This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Tech Community.
Thanks to
Watchlists in Microsoft Sentinel allow you to correlate data from a data source you provide with the events in your Microsoft Sentinel environment. For example, you might create a watchlist with a list of high-value assets, terminated employees, or service accounts in your environment.
You can use watchlists in your search, detection rules, threat hunting, and response playbooks.
Recently, we have published new Microsoft Sentinel API endpoints focused on a watchlist. Together with these APIs, we also created new playbook actions that you can use in your day-to-day automation.
In addition to being a Security Information and Event Management (SIEM) system, Microsoft Sentinel is also a platform for Security Orchestration, Automation, and Response (SOAR). One of its primary purposes is to automate any recurring and predictable enrichment, response, and remediation tasks that are the responsibility of your Security Operations Center and personnel (SOC/SecOps), freeing up time and resources for more in-depth investigation of, and hunting for, advanced threats. Automation takes a few different forms in Microsoft Sentinel, from automation rules that centrally manage the automation of incident handling and response, to playbooks that run predetermined sequences of actions to provide powerful and flexible advanced automation to your threat response tasks.
New playbooks watchlist actions
First, we updated two watchlist actions, that already existed, to support SearchKey:
- Watchlist – Add a new watchlist item
- Logic App Action doc - Microsoft Sentinel - Connectors | Microsoft Docs
- API doc - Watchlist Items - Create Or Update - REST API (Azure Sentinel) | Microsoft Docs
- Watchlist – Update an existing watchlist item
- Logic App Action doc - Microsoft Sentinel - Connectors | Microsoft Docs
- API doc - Watchlist Items - Create Or Update - REST API (Azure Sentinel) | Microsoft Docs
Additionally, we published six more actions to cover various watchlist use-cases:
- Watchlist – Create a new watchlist with data
- Logic App Action doc - Microsoft Sentinel - Connectors | Microsoft Docs
- API doc - Watchlists - Create Or Update - REST API (Azure Sentinel) | Microsoft Docs
- Watchlist – Delete a watchlist
- Logic App Action doc - Microsoft Sentinel - Connectors | Microsoft Docs
- API doc - Watchlists - Delete - REST API (Azure Sentinel) | Microsoft Docs
- Watchlist – Delete a watchlist item
- Logic App Action doc - Microsoft Sentinel - Connectors | Microsoft Docs
- API doc - Watchlist Items - Delete - REST API (Azure Sentinel) | Microsoft Docs
- Watchlist - Get a watchlist by alias
- Logic App Action doc - Microsoft Sentinel - Connectors | Microsoft Docs
- API doc - Watchlists - Get - REST API (Azure Sentinel) | Microsoft Docs
- Watchlist - Get a watchlist item
- Logic App Action doc - Microsoft Sentinel - Connectors | Microsoft Docs
- API doc - Watchlist Items - Get - REST API (Azure Sentinel) | Microsoft Docs
- Watchlist – Get all watchlist items for a given watchlist
- Logic App Action doc - Microsoft Sentinel - Connectors | Microsoft Docs
- API doc - Watchlist Items - List - REST API (Azure Sentinel) | Microsoft Docs
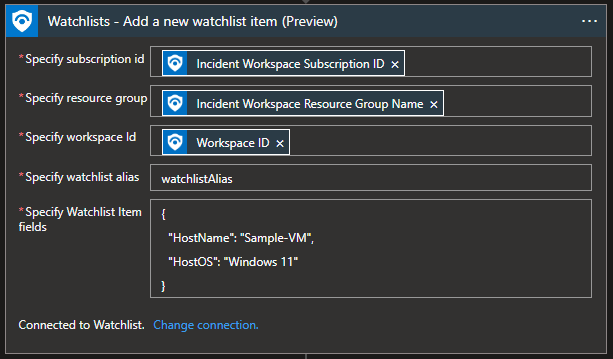
Watchlist – Add a new watchlist item
A standard use case for the “Add a new watchlist item” action would be when there are IP, URL, user, or host, in the incident that we want to add to the watchlist automatically.
Example:
Fields Subscription ID, Resource group, and Workspace ID are available as dynamic content when using “Microsoft Sentinel Incident” or “Microsoft Sentinel Alert” as a trigger.
