This post has been republished via RSS; it originally appeared at: Security, Privacy and Compliance Blog articles.
The Microsoft Threat Protection team has been working hard to make your advanced hunting experience even more straightforward, interesting, and productive. With app & identity signals, custom detections, and charts now available on preview, your proactive threat hunting activities have never been as comprehensive and effective. Turn on Microsoft Threat Protection and sign up for previews to can start enjoying these new experiences and let us know what you think.
Hunt across domains with identity and cloud app signals
While Microsoft Threat Protection automatically flags and remediates threats, advanced hunting lets you take your response a step further by enabling you to efficiently inspect benign events that in certain contexts can be indicative of breach activity. For several months now, in Microsoft 365 security center, SecOps staff for various organizations have started hunting for clues on endpoints after receiving suspicious emails. This has been made easy and convenient by endpoint data from Microsoft Defender ATP and email data from Office 365 ATP.
Today, we’re expanding that coverage to include data from Azure ATP and Microsoft Cloud App Security with the following new schema tables:
- IdentityQueryEvents — contains data about attempts to query identity information in Active Directory using LDAP and other protocols. These events are also tracked by Azure ATP to find reconnaissance activities, including activities meant to discover critical targets on your network.
- IdentityLogonEvents — contains authentication events from Active Directory as well as monitored cloud apps and services. Use this to surface suspicious logon activities, including repetitive attempts and the use of atypical logon methods.
- AppFileEvents — covers file-related activities involving apps monitored by Microsoft Cloud App Security. This gives you coverage over attempts to handle files that might contain sensitive information as well as malicious code.
See the full list of advanced hunting schema tables
Sample scenarios you can try
With these new data sets, you can hunt for activities that happen across the cybersecurity attack chain. Check out the sample scenarios below to explore what you can do with the expanded schema.
SAMR queries to Active Directory
With IdentityQueryEvents, you can now quickly find reconnaissance activities, such as processes performing suspicious SAMR queries against users and admins in your org.
IdentityQueryEvents
| where Timestamp > ago(7d)
| where ActionType == "SamrQuerySuccess" and isnotempty(AccountName)
| project QueryTime = Timestamp, DeviceName, AccountName, Query, QueryTarget
| join kind=inner (
DeviceProcessEvents
| where Timestamp > ago(7d)
| extend DeviceName = toupper(trim(@"\..*$",DeviceName))
| project ProcessCreationTime = Timestamp, DeviceName, AccountName, InitiatingProcessFileName,
InitiatingProcessCommandLine
) on DeviceName, AccountName
| where ProcessCreationTime - QueryTime between (-2m .. 2m)
| project QueryTime, DeviceName, AccountName, InitiatingProcessFileName,
InitiatingProcessCommandLine, Query, QueryTarget
LDAP authentication with cleartext passwords
With IdentityLogonEvents, you can identify possible lateral movement activities by searching for logon attempts using compromised accounts or logons over unprotected protocols, such cleartext authentications over LDAP.
This query identifies processes that have attempted to authenticate using a clear-text password, which are typically obtained using known credential theft methods.
IdentityLogonEvents
| where Timestamp > ago(7d)
| where LogonType == "LDAP cleartext" and isnotempty(AccountName)
| project LogonTime = Timestamp, DeviceName, AccountName, Application, LogonType
| join kind=inner (
DeviceNetworkEvents
| where Timestamp > ago(7d)
| where ActionType == "ConnectionSuccess"
| extend DeviceName = toupper(trim(@"\..*$",DeviceName))
| where RemotePort == "389"
| project NetworkConnectionTime = Timestamp, DeviceName,
AccountName = InitiatingProcessAccountName, InitiatingProcessFileName,
InitiatingProcessCommandLine
) on DeviceName, AccountName
| where LogonTime - NetworkConnectionTime between (-2m .. 2m)
| project Application, LogonType, LogonTime, DeviceName, AccountName,
InitiatingProcessFileName, InitiatingProcessCommandLine
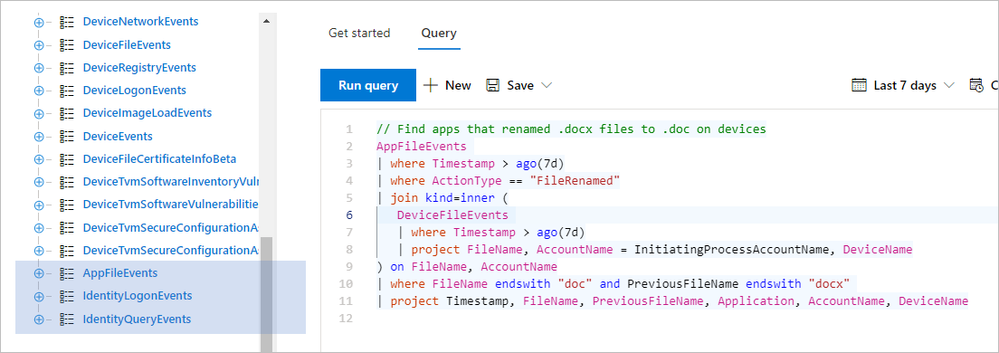
Renaming of .docx files to .doc
With AppFileEvents, you can hunt for attempts to move and stage malicious content using cloud apps. The following query locates attempts to rename .docx file to .doc, possibly to bypass protection mechanisms and allow malicious macros to run.
AppFileEvents
| where Timestamp > ago(7d)
| where ActionType == "FileRenamed"
| join kind=inner (
DeviceFileEvents
| where Timestamp > ago(7d)
| project FileName, AccountName = InitiatingProcessAccountName, DeviceName
) on FileName, AccountName
| where FileName endswith "doc" and PreviousFileName endswith "docx"
| project Timestamp, FileName, PreviousFileName, Application, AccountName, DeviceName
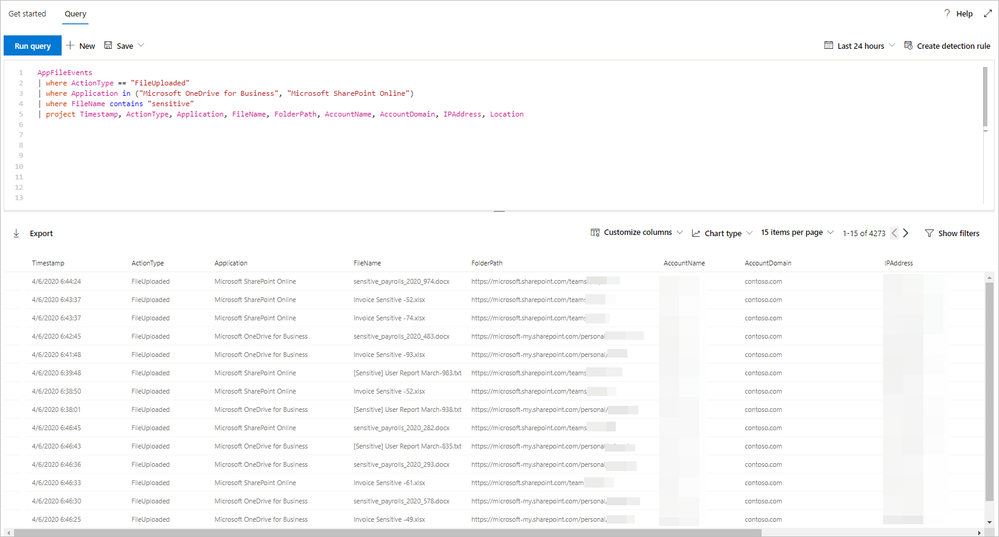
Sensitive file uploads
You can also use the AppFileEvents table to hunt for exfiltration scenarios by querying for attempts to upload sensitive files to cloud apps like SharePoint, OneDrive, or Dropbox. You can use data under SensitivityLabel in the DeviceFileEvents table to locate sensitive files. However, a simpler way would be look for a specific string in file names, like sensitive in the query below:
AppFileEvents
| where ActionType == "FileUploaded"
| where Application in ("Microsoft OneDrive for Business",
"Microsoft SharePoint Online", "Dropbox")
| where FileName contains "sensitive"
| project Timestamp, ActionType, Application, FileName, FolderPath, AccountUpn,
AccountName, AccountDomain, IPAddress, Location
| take 10
For more queries, check out the Microsoft Threat Protection query repository on GitHub.
Customize alerts and take automatic actions
Many of you might have already benefited from custom detection alerts driven by advanced hunting queries in Microsoft Defender ATP. To simplify your hunt and optimize your use of the expanded schema, we’ve delivered the same custom detection functionality to Microsoft Threat Protection.
Using advanced hunting queries, you can now automate your hunts so that you can effortlessly check fresh signals and raise alerts for new finds. Make sure you set your custom detection rules to take immediate response actions for you.
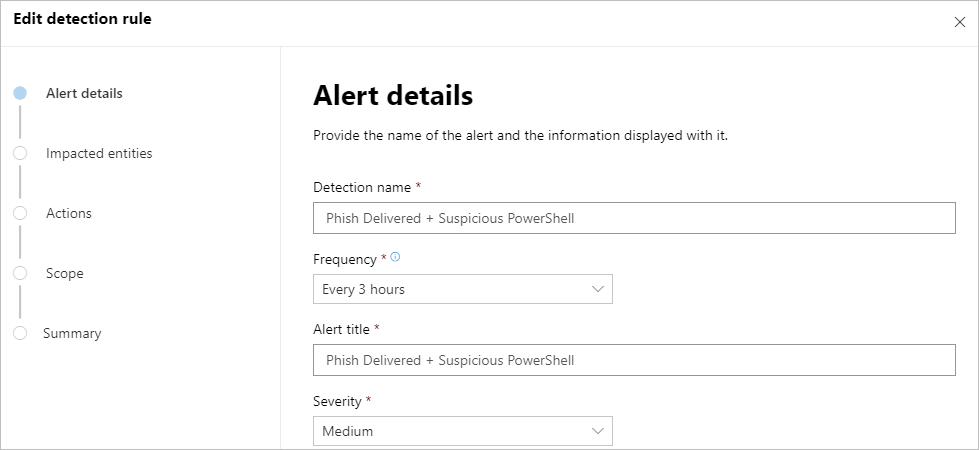
To create one, simply run a query—we used the last example above for sensitive file uploads. If you don’t have results, simulate the activity by uploading a file called sensitive.txt to OneDrive, SharePoint, or Dropbox.
