Azure key vaults safeguard cryptographic encryption keys, certificates, and other secrets like connections strings and passwords used by cloud apps and services. Securing key vaults, is therefore, of utmost importance. Azure Defender for Key Vault monitors key vault activity and alerts when suspicious and malicious behavior is observed.
Now you can get further insights and visibility on your key vault activity using the new Azure Key Vault Workbook in Sentinel. The workbook allows you to visualize alerts from Azure Defender and monitor its coverage across your Sentinel workspaces. In addition, it provides security insights from the activity logs. These insights include baselines for key vault access and anomalous deviations from them, as well as event and operation analysis over time. The analysis allows you to inspect failed events, caller IPs, active users & services, as well as their operations. You can further investigate notable and suspicious entities and their activities using the direct links provided in the workbook to relevant incidents involving these entities.
We recommend checking this workbook on a periodic basis, in which you can check anomalous behavior on your key vaults and drilling down to validate that the behavior is legitimate or not. In addition, we recommend checking the workbook when you see a key vault being involved in an incident. In such a case, we recommend filtering the workbook on the specific key vault to create an understanding on its usage and the actions on it.
Configuration
To get full benefit of the workbook, enable audit events in the diagnostic settings of the key vault and make sure that Azure Defender alerts are ingested in Azure Sentinel.
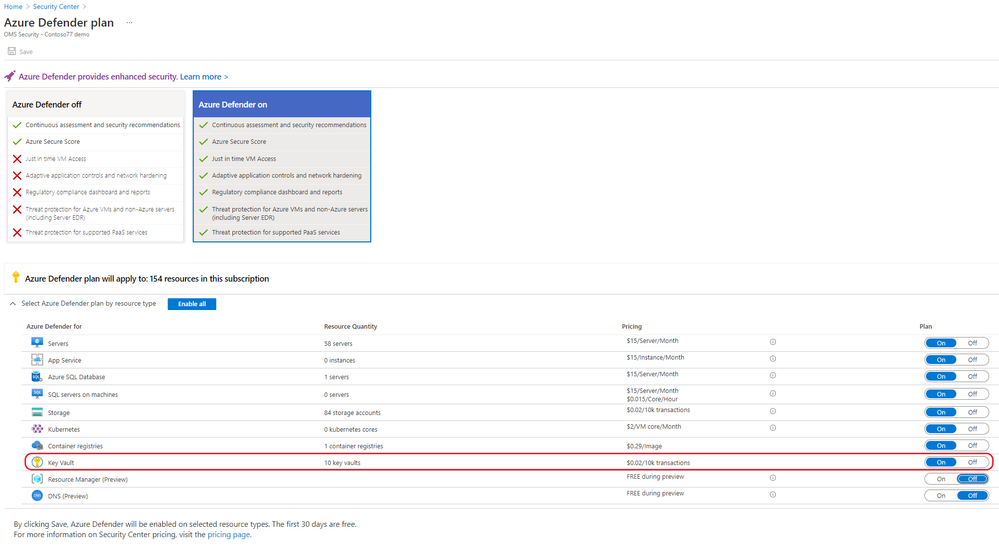
To enable Azure Defender for Key Vault, go to Azure Security Center –> Pricing & Settings –> Select the relevant subscription and make sure that key vault plan is enabled:
To ingest the security alerts to Sentinel, go to Sentinel –> Data connectors –> Azure Defender
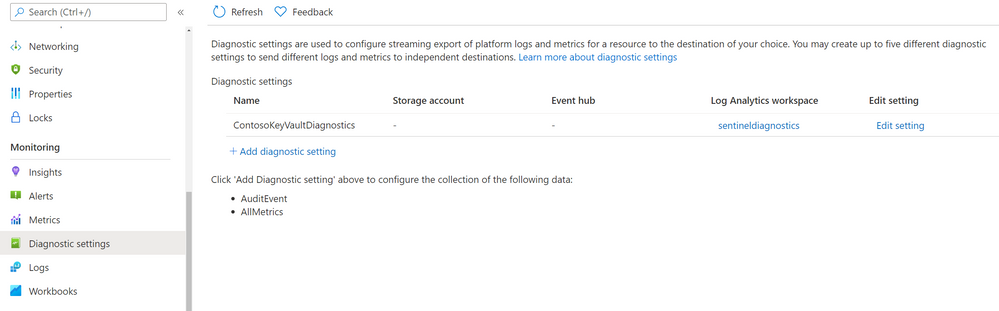
To enable Diagnostic logs for Key Vaults, go to your key vault –> Diagnostic setting –> Add diagnostic setting –> select AuditEvent log and Send to Log Analytics workspace
Once the diagnostic logs are injected in the workspace, you can see the data in the AzureDiagnostics table.
The workbook leverages this data as well as the SecurityAlert table.
Usage
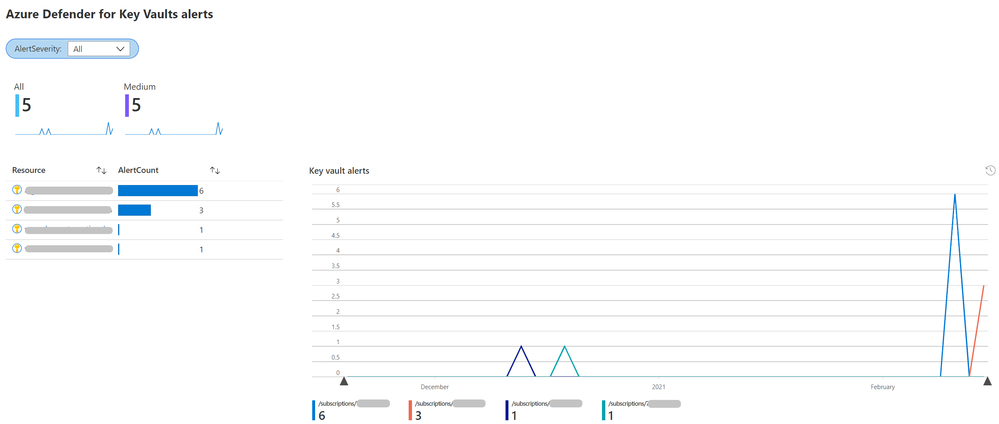
The workbook comprises three main tabs: Azure Defender for Key Vault alerts, Analytics over Key Vault events, and Key Vault activity monitoring. In the first tab, you can see the coverage of Azure Defender on your chosen subscriptions and key vaults, as well as onboard subscriptions to Azure Defender.
Following, you can see the Azure Defender alerts, their distribution over the various key vaults, and the details of each alert. These details include a link to the alert page in Azure Security Center and a link to the Incident page in Sentinel, from which you can initiate an investigation. In addition, for each alert you can see a graph of all entities involved in the alert.
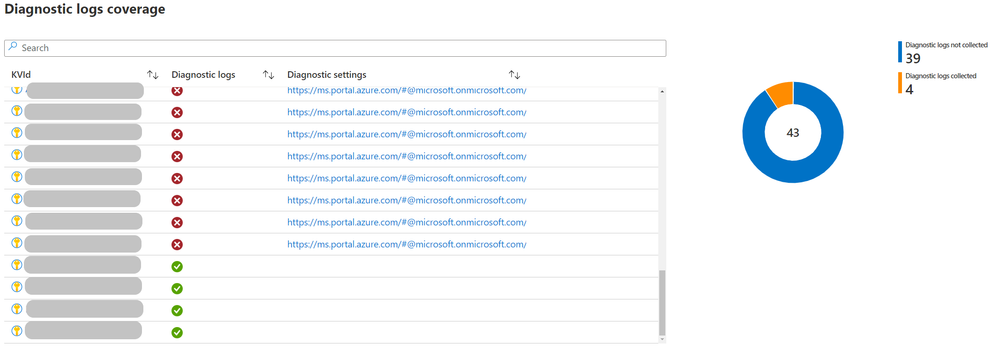
On the second tab, you can see the analytics of the key vault activities, starting with the coverage to diagnostic logs reporting for the selected key vaults and onboarding those that do not log activity to log analytics.
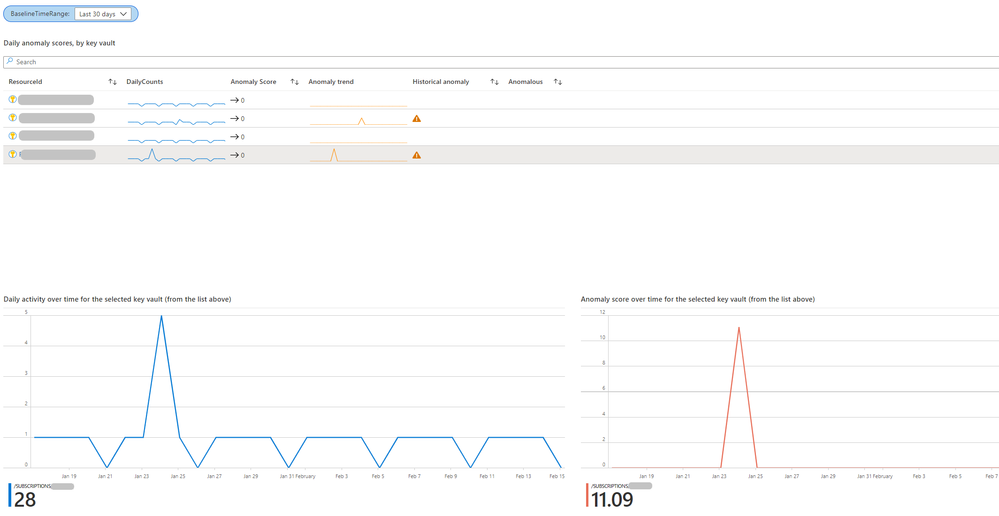
Following on, you can see baselines of activity volume on each key vault and an anomaly score based on time series anomaly detection.
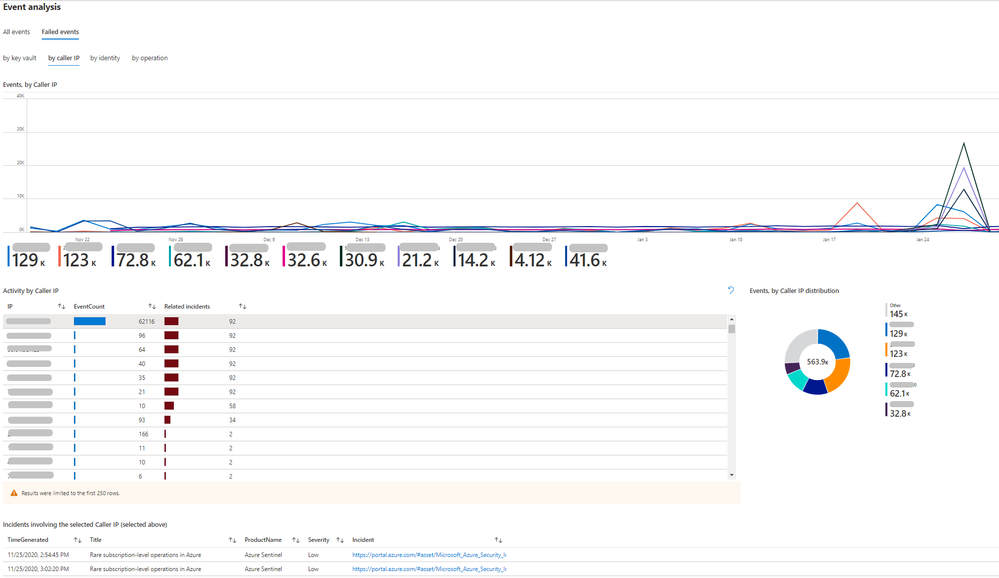
Further in event analysis, you can inspect notable events and their distribution based on key vault, caller IP, user/service identity, and operation type. For each such entity, you can also find all other incidents that were triggered and are related to it. Each such incident can then be investigated by clicking on its link and navigating to the incident page.
Additionally, you can hunt for sensitive operations, e.g., delete, purge, and backup operations:
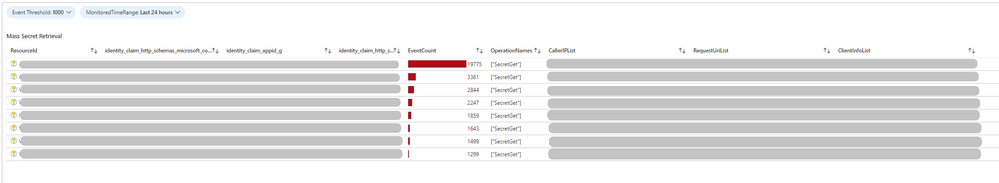
As well as look for mass secret dumps based on a threshold and monitoring period of your choice:
In addition, you can inspect the operations on key vaults and monitor their relations for spikes and other suspicious behaviors in the operation analysis section. You can inspect the type of activity performed on a key vault or a set of key vaults over time. You can choose to look at either secret, key, or certificate operations, as well as filter on users or services performing the activity.
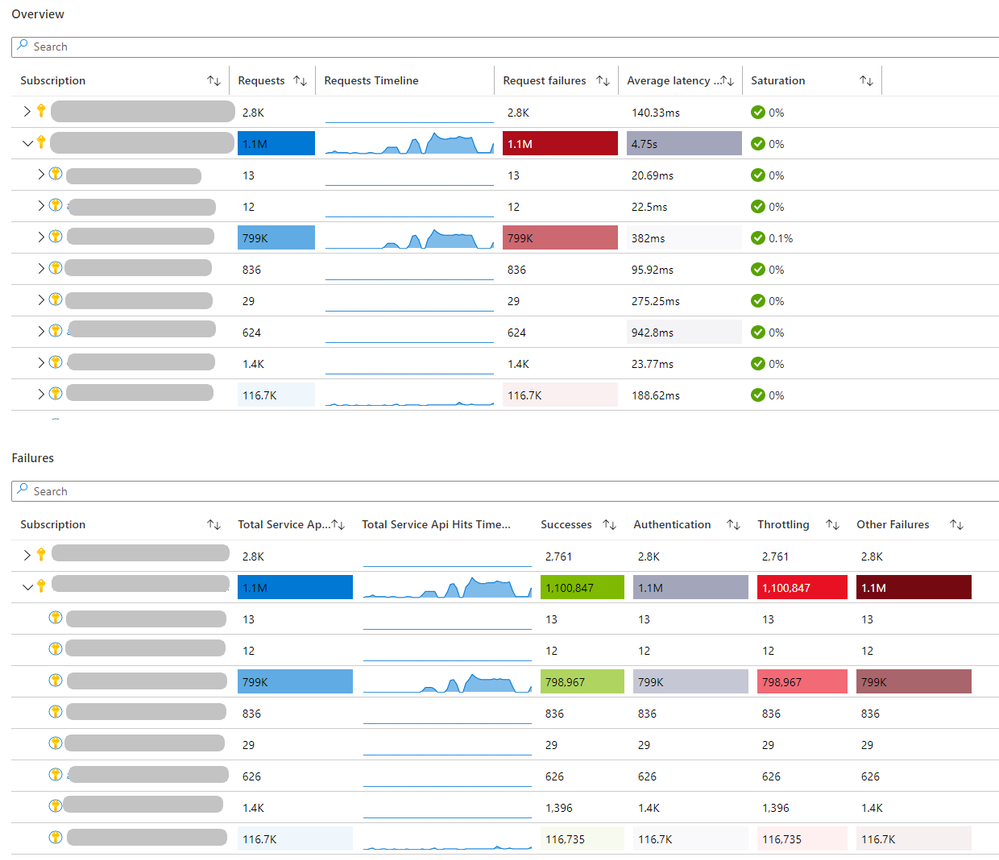
On the third tab you can inspect the monitoring metrics that can be found in the Azure Monitor for Key Vault workbook:
The workbook was developed with the assistance of: Lior Arviv, Hesham Saad, Yaniv Shasha, and Yossi Weizman.