This post has been republished via RSS; it originally appeared at: Microsoft Developer Blogs - Feed.
This is the last blog of a six-part series where we’ve demonstrated the application of Zero Trust concepts for securing federal information systems with Microsoft Azure. In this sixth blog of the series we will explore how to leverage Microsoft Azure for supply chain risk management in Zero Trust models. This blog series is coauthored by TJ Banasik, CISSP-ISSEP, ISSAP, ISSMP, Sr. Program Manager, Azure Global Customer Engineering, Mark McIntyre, CISSP, Senior Director, Enterprise Cybersecurity Group and Adam Dimopoulos, Azure Global Customer Engineering.What is supply chain risk management?
The Microsoft Zero Trust vision paper outlines three principles of Zero Trust- Verify Explicitly, Least Privilege Access and Assume Breach. Assume breach is a mindset we must take beyond the enterprise to consider our partners, contractors and suppliers. NIST SP 800-207 for Zero Trust Architectures recommends organizations “should evaluate service providers on a holistic basis by taking into consideration factors such as vendor security controls, enterprise switching costs, and supply chain risk management.”[i] Supply Chain Risk Management is the process of securing vendors, partners and supply chains to prevent disruption to the organization. Threat actors target these assets to gain a foothold in a network and attacks can include:- Compromise of software building tools to ensure malware is imprinted into all software generated from the building tools.
- Replacing software update repositories with malicious replicas that distribute malware across entire software ecosystems.
- Steal code-signing certificates to make malicious software appear as legitimate code.
- Intercept hardware shipments to inject malicious code into hardware, firmware, and field-programmable gate arrays (FPGAs).
- Pre-install malware onto IoT devices before they arrive to target organizations.
Defining Zero Trust governance based on federal standards
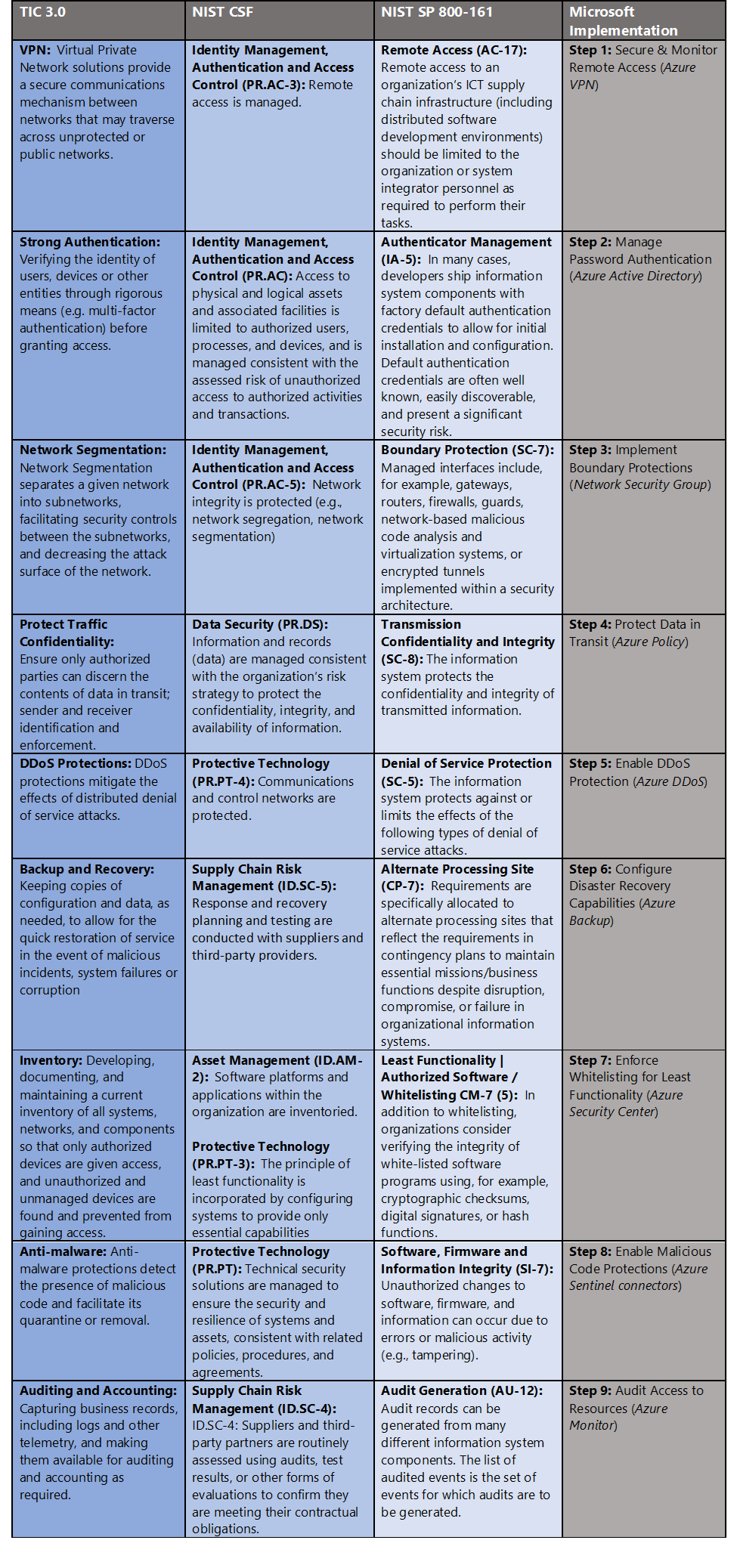
Governance definition is a critical precursor to any Zero Trust initiative. For this blog we’ve leveraged TIC 3.0 Zero Trust principles and aligned with respective NIST SP 800-161 and NIST CSF controls. Our sixth focus point is supply chain risk management and these standards have a wealth of information aligned to this principle. The diagram below highlights the key takeaways and requirements from the standards.