This post has been republished via RSS; it originally appeared at: Microsoft Tech Community - Latest Blogs - .
As mentioned at Disable Session affinity cookie (ARR cookie) for Azure web apps - Azure App Service, ARRAffinity cookie is a feature on Azure App Service that allows an end user to talk to the same Azure App Service worker instance until session finishes assuming App Service is hosted on multiple instances.
A common problem encountered in enabling ARRAffinity cookie when having Azure App Service behind Azure Application Gateway is the host url visited in browser (usually the custom domain) does not match the domain field in ARRAffinity cookie (usually the default hostname of Azure App Service). This would cause ARRAffinity cookie unable to set on browser side. Here is sample error message in browser.
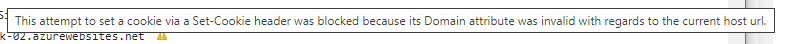
Cause for above problem is App Gateway didn't override value HTTP host header to custom domain when App Gateway forward request to backend App Service.
Below is an example solution to above problem with which clients are able to stick to a specific App Service instance throughout the session.
1. Add custom domain and ssl certificate on App Service.
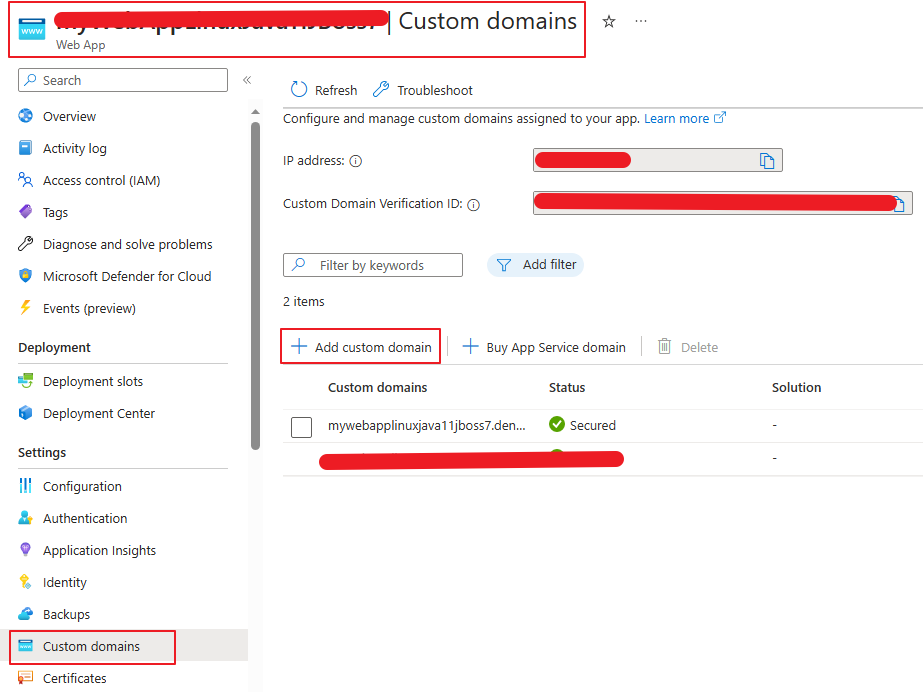
Although custom domain should be eventually resolved to the public frontend IP address of App Gateway, this step is still necessary for two reasons:
a. the domain attribute of ARRAffinity cookie set by App Service is determined by the value of host header in HTTP requests.
b. App Service needs to have custom domain binding in order to be identified by App Service Platform based on the custom domain host header in HTTP requests.
2. Create Health Probe for App Service on App Gateway side.

Here we set "Pick hostname from backend settings" to "Yes".
3. Create Backend setting for App Service on App Gateway side.
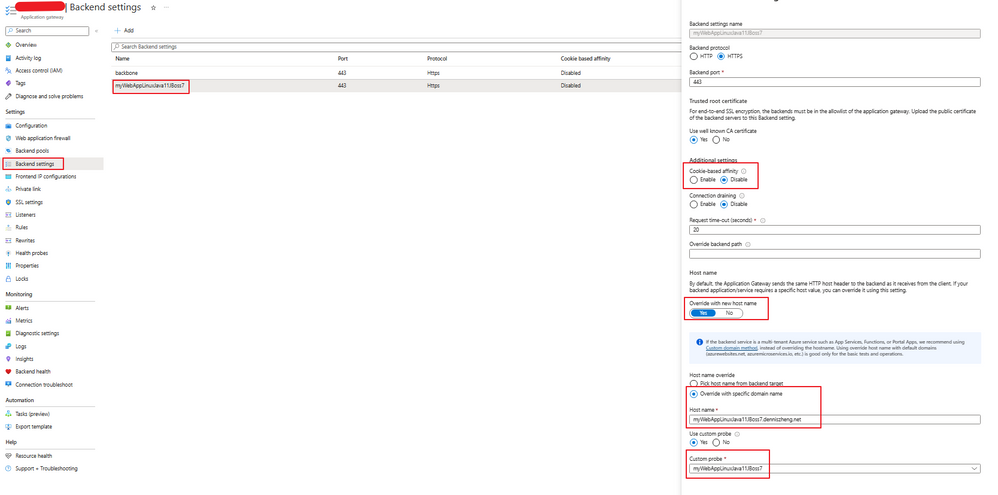
Here we need to
a. disable cookie-based affinity on App Gateway considering session data is kept on backend App Service.
b. override value of HTTP host header to custom domain.
c. use health probe created in previous step.
4. Add App Service to backend pool of App Gateway.
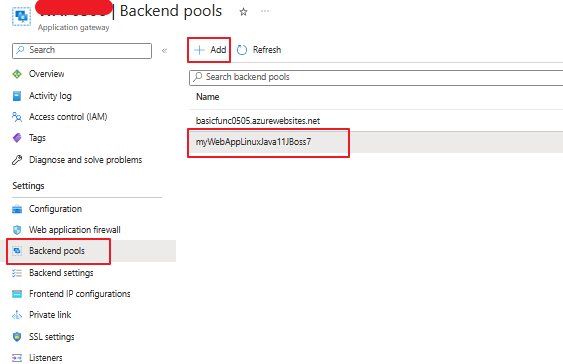

