This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Tech Community.
This post presents a shared effort which includes
Microsoft Sentinel automation rules and playbooks allow analysts to better automate their incident triage and response processes to lower their SOC’s MTTR (mean time to remediate). Playbooks are triggered automatically when an incident is created, or on demand during the triage, investigation, and remediation processes. Playbooks are a powerful automation tool, as they can call almost any REST API-based external service which plays a role in the SOC’s processes. Though playbooks can be developed by SOC engineers, creating your own integration from scratch may take time and require deep understanding of the 3rd party products. Therefore, having out-of-the-box, ready-to-use playbooks is a huge time saver and enabler for new scenarios, which will eventually save a lot of time for the SOC.
Over the last year a lot of out-of-the-box playbook content has been added to Microsoft Sentinel. Now, it is easier than ever to implement security automation scenarios, improve SOC efficiency, and become a playbooks ninja!
See the full list of SOAR integrations
Where SOAR integrations can be found?
- Today, we also announce the Playbook templates gallery (new tab under Automation) which presents the leading scenarios contributed by Microsoft security professionals and Microsoft Sentinel community. Learn more about this new feature in the announcement blog.
- Playbook templates can also be obtained as part of an Microsoft Sentinel Solution in the context of a specific product. The deployment of the solution produces active playbooks. Eventually, all SOAR OOTB content will be consumed from Content Hub.
- If content wasn’t packed yet as an Microsoft Sentinel Solution, it can be found in Microsoft Sentinel GitHub repository which contains many playbook templates.
SOAR integrations usually include:
- Logic Apps connectors which are the building blocks for creating playbooks. Logic Apps connectors encapsulate the authentication to the external product they interact with and wrap API calls into playbook actions.
- Playbook templates which use the Logic Apps connectors. Playbook template is a pre-built, tested, and ready-to-use workflow that can be customized to meet your needs.
Example scenarios
Below are common automation scenarios and the available integrations you can now use to implement them in playbooks.
Enrichment integrations
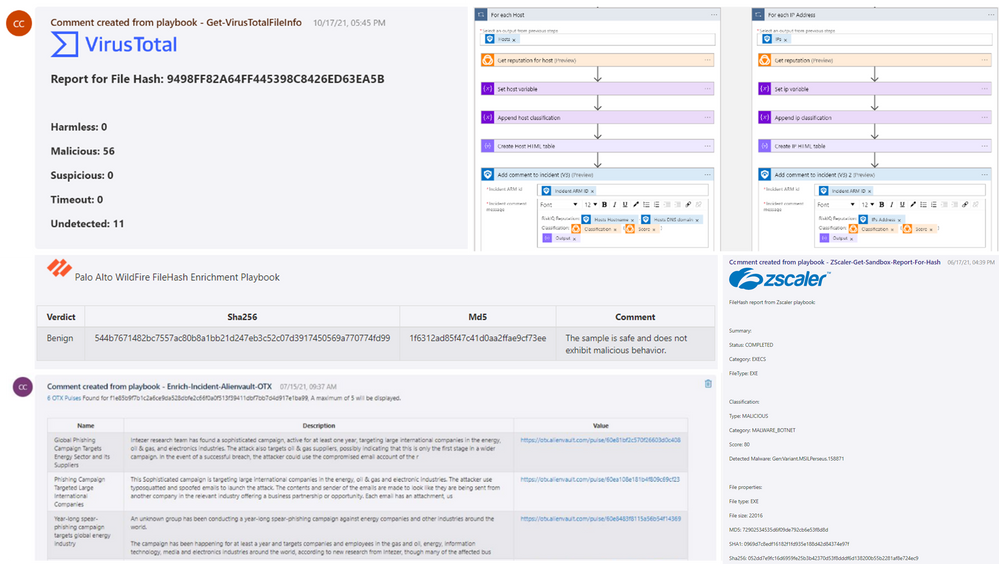
Fetch information from another service to add information to an incident. This information is usually added as a comment to the incident or sent to the SOC. Due to Microsoft Sentinel comments HTML and Markdown support, those comments can be formatted nicely.