- Trusted Internet Connections (TIC) is a federal cybersecurity initiative to enhance network and perimeter security across the United States federal government. The TIC initiative is a collaborative effort between the Office of Management and Budget (OMB), the Department of Homeland Security (DHS) Cybersecurity and Infrastructure Security Agency (CISA), and the General Services Administration (GSA).[ii] The TIC 3.0: Volume 3 Security Capabilities Handbook provides various security controls, applications and best practice for risk management in federal information systems.
- NIST Cybersecurity Framework. The National Institute of Standards and Technology (NIST) developed the Cybersecurity Framework to address risks highlighted in the Cybersecurity Enhancement Act of 2014 with a goal to identify “a prioritized, flexible, repeatable, performance-based, and cost effective approach, including information security measures and controls that may be voluntarily adopted by owners and operators of critical infrastructure to help them identify, assess, and manage cyber risks.”[iii] The Framework for Improving Critical Infrastructure Cybersecurity outlines these principles.
- NIST SP 800-161: Supply Chain Risk Management Practices for Federal Information Systems and Organizations. This publication “provides guidance to federal agencies on identifying, assessing, selecting, and implementing risk management processes and mitigating controls throughout their organizations to help manage Information and Communications Technology (ICT) supply chain risks.”[iv] NIST SP 800-161 outlines the ICT Supply Chain Risk Management process which directly maps to applicable NIST SP 800-53A Controls.
Supply chain risk management for Zero Trust with Microsoft Azure
Microsoft Azure Government has developed a 9-step process to facilitate supply chain risk management for federal information systems in Microsoft Azure which is aligned with the security monitoring principles within the TIC 3.0, NIST CSF and NIST SP 800-161 standards. Note this process is a starting point, as supply chain risk management programs require alignment of people, processes, policy and technology so refer to organizational requirements and respective standards for implementation. Azure has several offerings to facilitate supply chain risk management including VPN Gateway, Azure Active Directory, Network Security Groups, Azure Policy, Azure DDoS, Azure Backup, Azure Security Center, Azure Sentinel and Azure Monitor.- VPN Gateway is a specific type of virtual network gateway that is used to send encrypted traffic between an Azure virtual network and an on-premises location over the public Internet.
