This post has been republished via RSS; it originally appeared at: Microsoft Tech Community - Latest Blogs - .
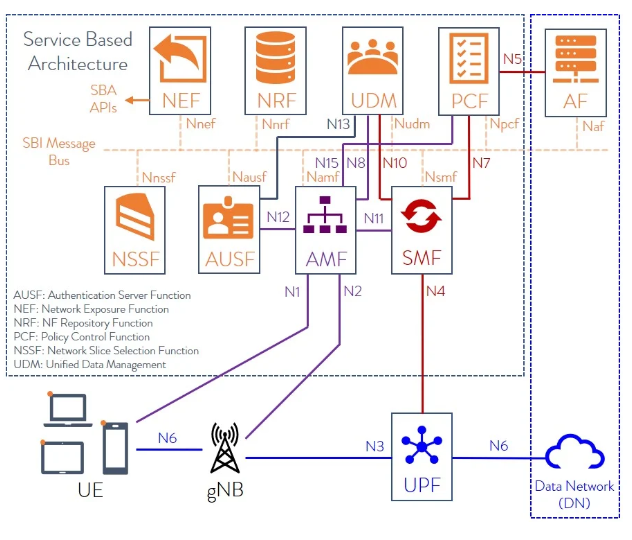
Service-Based Architectures provide a modular framework from which common applications can be deployed using components from various sources and suppliers. The 3GPP defines a Service-Based Architecture (SBA) in which the control plane functionality and common data repositories of a 5G network are delivered through a set of interconnected Network Functions (NFs), with each NF authorized to access the services of other NFs.
Assuming the role of either service consumer or service producer, Network Functions are self-contained, independent, and reusable. Each Network Function service exposes its functionality through a Service-Based Interface (SBI), which employs a well-defined REST interface using HTTP/2. To mitigate issues around TCP head-of-line (HOL) blocking, the Quick UDP Internet Connections (QUIC) protocol may be used in the future. The 5G SBA comprises numerous components, including:
What is the NF Repository Function (NRF)?
With Network Functions built using microservice methodologies, the 5G Service-Based Architecture will ultimately evolve into a complete service mesh with service discovery, load balancing, encryption, authentication, and authorization, employing a sidecar for interservice communication. Currently, however, the Service-Based Architecture employs a centralized discovery framework that leverages an NF Repository Function (NRF). The NRF maintains a record of available NF instances and their supported services. It allows other NF instances to subscribe and be notified of registrations from NF instances of a given type. The NRF supports service discovery by receiving discovery requests from NF instances and providing details on which NF instances support specific services.
What is the Network Slice Selection Function (NSSF)?
Network slicing is a fundamental new capability of 5G infrastructures, bringing a high degree of deployment flexibility and efficient resource utilization when deploying diverse network services and applications. A logical end-to-end network slice has predetermined capabilities, traffic characteristics, and service level agreements. It includes the virtualized resources required to service the needs of a Mobile Virtual Network Operator (MVNO) or a group of subscribers, including a dedicated User Plane Function (UPF), Session Management Function (SMF), and Policy Control Function (PCF).
The Access and Mobility Management Function (AMF) instance, serving User Equipment (UE), is common to all network slices that the UE is a member of. Identification of a Network Slice is done via the Single Network Slice Selection Assistance Information (S-NSSAI) identifier. The Network Slice instance selection is triggered by the first AMF that receives a UE registration request, which retrieves the permitted slices from the Unified Data Management (UDM) element and then requests an appropriate Network Slice Instance from the NSSF.
What is the Unified Data Management (UDM) Service?
The UDM provides services to other SBA functions, such as the AMF, SMF, and NEF. The UDM is typically recognized as a stateful message store, holding information in local memory. However, the UDM may also be stateless, storing information externally within a Unified Data Repository (UDR). Serving as a repository for subscriber-related information and playing a crucial role in authentication and authorization processes, the UDM is analogous to the Home Subscriber Server (HSS) in previous generations of cellular networks.
It is employed by the Access and Mobility Management Function (AMF) and Session Management Function (SMF) to retrieve essential information about the subscriber, such as user profiles, authentication keys, and service-specific settings. This data is necessary for establishing secure connections, managing sessions, and providing personalized services to the subscribers within a 5G network.
What is the Policy Control Function (PCF)?
The Policy Control Function (PCF) supports a unified policy framework within the 5G infrastructure to govern network behavior by managing and enforcing policies related to quality of service (QoS), traffic management, and resource allocation. Similar to the PCRF (Policy and Charging Rules Function) in EPC architectures, the PCF acts as a policy decision point in the 5G network. It interacts with other network elements, such as the AMF, SMF, and UDM, to gather essential information and make informed policy decisions.
The PCF retrieves subscription information, including service entitlements, preferences, and QoS requirements, from the UDM. This information serves as a basis for determining the appropriate policy rules that need to be applied to the user's session or connection. The PCF then communicates these policy rules to the relevant control plane functions, ensuring their enforcement throughout the network. This enables operators to adapt and customize network behavior based on user requirements and network conditions.
What is the Service Communication Proxy (SCP)?
Appearing in the second specification iteration of 5G, known as release 16 in 3GPP terminology, the Service Communication Proxy (SCP) was defined within TS23.501 - System architecture for the 5G System. It is a function that arises out of necessity. The SCP is not mandatory for the functioning of a 5G SBA but becomes essential in a highly distributed multi-access edge compute cloud environment.
The Service Communication Proxy serves as a single point of entry for a cluster of network functions once they have been successfully discovered by the NRF. This enables the SCP to act as the designated discovery point within a data center, relieving the NRF from the task of managing numerous distributed service meshes that form the network operator's infrastructure. Together with the NRF, the SCP forms the hierarchical 5G Service Mesh.