This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Tech Community.
We are happy to announce that tamper protection is now supported in Microsoft Defender ATP Threat & Vulnerability Management to help raise your organization’s security posture.
Now, within the security recommendations section of Threat & Vulnerability Management (TVM), SecOps and security administrators can see a recommendation to turn on tamper protection and then be able to learn more about the recommendation and act on it. This provides security teams greater visibility into how many machines don’t have this feature turned on, the ability to monitor changes over time, and a process to turn on the feature.
Tamper protection keeps threat actors from disabling the very security protection features that work to stop them from entering your unsuspecting network.
Shields up on malicious and unauthorized security changes
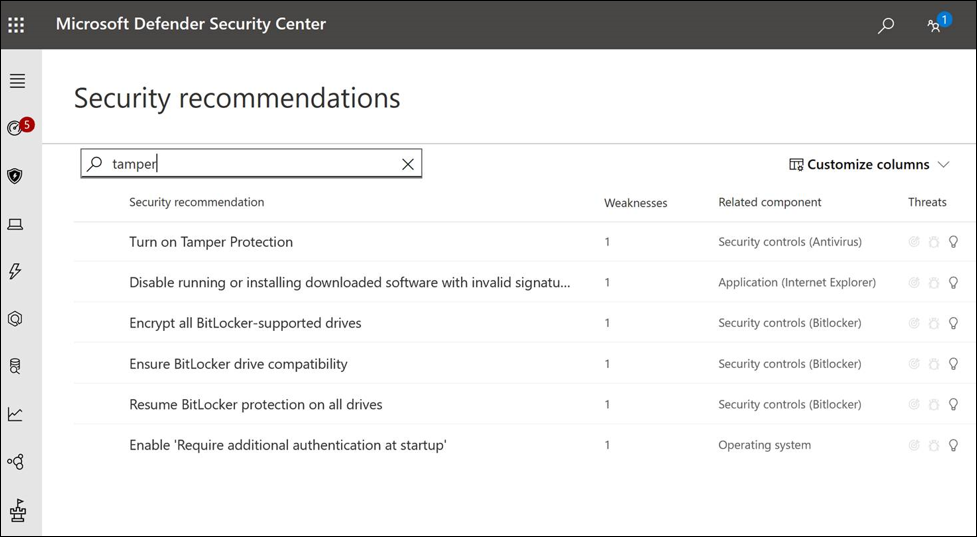
To see tamper protection status from within TVM, go to the security recommendations page and search for tamper, as shown in the following image:
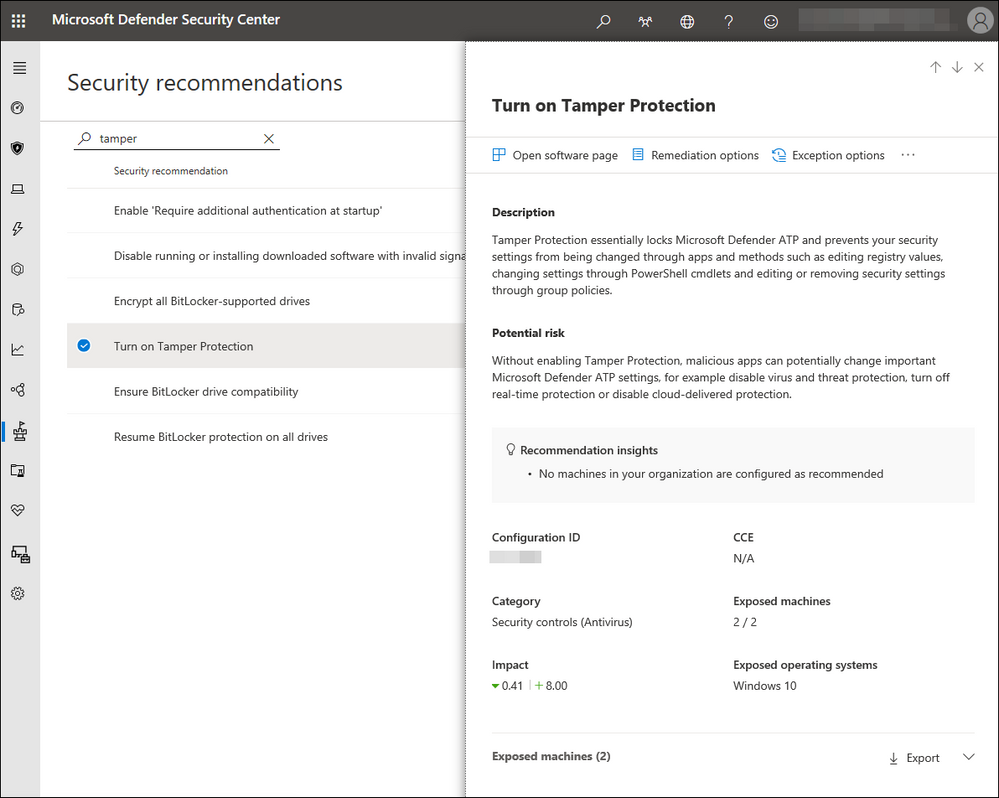
In the list of results, you can select Turn on Tamper Protection. It opens up a flyout screen so you can learn more about it and turn it on. You can see export option from the flyout screen to get the exposed device list.
Availability in previous Windows 10 versions
Tamper protection is now also available in earlier versions of Windows 10.
We understand each organization’s environment is unique, with different needs, requirements, and therefore different timelines for planning, testing, and deploying Windows updates. We also know that our customers want to have the latest security features on the versions of Windows that are currently in their organizations. We listened to this customer feedback and are excited to be backporting this latest feature.
