This post has been republished via RSS; it originally appeared at: Microsoft Tech Community - Latest Blogs - .
As cloud security threats continue to evolve, we are seeing an increase in attacks targeting IoT devices used in enterprise environments in addition to operational technology (OT) devices used in industrial systems and critical infrastructure. These devices, which are often unpatched, misconfigured, and unmonitored, are ideal targets for adversaries.
Security teams traditionally have not had tooling nor the expertise to provide them with visibility to monitor Internet of Things (IoT)/ Operational Technology (OT) networks for vulnerabilities. As a result, IoT/ OT security risks have traditionally been overlooked. This poses a great risk to organizations, as we see adversaries moving laterally from IT to OT with ease.
Existing Security Operations Center (SOC) solutions focus on IT security and tend to lack OT telemetry and insights. Where we do see OT solutions, they lack integration with existing SOC tools and workflows. Teams are looking for a comprehensive, unified solution that spans IT and OT.
Microsoft Sentinel: IT/OT Threat Monitoring with Defender for IoT Solution unites IT and OT, providing an unprecedented step toward protecting critical OT assets and securing your organization.
This solution provides visibility, remediation, and response all from one pane of glass; empowering security teams to detect, analyze and respond to IoT/OT threats within the context of their IT environment and by leveraging their existing tooling.
Learn more by watching the demo: Demo: Microsoft Sentinel: IoT/OT Threat Monitoring with Defender for IoT solution - YouTube
Content Use Cases
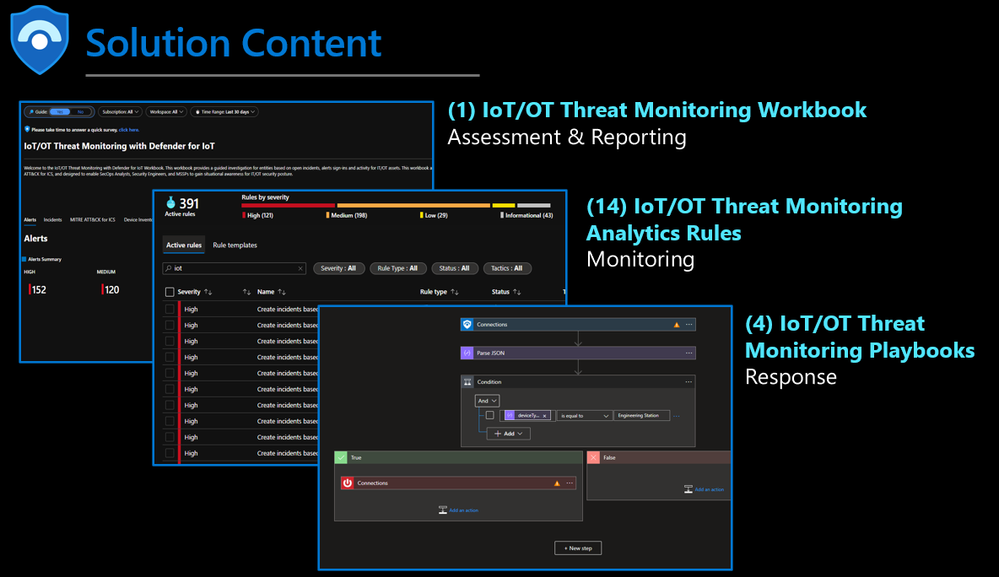
This solution provides the foundation for building a SOC for monitoring IoT/ OT and includes (1) workbook for visibility/reporting, (14) analytics rules for monitoring, and (4) playbooks for response. The workbook leverages Microsoft Sentinel telemetry to create visualization to understand, analyze, and respond to IoT/OT threats. Understanding alerts over time provides unprecedented insights into security posture and where teams need to focus to harden against threats. Deep links directly to Microsoft Defender for IoT alerts empower analysts to focus on remediating threats rather than pivoting between tools.
Benefits
- Detect, analyze, and respond to IoT/OT threats from a single pane of glass
- Assess security alert and incident response efficiency to improve SOC team capability
- Streamlined, consistent alignment between threat behavior and MITRE ATT&CK for ICS matrix
- Customizable reporting for subscription, workspace, and time filters
- Deep links integration for seamless pivots between Microsoft Sentinel and Microsoft Defender for IoT
- Device Inventory for identification, configuration, and baselining of OT
- Advanced analytics for detection of IoT/OT threats
- Playbook Automation for response to IoT/OT threats
Getting Started
This content is designed to provide the foundation for designing, building, and operating an IoT/OT monitoring team. Below are the steps to onboard required dependencies, review content, and provide feedback.
- Onboard Microsoft Sentinel
- Onboard Microsoft Defender for IoT
- Connect Microsoft Defender for IoT to Microsoft Sentinel
- Deploy the Microsoft Sentinel: IT/OT Threat Monitoring with Defender for IoT Solution
- Microsoft Sentinel > Content Hub > Select IT/OT Threat Monitoring with Defender Solution > Install
- In Government Regions, leverage the Deploy to Azure Gov button from the GitHub ReadMe for deployments.
- Microsoft Sentinel > Content Hub > Select IT/OT Threat Monitoring with Defender Solution > Install
- Review the IT/OT Threat Monitoring with Defender for IoT Workbook
- Microsoft Sentinel > Workbooks > Select IT/OT Threat Monitoring with Defender for IoT
- Review the IT/OT Threat Monitoring with Defender for IoT Analytics Rules
- Microsoft Sentinel > Analytics > Search “IoT”
- Review the IT/OT Threat Monitoring with Defender for IoT Playbooks
- Microsoft Sentinel > Automation > Playbooks > Search “IoT”
- Review the content and provide feedback through the survey
Frequently Asked Questions
- Are custom views and reports supported?
- Yes, via subscription, workspace, time, parameters.
- Are additional products required?
- There are not additional product requirements beyond Microsoft Sentinel and Microsoft Defender for IoT.
- Is this available in government regions?
- Yes, this is deployable in all environments.
- What rights are required to use this content?
- Security Contributor can create and edit workbooks, analytics rules, and other Microsoft Sentinel resources. Security Reader can view data, incidents, workbooks, and other Microsoft Sentinel resources.
Learn More About Defending IoT/OT with Microsoft Security
- Defending Critical Infrastructure with the Microsoft Sentinel: IT/OT Threat Monitoring Solution (Azure Sentinel Tech Community)
- Protecting federal information systems and critical infrastructure with the Microsoft Sentinel: IT/OT Threat Monitoring Solution (Azure Government DevBlogs)
- Microsoft Sentinel: IoT/OT Threat Monitoring with Defender for IoT solution (YouTube)
- Enabling IoT/OT Threat Monitoring in Your SOC with Microsoft Sentinel
- Defender for IoT product summary
- Cloud-delivered IoT/OT threat intelligence
- 5 steps to enable your corporate SOC to rapidly detect and respond to IoT/OT threats