This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Community Hub.
Introduction
This article is a continuation of Microsoft Defender PoC Series which provides you guidelines on how to perform a proof of concept for a specific Microsoft Defender plan. For a more holistic approach where you need to validate Microsoft Defender for Cloud, please read How to Effectively Perform an Microsoft Defender for Cloud PoC article.
There are two DevOps platforms currently covered by Defender for DevOps- GitHub and Azure DevOps. This article will go into detail about Azure DevOps Services.
If you'd like to also learn about the GitHub connector with Microsoft Defender for DevOps, then check out this article here.
Importance of Defender for DevOps
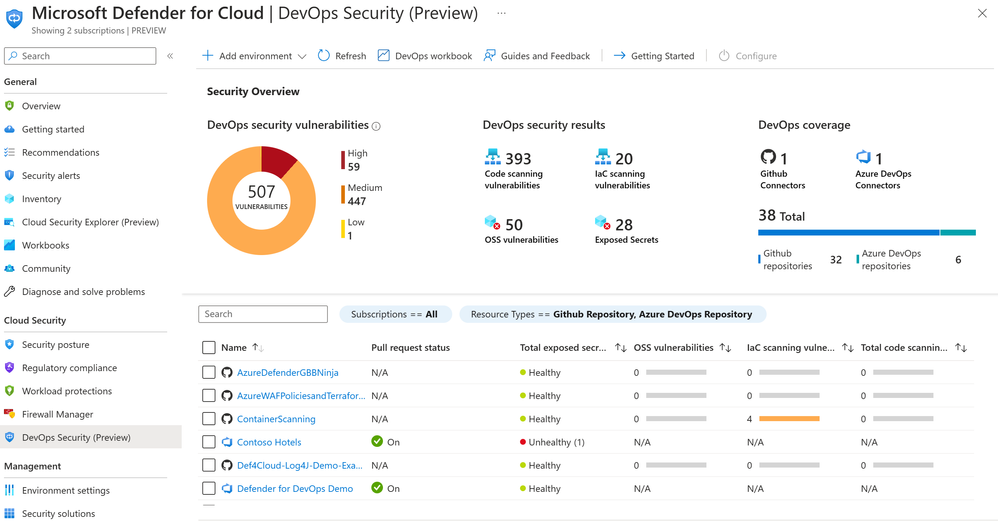
Microsoft Defender for DevOps with Azure DevOps provides security teams with visibility into the security posture of their Azure DevOps environments, while also giving developers and DevOps teams a simplified remediation experience for pre-production vulnerabilities and misconfigurations.
With Defender for DevOps, security administrators get full visibility in a single view from DevOps inventory and the security posture of pre-production application code. Based on the Microsoft Security DevOps extension, you can leverage a collection of static analysis tools to scan code for security issues in Azure DevOps using Azure Pipelines. These static analysis tools include ESLint which scans Javascript code for security issues, Bandit for scanning Python code, Infrastructure as Code (IaC) scanning for Terraform (among others) using Terrascan, IaC scanning for ARM and Bicep files using Template Analyzer, and AntiMalware scanning on Windows agents from Windows Defender (not open source, and requires Windows Defender to be enabled on the Windows agent in order to run). See more here.
Teams can gather comprehensive code to cloud contextual insights within Defender for Cloud. Security admins can also help developers prioritize critical code fixes with Pull Request annotations.
Planning & Pre-Requisites
To start a POC (proof of concept) for Microsoft Defender for DevOps, you need to have the correct setup in Azure DevOps and in Microsoft Defender for Cloud.
Create an Azure DevOps Trial subscription in the same tenant as your Azure subscription where you use Microsoft Defender for Cloud. See here.
Then create an organization in Azure DevOps.
Next, you need to have the necessary permissions:
- Project Collection Admin role enabled in Azure DevOps in order to enable the connector from within Azure DevOps, as here.
