This post has been republished via RSS; it originally appeared at: Core Infrastructure and Security Blog articles.
Dear IT Pros,
Today we discuss about MBAM's Bitlocker data migration to MEM
Microsoft provides a range of flexible BitLocker management alternatives to meet organization’s needs, as follows:
- Cloud-based BitLocker management using Microsoft Endpoint Manager.
- On-premises BitLocker management using System Center Configuration Manager
- Microsoft BitLocker Administration and Monitoring (MBAM) ended support on 7/9/2019, extended support 4/14/2026.
In order to future proof the Bitlocker Management and simplify the administration, some corporates have planned to migrate MBAM data directly from MBAM servers to Microsoft Endpoint Manager. The key point of the migration is that, making sure the amount of the recovery key IDs listed by MBAM Server are the same as the ones listed by Azure AD before the cut-off point of time in the migration process. I would suggest the a migration process with 5 steps.
Migration steps:
- Generate a list of Bitlocker recovery keys in MBAM SQL Server
- Setup MEM Policy to escrow Bitlocker recovery passwords to Azure AD Device Accounts.
- Generate a list of Bitlocker recovery keys by Graph API in Azure AD, also generate a list of devices failed to escrow their keys
- Compare list and make manually escrow of recovery keys to Azure AD
- Shutdown MBAM Server and decommission them.
Now we would look into the detail steps.
1. Generate a list of Bitlocker recovery keys in MBAM SQL Server:
- To backup the recovery keys by SQL:
Open the SQL Management Studio, and Expand the MBAM_Recovery_and_Hardware database. - Under Tables, Select RecoveryAndHardwareCore.Keys.
- Right-Click RecoveryAndHardwareCore.Keys, and Select Top 1000 Rows.
- This should create a query that will give you a list of all RevoveryKeyID’s and RecoveryKey’s in the Database.
You could modify the above query for more rows with SELECT TOP nnnnn instead of 1000 (rows)
2. Setup MEM Policy to escrow Bitlocker recovery passwords to Azure AD Device Accounts.
2.1 Make 2 device groups: Bitlocker GPO devices and Bitlocker MEM devices
During the transition period, you will migrating batch by batch the devices from the “Bitlocker GPO devices group” to the “Bitlocker MEM devices group”.
2.2 Manage BitLocker using Microsoft Endpoint Manager – Intune
In Microsoft Endpoint Manager admin center.
- Select Endpoint security > Disk encryption, and then
- Create policy. Enter in the Platform and Profile indicated in the screen capture below, and then select Create.
creating a new Microsoft BitLocker policy in Microsoft Endpoint Manager
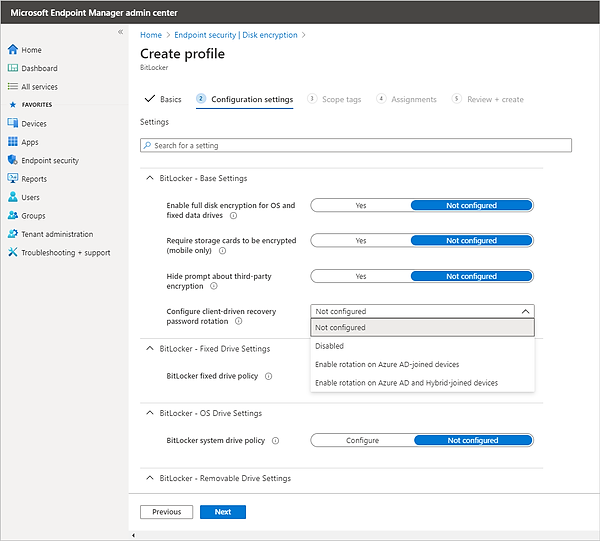
- Next, enter the basics, such as the name of the policy and an optional description, then move on to Configuration settings. Notice you can search for a specific setting, like “fixed drive policy,” or you can scroll through the settings. Also notice the options offered for key rotation. This setting, which requires Windows 10, version 1909 or later, will change the recovery key when the recovery key is used to unlock a drive.
Create an Endpoint Security profile in Microsoft Endpoint Manager
- As you enable settings, additional settings may appear. For example, Enabling Fixed drive encryption expands more options: Recovery key file creation and Configure BitLocker recovery key package.
