This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Community Hub.
Web APIs have experienced an exponential increase in popularity and usage in the past few years. APIs exist at the intersection of business, products, and technologies and have transformed the way businesses interact with each other and the way they provide value to their customers. Web APIs allow businesses to access 3rd-party data, allow for cross-platform communication and seamless integration anywhere and anytime it's required, offering unmatched data processing efficiencies and cost savings.
Azure API Management
API Management Authorizations
Authorization scenarios
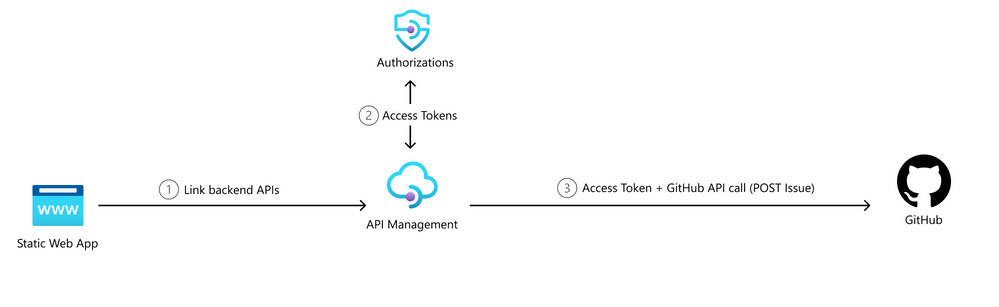
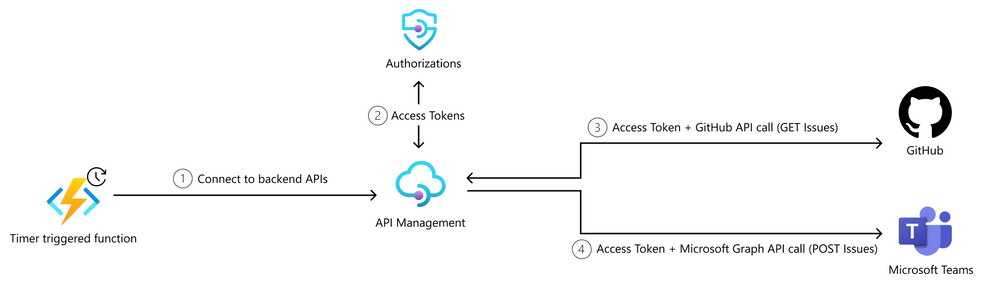
Today, we will talk about an unattended scenario with Azure Functions. With our Static Web App Scenario, users are able to post a GitHub issue to a repository. We now want to implement a timer triggered Azure Function that will GET the count of GitHub issues and POST about it in a Microsoft Teams channel. This will create a reminder notification in Teams about how many issues are still open:
Prerequisites
- A running Azure API Management service instance. Check out our Quickstart: Create a new Azure API Management service instance by using the Azure portal
- Managed system-assigned identity must be enabled for the API Management instance.
- Visual Studio 2022 (Make sure you select the Azure development workload during installation) or Visual Studio Code
STEP 1 - Configure Authorizations in Azure API Management
For our scenario, we need two API Management Authorizations, one for the GitHub API and one for the Microsoft Graph API.