- Admin privileges in order to enable the Microsoft Security DevOps extension (the Microsoft Security Devops extension installs all the security scanning tools) as per here
- Defender for Cloud permissions here (Defender for DevOps specific):
- Azure Account- with permissions to sign into Azure portal
- Contributor role- on the relevant Azure subscription
- Security Administrator role- on the relevant subscription
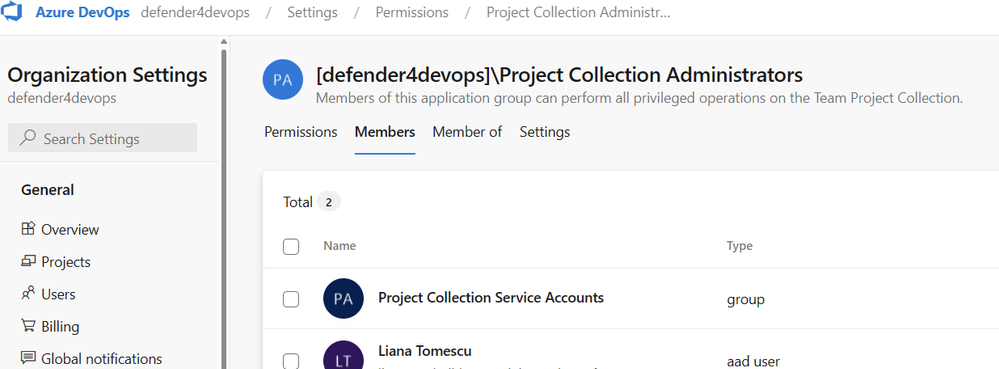
- OAuth enabled in the Azure DevOps Organization Settings, which you can find by looking at the Organization Settings in Azure DevOps as shown the image below.
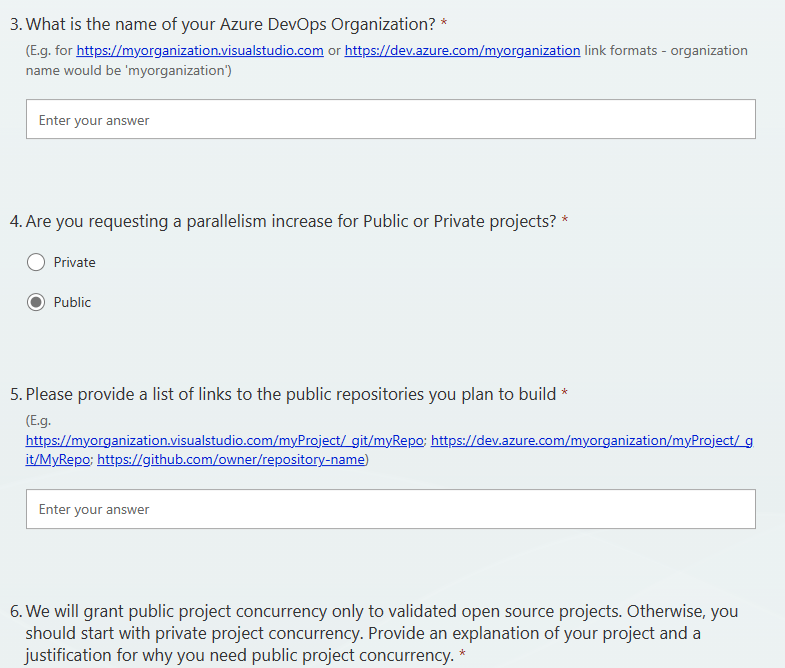
- If you are using the free version of Azure DevOps and you're trying to execute a pipeline, you will receive an error message when trying to execute the pipeline. This message will ask you to visit here and request increased parallelism in Azure DevOps. This can take 2-4 days.
If you don’t want to wait this time, or your PoC schedule can’t afford this time, an alternative to create a pipeline is by using a Hosted Build Agent, which you can do by following these steps.
Preparation
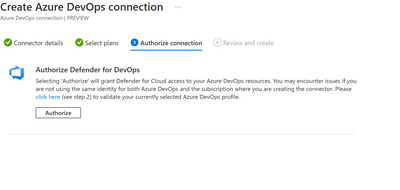
For beginning the preparation of the POC, you will need to first create the Azure DevOps connector in Microsoft Defender for Cloud. Follow the guidance for enabling the Azure DevOps connector in Microsoft Defender for Cloud to authorize the connection.
Note: You will need to have an Azure subscription and Azure DevOps organization in the same tenant to enable the Azure DevOps connector in Microsoft Defender for Cloud. Follow the guidance here to create a new organization in Azure DevOps. See the troubleshooting guide here.
Then, switch over to Azure DevOps, by going to https://dev.azure.com/ .
