As highlighted in my last blog posts (for Splunk and Qradar) about Azure Sentinel’s Side-by-Side approach with 3rd Party SIEM, there are some reasons that enterprises leverage Side-by-Side architecture to take advantage of Azure Sentinel capabilities.
For my last blog post I used the Microsoft Graph Security API Add-On for Splunk for Side-by-Side with Splunk. Another option would be to implement a Side-by-Side architecture with Azure Event Hub. Azure Event Hubs is a big data streaming platform and event ingestion service. It can receive and process events per second (EPS). Data sent to an Azure Event Hub can be transformed and stored by using any real-time analytics provider or batching/storage adapters.
This blog describes the usage of Splunk app Splunk Add-on for Microsoft Cloud Services in Side-by-Side architecture with Azure Sentinel.
For the integration, an Azure Logic app will be used to stream Azure Sentinel Incidents to Azure Event Hub. From there Azure Sentinel Incidents can be ingested into Splunk.
Let’s go with the configuration!
Preparation
The following tasks describe the necessary preparation and configurations steps.
- Onboard Azure Sentinel
- Register an application in Azure AD
- Create an Azure Event Hub Namespace
- Prepare Azure Sentinel to forward Incidents to Event Hub
- Configure Splunk to consume Azure Sentinel Incidents from Azure Event Hub
- Using Azure Sentinel Incidents in Splunk
Onboarding Azure Sentinel
Onboarding Azure Sentinel is not part of this blog post. However, required guidance can be found here.
Register an Application in Azure AD
The Azure AD app is later required to use it as service principle for the Splunk Add-on for Microsoft Cloud Services app.
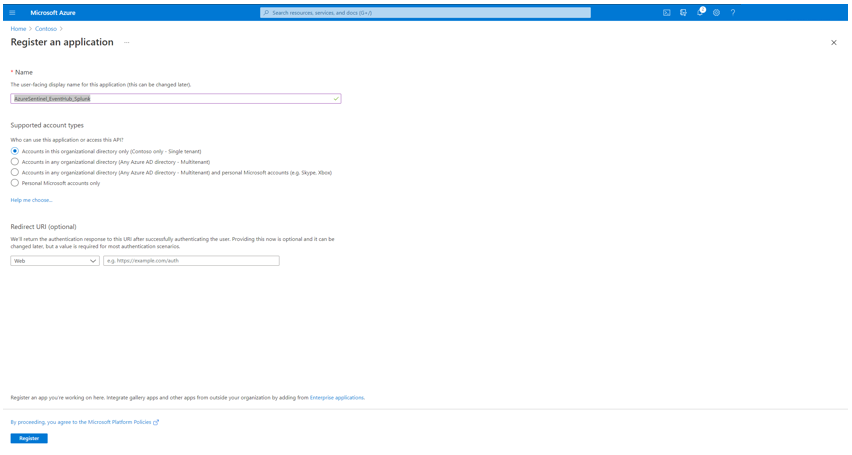
To register an app in Azure AD open the Azure Portal and navigate to Azure Active Directory > App Registrations > New Registration. Fill the Name and click Register.
Click Certificates & secrets to create a secret for the Service Principle. Click New client secret and make note of the secret value.
For the configuration of Splunk Add-on for Microsoft Cloud Services app, make a note of following settings:
- The Azure AD Display Name
- The Azure AD Application ID
- The Azure AD Application Secret
- The Tenant ID
Create an Azure Event Hub Namespace
As next step create an Azure Event Hub Namespace. You can use an existing one, however for this blog post I decided to create a new one.
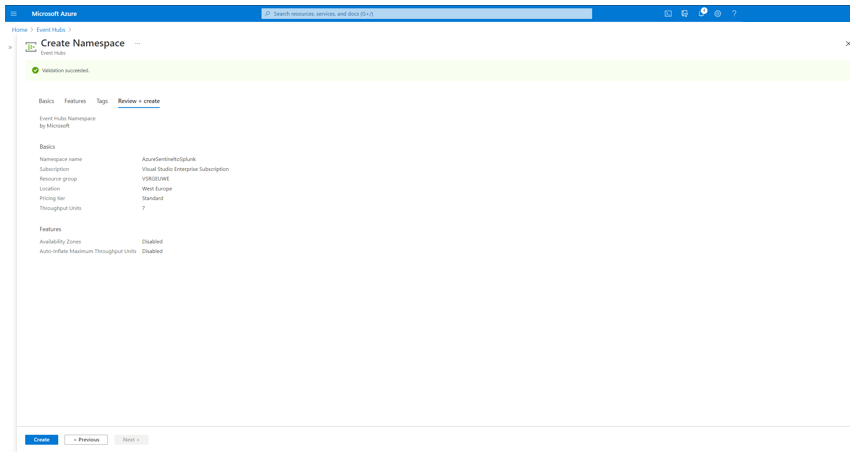
To create an Azure Event Hub Namespace open the Azure Portal, and navigate to Event Hubs > New. Define a Name for the Namespace, select the Pricing Tier, Throughput Units and click Review + create.
Review the configuration and click Create.
Once the Azure Event Hub Namespace is created click Go to resource to follow the next steps.
Click Event Hubs, after to Event Hub to create an Azure Event Hub within the Azure Event Hub Namespace.
Define a Name for the Azure Event Hub, configure the Partition Count, Message Retention and click Create.
Navigate to Access control (IAM) and click to Role assignments. Click + Add to add the Azure AD Service Principle created before and delegate as Azure Event Hubs Data Receiver and click Save.
