Special thanks to Nicholas DiCola for collaborating on the solution!
In this blog you will learn how to bring guided remediation steps into Azure Sentinel (from Azure Defender and Microsoft Defender for Endpoint) to enhance the security posture of your organization and stop attacks.
Background
Once an investigation is underway in Sentinel, SOC Analysts are then tasked with responding to true threats and preventing malicious activity from further occurring. With Sentinel’s Incidents, SOC’s have a collection of entities, events, and alerts to analyze and determine what resources need further security or remediation.
With this playbook, Azure Sentinel users that have Microsoft Defender for Endpoint or Azure Defender will experience a tighter integration of their best security tools within Azure Sentinel.
Rather than having to jump from portal to portal, this playbook identifies recommended steps to resolve a potentially malicious or suspicious event and surfaces this guidance in the form of a comment on the related Sentinel incident.
Ready, Set, Go
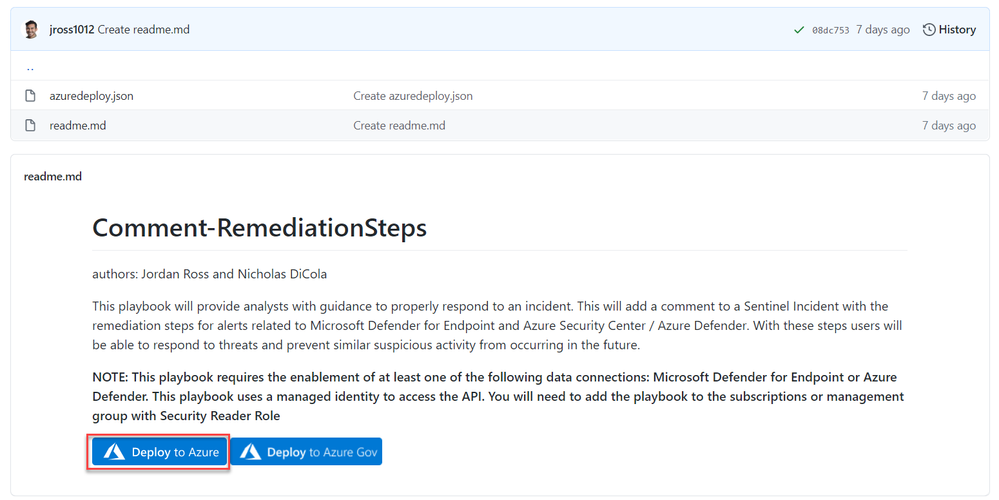
1. To get started, deploy the playbook to Azure using the GitHub artifact using this link: Remediation Steps Playbook