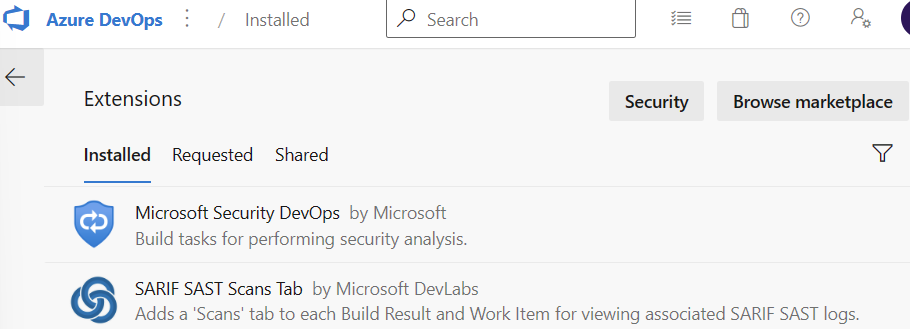
You will need to enable two extensions in Azure DevOps- the Microsoft Security DevOps extension to run the security scans, and the SARIF SAST Scans Tab extension to view the results of the Security DevOps extension in simplified manner in a new tab in the Azure DevOps build results.
Next in the Azure DevOps organization, you should create a new Azure DevOps project.
Then, you’ll be installing a new empty Git repository in that ADO project, which should include some sample code that you want to test.
The two Microsoft Defender for DevOps extensions in Azure DevOps.
You can run security scans via the Security DevOps extension on the Azure pipeline builds. For this reason, you need to configure a pipeline using YAML code. You can follow the guidance to create a new pipeline and to include the required YAML code to the Microsoft Security DevOps task and the dotnet dependencies here. This includes the yaml code with the necessary tasks for the build to run with the security scans.
Note: In the yaml file, if you would like to break the build from succeeding if any security scanning tool in the Security DevOps extension has found issues in the Build, then include the necessary category and break: true to the Security DevOps task in the yaml file. Here is an example of a configuration that will break the build if a secret is detected by Microsoft Security DevOps.
Note: There are dotnet dependencies when using the Microsoft Security DevOps task if using a self-hosted agent to be included in the yaml (see the docs here or the Github lab 14). The dotnet dependencies are not required if using the default Azure DevOps agents of windows-latest or ubuntu-latest.
Implementation and Validation
In order to validate the implementation was successful for Azure DevOps, developers can run the Azure Pipelines with the Microsoft Security DevOps extension as above, and see the security scan results during the Azure pipeline build runs. Your security team can manage secrets, code scanning findings and infrastructure as code findings found in Azure DevOps directly from Microsoft Defender for Cloud. The other validation in Azure DevOps for developers involves seeing secrets at the pull request stage as pull request annotations, before they’re merged into the main branch, usually the main/master repository.
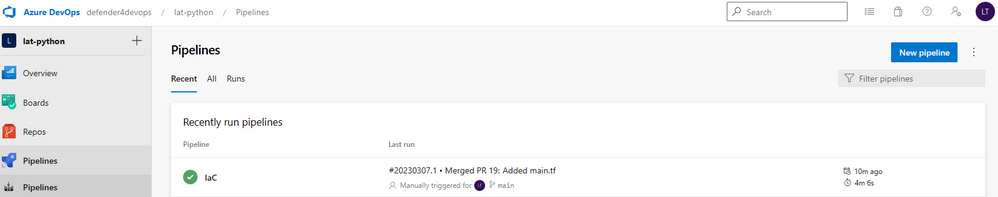
For DevOps teams, it’s useful for them to be able to see the security scan results, such as secrets, during the Azure pipeline build runs, as they are used to interacting in Azure DevOps. To validate this, go to the Pipelines in Azure DevOps.
Select your pipeline that you enabled with the Security DevOps extension, and click Run pipeline.
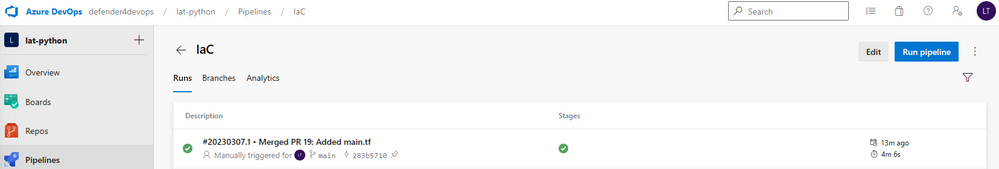
After a few minutes, you will see if your run has succeeded or failed.
