This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Community Hub.
When it comes to managing IoT devices, security is of the utmost importance. But, you’d also rest easier if devices are secure without concern about manual certificate management. In this post, we'll show you a solution that streamlines IoT Edge certificate management using GlobalSign's IoT Edge Enroll EST service.
An analogy
Think of each IoT Edge device as a new driver, ready to hit the road and communicate with the IoT Hub. And like a new driver, each device needs its own set of credentials that need renewal. Here's how GlobalSign's EST service makes it a breeze:
- Birth Certificate: During manufacturing, each device is given a unique Initial Device Identifier (IDevID) certificate and private key (ideally, something like Trusted Computing Group’s (TCG) Trusted Platform Module’s (TPM) Endorsement Key (EK) certificates with factory burnt secured hardware backed private keys). This is like the device's birth certificate, proving its identity.
- Driver's License: When the device connects for the first time, it uses its IDevID to authenticate with GlobalSign for certificate signing request (CSR). In return, GlobalSign provides a short-lived Locally Significant Device Identifier (LDevID) certificate from a trusted root CA. This LDevID acts as the device's driver's license, allowing it to operate for some time. The LDevID serves as the device's unique identifier in IoT Hub, registered through Device Provisioning Service (DPS).
- Automatic Renewal: To make sure your devices never lose their communication privileges, IoT Edge automatically renews the LDevID certificates before expiration. Like a driver license renewal, but automated!
By using GlobalSign's EST service, you can enjoy secure and effortless certificate management for your IoT Edge devices. It's like having a personal assistant renewing your driver's license for you.
Give it a try to start streamlining your IoT Edge certificate management.
Prerequisites
- An IoT hub and Device Provisioning Service linked to it.
- A GlobalSign demo account:
- Sign up for Test Your Azure IoT Edge PoC with live device certificates from GlobalSign's IoT Edge Enroll.
- You'll receive an email with details for your EST server endpoint within a few days, including three endpoints (IDevID, LDevID, and Edge CA).
- Reply to the GlobalSign contact and ask to:
- Enable X.509 authentication (mTLS) for both the LDevID and the Edge CA endpoints
- Turn off “re-enrollment forcing” (the default behavior with GlobalSign IoT Edge Enroll is that it notices that a previously issued certificate was presented and "upgrade" the request to the reenrollment workflow. This overrides the subject CN to be the same as the previously issued certificate. Typically, customers would use a separate CA for the bootstrap/idevid, so in practice this outcome usually wouldn't be seen. But for simplicity of this post, it’s easier to ask GlobalSign to respect the certificate signing request (CSR) and not perform the “upgrade”).
- Linux machine, VM, or device with IoT Edge installed:
- Don't provision the IoT Edge device identity.
Create the IDevID
In this section, we create the IDevID certificate, which serves as the device's birth certificate. It’s a one-time process that occurs during device manufacturing, and ensures that the initial secret value for first-time authentication to GlobalSign never leaves the factory. Later, when the device wakes up, it will use the IDevID certificate to get a driver's license, or the LDevID certificate.
- On your local machine or SSH into the IoT Edge device, create directories to store certificates and private keys for IoT Edge and assign ownership of these directories to the "aziotcs" certificate service and "aziotks" key service.
- Retrieve the GlobalSign demo root CA certificate with curl and convert it to PEM format using openssl. This certificate serves as the common root of trust between IoT Edge, GlobalSign, and DPS (and thus IoT Hub).
- Use openssl to create a new private key and certificate signing request (CSR).
- Send the CSR to GlobalSign's simple enroll EST endpoint using curl, to obtain the IDevID certificate that is signed with the root CA and paired with the private key created earlier.
- Move the certificates and private keys to the directories you created earlier, and give the IoT Edge certificate and key services the appropriate permissions to the PEM files and directories.
- Use the ls command to verify that the files are in place with the proper permissions and match the expected values.
Prepare DPS for provisioning
Here's how to get DPS ready for device provisioning:
- If you haven’t already done so, create an IoT hub and DPS, then link them together.
- Go to the DPS instance in Azure portal, then select Certificates > Add.
- In the pop-up, select your GlobalSign EST root CA certificate. You can use SFTP, VS Code Remote Extension to copy it from the IoT Edge device, or use curl to get it again.
- Select Set certificate status to verified on upload so that you can skip proof-of-possession.
- Click Save.
