This post has been republished via RSS; it originally appeared at: Microsoft Tech Community - Latest Blogs - .
Automate Defender for DevOps Recommendation Remediation
Logic Apps are a workflow automation feature of Microsoft Defender for Cloud (MDC) in which you can create and run automated workflows that integrate your apps, data, services, and systems. This blog walks through creating a Logic App that you can use to auto-remediate the Defender for DevOps Recommendation in MDC called “GitHub repositories should have Dependabot scanning enabled” by enabling Dependabot on a GitHub repo.
Security Operators will find this Logic App particularly useful because they do not need to be familiar with GitHub or login to GitHub to enable Dependabot scanning. Instead, SecOps can enable Dependabot open source dependency scanning remotely and on numerous repositories by using Logic App automation.
Objectives:
- Create a Logic App to enable Dependabot in GitHub
- Create a PAT Token and secure it in Azure Key Vault
- Test the Logic App
Prerequisites:
- Key Vault – for Personal Access Token secret
- Connector provisioned in MDC to your GitHub Source Code Management System
- Sample GitHub repository – with Dependabot disabled
Create a Logic App to enable Dependabot on a GitHub repo
- Login to Azure and search for or click Logic Apps
- Click + Add
- Choose a Subscription and Resource group
- Enter a name for your Logic App
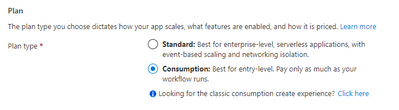
- Under Plan, choose Consumption
- Click Review + create
- Click Create
- Go to the Logic App you created and click Logic app designer in the left menu
- Click Blank Logic App
- In the search box, type Recommendation
Choose When a Microsoft Defender for Cloud Recommendation is created or triggered
- Click + New step
Type variable in the search box
Choose Initialize variable
For Name, type repo_name
For Type, choose String
- Click + New step
Type variable in the search box
Choose Initialize variable
For Name, type owner
For Type, choose String
- Click + New step
Type variable in the search box
Choose Set variable
For Name, choose repo_name from the dropdown menu
For Value, click in the empty box
In the Add dynamic content flyout, click Expression and type the following: first(skip(split(triggerBody()?['properties']?['resourceDetails']?['id'],'/'),12)) and click OK
- Click + New step
Type variable in the search box
Choose Set variable
For Name, choose owner from the dropdown menu
For Value, click in the empty box
In the Add dynamic content flyout, click Expression and type the following: first(skip(split(triggerBody()?['properties']?['resourceDetails']?['id'],'/'),10)) and click OK
For this Logic App to execute securely, you need a Personal Access Token (PAT) to use in the API request.
Follow the steps here in the GitHub documentation to create a PAT: https://docs.github.com/en/authentication/keeping-your-account-and-data-secure/creating-a-personal-access-token
Important: The PAT needs permissions to enable Dependabot—which requires Full control of private repositories
After you create a PAT, this should be stored in a Key Vault to keep it secure and accessible by the Logic App. Add the PAT as a secret to your Key Vault.
- Click Save on the Logic App canvas.
Navigate back to the Logic App
- Click Identity
On the System assigned tab, set status to On
Click Save, then Yes
Click Azure role assignments
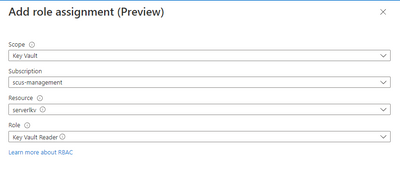
Click + Add role assignment
In Scope, choose Key Vault. In Subscription, choose the subscription with your Key Vault. In Resource, select the Key Vault. In Role, choose Key Vault Reader
Click Save
Navigate back to the Logic App
- Click Identity
On the System assigned tab, copy the Object (principal) ID
- Navigate to your Key Vault
Click Access policies
Click + Create
In the Secret permissions list, tick Get and List
Click Next
Paste the Object (principal) ID that you copied earlier in the Search by box
Click the Identity and click Next
Click Next, then click Create
Click Add, then click Save
Navigate back to the Logic App
- Click Edit to go to the Logic Apps Designer
- Click + New step
Type key vault in the search box
Choose Azure Key Vault, click Get secret
Click Connect with managed identity
Type a Connection name, then type your Key Vault name in the Vault name box
Click Create
Choose your secret from the Name of the secret dropdown list
- Click + New step
Type HTTP in the search box and click HTTP
In Method, choose PUT. In URI, type https://api.github.com/repos///vulnerability-alerts.
Put your cursor after repos/ and in the dynamic content click owner
Move after the next / and click repo_name from the dynamic content
In Headers, for Enter key type Accept and for Enter value type application/vnd.github+json
In Headers, for Enter key type Authorization and for Enter value type token <space> click Value in the dynamic content
Your HTTP step should now look like the following:
- Click Save to save the workflow
Your no code Logic App is now complete and needs to be tested.
Test the Logic App
- Navigate to Microsoft Defender for Cloud
- Click Recommendations
Expand Enable enhanced security features, click GitHub repositories should have Dependabot enabled
Expand Affected resources, tick a GitHub repository
Click Trigger logic app
- In the Selected subscription dropdown, choose the Subscription that contains the Logic App
Tick the box next to the Logic app
Click Trigger
Now let’s verify that Dependabot has been enabled
- Navigate to the GitHub repository that did not have Dependabot enabled
Click Settings
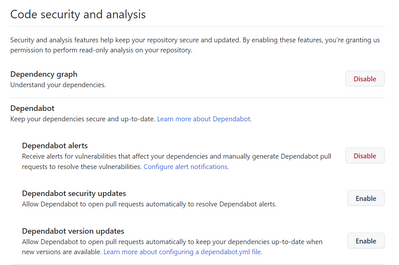
Click Code security and analysis
You should now see that Dependabot alerts is enabled
Conclusion
To review, we’ve walked through creating a Logic App to auto-remediate the MDC recommendation: “GitHub repositories should have Dependabot scanning enabled” by enabling Dependabot on a GitHub repo. This helps harden the security on your organization’s GitHub repositories and provides Security Operators with visibility into your organization’s open source dependencies via Dependabot scanning findings.
Additional Resources
- To learn more about Defender for DevOps, read this documentation
- Download (free) a special Appendix about Defender for DevOps from the latest Microsoft Defender for Cloud book published by Microsoft Press
- To learn how to onboard your GitHub Source Code Management System to Defender for Cloud, read this documentation for GitHub