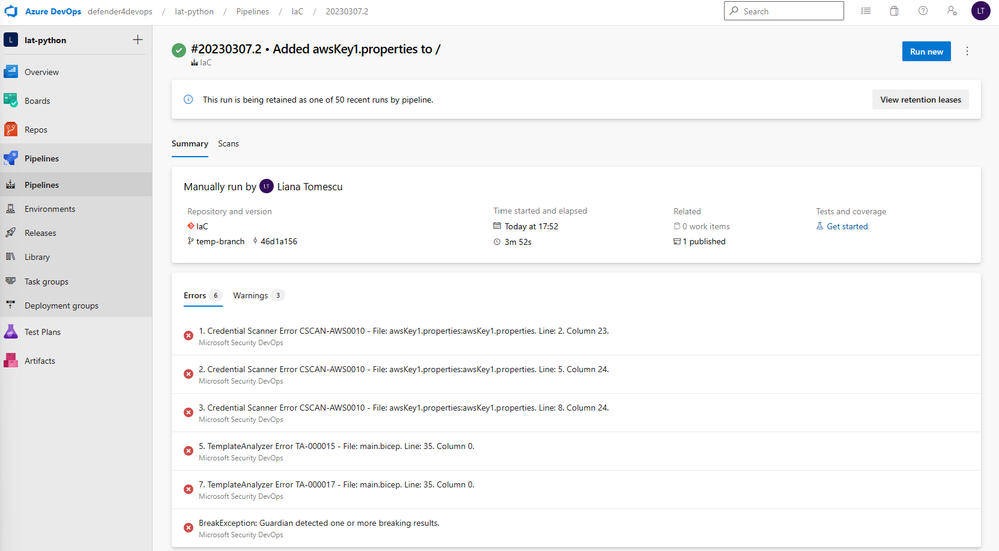
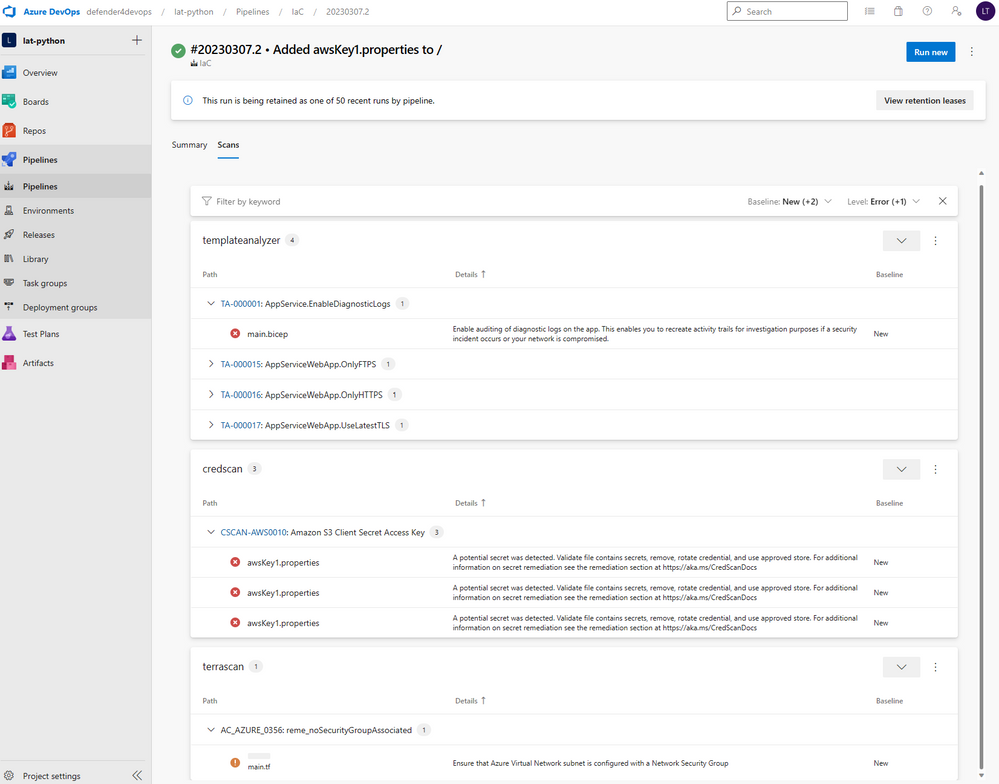
Click on the pipeline run, and see the Summary of the run. Notice the Errors tab and the Warnings tab, which include security issues found in the repo.
Beside Summary, go to the Scans tab, which appears due to the SARIF SANS Scans Tab extension you enabled. This scans tab will show the security scan findings per scanning tools.
This is one view of the security scans that your developers can see from Azure DevOps.
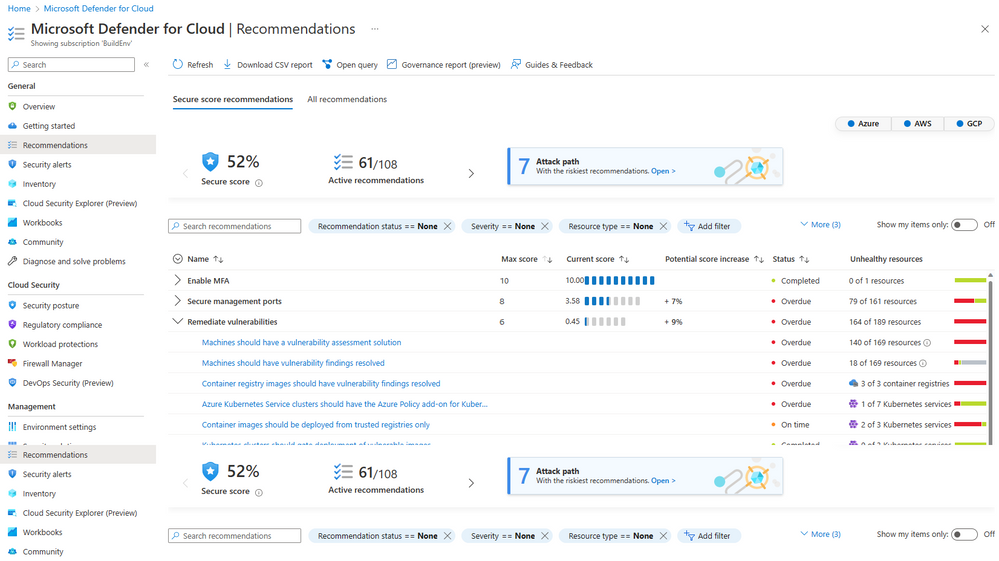
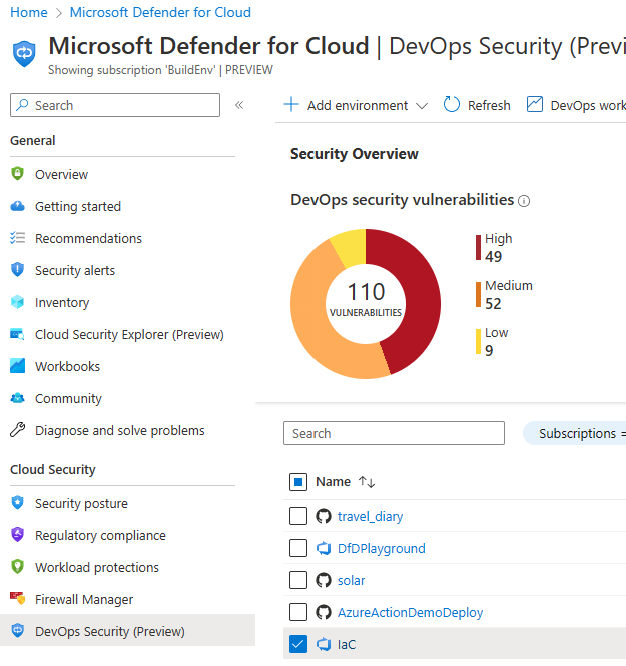
However, Defender for DevOps crucially allows customers to manage the secrets, code scanning finding results and infrastructure as code findings found in Azure DevOps directly from Microsoft Defender for Cloud. This means that your security team can view these ADO security issues across the Azure DevOps organizations, projects and repos from one centralised location of Microsoft Defender for Cloud. To see the credentials in Microsoft Defender for Cloud, go to the portal.azure.com and to Microsoft Defender for Cloud.