In “Specify Watchlist Item fields” we specify fields we want to add to the watchlist. A watchlist with these fields must be pre-created.
“HostName” and “HostOS” are column names in the watchlist.
Note: These fields are case-sensitive. If you specify a column name that does not exist in the watchlist, a new column with that name will be created. Ex., if we write “Hostname” instead of “HostName”, a new column called “Hostname” will be created, and data will be saved there. This can also affect SearchKey if it’s connected to “HostName” field because when we filter by SearchKey, it will not show data from “Hostname”.
“Sample-VM” and “Windows 11” are custom data we want to add to specified columns.
For custom data, we can use the playbook’s dynamic content to add host, IP, or URL from the incident itself.
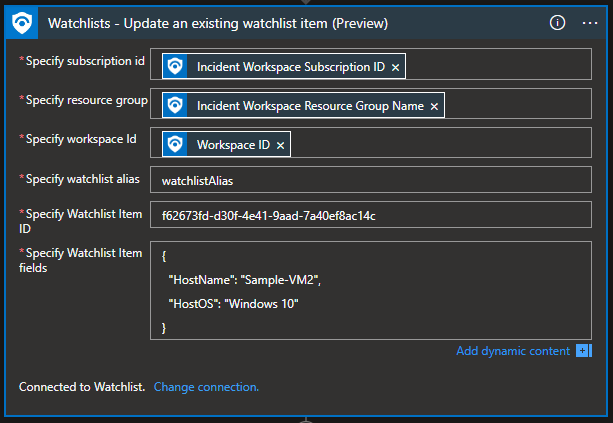
Watchlist – Update an existing watchlist item
Use case for “Update an existing watchlist item” action would be when there are IP, URL, user, or host, in the incident that we want to update in the watchlist automatically.
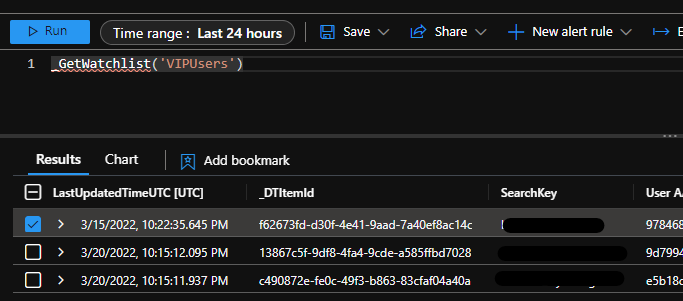
To update a watchlist item using playbooks, you need a watchlist item ID. It can be found in Log Analytic logs when searching for a watchlist in the field “_DTItemd”.
Example:
In the “Specify Watchlist Item ID” field, you paste the “_DTItemd” field from Log Analytics logs.
In “Specify Watchlist Item fields” you add fields that you want to be updated. Please note that if you have five columns in a watchlist and update two columns, the three columns not specified in the update will be updated with an empty value, i.e., if there is any value, it will be deleted.
“HostName” and “HostOS” are column names in the watchlist.
Note: These fields are case-sensitive. If you specify a column name that does not exist in the watchlist, a new column with that name will be created. Ex., if we write “Hostname” instead of “HostName”, a new column called “Hostname” will be created, and data will be saved there. This can also affect SearchKey if it’s connected to “HostName” field because when we filter by SearchKey it will not show data from “Hostname”. “HostName” field will be overwritten with an empty value in this case.
“Sample-VM2” and “Windows 10” are new values for our existing watchlist item.