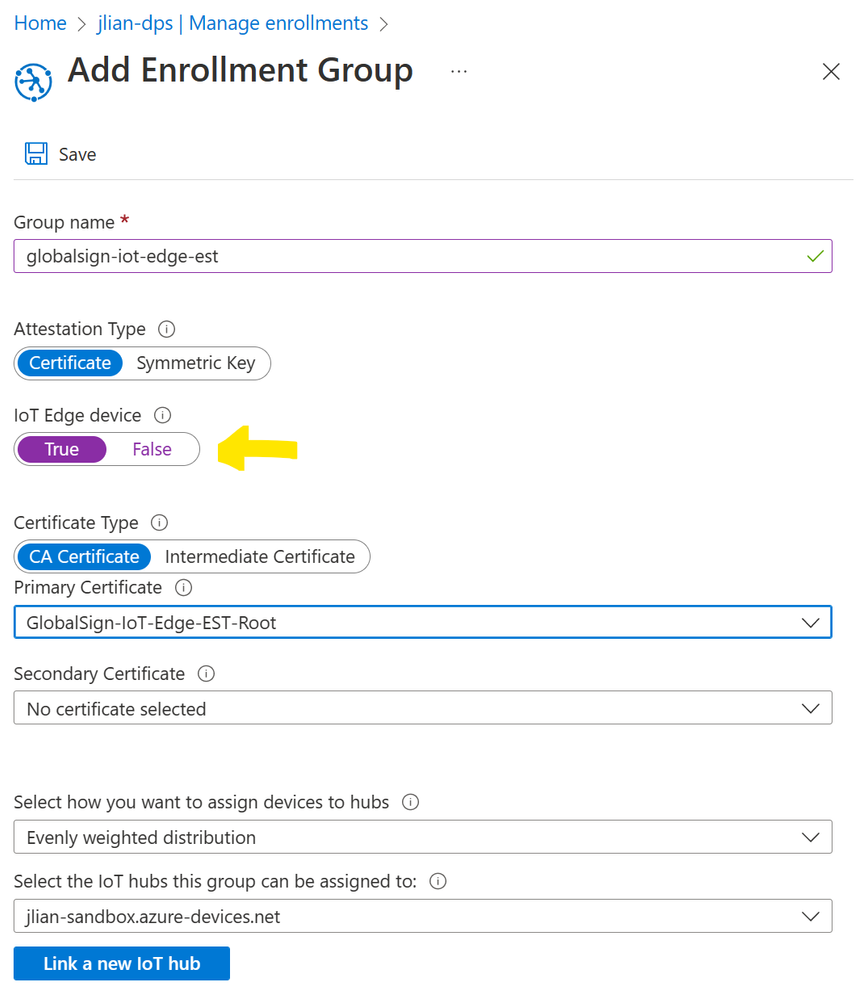
- Create a DPS enrollment group. Make sure attestation type is set to Certificate, IoT Edge device is set to True, certificate type is set to CA Certificate, and the root CA you just uploaded is set as the Primary Certificate.
Now, your DPS is ready to provision the IoT Edge device when it wakes up, using the root CA certificate as the trusted source of authentication.
Configure and start the IoT Edge device
In this section, we set up the IoT Edge device with its birth certificate (IDevID) to communicate with the GlobalSign EST server and receive its driver license (LDevID). The LDevID allows the device to talk to DPS and get the proper authorization for communication with IoT Hub.
- On the IoT Edge device, create a config file config.toml. Replace marked parameters with details from your GlobalSign account and DPS.
This config.toml file sets up the IoT Edge device to communicate with the EST server, which issues the LDevID (the device's license plate), and the Edge CA.
It starts by setting the GlobalSign root CA as the trusted root certificate. The file then sets up authentication to EST using the IDevID cert and private key.
Next, it sets up the IoT Edge device's connection to the DPS with X.509 certificate. The ID scope from your DPS is entered into the file. The device ID is set up to be registered with the registration ID "my-device-id".
The file then sets up the process for the IoT Edge device to obtain the LDevID and Edge CA certificates from EST. Both LDevID and Edge CA certificates will be automatically renewed with a specified threshold and retry rate if needed.
The settings for auto-renewal are specified with threshold and retry rates to 80% and 4% respectively.
- Copy the file over as root and apply configuration with iotedge config apply. This also starts the IoT Edge device.