Here we select App Service as backend Target type and default hostname of App Service as the Traget FQDN.
5. Create Listener for backend App Service on App Gateway end.
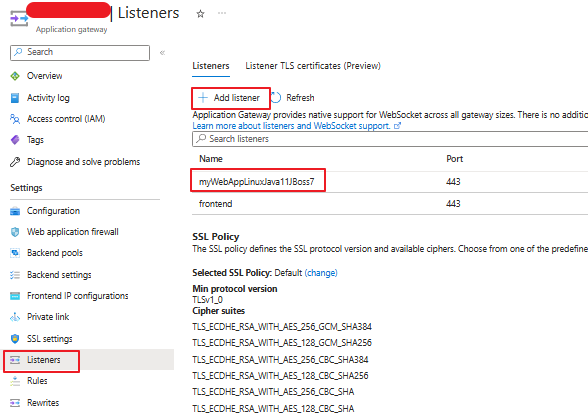
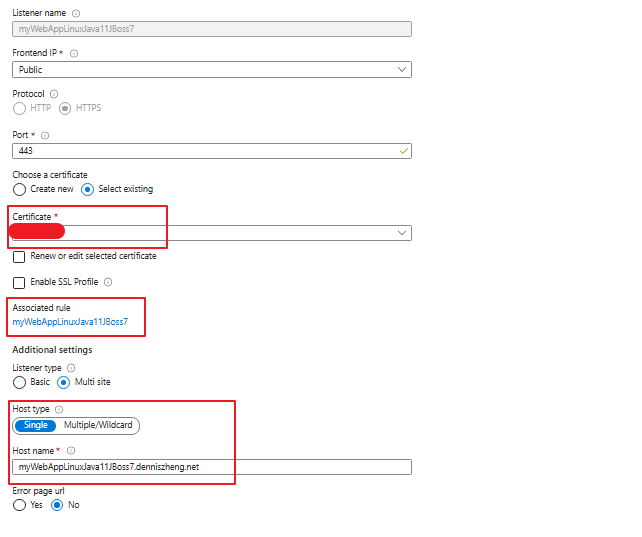
Here we need to
a. attach the certificate for the custom domain to the App Gateway.
b. listen on requests to the custom domain
6. Create routing rule on App Gateway to connect Listener and Backend target configured previously.
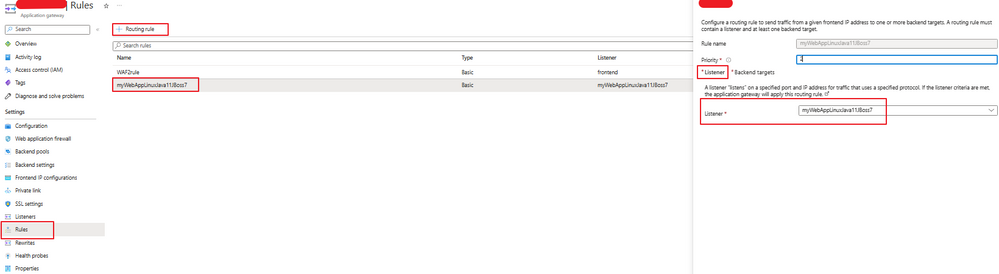
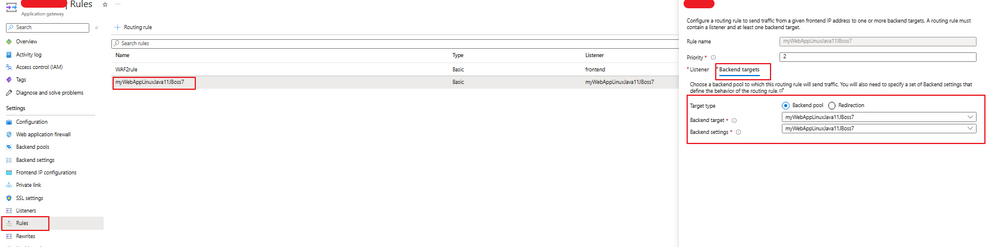
7. Change DNS entry to resolve custom domain to the public frontend IP address of App Gateway.
8. Enable ARRAffinity cookie on App Service.

With above configurations in place, we can see ARRAffinity cookie is set successfully.