- Azure Active Directory is an identity and access management-as-a-service (IDaaS) solution that combines single-on capabilities to any cloud and on-premises application with advanced protection.
- Network Security Groups contain security rules that allow or deny inbound network traffic to, or outbound network traffic from, several types of Azure resources.
- Azure Policy helps you manage and prevent IT issues with policy definitions that enforce rules and effects for your resources.
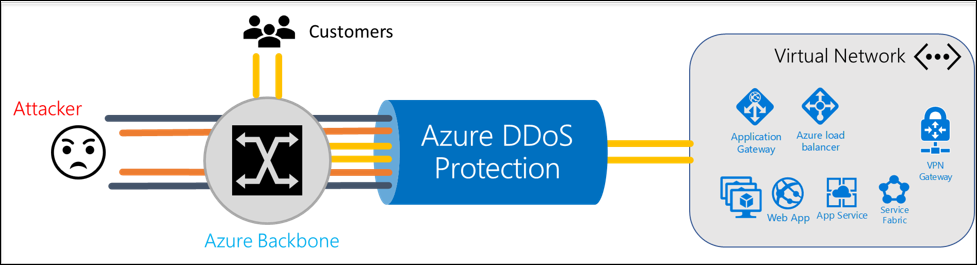
- Azure DDoS Protection protects against Distributed denial of service (DDoS) attacks which are some of the largest availability and security concerns facing customers that are moving their applications to the cloud.
- Azure Backup provides simple, secure, and cost-effective solutions to back up your data and recover it from the Microsoft Azure cloud.
- Azure Security Center is a unified infrastructure security management system that strengthens the security posture of your data centers, and provides advanced threat protection across your hybrid workloads in the cloud - whether they're in Azure or not - as well as on premises.
- Azure Sentinel is a scalable, cloud-native, security information event management (SIEM) and security orchestration automated response (SOAR) solution.
- Azure Monitor maximizes the availability and performance of your applications and services by delivering a comprehensive solution for collecting, analyzing, and acting on telemetry from your cloud and on-premises environments.
9 steps to supply chain risk management for Zero Trust with Microsoft Azure
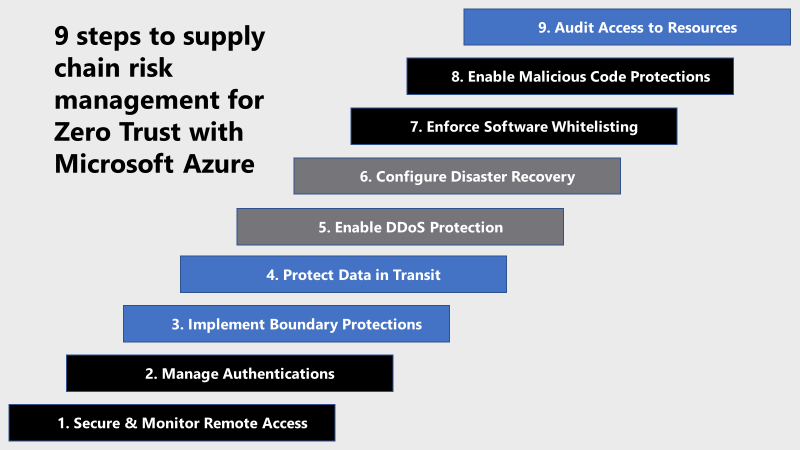 1) Secure and Monitor Remote Access
Partner remote access to a network can introduce vulnerabilities if not properly implemented, secured and controlled. Azure has several options to facilitate remote access including virtual network gateway. A virtual network gateway is composed of two or more VMs that are deployed to a specific subnet you create called the gateway subnet. Virtual network gateway VMs contain routing tables and run specific gateway services. ]
VPN gateways can be deployed in Azure Availability Zones. This brings resiliency, scalability, and higher availability to virtual network gateways. Deploying gateways in Azure Availability Zones physically and logically separates gateways within a region, while protecting your on-premises network connectivity to Azure from zone-level failures.