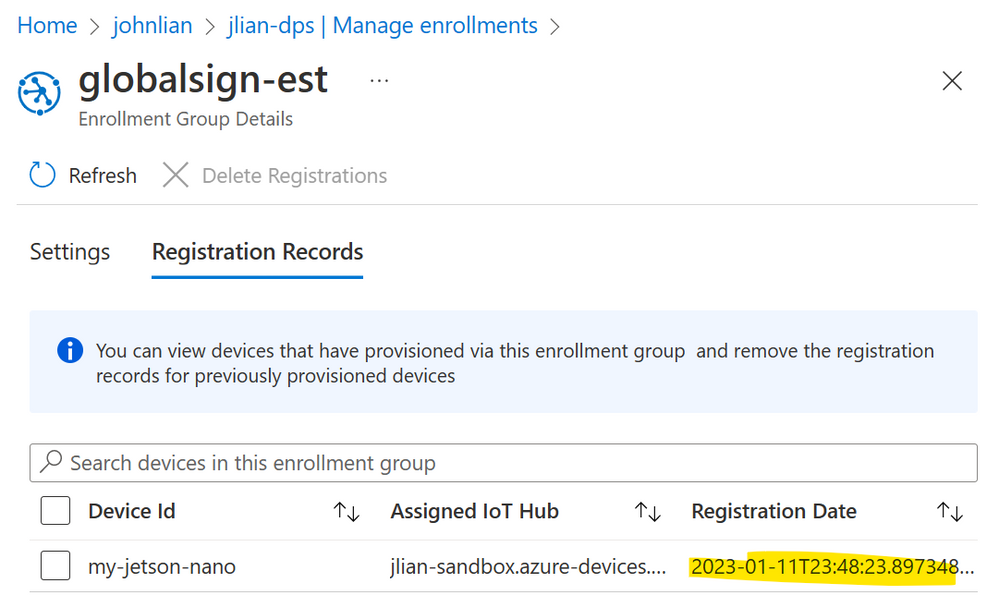
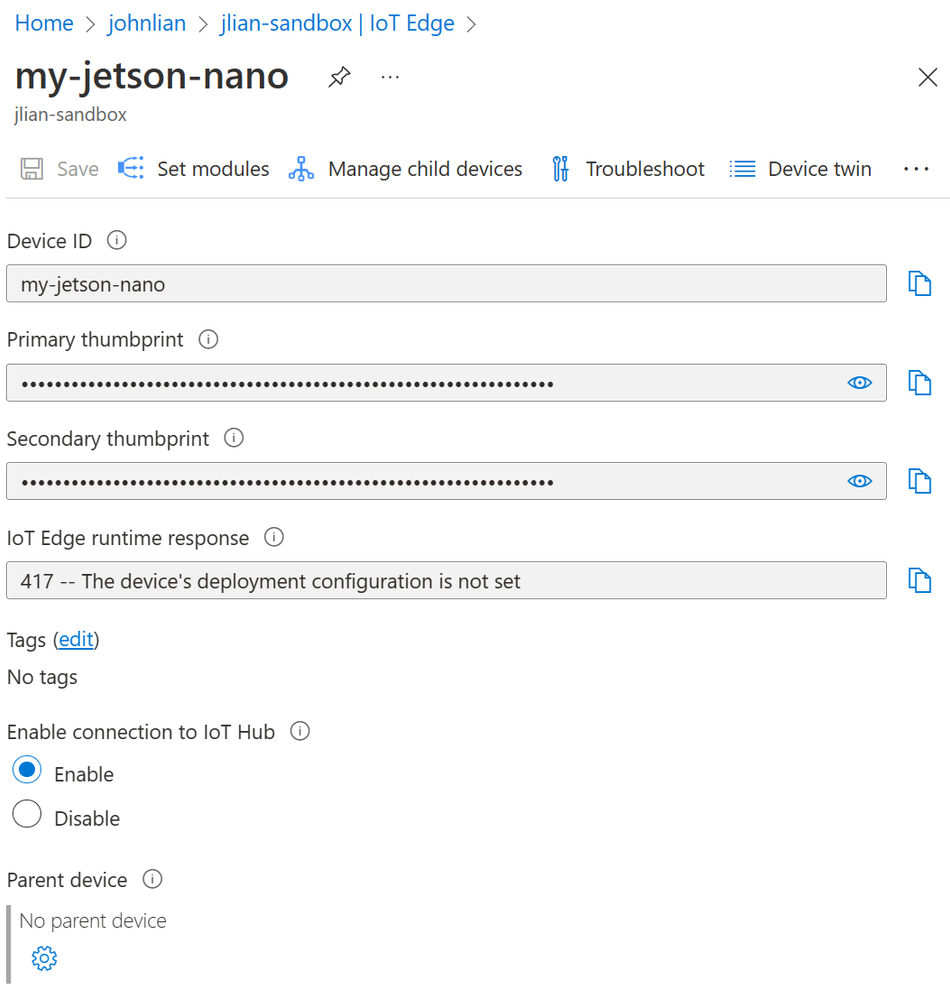
- Verify that the configuration was successful by using the iotedge check command. You should see successful checks on the connection with DPS and the status of certificates and keys. You can also check in your DPS Enrollment Group > Registration Records or IoT Hub to see that the IoT Edge device is registered (shown below). sudo iotedge check
Note: if you haven’t configured an IoT Edge deployment, you might see an error about edgeHub container being missing in iotedge check and a 417 in IoT Hub. That’s normal until you add the deployment via Set modules.
