This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Community Hub.
Microsoft Defender External Attack Surface Management (Defender EASM) discovers and classifies assets and workloads across your organization's digital presence to enable teams to understand and prioritize exposed weaknesses in cloud, SaaS, and IaaS resources to strengthen security posture. Features recently added boost usability and enable exciting new ways for customers to leverage their inventory data and critical security insights derived from their organization's assets and workloads. Below, learn about these powerful new enhancements and how you can begin using them today.
New Features
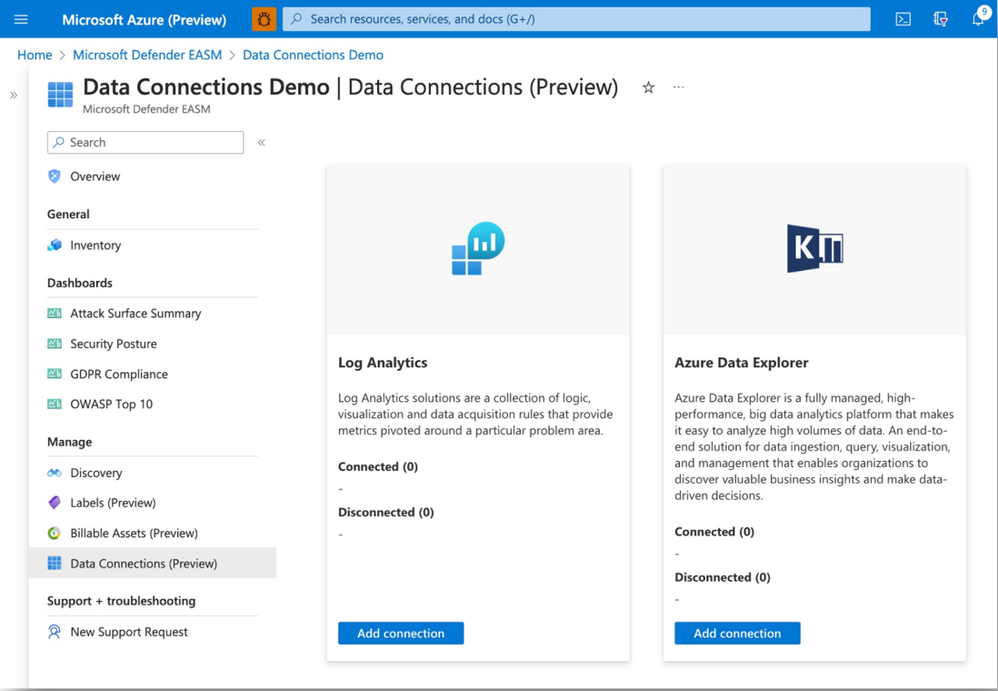
Data Connections
Defender EASM now offers data connections to help users seamlessly integrate their attack surface data into other Microsoft solutions to supplement existing workflows with new insights. The data connector sends asset data to two different platforms: Microsoft Log Analytics and Azure Data Explorer. Users need to be active customers to export Defender EASM data to either tool, and data connections are subject to the pricing model of each respective platform. Data connections can support large exports – more than 100 million assets a day.
Read more about the Data Connector here>
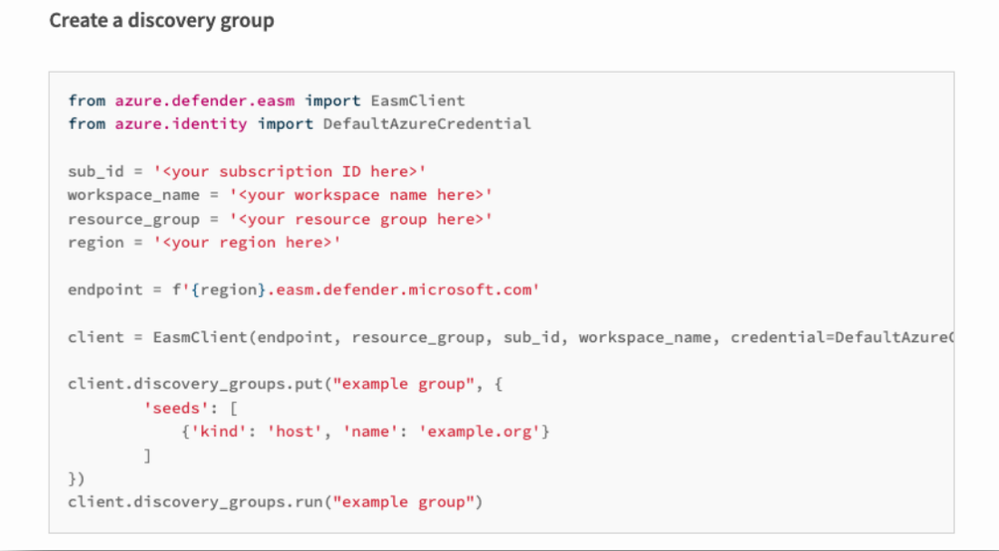
Software Development Kit (SDK)
Customers can now access a client library for Python that helps them operationalize the Defender EASM REST API to automate processes and improve workflows. The SDK is now available to customers in Public Preview.