Creating a virtual network gateway can take up to 45 minutes to complete. When you create a virtual network gateway, gateway VMs are deployed to the gateway subnet and configured with the settings that you specify. After you create a VPN gateway, you can create an IPsec/IKE VPN tunnel connection between that VPN gateway and another VPN gateway (VNet-to-VNet), or create a cross-premises IPsec/IKE VPN tunnel connection between the VPN gateway and an on-premises VPN device (Site-to-Site). You can also create a Point-to-Site VPN connection (VPN over OpenVPN, IKEv2, or SSTP), which lets you connect to your virtual network from a remote location, such as from a conference or from home.
For more information, see What is VPN Gateway?
2) Manage Authentications
Weak authentication is another concern in supply chain risk management. Software generally ships with default credentials, but sometimes hard-coded default credentials are exposed in the code. Azure Active Directory provides the capabilities to set granular authentication controls for users, applications and services. Azure Active Directory provides administrators the flexibility to apply granular user authentication per their requirements. As an administrator, choosing authentication methods for Azure Multi-Factor Authentication and self-service password reset (SSPR) it is recommended that you require users to register multiple authentication methods. When an authentication method is not available for a user, they can choose to authenticate with another method. Authentication methods include password, security questions, email address, Microsoft Authenticator app, OATH Hardware token, SMS, Voice call, and App passwords. For more information, see Authentication methods.
3) Implement Boundary Protections
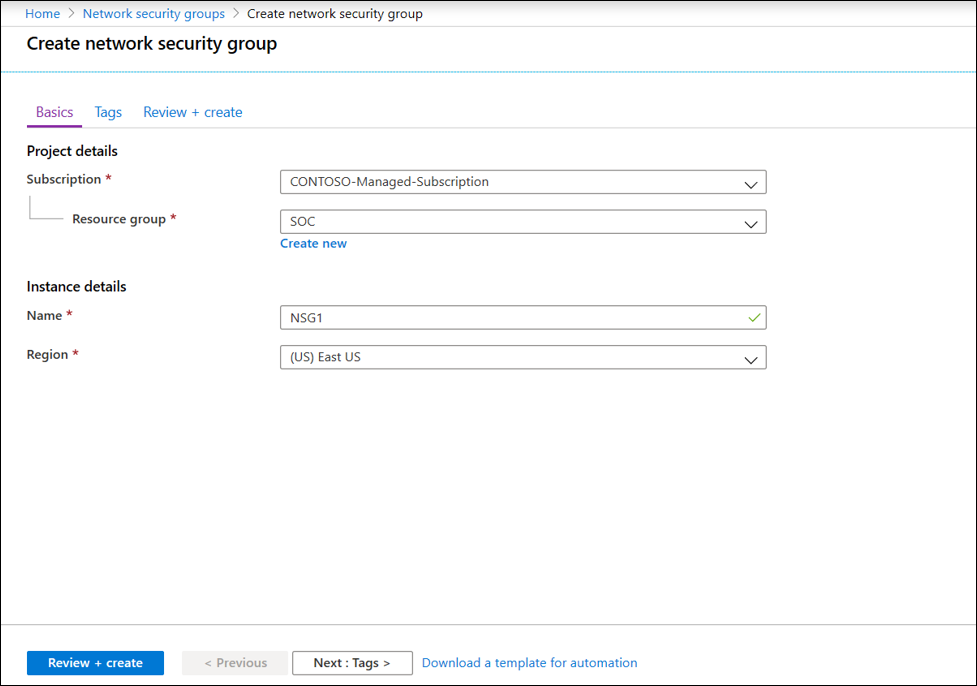
Boundary protections are a critical control in Zero Trust models and are another effective control in protecting supply chain risk management. Boundary controls can contain malware outbreaks such as ransomware which can traverse from partner networks and shut down entire organizations. Azure provides Network Security Groups to filter the type of network traffic that can flow in and out of virtual network subnets and network interfaces. Create a network security group via the following steps:
1) Secure and Monitor Remote Access
Partner remote access to a network can introduce vulnerabilities if not properly implemented, secured and controlled. Azure has several options to facilitate remote access including virtual network gateway. A virtual network gateway is composed of two or more VMs that are deployed to a specific subnet you create called the gateway subnet. Virtual network gateway VMs contain routing tables and run specific gateway services. ]
VPN gateways can be deployed in Azure Availability Zones. This brings resiliency, scalability, and higher availability to virtual network gateways. Deploying gateways in Azure Availability Zones physically and logically separates gateways within a region, while protecting your on-premises network connectivity to Azure from zone-level failures.
Creating a virtual network gateway can take up to 45 minutes to complete. When you create a virtual network gateway, gateway VMs are deployed to the gateway subnet and configured with the settings that you specify. After you create a VPN gateway, you can create an IPsec/IKE VPN tunnel connection between that VPN gateway and another VPN gateway (VNet-to-VNet), or create a cross-premises IPsec/IKE VPN tunnel connection between the VPN gateway and an on-premises VPN device (Site-to-Site). You can also create a Point-to-Site VPN connection (VPN over OpenVPN, IKEv2, or SSTP), which lets you connect to your virtual network from a remote location, such as from a conference or from home.
For more information, see What is VPN Gateway?
2) Manage Authentications
Weak authentication is another concern in supply chain risk management. Software generally ships with default credentials, but sometimes hard-coded default credentials are exposed in the code. Azure Active Directory provides the capabilities to set granular authentication controls for users, applications and services. Azure Active Directory provides administrators the flexibility to apply granular user authentication per their requirements. As an administrator, choosing authentication methods for Azure Multi-Factor Authentication and self-service password reset (SSPR) it is recommended that you require users to register multiple authentication methods. When an authentication method is not available for a user, they can choose to authenticate with another method. Authentication methods include password, security questions, email address, Microsoft Authenticator app, OATH Hardware token, SMS, Voice call, and App passwords. For more information, see Authentication methods.
3) Implement Boundary Protections
Boundary protections are a critical control in Zero Trust models and are another effective control in protecting supply chain risk management. Boundary controls can contain malware outbreaks such as ransomware which can traverse from partner networks and shut down entire organizations. Azure provides Network Security Groups to filter the type of network traffic that can flow in and out of virtual network subnets and network interfaces. Create a network security group via the following steps:
- On the Azure portal menu or from the Home page, select Create a resource.
- Select Networking, then select network security group.
- Enter a Name for the network security group, select your Subscription, create a new Resource group, or select an existing resource group, select a Location, and then select Create.
- API App should only be accessible over HTTPS
- Audit Windows web servers that are not using secure communication protocols
- Deploy requirements to audit Windows web servers that are not using secure communication protocols
- Function App should only be accessible over HTTPS
- Only secure connections to your Redis Cache should be enabled
- Secure transfer to storage accounts should be enabled
- Web Application should only be accessible over HTTPS
- In the Policy portal, select Assignments
- Select Assign Policy from the top of the Policy - Assignments page.
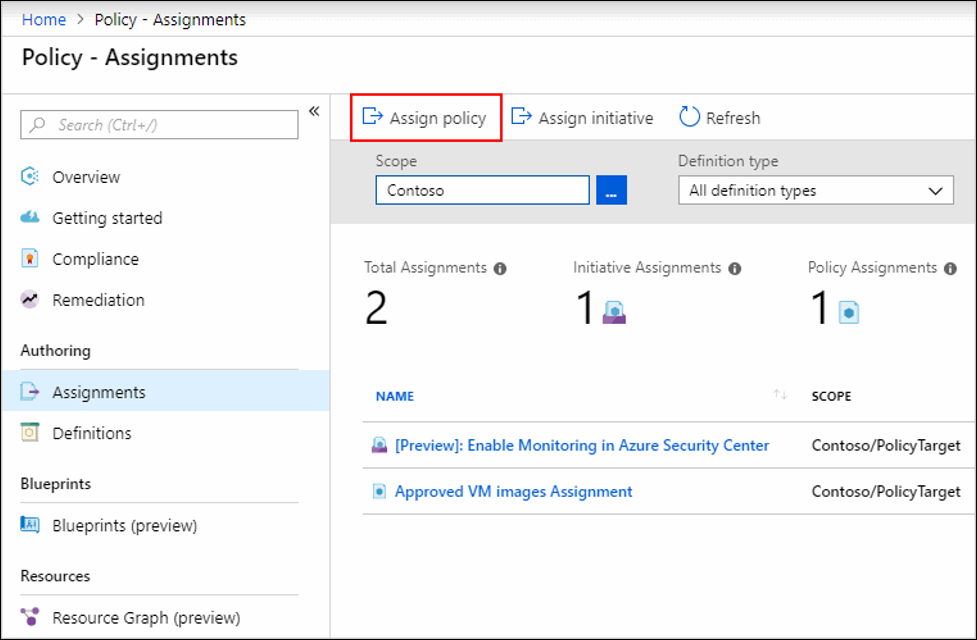
- On the Assign Policy page, select the Scope by clicking the ellipsis and selecting either a management group or subscription.
- Select the Policy definition ellipsis, search for the desired policy definition and click Select.
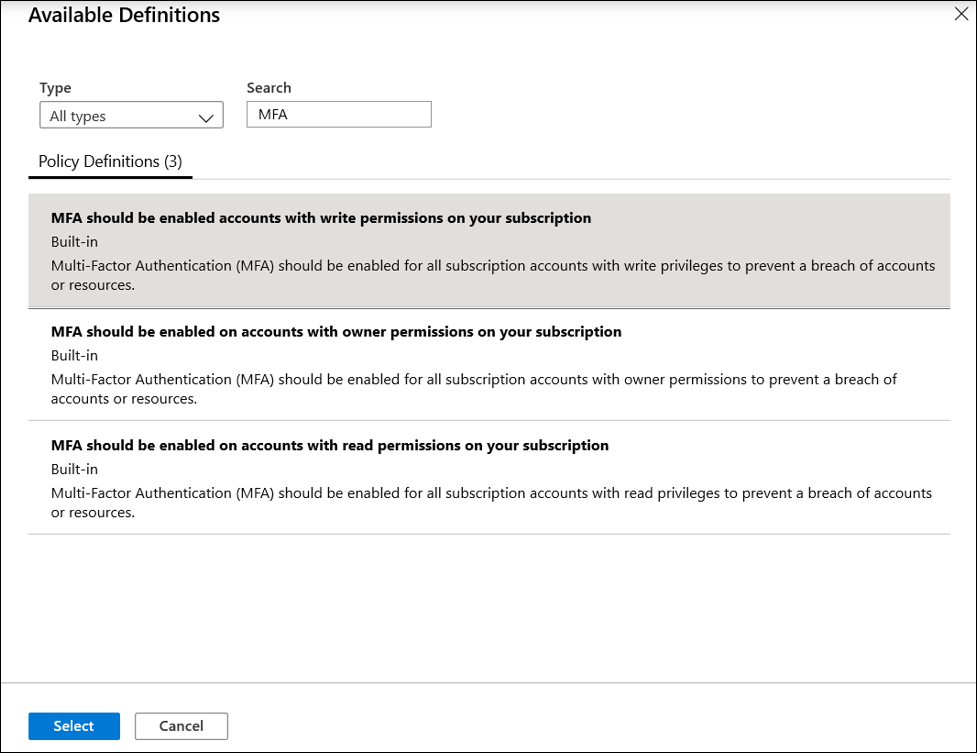
- Set an Assignment name, Description, and set Policy Enforcement to Enabled.