Configuring BitLocker settings in Microsoft Endpoint Manager
- Finally, add Scope tags, assign the new policy to the “Bitlocker MEM devices” group, and select Create.
The settings that can be configured here include:
- BitLocker – Base Settings
- Enable full disk encryption for OS and fixed data drives
- Require storage cards to be encrypted (mobile only)
- Hide Prompt about third-party encryption
- Configure client-driven recovery password rotation
- BitLocker – Fixed Drive Settings
- BitLocker fixed drive policy
- BitLocker – OS Drive Settings
- BitLocker system drive policy
- BitLocker – Removable Drive Settings
- BitLocker removable drive settings
2.2 For End Users To get the Bitlocker Recovery Key
Option 1, Using the Azure Management Portal
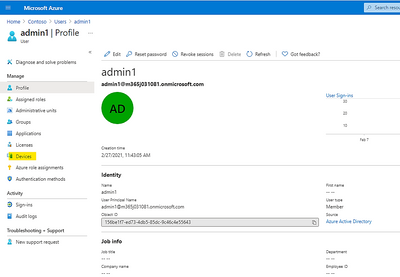
- Open the Azure AD resource object in the Management Portal
- Go to the All Users object and search for the account associated to the device.
- Click the user object name to view the profile properties.
Go to the Devices object under the Manage heading.
- Select the appropriate listed device.
If the device is registered with Bitlocker encryption, then the Bitlocker Key ID and Recovery Key will be visible.
- Click the Copy to Clipboard button and paste the data to view the entire string.
Option 2, Using the Microsoft Endpoint Manager Admin Center Portal
- Open the admin center https://endpoint.microsoft.com
- Go the Devices blade
- Search for the appropriate target device
- In the “Monitor” section, find and click on “Recovery keys”
