This post has been republished via RSS; it originally appeared at: Microsoft Tech Community - Latest Blogs - .
While creating Event Grid System Topic for specific resource type by using Terraform deployment, we may get following error message which indicates that we don’t sufficient permission upon target resource (for example, Storage Account resource type):
Error: eventgrid.SystemTopicsClient#CreateOrUpdate: Failure sending request: StatusCode=400 -- Original Error: Code='InvalidRequest' Message='The user does not have permission to perform the operation on the resource /subscriptions/***/resourceGroups/***/providers/Microsoft.Storage/storageAccounts/***.'
Or we may get following error message:
checking for presence of existing System Topic: (Name "***" / Resource Group "***"): eventgrid.SystemTopicsClient#Get: Failure responding to request: StatusCode=403 -- Original Error: autorest/azure: Service returned an error. Status=403 Code="AuthorizationFailed" Message="The client *** with object id ***' does not have authorization to perform action 'Microsoft.EventGrid/systemTopics/read' over scope '/subscriptions/***/resourceGroups/***/providers/Microsoft.EventGrid/systemTopics/*** or the scope is invalid. If access was recently granted, please refresh your credentials."
Or we will get following error message while creating event grid system topic in the azure portal:
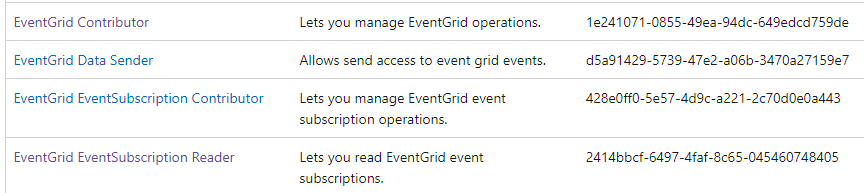
To solve these exceptions, please kindly make sure that EventGrid Contributor and EventGrid EventSubscription Contrinbutor(RBAC permission link) are granted to the client user or service principal object correctly.
- The EventGrid Contributor and EventGrid EventSubscription Contributor allow us to create/manage EventGrid resources and EventGrid EventSubscription resources. It’s used for control plane operation.
- The EventGrid Data Sender is used for data plane operation which allows us to send message into event grid topic. Meanwhile, EventGrid EventSubscription Reader role allows us to receive message/event from event subscriptions.
In addition, we don’t need to grant write permission of target resource provider to client user/service principal object while creating event grid system topic via ARM template or Terraform. Let’s say we are creating event grid system topic for Storage Account:
- The Storage Account Contributor role is not required for ARM template/Terraform deployments.
- However, it’s required while performing in the azure portal. The reason is we still need to list target Storage Account services over azure portal UI. Surely, you could remove the resource provider permission after creating Event Grid system topic due to original security(permission control) consideration.