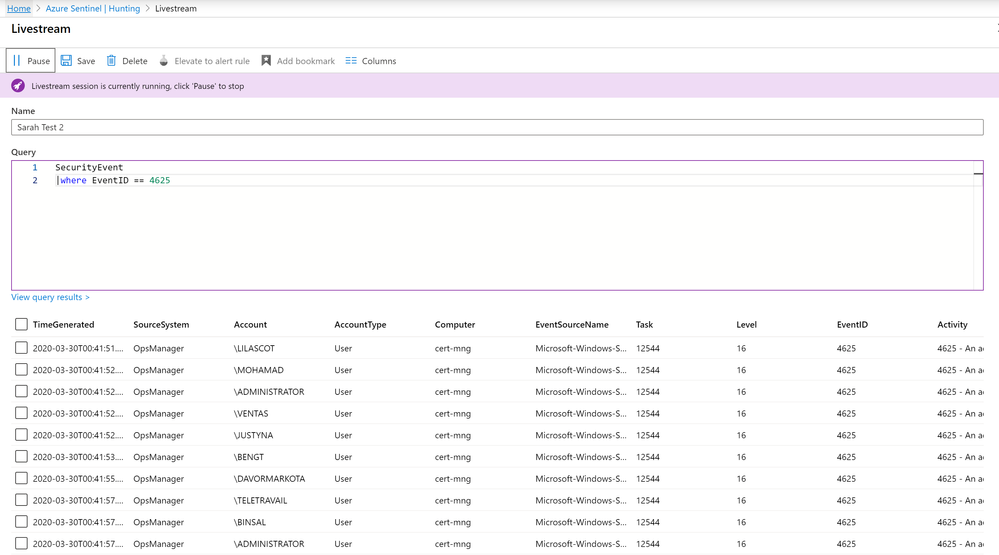
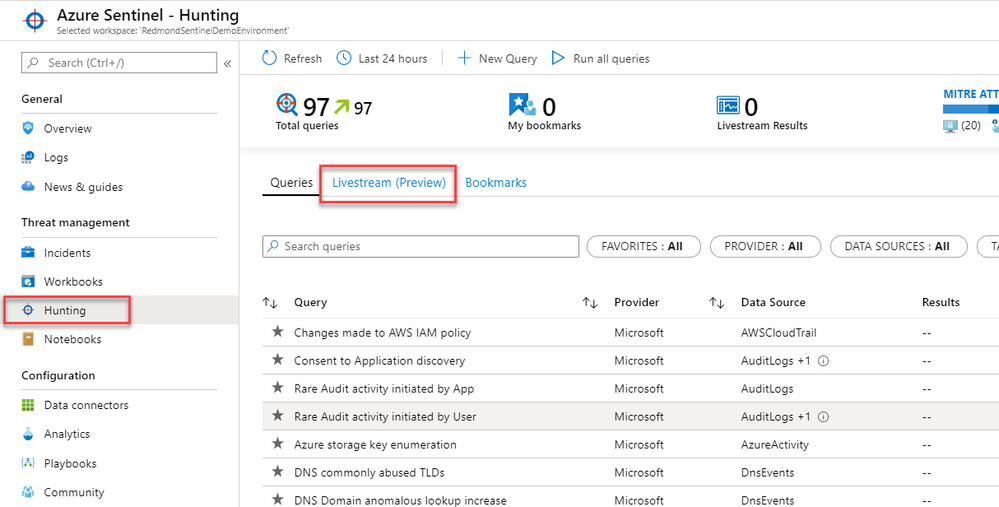
Azure Sentinel Livestream is a user session-based, user interface driven feature that allows an Azure Sentinel user to quickly create a Livestream session using a Log Analytics query. The Livestream query will run in the background and will notify you of any results obtained during the Livestream session. It can be found under the Hunting blade of Azure Sentinel, next to the Queries tab.