Click the Copy to Clipboard button and paste the data to view the entire string.
Option 3, Using the Company Portal website to get MacOS Recovery Key:
- Sign into the Intune Company Portal website from any device.
- In the portal, go to Devices and select the macOS device that is encrypted with FileVault.
- Select Get recovery key. The current recovery key is displayed.
On an iPhone, you must select the three dots before the Get recovery key option appears.
2.3 Force current MBAM devices to backup recovery password keys to MEM by script
From Endpoint Manager Portal, you could deploy to all Windows 10 devices the script to force current MBAM Clients to backup their recovery password keys to Azure AD. You could use the Github's powershell script provided by Michael Mardahl as per the "How to migrate Bitlocker to Azure AD" article
3. Generate a list of Bitlocker recovery key IDs by Graph API in Azure AD
3.1 Export list of recovery keys from Azure AD
- The BitLocker Recovery Keys are stored in Azure AD, and there is Graph API (beta) to export the whole recovery key IDs by Graph Explorer
|
Method |
Return type |
Description |
|
bitlockerRecoveryKey collection |
Get a list of the bitlockerRecoveryKey objects and their properties. |
|
|
Retrieve the properties and relationships of a bitlockerRecoveryKey object. Note: The key property is not returned by default. |
Prerequisite for Bitlocker Graph API
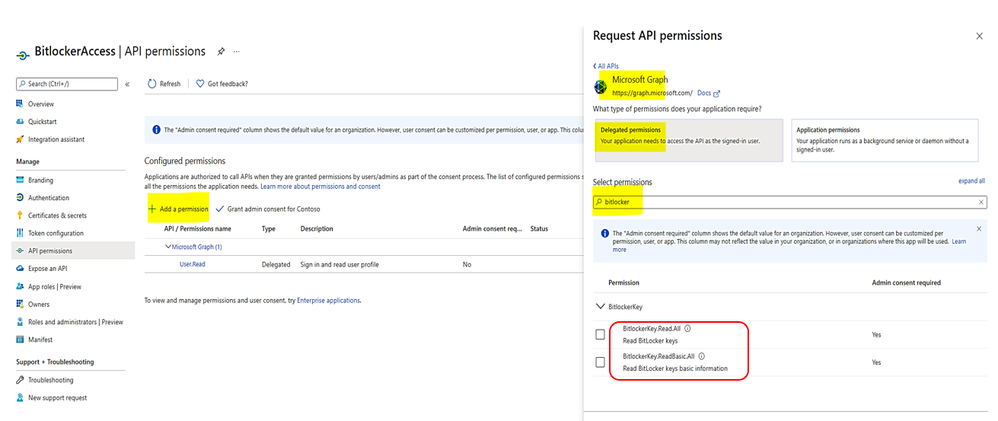