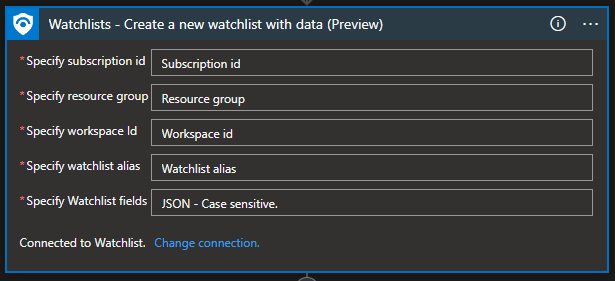
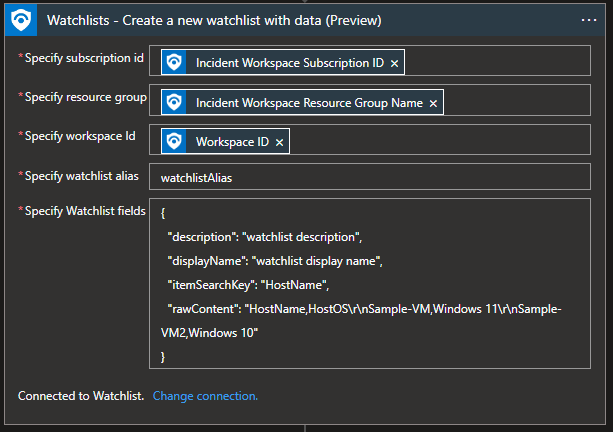
Watchlist – Create a new watchlist with data
Not always do we have a watchlist to which we want to add data, and sometimes we need to create a watchlist and add data from the incident. It can be a watchlist that will contain incident entities as IoCs.
Example:
“Specify Watchlist fields” must contain this JSON data:
- description – description of the watchlist
- displayName – display the name of the watchlist (does not need to be the same as the watchlist alias
- itemSearchKey – connecting SearchKey to a specific column (in my case column is “HostName”)
- rawContent – columns and column values. You first specify columns, and then column values for each row. In my case it is "HostName,HostOS\r\nSample-VM,Windows 11\r\nSample-VM2,Windows 10".
- HostName,HostOS – column names
- \r\n – separation between values
- Sample-VM,Windows 11 – HostName and HostOS value for first entry (it is mapped that HostName is Sample-VM and HostOS is Windows 11)
- Sample-VM2,Windows 10 – HostName and HostOS value for second entry (it is mapped that HostName is Sample-VM2 and HostOS is Windows 10)
If we need to add multiple dynamic values (ex., we have multiple IPs in the incident that we need to add to a new watchlist), we can create a CSV table from those values and add the output of that table to the “rawContent”. This example is used in the template watchlist at the end of the blog (add IP, URL, user, or host to the watchlist).
Example:
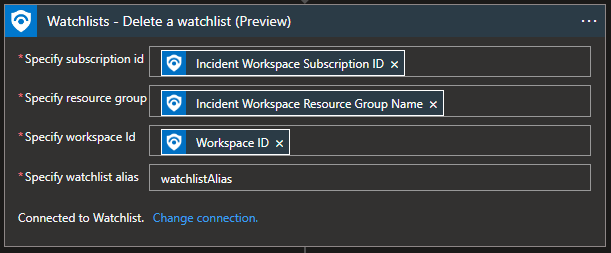
Watchlist – Delete a watchlist
We can use this action to continue from the “Create a new watchlist with data” action and delete the watchlist with incidents IoC’s once the incident is closed.
Example:
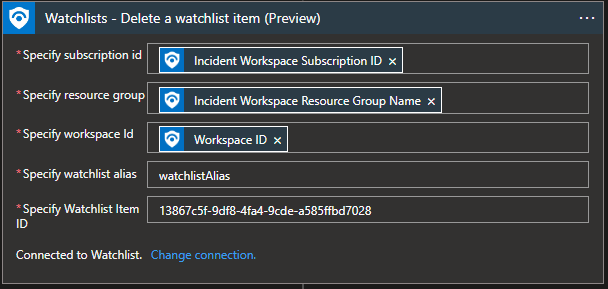
Watchlist – Delete a watchlist item
During the incident enrichment, we can find that one entity is not malicious anymore, and it is part of the existing watchlist. With this specific action, we can remove the entity from the malicious entity watchlist.