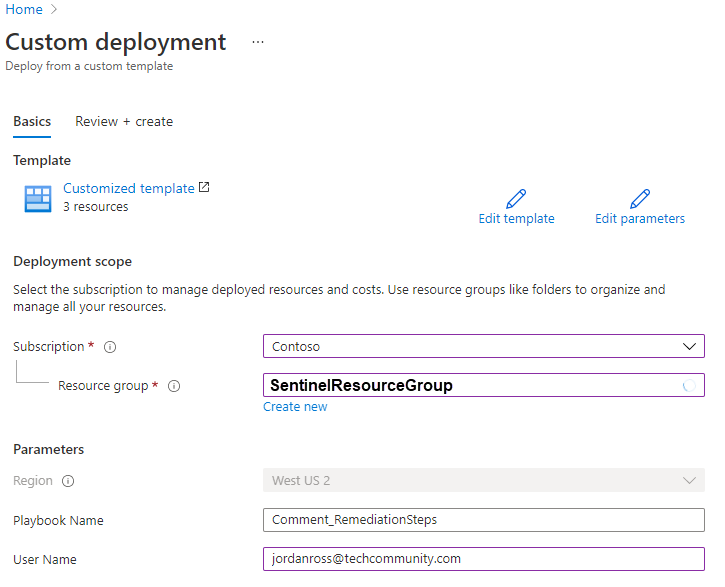
2. After you have deployed the playbook from the Sentinel GitHub and add it to your Sentinel related resource group.
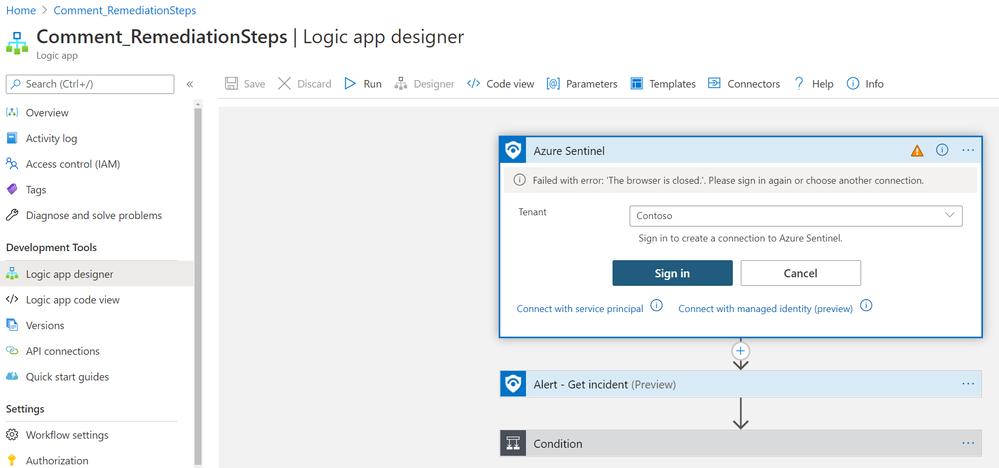
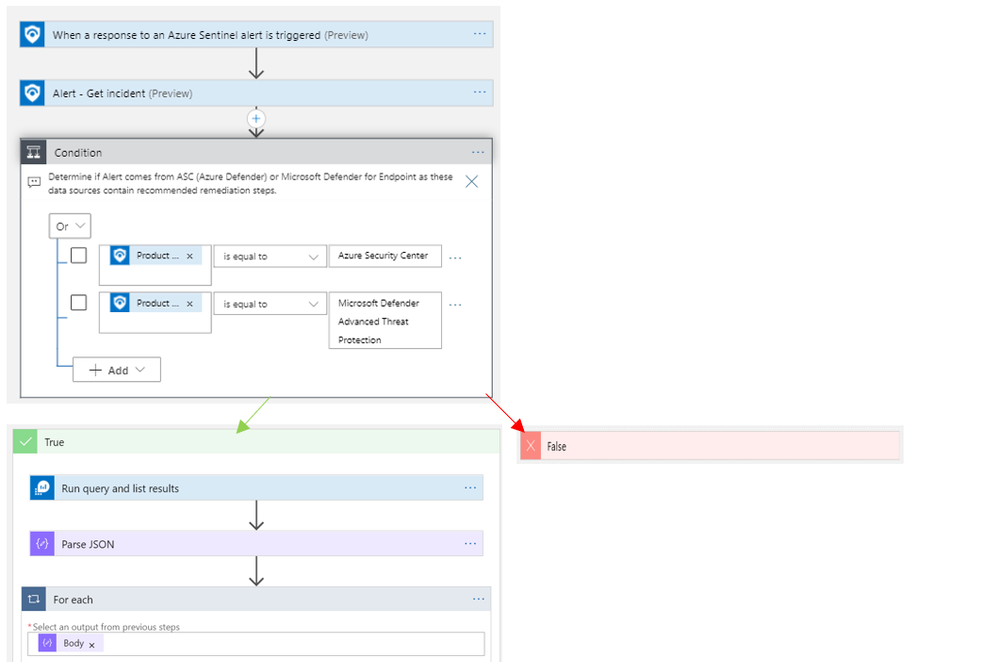
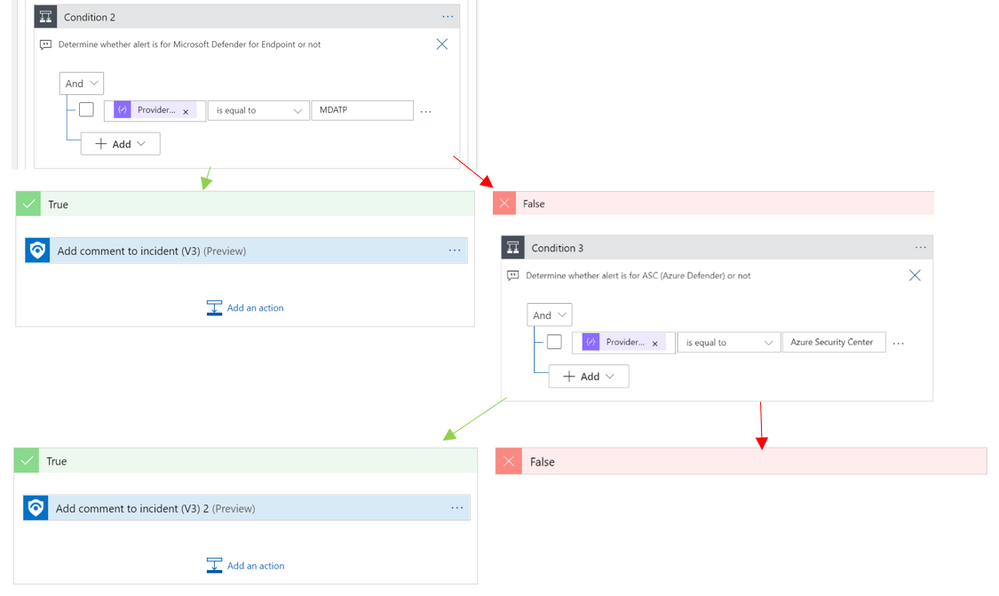
3. Once the playbook has successfully deployed, navigate to the playbook’s (‘Comment_RemediationSteps’) Logic App Designer. Once in the designer, be sure to enable the connections to Azure Monitor and Sentinel. This is as simple as selecting the connection in the Logic App designer and clicking ‘Add new’ to establish your new connection as seen below:
(Note: there are three areas in the logic app where a connection to an identity or service principal is required. This is needed at the trigger “When a response to an Azure Sentinel alert is triggered”, and the two actions: “Alert – Get incident” and “Run query and list results”)
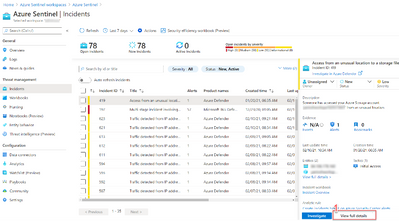
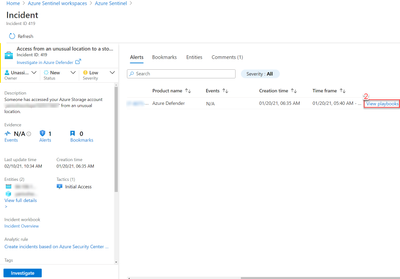
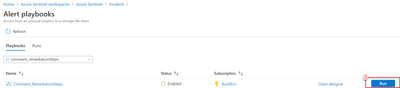