a. Register an App API in Azure AD. Example of an bitlocker client app created
> App Registration > New registration, Create, …
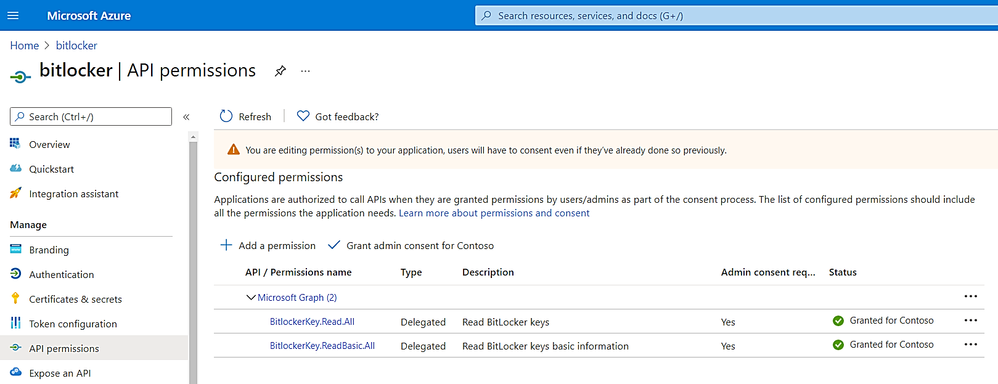
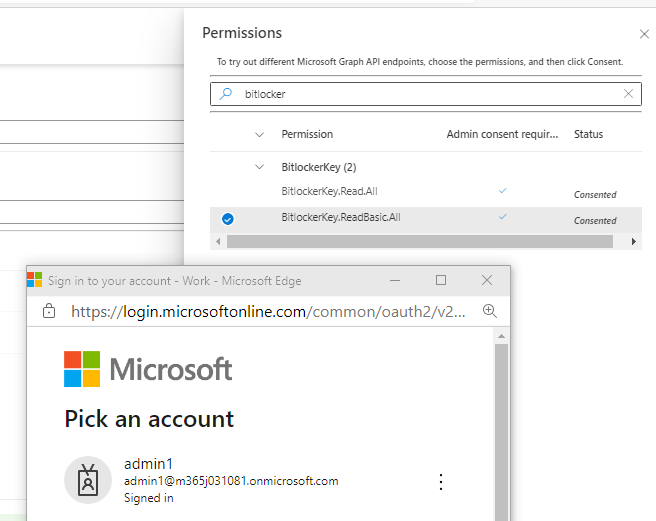
b. Assign permission: Read all or Read basic of bitlocker data:
c. Delegate permission for App to receive BitLockerRecoveryKey data on behalf of the signed-in User and grant admin consent:
d. Signed-in User needed to be assigned one of the following roles:
Global administrator
Cloud device administrator
Helpdesk administrator
Intune service administrator
Security administrator
Security reader
Global reader
3.2 Steps to get Bitlocker Recovery Password List
- Sign into Graph Explorer as Global Admin or Intune Admin,
Graph Explorer - Microsoft Graph
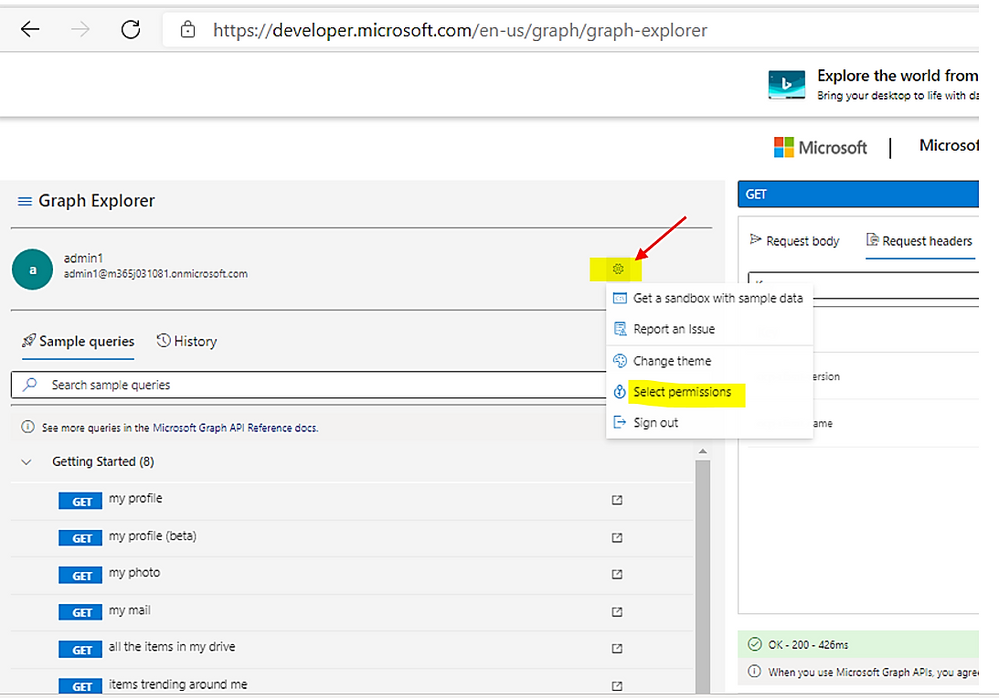
> Choose the permission to read Bitlocker ‘s properties as shown here:
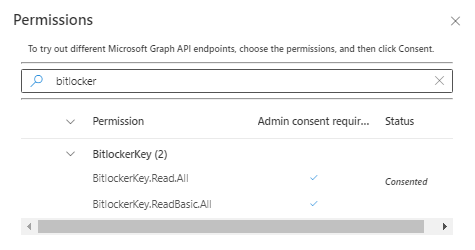
> In the search box: typing bitlocker to search for bitlocker permissions
> Choose the permission to read Bitlocker ‘s properties as shown here:
> Sign-in,
> Check the box “Consent on behalf of your Organization”
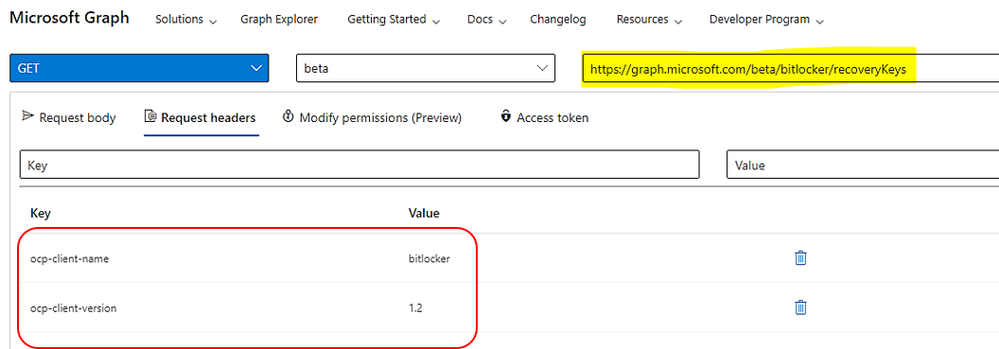
> Make Query with the HTTP Graph beta and Header as shown here:
GET, V1.0, https://graph.microsoft.com/beta/bitlocker/recoverykeys
Request headers: Adding the keys
Ocp-client-name: anything (you could use your application API name registered in Azure AD
Ocp-client-version: 1
> Run Query
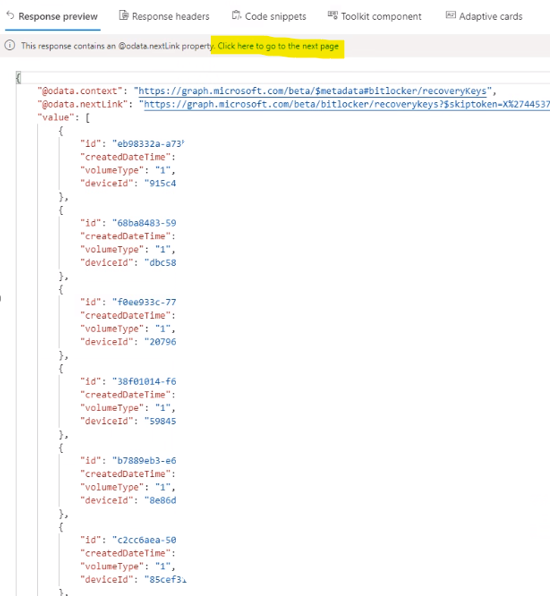
- The current list of JSON is limited to 999 items.