Go to Recommendations.
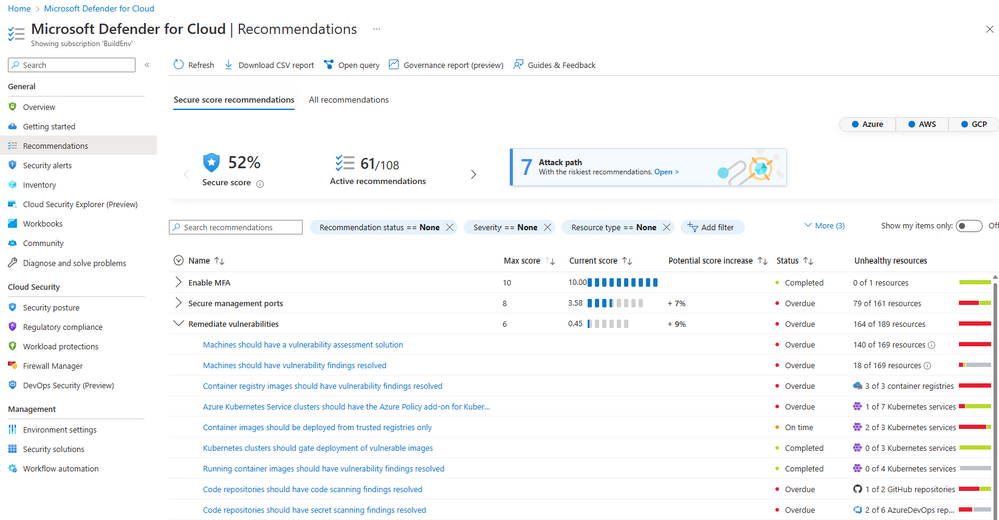
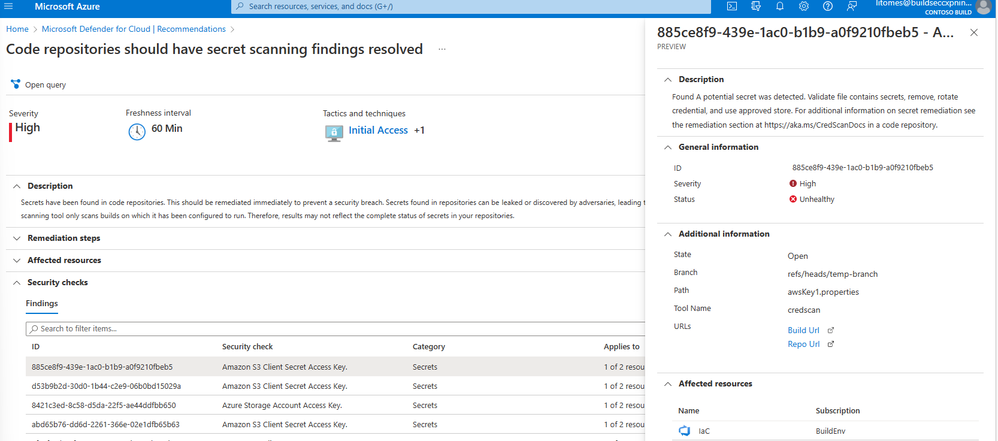
Under Remediate vulnerabilities, select the recommendation Code repositories should have secret scanning findings resolved.
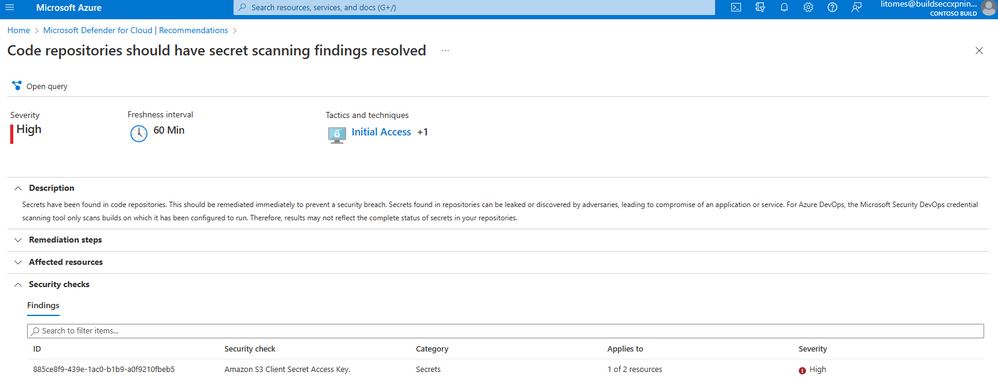
See the secrets found under Findings.