Firstly, let’s take a simple example to explain the concept:
The query we’re running is below:
SecurityEvent
|where EventID == 4625
In this query we’re asking Azure Sentinel to stream all Windows login events in this workspace where the event ID = 4625 (that’s for when an account fails to log on). As you can see, we’re getting a lot of events here, and they’re being updated every 30 seconds by the live stream.
In our demo environment we have lots of failed logins happening all the time to make interesting data for us to play around with; but if this were a real life production environment, we wouldn’t typically expect to see very many failed logins at all. However, failed logins can and do happen in production as per the course of normal events, and we certainly wouldn’t want to trigger a full incident every time a failed logon occurs as this would lead to incident overload and alert fatigue for your SOC analysts.
So, what’s the point of Livestream in Sentinel and how does it help us in proactively addressing threats in your environment? Using the example above, we know that some failed logon events are normal. However, Livestream can help you identify if these “normal” events suddenly increase in frequency: this is possibly an indicator that something is amiss in your environment. It’s for this reason that we have added an “Elevate to alert rule” button as part of Sentinel Livestream: if your SOC analysts detect there is a change in the threshold of your baseline environment activities as monitored by Livestream, they can use this button to upgrade the Livestream query to an alert rule, and thus it will start generating incidents to be allocated and can be dealt with as per your security incident response process.
Advanced Sentinel Livestream use cases
In the previous section, we took a straightforward query we could run as part of a Sentinel Livestream interactive session. Now let’s look at an example of a more advanced use case where Sentinel Livestream can help with proactive hunting.
Below is an alert rule that is comparing threat intelligence data feeds to aggregated log data and will notify you when a match occurs. Threat data feeds are ongoing streams of data that are related to potential or current threats, so the notification might indicate a potential threat to your organization. As in our earlier example, instead of creating a custom alert rule for this, you could create a Livestream session instead when you want to be notified of a potential issue. If required, you could elevate this to an alert rule.
let dt_lookBack = 1h;
let ioc_lookBack = 14d;
ThreatIntelligenceIndicator
| where TimeGenerated >= ago(ioc_lookBack) and ExpirationDateTime > now()
| where Active == true
| where isnotempty(FileName)
| join (
SecurityEvent | where TimeGenerated >= ago(dt_lookBack)
| where EventID in (“4688″,”8002″,”4648″,”4673”)
| where isnotempty(Process)
| extend SecurityEvent_TimeGenerated = TimeGenerated, Event = EventID
)
on $left.FileName == $right.Process
| summarize LatestIndicatorTime = arg_max(TimeGenerated, *) by IndicatorId
| project LatestIndicatorTime, Description, ActivityGroupNames, IndicatorId, ThreatType, ExpirationDateTime, ConfidenceScore,
SecurityEvent_TimeGenerated, FileName, Computer, IpAddress, Account, Event, Activity
| extend timestamp = SecurityEvent_TimeGenerated, AccountCustomEntity = Account, HostCustomEntity = Computer, IPCustomEntity = IpAddress
How do I create my own Sentinel Livestream?
There are two ways to create your own Sentinel Livestream. The first way is to elevate an existing hunting query by right clicking on that query and selecting “Add to Livestream.”
The second way to create a Livestream is to go to Hunting blade of Azure Sentinel and select the Livestream tab next to the Queries tab.
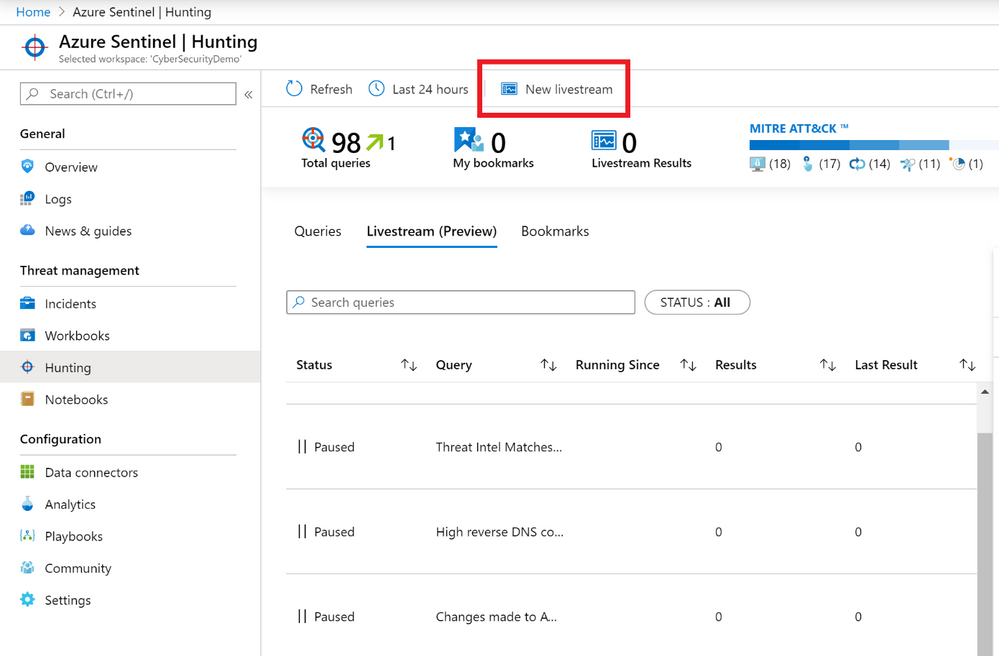
Select “New Livestream”.
Give your Livestream a name and enter your query. It’s important to remember that queries for Livestreaming cannot reference time periods due to the nature of the Livestream looking for query matches in real-time.
Save the query and select “Play” to start the Livestream running. You will see the results in the bottom half of the screen.
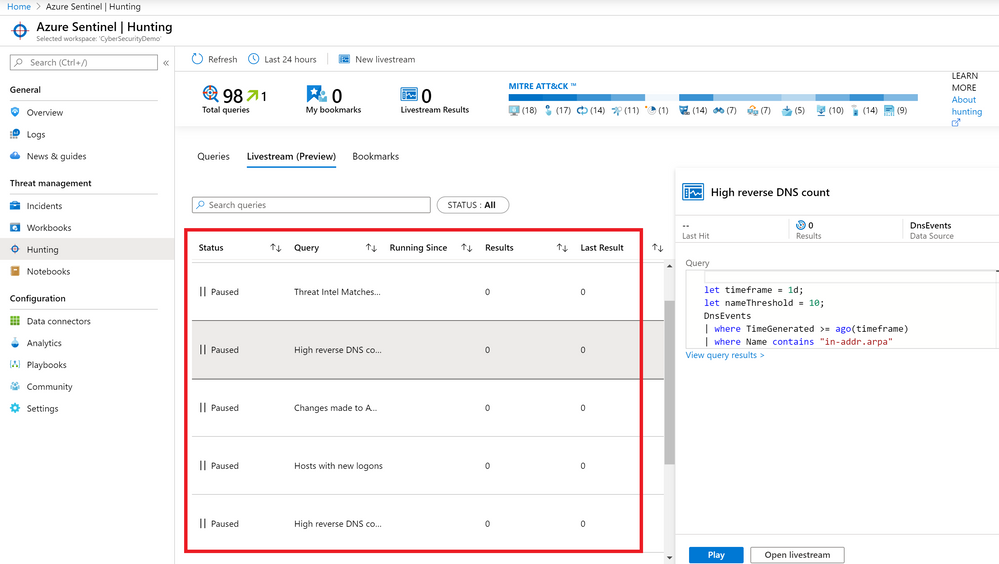
You can also check on the status of your Livestreams from the main Livestream tab in Sentinel: whether they are playing or paused, how many results the Livestream has generated and when the last result that the query in the Livestream matched was. Be mindful that when the user who initiated the Livestream running signs out of Azure, the Livestream will cease running.
Summary
Sentinel Livestream provides a powerful, flexible way to turn your hunting queries into an additional proactive monitoring tool to further enhance your security operations without the risk of increasing overhead on your SOC analysts. Try Sentinel Livestream in Public Preview today, let us know your thoughts and please share your hunting queries on our Github!