This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Community Hub.
Reputation
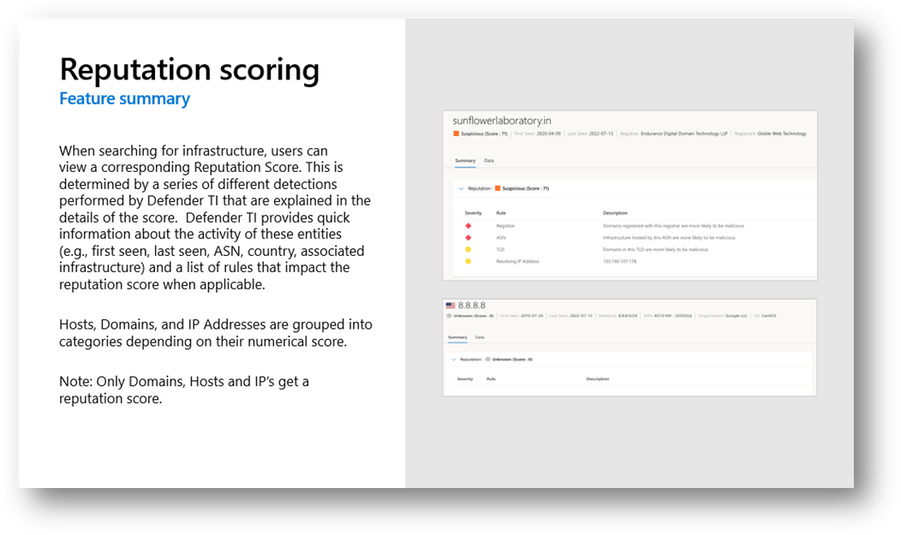
The power of machine learning models comes from the data that is used to train them, and Defender TI’s vast Internet telemetry is powering models that allow us to define the criteria that factor into reputation scores for IP addresses, domains, and hostnames across the Internet. These scores are meant to indicate the likelihood that the entity is associated with an elevated level of risk.
The factors that could influence reputation are dynamic. As our researchers and threat models continue to analyze the dynamic nature of threat infrastructure, including new tactics, techniques, or procedures that may play a part in infrastructure deployment, these rules are bound to update. Additionally, on top of the update of the actual rules in place, it is expected that the values that fall under a given rule are also subject to change. For example, one factor that has consistently contributed to reputation across time is the location where infrastructure is hosted. The list of locations may change over time, but the location factor itself will likely remain in place.
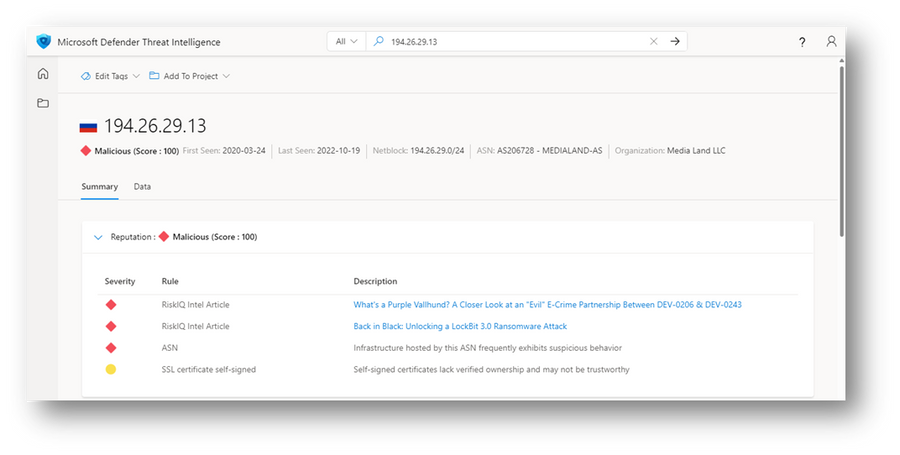
Check out the example below of a reputation returned for a specific IP address. Note that the criteria that play into the score are all listed out for transparency’s sake. Since the score is dynamic, if you search for this IP address yourself, you may see a different result if any machine learning models were updated. We will also frequently see indicators added to or dropped from blocklists, and since this is a factor in our score, sometimes the change in score will result simply from that.