Tip: Enrichment integration are great to prepare the incident for investigation. To improve SOC efficiency, attach enrichment playbooks as part of your automation rules which are triggered when an incident is created, so when analysts triage and investigate their incident relevant queries results and reports are already presented there.
- AlienVault OTX
- CrowdStrike Falcom
- CarbonBlack Cloud
- Geo IP
- GreyNoise
- Have I Been Pwnd
- HYAS
- Palo Alto Wildfire
- Proofpoint TAP
- Recorded Future
- Reversing Labs
- RiskIQ
- Virus Total
- Zscaler
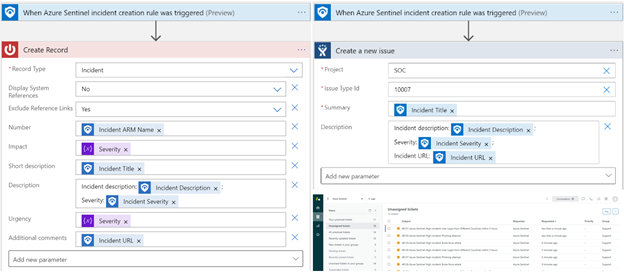
Sync incidents with external systems
When an incident is created, create a linked ticket in your external ITSM.
Tip: An advantage for using playbooks for syncing incidents is that you can customize the fields mapping.
- ServiceNow
- Azure DevOps
- Jira
- Zendesk
- IronNet Iron Defense
- Freshdesk
- Freshservice
Identities management and response
Enrich incidents with suspicious users and groups information. Respond to risky users: reset password, suspend/unsuspend, clear user sessions, add user to a group.
Tip: use prompt user playbooks to involve an interactive message sent to the suspicious user, to ask if they performed the suspicious activity.
- Azure Active Directory
- AAD Identity Protection
- Microsoft 365 Users
- Okta
Endpoint Protection Enrichment and Response
Quarantine endpoint, update policies, run scripts on endpoints and enrich incident with endpoint information. Audit the actions take as a comment to the incident.
- Crowdstrike Falcon
- Microsoft Defender for Endpoints
- VMWare Carbon Black Cloud
Network Security Enrichment and Response playbooks
When a new incident is created, update firewall policies, network object groups or security rules to block traffic from suspicious Ips; Add domains and URLs to destination lists; Check if firewall rules already mitigated the threat and post a comment on the incident.
- Azure Firewall
- Cisco ASA
- Cisco Firepower
- Cisco ISE
- Cisco Meraki
- Cisco Umbrella
- F5 Big IP
- Forcepoint NGFW
- Fortinet FortiGate
- Palo Alto PAN OS
- Palo Alto Wildfire
- Zscaler
Respond automatically, but require analyst confirmation
Playbooks can be attached to an automation rules to run when an incident is created, or run manually by the analyst during the triage, investigation and remediation processes.
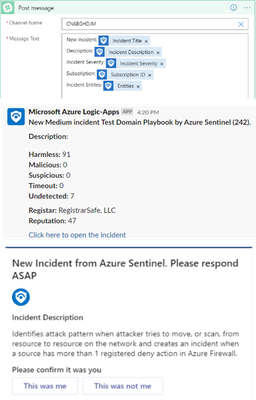
For scenarios which require sensitive remediation actions, such changing firewall configurations or disable a user, we usually supply at list one playbook template which includes a human intervention step using Microsoft Teams adaptive cards.
For example, a playbook which blocks an IP in Azure Firewall would send to the SOC Teams channel a card with incident information and ip status in the firewall, and allows the analyst to take the decision if the IP should be blocked or not.
Orchestration and notification
When an incident is created, playbook collects details from an incident and sends it to the SOC shared mailbox, chat channel in Teams or Slack, assigned user email or SMS. Analysts can quickly understand the severity, what tactics and entities are associated with the incident, and use the incident link to pivot directly to the specific incident page in the Microsoft Sentinel.
Tip: use
- Microsoft Teams
- Office Outlook 365
- Shift for Microsoft Teams
- Slack
Learn more
- Microsoft Sentinel SOAR (Orchestration, automation, and response)
- Automation rules
- Playbooks
- Customize playbooks from templates
- Authenticate playbooks to Microsoft Sentinel
- Use triggers and actions in playbooks