This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Community Hub.
Azure Policy is happy to introduce a new preview effect: DenyAction! Unlike other effects that focus on resource configurations, the denyAction effect will block requests based on intended action, regardless of user permissions. Today this new effect supports deletions, but it's set up to handle other types of actions in the future. With the at-scale power of Azure Policy and the ability to block delete calls, denyAction allows you to prevent accidental deletions of your critical resources.
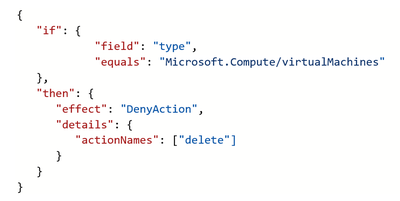
Sample denyAction definition that blocks delete calls on any virtual machines:
You are able to create these definitions in Portal or API. All denyAction definitions will have a compliance state of 'Not Started' during preview, and will introduce a new compliance state of 'Protected' for GA. Check out the documentation to learn more about how this effect works, and keep an eye out for the GA of this effect in the coming months!