For the GitHub authorization, you can follow this tutorial to configure your authorization. Make sure you use the following configurations:
|
Settings
|
Value
|
|
Provider name
|
githubissue01
|
|
Identity provider
|
Select GitHub
|
|
Grant type
|
Select Authorization code
|
|
Client id
|
Create a new GitHub OAuth app or use existing one from Blog Post
|
|
Client secret
|
Paste the value from the GitHub OAuth app
|
|
Scope
|
repo
|
|
Authorization name
|
githubissue01
|
For the Microsoft Graph API authorization, you can follow this tutorial to configure your authorization. Make sure you use the following configurations:
|
Settings
|
Value
|
|
Provider name
|
channel-aad
|
|
Identity provider
|
Select Azure Active Directory
|
|
Grant type
|
Select Authorization code
|
|
Client id
|
Paste the value you copied earlier from the app registration - follow tutorial for setting this up
|
|
Client secret
|
Paste the value you copied earlier from the app registration
|
|
Resource URL
|
|
|
Scopes
|
Note: Leave this input empty since your scopes are defined in the app registration
|
|
Authorization name
|
channel-aad
|
STEP 2 - Add your GitHub API and configure a policy
|
Setting
|
Value
|
|
Display name
|
githubissue
|
|
Name
|
githubissue
|
|
Web service URL
|
|
|
API URL suffix
|
githubissue
|
|
Setting
|
Value
|
|
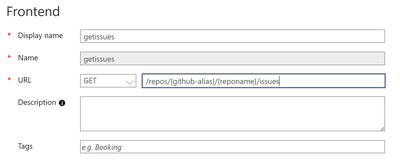
Display name
|
getissues
|
|
URL for GET
|
/repos/{github-alias}/{reponame}/issues
|
STEP 3 - Add your Microsoft Graph API and configure a policy
|
Setting
|
Value
|
|
Display name
|
TeamsChannelMessage
|
|
Name
|
TeamsChannelMessage
|
|
Web service URL
|
|
|
API URL suffix
|
TeamsChannelMessage
|
|
Setting
|
Value
|
|
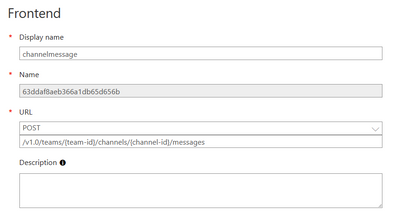
Display name
|
postchannelmessage
|
|
URL for POST
|
/v1.0/teams/{team-id}/channels/{channel-id}/messages
|
Once you added the API, we can make use of the provider in the Inbound Processing Policy and apply the previously created Authorization. Add the following snippet to the inbound JWT policy:
NOTE: For more information, check out the get-authorization-context policy references to learn more about how to use the policy.
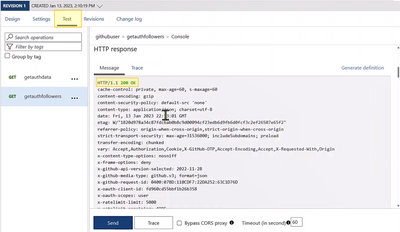
STEP 4 - Test the APIs
- Select your API and the operation you added previously
- Go to the Test tab.
- Select Send.
STEP 5 - Building your timer triggered Azure Function
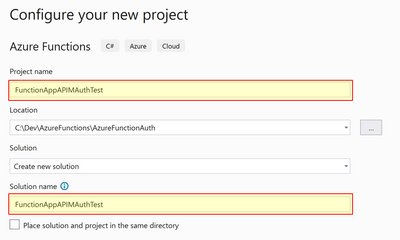
Next, we will build our timer triggered function in Azure Functions. For this, you can follow the Quickstart: Create your first C# function in Azure using Visual Studio and use the AuthorizationsDemoAzureFunction GitHub repo. We used the following configurations in Visual Studio:
|
Setting
|
Value
|
|
Project name
|
FunctionAppAPIMAuthTest
|
|
Solution name
|
FunctionAppAPIMAuthTest
|
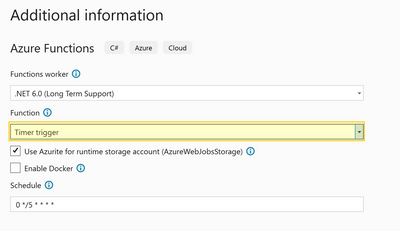
Make sure to use Time trigger as the initial trigger for your Azure function.
In local.settings.json file, we will add the following code:
In our FunctionAppAPIMAuthTest.cs file, we will add the following code:
Note: Function1 referring to your function class file.
STEP 5 - Test Azure Function locally
Further Resources