This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Tech Community.
Disclaimer
This document is provided “as is.” MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, IN THIS DOCUMENT. This document does not provide you with any legal rights to any intellectual property in any Microsoft product. You may copy and use this document for your internal, reference purposes.
Introduction
Azure Defender for App Service helps organizations be more secure by providing dedicated security analytics for your App Service resources. The purpose of this article is to provide specific guidance on how to validate Azure Defender for App Service alerts, by simulating a suspicious activity on applications running over App Service. For more validation scenarios, visit our
Preparation
The first step in validating Azure Defender alerts for App Service is to ensure that Azure Defender for App Service is enabled on the subscription(s) as shown in Figure 1, that you want to use to validate the alert.

Enabling Azure Defender for App Service provides monitoring and threat detection for a multitude of threats to your App Service resources. Additionally, enabling Azure Defender for App Service, surfaces security findings with recommendations on how to harden your resources covered by the App Service plan. To learn more about Azure Defender for App Services, watch this video.
Azure Defender plans can be enabled individually. For the purpose of validating the scenario covered in this article, pre-requisite is to solely enable Azure Defender for App Service.
After enabling Azure Defender for App Service, you need to determine the scenario that you want to validate. Common scenarios that can be simulated range from php uploads, to NMAP scanning, or even Content Management System (CMS) fingerprinting. When determining the scenarios for which you would like to validate Azure Defender alerts, you can also consult the reference guide of Alerts for Azure App Service. Azure Defender for App Service alerts are mapped to and cover almost the complete MITRE ATT&CK tactics from pre-attack to command and control, which can be useful when deciding which scenario(s) you wish to simulate.
In case you wish to solely test that the pipeline is working, there is also a like alert for App Service which can be invoked by making a web request to a “/This_Will_Generate_ASC_Alert” URI. I.e. if your site is named ‘foo’, making a request to https://foo.azurewebsites.net/This_Will_Generate_ASC_Alert, will generate an alert similar to the one shown in Figure 2.

In this article, we will simulate the scenario of accessing a suspicious PHP page located in the upload folder, which will generate the “PHP file in upload folder” alert. This type of folder doesn’t usually contain PHP files and its existence might indicate exploitation taking advantage of arbitrary file upload vulnerabilities.
Implementing
In order to simulate this scenario, you could either use an existing Web App or create a new one. When creating a new Web App, you can deploy a PHP app to Azure App Service on Linux (as a runtime stack select PHP 7.4) The alert that will be generated applies to both App Service on Linux and Windows. Once you’ve created the App Service Plan and the Web App, install Wordpress 5.8 (including creating an Azure Database for MySQL server). To learn more about how to create a PHP Web App in Azure App Service, read this guidance.
Note: In most cases, once a new web site is created, it might take up to 12h for alerts related to a newly created web site to appear.
To simulate the scenario of accessing a suspicious PHP page located in the upload folder, a PHP page is required. You can use the sample below to create a test PHP page (shown in Figure 3) and save it as a PHP file.
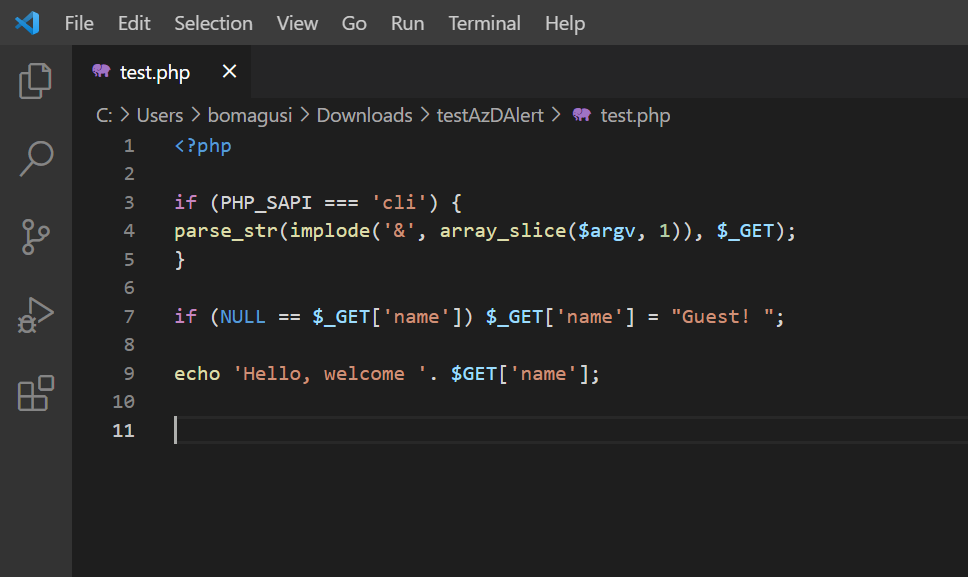
Afterwards, navigate to “/wp-content/uploads/2021/08/” (alternatively you can create

Important: After you’ve uploaded the PHP file to this folder, you need to browse to this PHP page using a browser (similarly to Figure 5). Please note that the output on the page, will depend on the code in your test PHP file.

Validating
Once Azure Defender for App Service generates the alert on target subscription(s), you can find it in the “Security alerts” section of the Azure Security Center dashboard. Selecting the generated alert (in this case “PHP file in upload folder”) will open a blade, which provides more context and rich metadata about the alert (similar to Figure 6).

When validating the alerts, be sure to consult the full list of App Service alerts.
You can also export Azure Defender alerts to a SIEM (i.e. Azure Sentinel or 3rd party SIEM).
- Learn more about how to stream alerts to a SIEM, SOAR or ITSM.
- Learn more about how to investigate Azure Security Center alerts using Azure Sentinel.
- Learn more about Analysing Web Shell Attacks with Azure Defender data in Azure Sentinel - Microsoft Tech Community.
Final Considerations
Azure Defender for App Service is all about providing threat detection and security recommendations for applications running over App Service. This article focuses on validating alerts for Azure Defender for App Service, by simulating a specific scenario, namely accessing a suspicious PHP page located in the upload folder. Properly executing the steps outlined in this article generates the security alert “PHP file in upload folder”. This article is not intended to cover all scenarios, but it does provide real value as you get started with validating Azure Defender for App Service alerts. Remember to keep an eye out for other article from this series, which can be found on our official ASC Tech Community.
Reviewers:
@Yuri Diogenes, Principal PM
@Tomer Spivak, Senior PM
Contributors:
Dotan Patrich, Principal Software Engineer,
Yossi Weizman, Senior Security Researcher
Ram Pliskin, Senior Security Researcher Manager
Lior Arviv, Senior PM