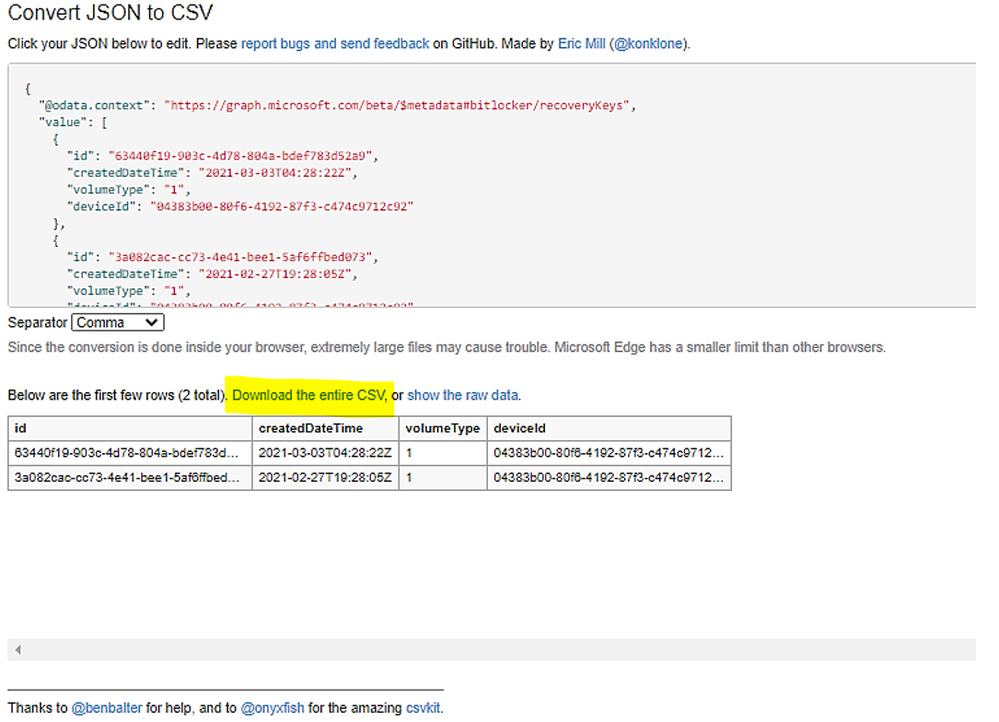
- Copy the JSON list and make a csv file from the query result by convert tool, the tool could be a PowerShell converter or your trusted online, converting JSON to csv Website. Please consider to use the online tool at your own risk.
- Result shown only 7 records per page, you may want to click on next page to view the next 7 records
- To export more than 1000 items, you could use the Github' script provided by Nickolaj Anderson as described in the "Get Intune Managed Devices without an escrowed bitlocker recovery key using PowerShell"
-
An Example of converting JSON to CSV file:
3.3 To monitor the status of Bitlocker device:
The Microsoft Intune encryption report is a centralized location to view details about a device's encryption status and find options to manage device recovery keys. The recovery key options that are available depend on the type of device you're viewing.
- To find the report, Sign in to the Microsoft Endpoint Manager admin center.
> Select Devices
> Monitor, and then
> under Configuration, select Encryption report.
- To View encryption details
The encryption report shows common details across the supported devices you manage. The following sections provide more details about the information that MEM presents in the report.