For the configuration of Splunk Add-on for Microsoft Cloud Services app, make a note of following settings:
- The Azure Event Hub Namespace Host Name
- The Azure Event Hub Name
Prepare Azure Sentinel to forward Incidents to Event Hub
For the forwarding for Azure Sentinel Incidents to Azure Event Hub you need to firstly configure an Azure Logic App, and secondly an Automation Rule in Azure Sentinel to trigger the playbook for any Incidents in Azure Sentinel.
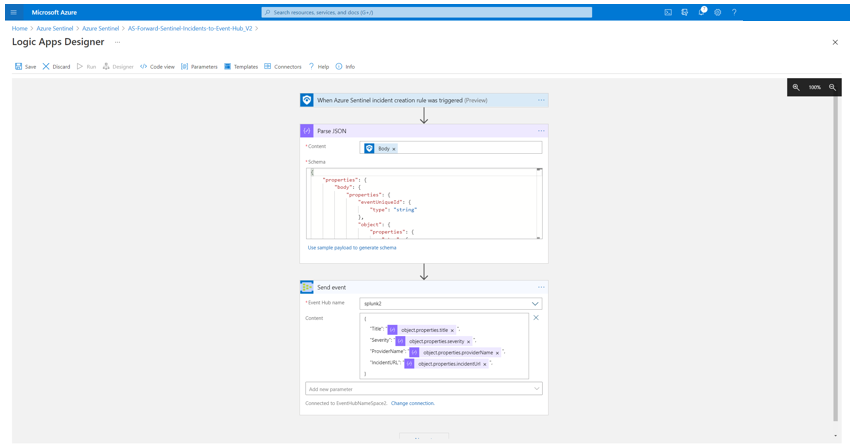
For my scenario I configured an Azure Logic App as following shown:
Startwith the Azure Sentinel trigger When Azure Sentinel Incident Cration Rule was Triggered. Parse the output for later usage. For the Azure EventHub connection, define first the connection to Azure Event Hub and select the Azure EventHub name. Define a JSON format as content to send selected fields from an Azure Sentinel Incident to Azure EventHub. For my case I want to forward the fields Title, Severity, ProviderName and the IncidentURL to Azure EventHub.
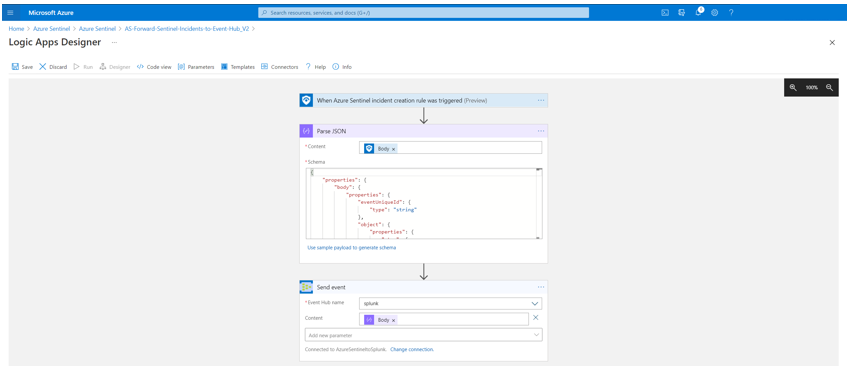
You can also have the full Body from Parse JSON output as well, to forward all attributes of an Azure Sentinel Incident.
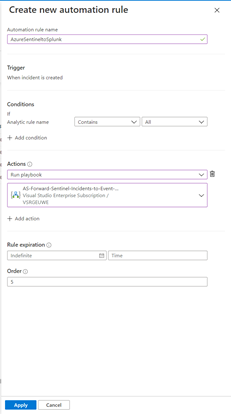
Save the Azure Logic App and navigate to Azure Sentinel > Automation. From here you can create an Automation rule to trigger the Azure Logic App, created in previous step.
Click to + Create and select Add new rule.
Define a Name for the Automation rule name and define the Conditions. As I want to trigger the Azure Logic App for any Analytics rule in Azure Sentinel, I let the Condition as is – “all” (for “all rules” is selected, you can choose specifc rules to inculde or exclude. Select the Run Playbook as Action and the Azure Logic App created before and click Apply.
Once the configuration is completed, you can review the Automation rule in Automation page.
Configure Splunk to consume Azure Sentinel Incidents from Azure Event Hub
To ingest Azure Sentinel Incidents forwarded to Azure Event Hub there is a need of to install the Splunk App, Splunk Add-on for Microsoft Cloud Services.
For the installation open the Splunk portal and navigate to Apps > Find More Apps. For the dashboard find the Splunk Add-on for Microsoft Cloud Services app and Install.
Once installed, navigate to App Splunk Add-on for Microsoft Cloud Services > Azure App Account to add the Azure AD Service Principles, and use the noted details from previous step. Click Add and define a Name for the Azure App Account, add the Client ID, Client Secret, Tenant ID and choose Azure Public Cloud as Account Class Type. Click Update to save and close the configuration.
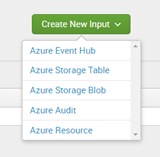
Now navigate to Inputs within the Splunk Add-on for Microsoft Cloud Services app and select Azure Event Hub in Create New Input selection.
Define a Name for the Azure Event Hub as Input, select the Azure App Account created before, define the Event Hub Namespace (FQDN), Event Hub Name, let the other settings as default and click Update to save and close the configuration.
Using Azure Sentinel Incidents in Splunk
Once the ingestion is processed, you can query the data by using sourcetype=”mscs:azure:eventhub” in search field.
Summary
We just walked through the process of how to implement Azure Sentinel in Side-by-Side with Splunk by using the Azure Event Hub.
Stay tuned for more us cases in our Blog channel!
Thank you for
Many thanks to Clive Watson for brainstorming and ideas for the content.