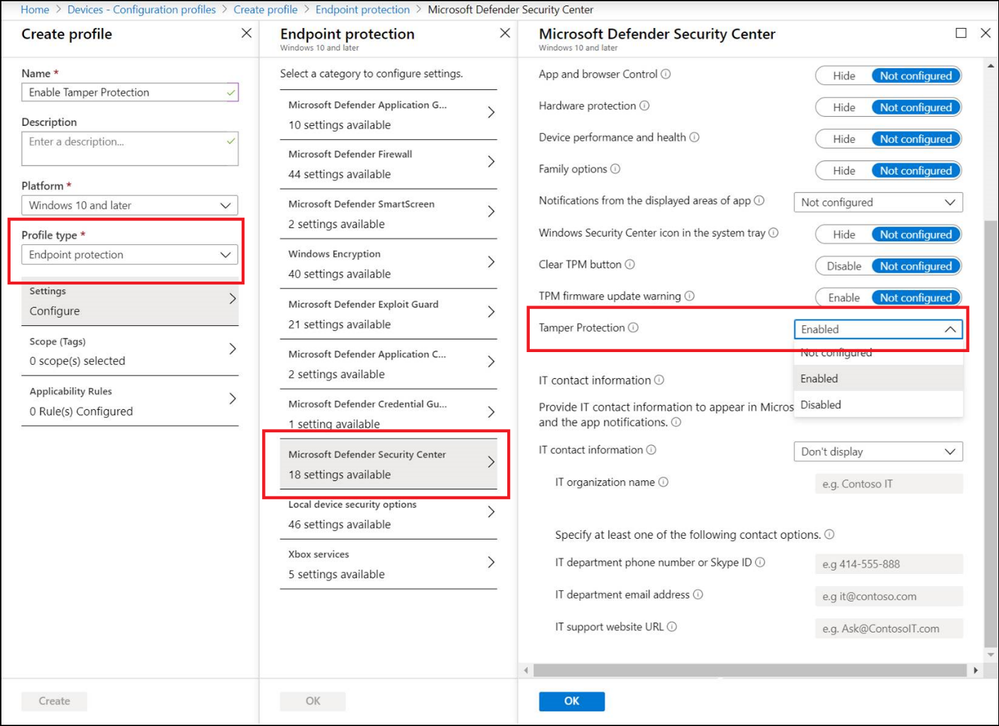
You can continue to enable tamper protection from Microsoft Intune based on user or device groups. Go to Microsoft Endpoint Manager > Device Configuration – Profiles > Create profile > Endpoint protection and configure tamper protection as shown in the following image:
Once tamper protection is enabled by administrators, customers with Windows versions 1709, 1803, 1809 and 1903 can use PowerShell to confirm tamper protection is turned on:
- Open the Windows PowerShell app in administrator mode
- Use the Get-MpComputerStatus PowerShell cmdlet.
- In the list of results, look for IsTamperProtected. (A value of true means tamper protection is enabled.)
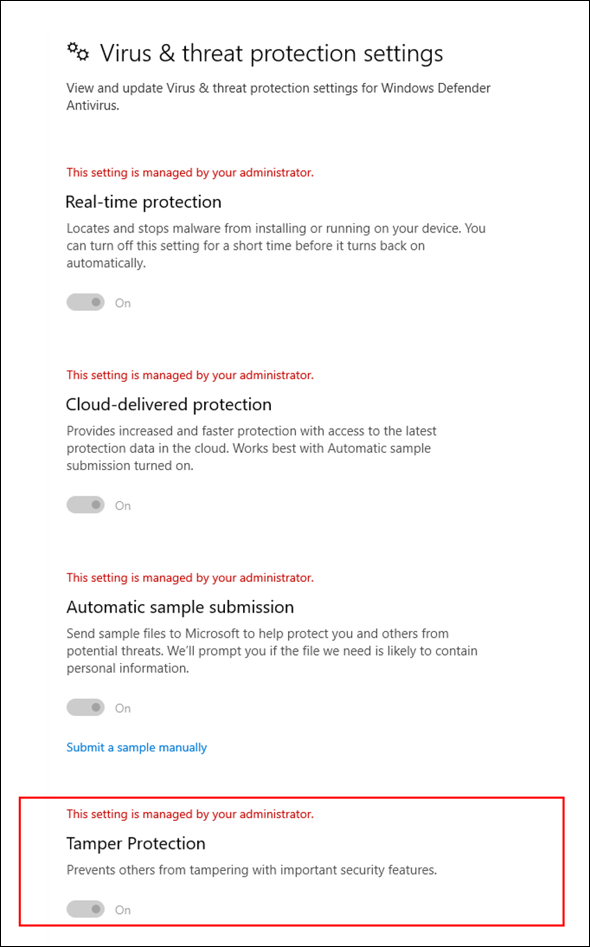
Those customers with Windows 10 version 1903 can also see that protection is turned on in the Windows Security app:
Let us know what you think
Turn tamper protection on in your environment and give us your feedback. You can use Threat & Vulnerability Management to get the latest security recommendations and insights. Stay tuned! More exciting enhancements are coming up.
Learn more
Protect security settings with tamper protection.
Want to experience Microsoft Defender ATP? Sign up for a free trial. Microsoft Defender ATP is part of the Microsoft Threat Protection solutions which provides unified protection for identities, endpoints, email and data, apps, and infrastructure. Through signal sharing across Microsoft services, customers can count on Microsoft’s industry-leading optics and security technologies for combating today’s threats.
Shweta Jha (@shwetajha_MS)
Microsoft Defender ATP team