|
Encryption readiness |
Ready: The device can be encrypted by using MDM policy, which requires MacOS10.13 or later, Windows with TPM and Enterprise version 1709 or Pro 1809 |
|
Not ready |
The device doesn't have full encryption capabilities, but may still support encryption. |
|
Not applicable |
There isn't enough information to classify this device. |
|
Encryption status |
Whether the OS drive is encrypted |
|
… |
… |
When you select a device from the Encryption report, MEM displays the Device encryption status pane with the following detail:
A list of the Device configuration profiles that apply to this device·
- macOS: Profile type = Endpoint protectiono Settings > FileVault > FileVault = Enable·
- Windows 10: Profile type = Endpoint protectiono Settings > Windows Encryption > Encrypt devices = Require
|
Encryption readiness |
TPM status is ready for bitlocker encryption or not (the device can still be manually encrypted. or through a MDM/Group Policy setting that can be set to allow encrypting without a TPM.) |
|
Encryption status |
Whether the OS drive is encrypted. It can take up to 24 hours for MEM to report For Windows devices, this field does not look at whether other drives, such as fixed drives, are encrypted |
|
Profiles |
|
|
Status details |
This field displays information for each applicable error that can be detected. You can use this information to understand why a device might not be encryption ready: MacOS: · The recovery key hasn't been retrieved and stored yet, · The user is deferring encryption or is currently in the process of encryption. · The device is already encrypted. Device user must decrypt the device to continue. · FileVault needs the user to approve their management profile in macOS Catalina and higher. · Unknown Windows: · The BitLocker policy requires user consent to launch the BitLocker Drive Encryption Wizard on the OS volume. · The encryption method of the OS volume doesn't match the BitLocker policy. · The policy BitLocker requires a TPM protector, or PIN, or Startup Key. · Recovery key backup failed. · A fixed drive is unprotected. · The encryption method of the fixed drive doesn't match the BitLocker policy. · To encrypt drives, the BitLocker policy requires either the user to sign in as an Administrator or, if the device is joined to Azure AD, the AllowStandardUserEncryption policy must be set to 1. · Windows Recovery Environment (WinRE) isn't configured. · The TPM isn't ready for BitLocker. · The network isn't available. |
3.4 To view list of Unencrypted devices:
We need to know if the Devices ever backup the recovery keys to Azure AD. Jos Lieben provided the script to generate a report about the devices who have not been escrowed the bitlocker recovery key to Azure AD.
Download the Get-bitlockerEscrowStatusForAzureADDevices.ps1script from Github
4. Compare between lists and make manually escrow of recovery keys to Azure AD
Use the Excel spreadsheet’s comparing feature to make sure no discrepancy between the 2 files. One CSV file who listed the Recovery Password Key IDs from MBAM Database and one listed the Key IDs from Azure AD. There should be no difference.
You could repeat step 2.3 mentioned above to deploy a script for backing up the Bitlocker Recovery Keys to Azure AD, assign script to the group of devices without keys in AAD.
5. Shutdown MBAM Server and decommission them.
- Correct any problem with the devices who are missing recovery passwords in Azure AD or MEM
- Power off the MBAM Server for 2 months (optional),
- Backup and Remove the MBAM Database.
- Decommission the MBAM Servers.
I hope the information is useful for your migration plan and deployment.
Thanks for viewing and discussing this topic.
Reference
- Manage Bitlocker in the Enterprise
- Bitlocker documents
- migrate Bitlocker to Azure AD
- Encrypt recovery data in the database
- Backup MBAM Recovery Key
- Bitlocker in Azure AD
- How to find Bitlocker Recovery Key
- Authentication vs. authorization - Microsoft identity platform | Microsoft Docs
- Intune – Query Azure AD Bitlocker Keys using Graph API – Azure Cloud & AI Domain Blog
- Encrypt macOS devices with FileVault disk encryption with Intune - Microsoft Intune | Microsoft Docs
- Jos Lieben script to list devices which have not been escrowed recovery keys to AAD.
- Authorization and Microsoft Graph Security API - Microsoft Tech Community
- Microsoft Graph PowerShell SDK and Azure Active Directory Identity Protection | Microsoft Docs
- Intune – Query Azure AD Bitlocker Keys using Graph API – Azure Cloud & AI Domain Blog
- Get Intune devices with missing BitLocker keys in Azure AD - MSEndpointMgr
- Microsoft Graph permissions reference - Microsoft Graph | Microsoft Docs
- How to migrate Bitlocker to Azure AD
Disclaimer The sample scripts are not supported under any Microsoft standard support program or service.
The sample scripts are provided AS IS without warranty of any kind. Microsoft further disclaims all
implied warranties including, without limitation, any implied warranties of merchantability or of
fitness for a particular purpose. The entire risk arising out of the use or performance of the
sample scripts and documentation remains with you. In no event shall Microsoft, its authors, or
anyone else involved in the creation, production, or delivery of the scripts be liable for any
damages whatsoever (including, without limitation, damages for loss of business profits,
business interruption, loss of business information, or other pecuniary loss) arising out of
the use of or inability to use the sample scripts or documentation, even if Microsoft has been
advised of the possibility of such damages.