Hey everyone!
Having the right information during an investigation is crucial to differentiating between FP and TP, and to starting the ‘Scope of Breach’ process on time, since every second counts.
The attack surface used by hackers is often the company’s user and service accounts, so the information about those accounts – who is the user behind them, what are their privileges, and additional data – is important for the analyst to have while investigating those entities.
Furthermore, embedding entity information in your analytics rules will result in ‘tailor-made’ analytics for your organization that fit your use cases and scenarios and can reduce FP.
How Do I Start?
If you haven’t enabled UEBA – we encourage you to do so! It’s so simple.
Part of the process of enabling UEBA is providing consent for Sentinel UEBA to synchronize you Azure Active Directory. This allows us to create profiles for user accounts in the organization.
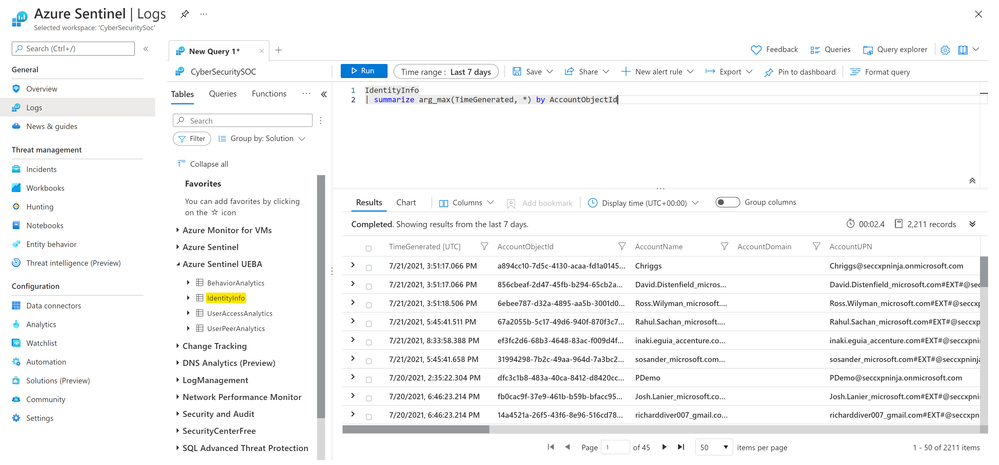
If already have UEBA enabled, you will notice that a new table called ‘IdentityInfo’ is now available under ‘Azure Sentinel UEBA’ group in LA.
The Identity info table contains a snapshot of the user’s profile: metadata information, groups membership, Azure AD roles assigned and UEBA enrichments.
Important information:
- Once UEBA is enabled, we will sync all your AAD users into the ‘IdentityInfo’ table
- Default retention time for the table is 30 days
- After the initial sync, any changes to made in AAD to your users will be saved in LA in up to 15 minutes.
- Groups & Roles are updated on a daily basis
- Every 21 days we will resync your entire AAD directory, to make sure stale records are updated.
- Note:
- Deleted groups (user was removed from a group) is not supported yet. It will still be listed in the user’s groups membership.
- We only support Azure Active Directory built-in roles for the assigned roles attribute.
- The initial sync might take a few days (depending of the size of the tenant).
What information can I find there?
The IdentityInfo table contains the following information taken from your Azure Active Directory:
Column | Type | Description |
AccountCloudSID | string | The Azure AD security identifier of the account |
AccountCreationTime | datetime | The date the user account was created (UTC) |
AccountDisplayName | string | The user account display name |
AccountDomain | string | Domain name of the user account |
AccountName | string | User name of the account |
AccountObjectId | string | The Azure Active Directory object ID for the account |
AccountSID | string | The on premises security identifier of the account |
AccountTenantId | string | The Azure Active Directory Tenant ID of the account |
AccountUPN | string | User principal name of the account |
AdditionalMailAddresses | dynamic | Additional email addresses of the user |
AssignedRoles | dynamic | AAD roles the user account is assigned to |
City | string | The city of the user account as defined in AAD |
Country | string | The country of the user account as defined in AAD |
DeletedDateTime | datetime | The date and time the user was deleted |
Department | string | The user account department as defined in AAD |
GivenName | string | The user account given name |
GroupMembership | dynamic | Azure AD Groups the user account is a member |
IsAccountEnabled | bool | Indication if the account is enabled in AAD or not |
JobTitle | string | The user account job title as defined in AAD |
MailAddress | string | The user account primary email address |
Manager | string | The user accounts manager alias |
OnPremisesDistinguishedName | string | Active Directory distinguished name (DN). A DN is a sequence of relative distinguished names (RDN) connected by commas. |
Phone | string | The phone number of the user account as defined in AAD |
SourceSystem | string | |
State | string | The geographical state of the user account as defined in AAD |
StreetAddress | string | The office street address of the user account as defined in AAD |
Surname | string | The user account surname |
TenantId | string | |
TimeGenerated | datetime | Time when the event was generated (UTC) |
Type | string | The name of the table |
UserType | string | The user type as appears in Azure AD |
What’s in it for me?
Having user information surfaced in Log Analytics allows you (as a SecOps / Threat Hunter) to address various lines of investigation, for example:
Which users are members of my “Executive” AAD security group?
| summarize arg_max(TimeGenerated, *) by AccountObjectId
| where GroupMembership contains “Executive”
Who are all my guest accounts in the tenant?
| summarize arg_max(TimeGenerated, *) by AccountObjectId
| where UserType == “Guest”
Which of my users are only AAD users (i.e. not synced from my on prem AD)?
| summarize arg_max(TimeGenerated, *) by AccountObjectId
| where isempty(OnPremisesDistinguishedName)
Which users have assigned “privileged” Azure Active Directory roles?
IdentityInfo
| summarize arg_max(TimeGenerated, *) by AccountObjectId
| mv-expand AssignedRoles
| where AssignedRoles in~ (PrivielgedRoles)
| summarize AssignedRoles=make_set(AssignedRoles) by AccountObjectId, AccountSID, AccountUPN, AccountDisplayName, JobTitle, Department
SecOps analysts can use this information to create their custom analytics rules:
I want to be alerted if a specific server is accessed by anyone outside of the ‘Finance Department’.
SecurityEvent
| where EventID in (LoginEvent)
| where Computer == “Financesrv.contoso.com”
| join kind=innerunique (
IdentityInfo
| summarize arg_max(TimeGenerated, *) by AccountObjectId
) on $left.TargetUserSid == $right.AccountSID
| where Department != “Finance”
Taking the above example you can extend it even further – if the user is a member of a specific group, don’t trigger alert.
In addition when using automation to create a ticket in the ticketing system, pull information about the user from the ‘IdentityInfo’ table .
You can read more about the IdentityInfo table and how to use it in our docs.
What’s next?
Our goal is to expose to you, the Sentinel user, the we have of the users in your organization. We’re going to constantly add more bits of information we learn about users (example below). In addition, we want to expand the entity profiles we have and surface those in Log Analytics as well (such as DeviceInfo, AppInfo, SecurityGroupInfo, IPaddressInfo…)
IdentityInfo table features to come:
- Applications
- Blast Radius
- EmployeeId
- Extension property from AAD
- Investigation priority – risk score
- Is MFA registered
- Last seen date
- On-prem extension property
- AAD IP risk level and state
- Related service principals
- Tags
- UACFlags
- UserState
- UserStateChangedOn
We Value Your Opinion!
Our goal is to make your life easier while you investigate security incidents. If you have any feedback – about the experience, the usage – or anything else,
Please let us know! We aim to improve ![]()