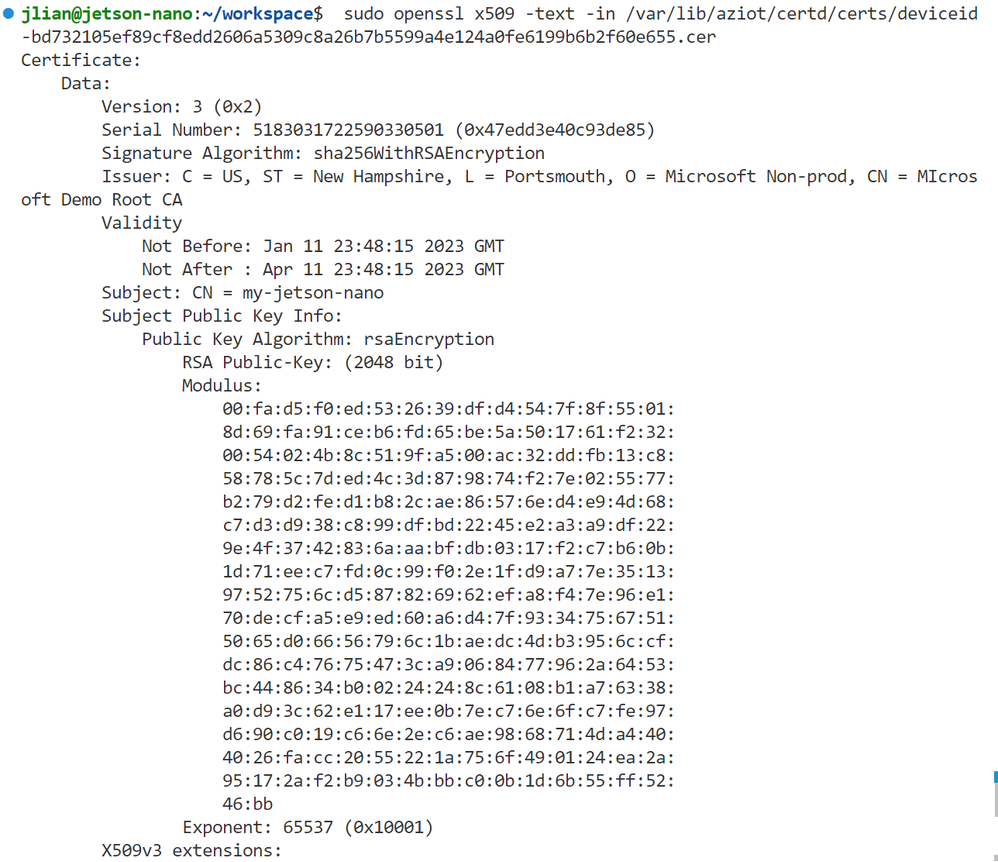
- On the device, check the new certificates from the EST server. In the "/var/lib/aziot/certd/certs" directory, you should see three different certificates starting with "estid", "aziotedgeca", and "deviceid". Use OpenSSL to inspect them. Note: the certificate names are randomly generated, use "ls" to find their names and paste them into the OpenSSL command.
That’s it! When the time (80% to expiration) comes, IoT Edge will automatically renew both the device ID and the Edge CA certificates without manual intervention.
Simplify IoT Edge security
This blog showed how to configure IoT Edge devices for secure communication using X.509 certificates without the need for manual certificate management. By using this approach, organizations can securely and efficiently manage their IoT Edge devices at scale, streamlining device enrollment and reducing the risk of security breaches.
To adapt the example to fit your needs, consider the following:
- Security level: Your security requirements may vary based on your use case. Consider whether a unique IDevID certificate per device is necessary or if sharing the same certificate among multiple devices is acceptable. It's important to never store the initial EST secret value on the device in plaintext.
- Comprehensive security: For a more robust security approach, refer to The blueprint to securely solve the elusive zero-touch provisioning of IoT devices at scale | Azure Blog and Updates | Microsoft Azure
- Dev/test scenarios: IoT Edge also supports basic authentication (username/password) for EST servers.
To restart
If you need to restart midway through, stop the IoT Edge service first, delete any certificates and keys that were generated, reapply the config, and restart IoT Edge.