Select the secret to get more information about it, including the Build URL and the Repo URL in Azure DevOps.
Pull Request Annotations
The other task you can do is to see pull request annotations which contain the secrets and Infrastructure As Code security issues found in the Azure DevOps repos.
See here to enable ADO pull request annotations in MDC and in ADO
- In Microsoft Defender for Cloud, go to DevOps Security in the side bar. Tick the box beside the Azure DevOps project. and Configure pull request annotations.
Select Configure at the top.
In the new screen, turn on pull request annotations.
Now pull request annotations are enabled for all branches in that repository.
- Then you need to enable pull request annotations in Azure DevOps, by following the guidance here.
See the process for validating pull request annotations in Azure DevOps for secrets here.
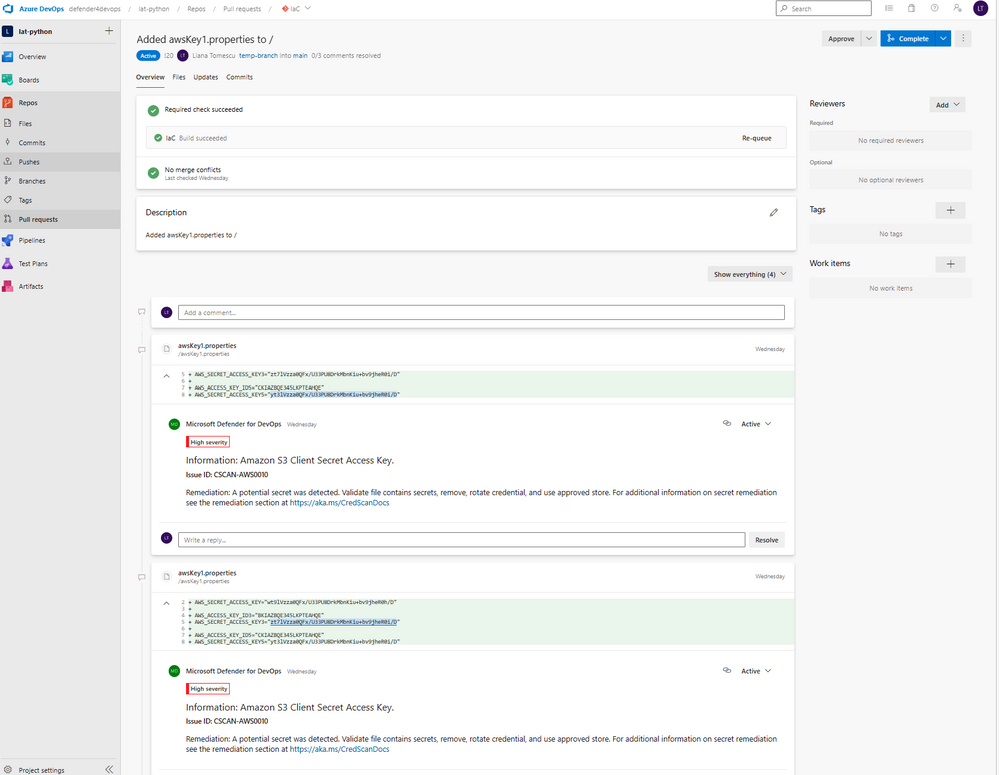
See the pull request annotations then in Azure DevOps, by going under Repos, in Pull Requests.
Click on the pull request to see the high severity pull request annotations showing Secret Access Keys discovered.
Now, the developers can take action on these secrets (by removing them from the repository, and having them in a key vault such as Azure Key Vault). The guidance for this can be found here and in the recommendation in Microsoft Defender for Cloud.
