This post has been republished via RSS; it originally appeared at: Microsoft Tech Community - Latest Blogs - .
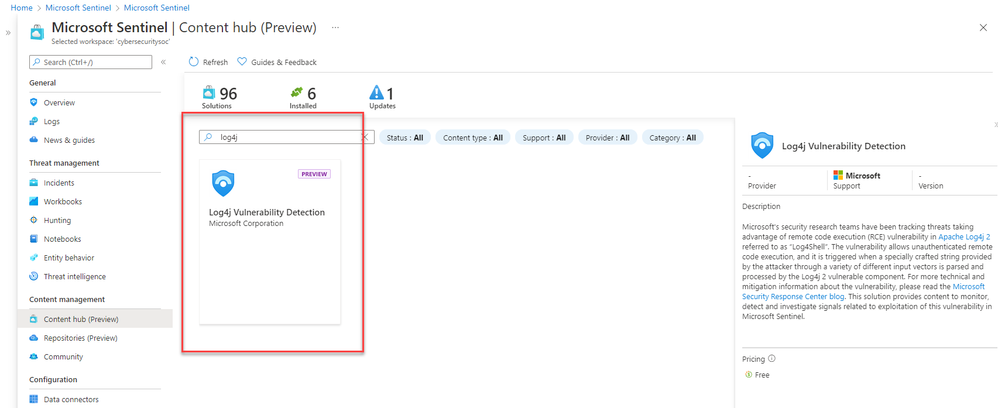
Microsoft's security research teams have been tracking threats taking advantage of the remote code execution (RCE) vulnerability in Apache Log4j 2 referred to as “Log4Shell” and tracked as CVE-2021-44228. The vulnerability allows unauthenticated remote code execution and is triggered when a specially crafted string provided by the attacker through a variety of different input vectors is parsed and processed by the Log4j 2 vulnerable component.
A new Microsoft Sentinel solution has been added to the Content Hub that provides content to monitor, detect and investigate signals related to exploitation of the recently disclosed Log4j vulnerability.
For technical and mitigation information about the vulnerability, please read: