This post has been republished via RSS; it originally appeared at: Microsoft Tech Community - Latest Blogs - .
Before we start, please not that if you want to see a table of contents for all the sections of this blog and their various Purview topics, you can locate the in the following link:
Microsoft Purview- Paint By Numbers Series (Part 0) - Overview - Microsoft Tech Community
Disclaimer
This document is not meant to replace any official documentation, including those found at docs.microsoft.com. Those documents are continually updated and maintained by Microsoft Corporation. If there is a discrepancy between this document and what you find in the Compliance User Interface (UI) or inside of a reference in docs.microsoft.com, you should always defer to that official documentation and contact your Microsoft Account team as needed. Links to the docs.microsoft.com data will be referenced both in the document steps as well as in the appendix.
All of the following steps should be done with test data, and where possible, testing should be performed in a test environment. Testing should never be performed against production data.
Target Audience
The Microsoft Defender for Cloud Apps section of this blog series is aimed at Security and Compliance officers who need protect data through a Cloud App, meaning a third-party cloud-based application.
Document Scope
This document is meant to guide an administrator who is “net new” to Microsoft E5 Purview through.
We will be blocking the ability to Cut and Copy date from a web-based Teams chat. This is limited in scope and meant to walk you through the basic process configuring a DLP activity.
Out-of-Scope
This document does not cover any other aspect of Microsoft E5 Purview, including:
- Data Classification
- Information Protection
- Data Protection Loss (DLP) for Exchange, OneDrive, Devices
- Data Lifecycle Management (retention and disposal)
- Records Management (retention and disposal)
- eDiscovery
- Insider Risk Management (IRM)
- Priva
- Advanced Audit
- Information Barriers
- Communications Compliance
- Licensing
This is limited in scope and meant to walk you through the basic process configuring a DLP activity in Microsoft Defender for Cloud Apps.
It is presumed that you have a pre-existing of understanding of what Microsoft E5 Compliance does and how to navigate the User Interface (UI).
For details on licensing (ie. which components and functions of Purview are in E3 vs E5) you will need to contact your Microsoft Security Specialist, Account Manager, or certified partner.
Overview of Document
- Create a Conditional Access policy for Microsoft Teams and your test users
- Access Microsoft Teams on a browser
- Verify Microsoft Teams is connected to Microsoft Defender for Cloud Apps
- Create a Session policy
- Test the Session policy
Use Case
An organization who wants to configure Data Loss Prevention against a cloud-based application. In this blog we will use Microsoft Teams.
Definitions
- Cloud App – meaning a third-party cloud based application
- Session Policy – a session policies enable real-time session-level monitoring, affording you granular visibility into cloud apps and the ability to take different actions depending on the policy you set for a user session.
Notes
None.
Pre-requisites
- You have read Part 0 of this blog series.
Conditional Access App Control
To enable Data Loss Prevention with Microsoft Teams running from a browser, or any other cloud-based application) being accessed by a browser, we will need to follow the steps below.
Create Conditional Access policy (Azure Portal)
We will block Microsoft Teams from being able to “Cut and Copy” as an initial test for MDCA.
First, we will set up Conditional Access for MS Teams and our Test user (ex. Megan Bowen).
- Go to portal.azure.microsoft.com
- Go to Security -> Conditional Access
- Click on Policies
- Click New Policy
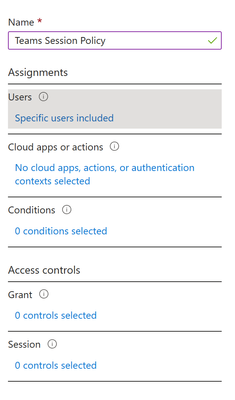
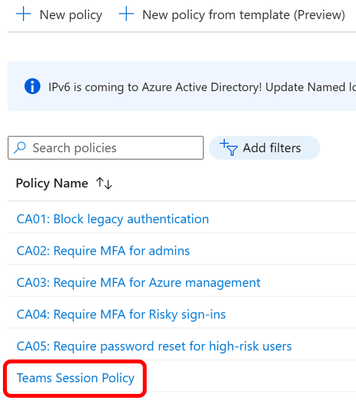
- Give the policy a name (ex. Teams Session Policy)
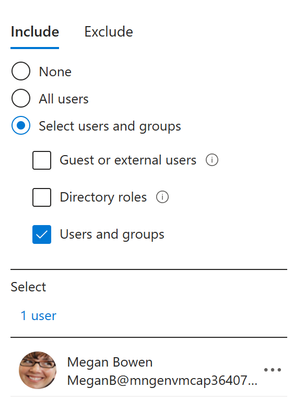
- Select a user for this policy under Assignments –> Users (ex. Megan Bowen).
- We must now select our test app for our policy. Go to Assignments –> Cloud Apps or Actions. Under Include, select the Microsoft Teams application.
- Under Assignments –> Conditions, we will not select any conditions at this time.
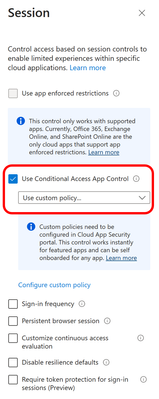
- For We will now verify the access Access Control –> Grant, leave at default of Grant Access to the App (ie. Microsoft Teams).
- For Session, go to Access Control –> Session, and enable Use Conditional Access App Control and set to Use Custom Policy
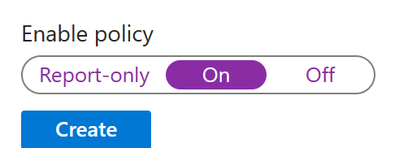
- At the bottom of the policy, set Enable policy to “On”.
- Now under Policies, you will see your new policy for Microsoft Teams.
- Now go to MDCA and verify your Connected apps.
Access Microsoft Teams on a Browser
For MFDC to see Microsoft Teams, your test users must be accessing it via a web browser.
- Login into Microsoft Teams via web browser with your test user (ex. Megan Bowen).
- Now go to MDCA and Connect apps.
Verify Microsoft Teams is a Connected App (MDCA)
- Login to portal.cloudappsecurity.com
- Go to Connected apps -> Conditional Access App Control Apps.
- Verify that Microsoft Teams shows up here
- If it is not showing up here, you might need to:
- Perform an App Onboarding (see the troubleshooting below).
- You might not have logged into Microsoft Teams on a web browser with your test users (see the section above).
Create a Session policy (MCAS)
We will now set up a Session Policy.
- Stay in MDCA and go to Policies – Conditional Access
- Click Create Policy -> Session Policy
- Give the policy a name and description (ex. Teams block Cut/Copy). Leave the Category art “DLP”.
- For Activity source, select the following 3 options:
- App, equals, Microsoft Teams.
- Activity Type, equals, Cut/Copy item.
- Devices, Tag, does not equal, Intune compliant, Hybrid Azure AD joined.
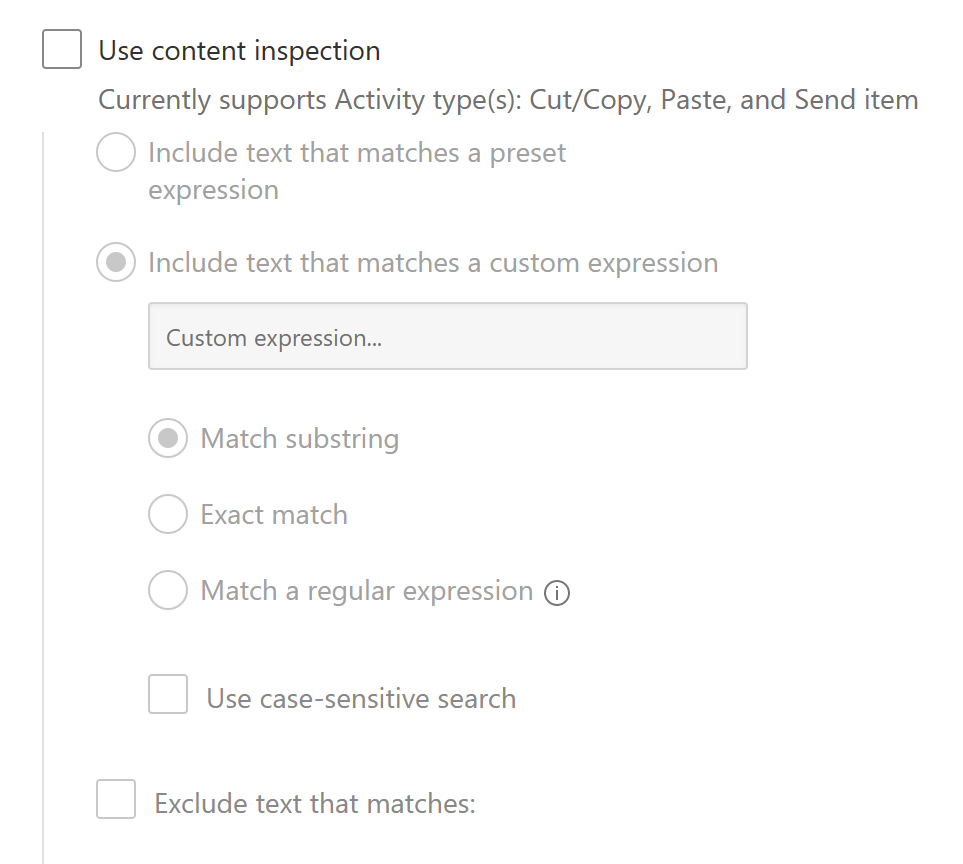
- For the section Use Content inspection, do not inspect the content at this time.
- Under Actions, enable Block with 1) also notify by email and 2) customize block message (place the date and time in the message in case you need to troubleshoot this policy).
- Now create the policy.
- You are now done preparing a Session Policy to block Microsoft Teams Cut and Copy. Proceed to the testing section below.
Test the Session policy
We will now test the blocking of Microsoft Teams Cut and Copy using a Session Policy from MFCA.
- Go to Teams online with your test user.
- You should see a message similar to the one below in your browser. Click Continue to Microsoft Teams.
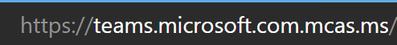
- You should see a URL similar to the one below. The “mcas” indicates you are now accessing Microsoft Teams via MFCA and the session policy.
- Type something into the Microsoft Teams chat, select that text and attempt to copy it. You should get a message similar to the one below.
Note – As you recall previously, we placed a date and time in our Session Policy message (see above). This is where having that information will help you know if the latest version of your policy is in effect.
- If all is working, you are now done with testing this Session Policy for Data Loss Prevention.
Troubleshooting
If you want MDCA to have a custom logo on splash pages, follow the steps below.
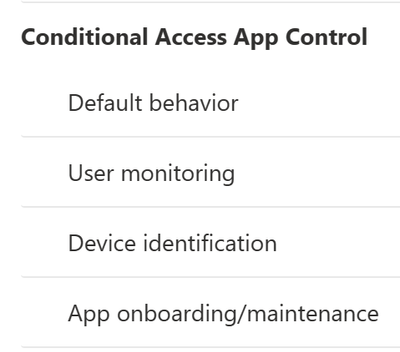
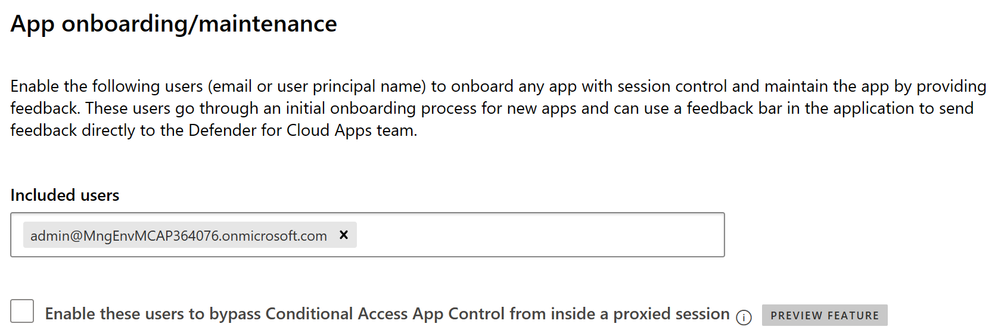
App Onboarding / Maintenance (MDCA)
It might be necessary to add your admin account to the App onbaoarding/maintance. Do to accomplish this, follow these steps.
- Go to either 1) security.microsoft.com or 2)your Microsoft Defender for Cloud Apps (MDCA)
- Go to Settings –> Cloud Apps -> Conditional Access App Control -> App onboarding/maintenance
- Add the Admin account if needed.
- Click Save.
Appendix and Links