Example:
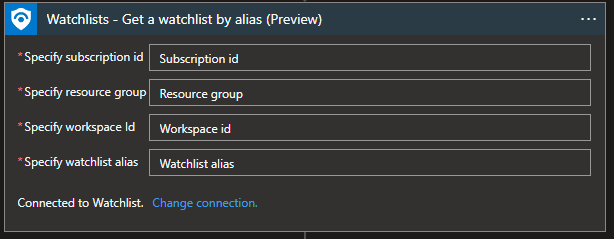
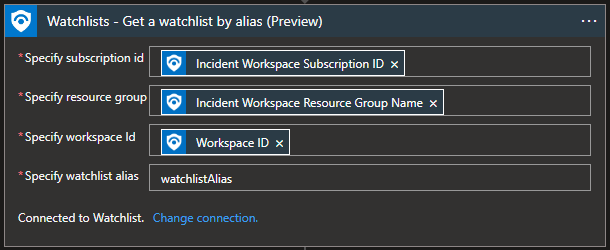
Watchlist - Get a watchlist by alias
Before we decide to create a watchlist in automation, we first need to ensure that there is no existing watchlist in the environment. “Get a watchlist by alias” will do just that. Status code 200 will mean that the watchlist is available. Status code 404 means that the watchlist is not available.
Example:
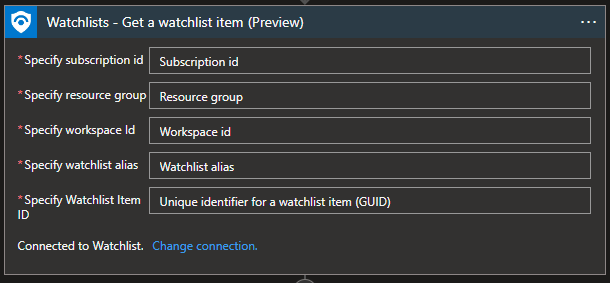
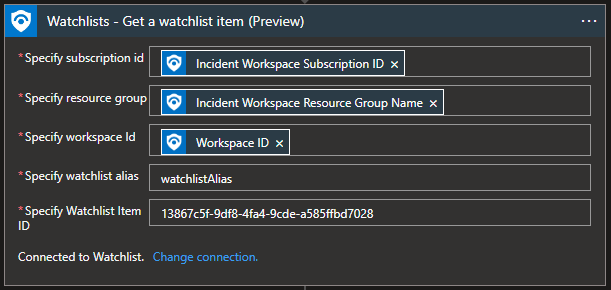
Watchlist - Get a watchlist item
“Get a watchlist item” will return a specific watchlist item using its GUID so that we can get all necessary information about that item from the watchlist.
Example:
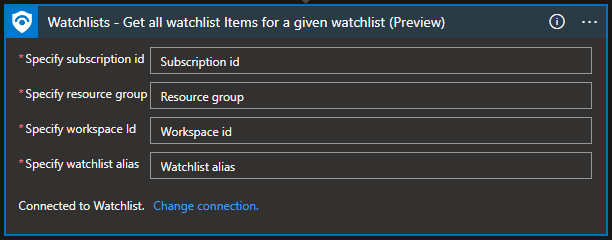
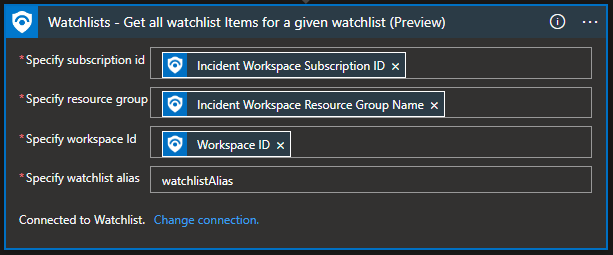
Watchlist – Get all watchlist items for a given watchlist
“Get all watchlist items for a given watchlist” will return us all watchlist items, and it can be helpful when we need to compare if an IP, user, or host is already part of the watchlist or not so that we do not create duplicates.
Example:
Sample Playbooks available with new watchlist actions
If you would like to evaluate new watchlist actions, we already have a few playbooks using these actions. You can access them using the official Microsoft Sentinel GitHub repo or the playbook Templates tab in Microsoft Sentinel.
- Update VIP User Watchlist using Azure AD Group
- Change Incident Severity and Title If User VIP
- Add IP to watchlist
- Add URL to watchlist
- Add user to watchlist
- Add host to watchlist
Please leave us feedback with watchlist and playbook use cases so that we can bring more content to you!