This post has been republished via RSS; it originally appeared at: Intune Customer Success articles.
By Anya Novicheva, Product Manager | Microsoft Intune, and Jaye Ren, Product Manager | Microsoft Intune
We are excited to announce Just in Time (JIT) Registration for Setup Assistant with modern authentication for iOS/iPadOS devices that enroll through Apple’s Automated Device Enrollment (iOS/iPadOS 13+). This enrollment flow is an improvement to the Setup Assistant with modern authentication enrollment method since it no longer requires the Company Portal app for Azure Active Directory (Azure AD) registration or compliance checking. By removing the Company Portal requirement, we eliminated extraneous steps, removed required app downloads that can’t be changed, and put an end to switching between apps to get the device compliant, thereby streamlining the user flow.
With JIT Registration, once the user completes enrollment during Setup Assistant and lands on the home screen, the user authentication can be completed in any Microsoft Office application to register the device with Azure AD and kick off compliance. The compliance checks are integrated right into the Office app that is used for authentication, so the user doesn’t need to switch between multiple apps to understand the steps that they need to take to become compliant.
We are utilizing Apple's single sign-on (SSO) extension functionality to significantly minimize authentication prompts. The first authentication in Setup Assistant completes enrollment and establishes user device affinity while the next authentication handles Azure AD registration within a pre-authorized Office app. This ensures that SSO is fully established across the device. These authentications are all that are required to fully enroll the corporate device with Intune, register it with Azure AD, and ensure compliance on the device with a fully integrated compliance experience right within any Office app.
To set up JIT registration for ADE on the admin side, refer to the following information.
Setting up the admin-side configuration for JIT Registration for ADE
Important! Before you begin, make sure you exclude "Microsoft Intune" from any Conditional Access (CA) policy targeted at the devices enrolling with JIT Registration.
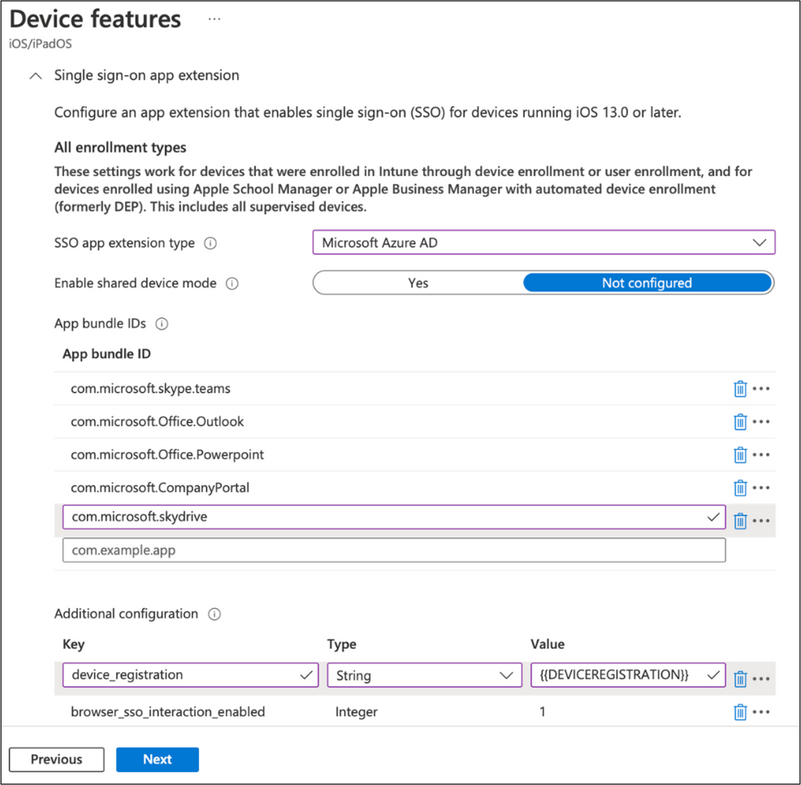
- Create a device configuration policy under Device features > Category > Single sign-on app extension. Refer to Single sign-on app extension for more information.
- Set the SSO app extension type to Microsoft Azure AD.
- Add all the App bundle IDs you want SSO to be established on.
- We recommend adding all Microsoft Office apps you want the SSO extension to apply to. The first sign in must go through an app that is configured with the SSO extension so that Azure AD registration can be completed. After that, the user will be signed into any app that’s part of the SSO extension policy.
- For example, if the user tries to sign into Outlook first but only Teams is added to the SSO extension, they will be blocked by Conditional Access. Only signing into Teams will kick off Azure AD registration with the SSO extension. Therefore, adding multiple Office apps to the SSO extension will ensure Azure AD registration regardless of which corporate managed, Office app the user signs into first.
- Add the required key value pair under the additional configuration.
- Key: device_registration
- Type: String
- Value: {{DEVICEREGISTRATION}}
- We recommend adding the key value pair that enables SSO within the Safari browser for all apps in the policy as well.
- Key: browser_sso_interaction_enabled
- Type: Integer
- Value: 1
- Specify the Microsoft Authenticator app as a required app and then assign it to a group. For instructions read, Add apps to Microsoft Intune and Assign apps to groups with Microsoft Intune.
- Within an active Intune ADE token from Apple Business Manager (ABM) or Apple School Manager (ASM), create the iOS/iPadOS ADE enrollment profile using the Setup Assistant with modern authentication method. Then, assign this enrollment profile to the devices that synced over from ABM/ASM. Refer to Automatically enroll iOS/iPadOS devices by using Apple's Automated Device Enrollment for more information.
Once these configuration steps are complete, the user will be able to complete setup and authentication on the device. They simply need to turn on the device, go through the Setup Assistant screens, and authenticate with their Azure AD credentials to fully enroll the device with Intune and establish user device affinity. When the user opens a managed Microsoft Office app that has an established SSO extension, the app automatically establishes SSO.
Here’s an example of the experience after a user has completed the enrollment in Setup Assistant and opens Microsoft Teams to start their work:
Note: The Company Portal is not required for a device to complete Azure AD registration or reach compliance. However, it may need to be installed to collect logs to aid in troubleshooting. We plan to remove this requirement in the future.
We hope you’re excited for this new experience and can’t wait to hear how it goes as you begin implementing it! If you have any questions or comments for the Intune team, reply to this post or reach out to @IntuneSuppTeam on Twitter.