Notice that one of the factors impacting the score in this screenshot is that the IP address in question appeared within a couple of Defender TI Intel Articles. For article indicators, this fact-of-impact to score will only apply for 90 days after the article is published.
Figure 1 - Reputation for an IP address
Figure 2 – Reputation scoring
Reputation scores range from 0 to 100; within that range are four buckets or classifications. Take a look at the examples below of scores falling into different buckets. Try to search for each indicator yourself within Defender TI and observe whether or not the same scores are observed.
|
LABEL |
SCORE RANGE |
SCORE DESCRIPTION |
EXAMPLE |
UNKNOWN
|
0-24 |
No match found. Machine learning may have returned one matched rule (displayed in the description), but it’s not a requirement. |
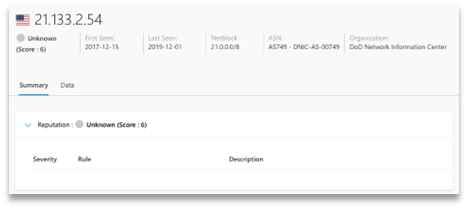 |
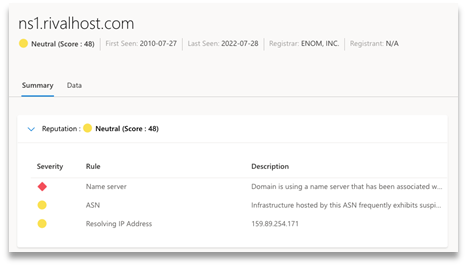
NEUTRAL |
25-49 |
No match found, but machine learning returned
|
 |
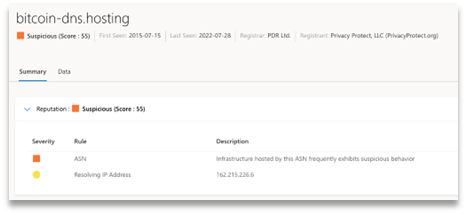
SUSPICIOUS |
50-74 |
No matches to the blocklist, but machine learning returned three or more matched rules (displayed in description).
|
 |
|
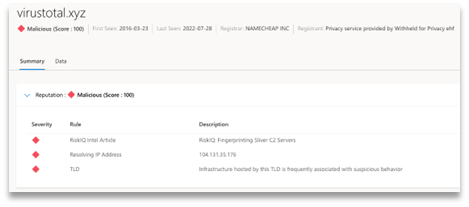
MALICIOUS |
75-100 |
Match found in our blocklist, and machine learning returned one or more matched rules (displayed in description).
|
 |
Analyst Insights
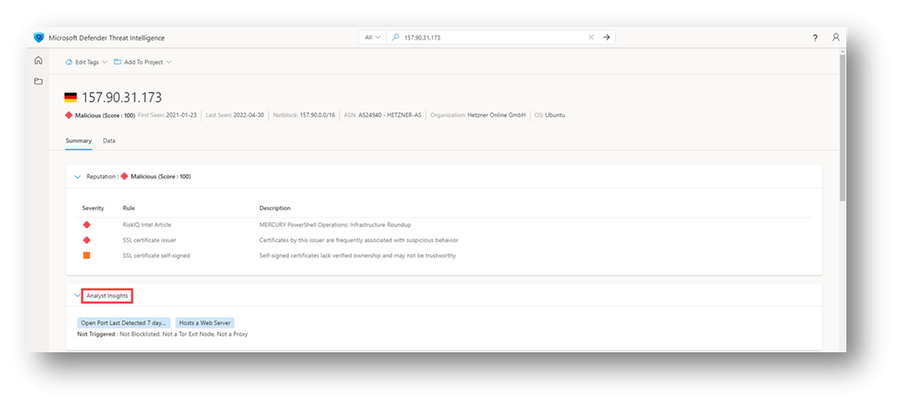
In Defender TI, the Analyst Insights section provides quick insights about the artifact that may help determine the next step in an investigation. This section will list any insights that apply to the artifact and those that do not apply for additional visibility. In the example below, we can quickly determine that the IP Address had an open port within the past seven days and hosts a web server. Furthermore, the system displays rules that were not triggered, which can be equally helpful when kickstarting an investigation.
Figure 3 – Analyst Insights for an IP address