This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Tech Community.
In August a new Microsoft Graph Security API add-on for Splunk for introduced, and you can read this article for more information on how to configure it. After finishing configuring this integration, the alerts from Azure Security Center will be start flowing to Splunk. Here are the core steps that you can use to access these alerts:
1. Access Splunk and click Microsoft Graph Security Add-On for Splunk, as shown below:
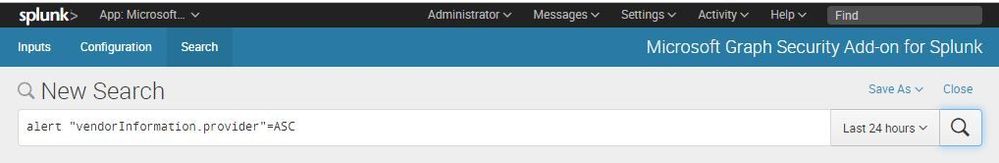
2. Click Search, and in the New Search page, type the query below and click the search button:
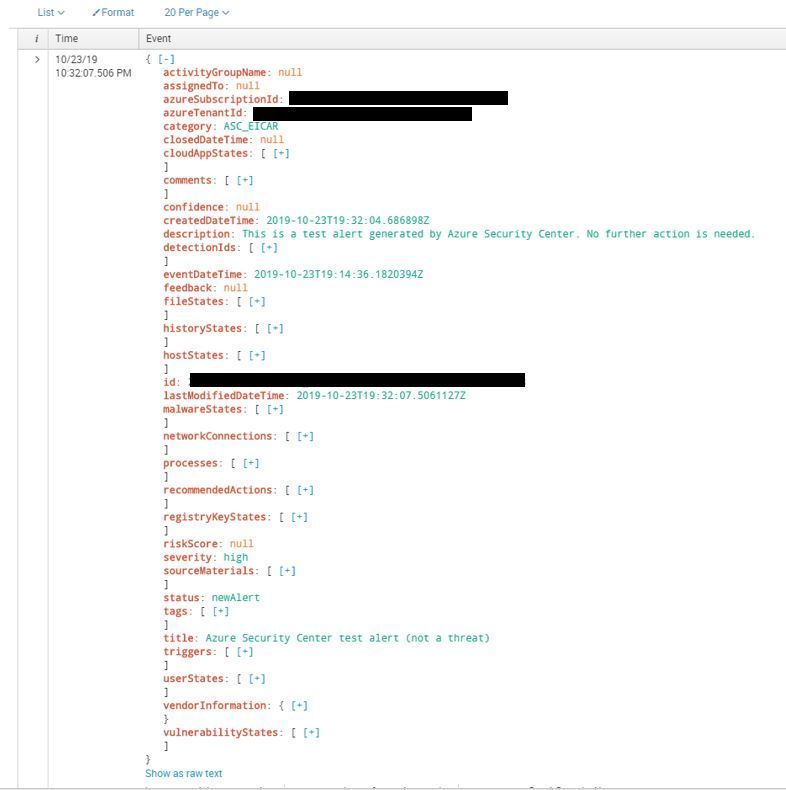
3. At this point you should see the alerts the results. Below you have a sample of how the alert will look like on Splunk:
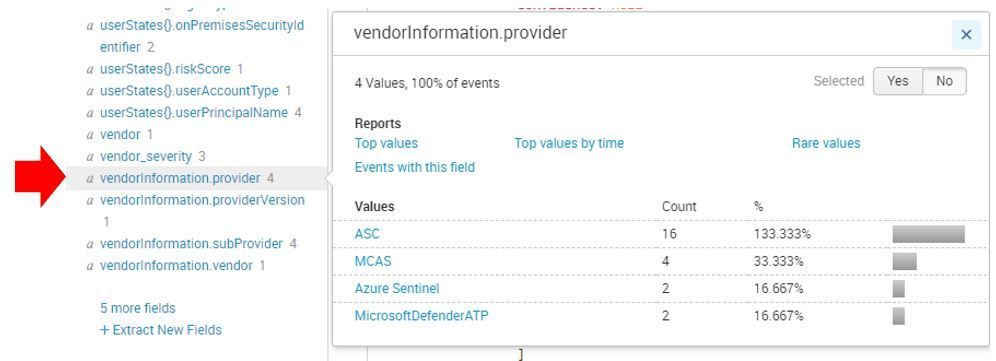
Another approach to quickly access alerts from different providers that are available via Graph Security API is to search for the keyword alert, once the result comes up, click vendorInformation.provider in the left, and click on the provider that you want to filter, as shown the sample below:
As you can see on the example above, data from Azure Sentinel will also be available using this Graph Security API Add-on.
Credit for setting up the Graph Security API Add-On for Splunk Lab
Yaniv Shasha, Program Manager, CxE Security