After confirming that the query runs well and returns meaningful results, click Create detection rules and start customizing your detection rule.
Note: To create custom detection rules, you need to be a security administrator or a security operator. If you have Microsoft Defender ATP RBAC turned on, make sure you have the managed security settings permission.
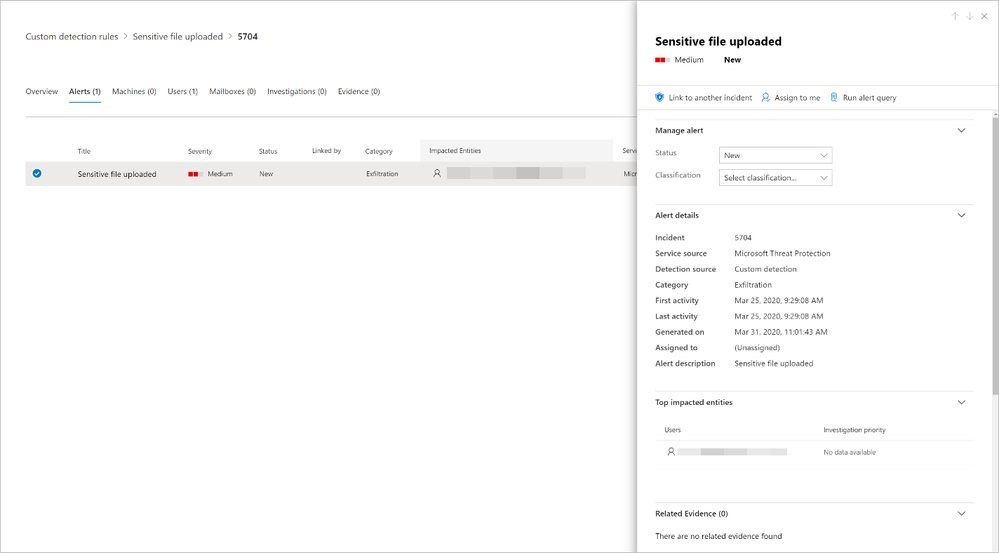
When identifying impacted entities, the user—identified by the AccountUpn column in this example—will work since the exfiltration event does not affect specific endpoints or mailboxes. Identifying the right impacted entities helps Microsoft Threat Protection aggregate relevant alerts, correlate incidents, and target response actions.
When you save your custom detection, it will run immediately and then run again based on your preferred interval. To check for alerts, head over to the Hunting > Custom detections > [Rule name] and open the Triggered alerts tab.
Learn more about creating custom detection rules
Visualize query results
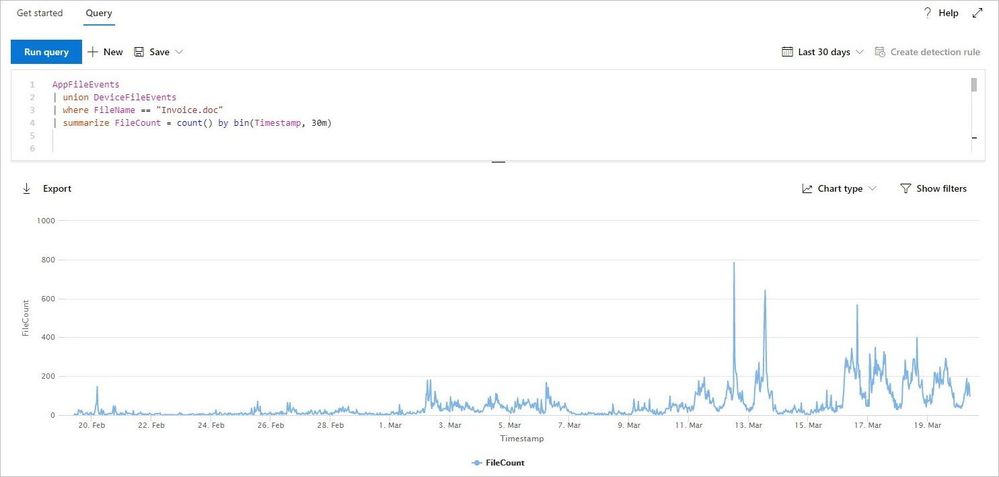
To help you extract insights from your queries and add some color to your work, we’ve added an option to view query results as a chart. Now available to all customers, the chart options currently include line, column, pie, scatter, and many other chart types. After running your query, select the right chart type that matches your data.
The line chart shown below highlights spikes in activity involving a specific file. Learn how to optimize queries to render effective charts
We hope you enjoyed learning about these new hunting experiences. Don’t forget to let us know what you think!
Stay safe and happy hunting!
- Microsoft Threat Protection Team