Workbook
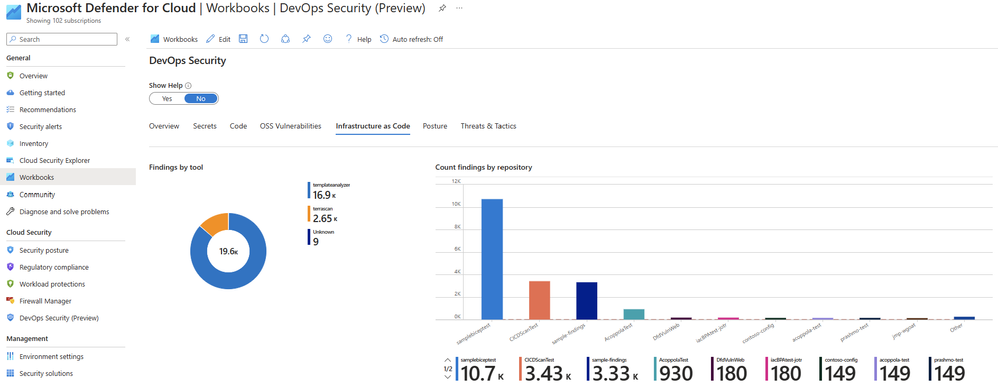
In Microsoft Defender for Cloud, you can view workbooks which are essentially reports specific to Defender for Cloud. To see these, go to Microsoft Defender for Cloud, and from the left-hand navigation blade, under the General section, select Workbooks.
From here, under the Defender for Cloud section, you can select the workbook DevOps Security Workbook, specifically focused on allowing you to focus on Defender for DevOps, to see an overview of security findings from Azure DevOps. There are several tabs that you click through. See more information about this workbook here.
Further Resources
- MDC Ninja Training: Become an Azure Security Center Ninja (microsoft.com) module 9 is DfD
- MDC Labs: https://aka.ms/MDFCLabs added DfD in module 14...working on module 15 in progress for the GitHub connector
- the latest episode of Defender for Cloud in the Field features DfD: https://www.youtube.com/watch?v=wYCOyFUMRPk
- DfD Interactive Guide: Unify DevOps security management with Microsoft Defender for Cloud (cloudguides.com)
- DfD Ignite On-Demand session: https://ignite.microsoft.com/en-US/sessions/418befd8-a7ee-4f46-a6a8-8b522b120135?source=sessions
Blogs
- Pre-Deployment Protection for Infrastructure as Code - Microsoft Community Hub
- DevOps Security Workbook - Microsoft Community Hub
- Compliance for Exposed Secrets Discovered by Defender for DevOps - Microsoft Community Hub
- Automate Defender for DevOps Recommendation Remediation - Microsoft Community Hub
- Automate SecOps to Developer Communication with Defender for DevOps - Microsoft Community Hub
- Integrate security into your developer workflow with GitHub Advanced Security for Azure DevOps - Azure DevOps Blog (microsoft.com)
- Download (free) a special Appendix about Defender for DevOps from the latest Microsoft Defender for Cloud book published by Microsoft Press
Defender for DevOps Documentation
- Microsoft Defender for DevOps - the benefits and features | Microsoft Learn
- Quickstart: Connect your GitHub repositories to Microsoft Defender for Cloud | Microsoft Learn
- Quickstart: Connect your Azure DevOps repositories to Microsoft Defender for Cloud | Microsoft Learn
- Configure the Microsoft Security DevOps GitHub action | Microsoft Learn
- Configure the Microsoft Security DevOps Azure DevOps extension | Microsoft Learn
- Discover misconfigurations in Infrastructure as Code - Defender for Cloud | Microsoft Learn
- Detect exposed secrets in code - Defender for Cloud | Microsoft Learn
- Tutorial Enable pull request annotations in GitHub or in Azure DevOps | Microsoft Learn
Conclusion
By the end of this article, you should have been able to understand the value proposition of Microsoft Defender for DevOps and now have the knowledge of how to run a PoC for it on Azure DevOps.
Thanks to the following teammates for reviewing this article:
Charles Oxyer, Microsoft Defender for DevOps Product Manager
Yuri Diogenes, Principal Microsoft Defender for Cloud Product Manager
P.S. Subscribe to our Microsoft Defender for Cloud Newsletter to stay up to date on helpful tips and new releases and join our Tech Community where you can be one of the first to hear the latest Microsoft Defender for Cloud news, announcements and get your questions answered by Azure Security experts.