4. Once the connections have been made, hit save and you are all set to use the playbook to provide guided remediation steps to you analysts. This playbook runs off a manual trigger, so when an analyst finds an incident related to Azure Defender or Microsoft Defender for Endpoint, all the analyst needs to do is open the incident -> click ‘View Full Details’ -> Under the ‘Alerts’ tab click ‘View Playbooks’ -> and click ‘Run’ on ‘Comment_RemediationSteps’as seen in the visuals below:
a. View Full Details
b. View playbooks
c. Run playbook
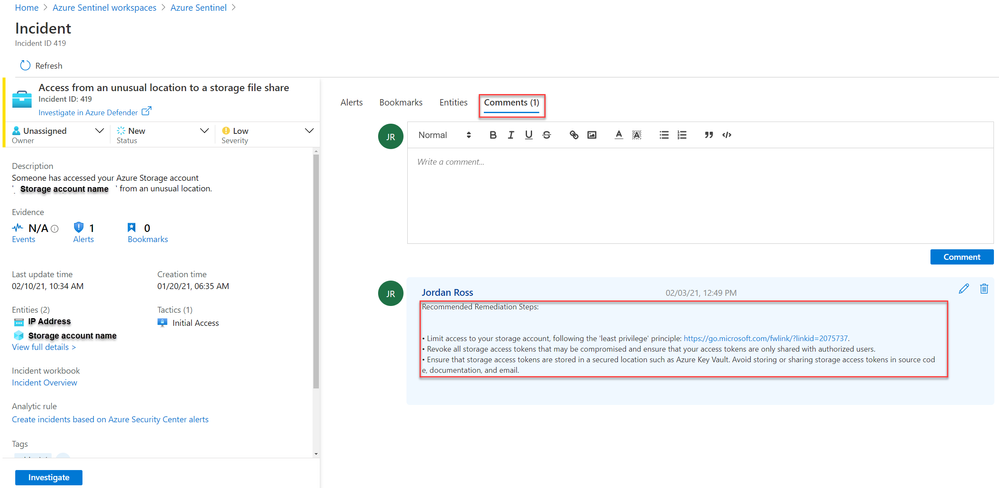
5. Once the playbook “Comment_RemediationSteps” has been run, return to the related incident’s ‘comments’ tab and you will find that the remediation steps have been posted as seen below:
Using these steps an analyst can ensure that an attack does not progress, and that the organization’s security posture has been improved to prevent future intrusions.
Related Content:
How Azure Sentinel and Azure Security Center Work Together – YouTube
Connect Microsoft Defender for Endpoint data to Azure Sentinel | Microsoft Docs
Connect Azure Defender data to Azure Sentinel | Microsoft Docs
Tutorial: Run a playbook in Azure Sentinel | Microsoft Docs
Overview of the Logic App: