This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Community Hub.
Chapter 2
- Bicep Development Environment
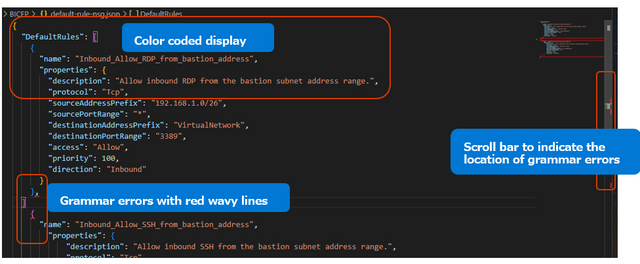
Bicep is a language. You will need an editor to write the language and an environment to run it.
Required
Visual Studio Code
reference: Deploy Bicep files from Visual Studio Code
Azure CLI or Azure PowerShell
reference: How to deploy resources with Bicep and Azure CLI
Deploy resources with Bicep and Azure PowerShell
!! The bicep file can be run from Visual Studio Code, so if you have VS Code installed, you do not need a command line.
Recommend
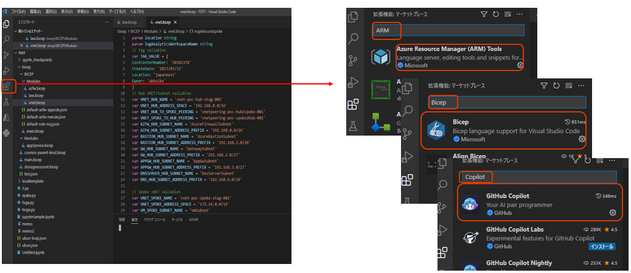
Visual Studio Code Extension
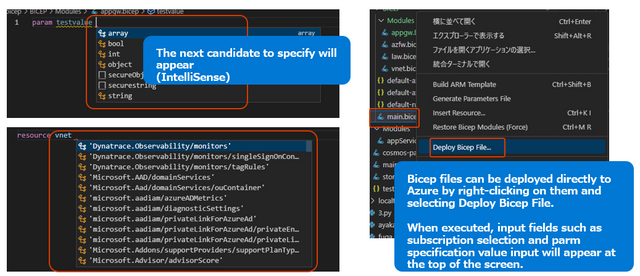
A feature called IntelliSense is useful. While you are coding in bicep, a pull-down pop up with options for the next candidate function, API version, etc. GitHub Copilot can also be used as an extension to make your work more efficient. (OpenAI Technology)
GitHub Account
Use it as a repository for bicep files.
- Tips
Install extensions from VS Code-- Only GitHub Copilot is available for a fee.
Azure Resource manager Tools Extensions
Bicep Extensions
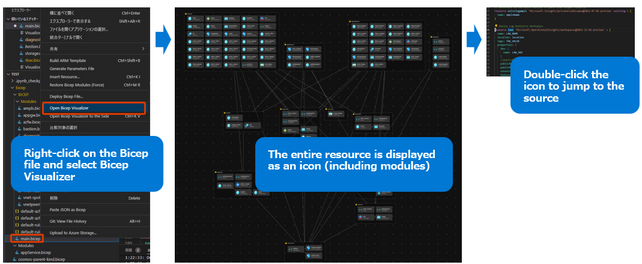
Bicep Visualizer
GitHub Copilot - Sample code and explanation
localtemplate/bicep/BICEP at master · akkoike/localtemplate (github.com)
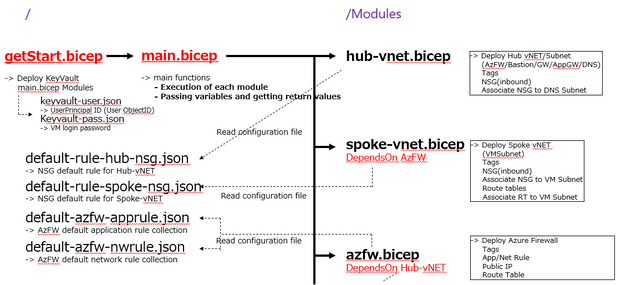
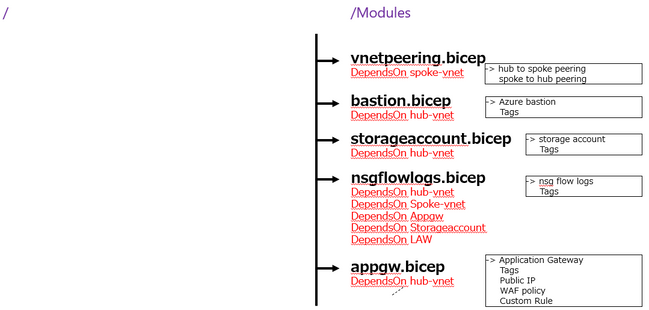
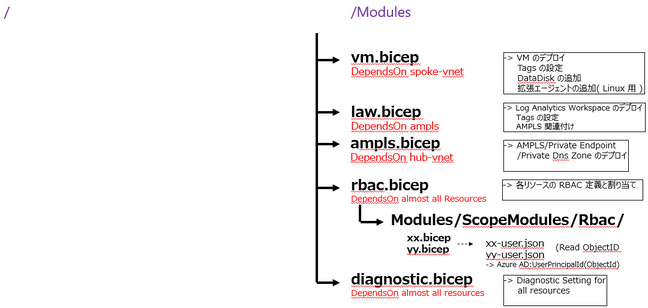
- Application sequence mapping
Based on vNET Hub&Spoke environment. Frequently updated settings were individually defined in JSON configuration files. Azure KeyVault was created first because I wanted to obtain a secure password using the getSecret function. RBAC and Diagnostic Setting are done at the end of the process for extended functions. NSG rules and Azure Firewall ruleset basically stated only the targets that should be allowed. All external communication from Azure VM is configured with a default route through Azure Firewall. Only Log Analytics with AMPLS may not work properly.
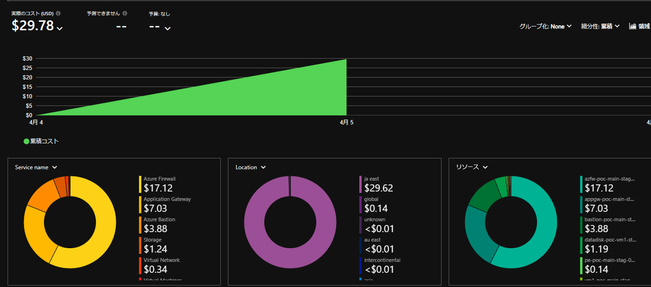
Almost 30 USD / day
>> Next Chapter (Traps and Avoidance)