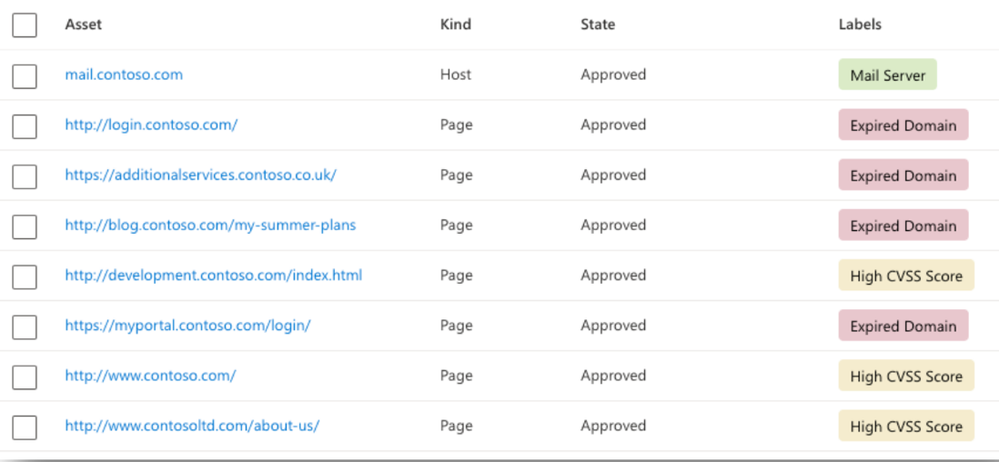
Asset Labels
Labels help you organize your attack surface and apply business context in a highly customizable way; you can apply any text label to any asset, allowing you to group assets and better operationalize your inventory.
Common labeling of assets includes:
- Assets from a merger or acquisition
- Require compliance monitoring
- Owned by a specific business unit in their organization
- Impacted by a specific vulnerability that requires mitigation
- Relate to a particular brand owned by the organization
- Added to inventory within a specific time range
Key Enhancements
REST API: The Defender EASM REST API lets customers manage their attack surface at scale. Users can leverage Defender EASM data to automate workflows by integrating into existing processes or creating new applications and clients. Recent updates include implemented validation checks & error responses, critical contextual information contained in response when retrieving task data (e.g., task ID, timestamps), and "groupBy" and "segmentBy" fields for asset details and summaries.
Regional Expansion: The "westeurope" region is now supported by Defender EASM. Currently supported regions:
- southcentralus
- eastus
- australiaeast
- westus3
- swedencentral
- eastasia
- japaneast
- westeurope
Latest Updated chart timestamps: Dashboard charts now have a "Last updated" timestamp that indicates the time the chart data was last refreshed. This transparency helps customers understand the freshness of the presented data. The timestamp is localized to the user's time zone.
Inventory sorting: Users can now sort most Defender EASM data by table columns. By clicking on the applicable column header name, users can choose for their data to ascend or descend by the selected value. Sorting is supported on both the Inventory page and Chart drill-downs displaying the assets comprising a count on a dashboard chart. Both pages support sorting by the "Asset" (name), "Kind," "First Seen," and "Last Seen" column values.
CVEs: Users can now filter host, IP address, and page assets by CVE ID. All CVEs in Defender EASM are now hyperlinked to the Defender Threat Intelligence Community portal, where you can obtain additional data. We now display CVE information by CVSS 2.0 and 3.x scores - all visible on the Asset Details page and dashboards.
Other Chart Enhancements:
- Billable asset chart: The marker ticks on the vertical axis indicating asset counts are now easier to interpret.
- SSL certificate CNAME added to dashboards: CNAMES have been added to all dashboard charts that pertain to SSL certificate information.
- "Securing the Cloud" columns added in the drill-down view for "Securing the Cloud" dashboard charts, users will now see a new column for the "Last Seen" value, indicating when our detection system last observed an asset.
CVSS v2.0 and CVSS 3.x breakdown in Charts:
We now display CVE information by CVSS 2.0 and 3.x scores. This is visible on the Asset Details page, as well as on dashboards:
New Attack Surface Insights:
- CVE-2019-15846 - Exim SNI Unauthenticated Remote Command Execution Vulnerability
- CVE-2022-47986 - IBM Aspera Faspex Unauthenticated Remote Code Execution
- CVE-2023-21745 - Microsoft Exchange Server Authenticated Privilege Escalation and Code Execution
- CVE-2023-21529 - Microsoft Exchange Server Authenticated Remote Code Execution
- CVE-2023-27898 - Jenkins Unauthenticated XSS to Remote Code Execution
- CVE-2023-20025 - Cisco Small Business RV Routers Unauthenticated Remote Command Execution
- (Non-CVE) Telnet Service Exposure Exim 21Nails Multiple Vulnerabilities
- (Non-CVE) Elementor Pro for WordPress Authenticated Privilege Escalation if Installed with WooCommerce
Potential Insights
Potential Insights are created when a vulnerable version of software has not been detected and needs to be validated by the customer. Customers using this software should check if they have the vulnerable versions highlighted in the insight:
- CVE-2022-44877 - CentOS Web Panel Unauthenticated Remote Code Execution
- CVE-2022-47966 - Zoho ManageEngine Products Unauthenticated SAML XML Remote Command Execution
- CVE-2022-24637 - Open Web Analytics Unauthenticated Remote Code Execution [Potential] CVE-2021-44529 - Ivanti Cloud Services Appliance Unauthenticated Command Injection
- CVE-2022-31702 VMware vRealize Network Insight Command Injection
- CVE-2022-31706 VMware vRealize Log Insight Unauthenticated Remote Code Execution
- CVE-2023-0669 - GoAnywhere MFT Unauthenticated Remote Code Execution via Deserialization in Licensing Service
- CVE-2023-27532 Veeam Backup Unauthenticated Credential Disclosure
- CVE-2023-26359 - Adobe ColdFusion Arbitrary File Read and Unauthenticated Remote Code Execution Non-CVE Insights |
We want to hear from you!
MDEASM is made by security professionals for security professionals. Join our community of security pros and experts to provide product feedback and suggestions and start conversations about how MDEASM helps you manage your attack surface and strengthen your security posture. With an open dialogue, we can create a safer internet together.