- Click Assign.
 6) Configure Disaster Recovery
Disaster recovery capabilities such as backup are a key tenant to supply chain risk management. Malware outbreaks such as ransomware can bring operations to a standstill so rapid recovery capabilities are critical to protecting organizations. Azure Backup provides capabilities to backup on-premises resources, Azure VMs, Azure File shares, SQL Servers, databases and many more cloud resources. The first step in backing up resources is creating a Recovery Services vault. A Recovery Services vault is an entity that stores the backups and recovery points created over time. The Recovery Services vault also contains the backup policies that are associated with the protected virtual machines. Create a Recovery Services Vault via the steps below:
6) Configure Disaster Recovery
Disaster recovery capabilities such as backup are a key tenant to supply chain risk management. Malware outbreaks such as ransomware can bring operations to a standstill so rapid recovery capabilities are critical to protecting organizations. Azure Backup provides capabilities to backup on-premises resources, Azure VMs, Azure File shares, SQL Servers, databases and many more cloud resources. The first step in backing up resources is creating a Recovery Services vault. A Recovery Services vault is an entity that stores the backups and recovery points created over time. The Recovery Services vault also contains the backup policies that are associated with the protected virtual machines. Create a Recovery Services Vault via the steps below:
- In the All services dialog box, enter Recovery Services. The list of resources filters according to your input. In the list of resources, select Recovery Services vaults.
- On the Recovery Services vaults dashboard, select Add.
- Set a respective Name, Subscription, Resource group, and Location for the Recovery Services vault.
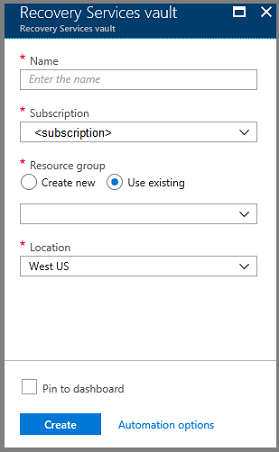
- Select Create and monitor the status of your vault via the Notifications area in the upper-right corner of the portal.
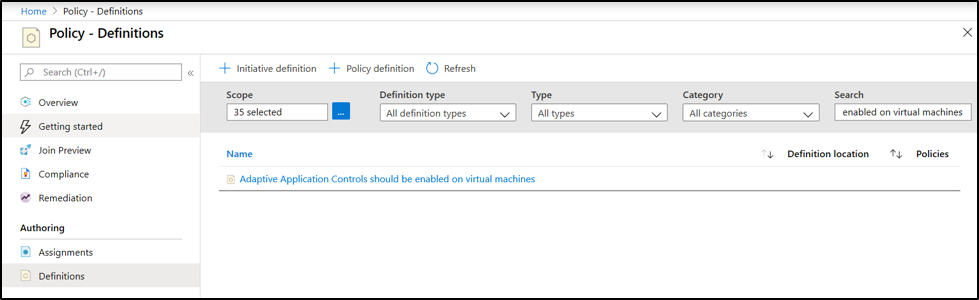 For more information, see Adaptive application controls.
8) Enable Malicious Code Protections
Malware detection is critical to identify threats to your organization and your suppliers. Rapid detection and remediation are key to maintaining operations and reducing downtime. Azure Sentinel has several built-in rules for monitoring files for suspicious actions and malware. Azure Sentinel can connect an endpoint security solution such as Microsoft Defender ATP for malware alerting via Azure Sentinel connectors. By using Fusion technology that’s based on machine learning, Azure Sentinel can automatically detect multistage attacks by combining anomalous behaviors and suspicious activities that are observed at various stages of the kill-chain. Azure Sentinel then generates incidents that would otherwise be very difficult to catch. These incidents encase two or more alerts or activities. By design, these incidents are low volume, high fidelity, and high severity. Customized for your environment, this detection not only reduces false positive rates but can also detect attacks with limited or missing information. For more information on defending against malware with endpoint security in federal information systems, see Securing the endpoint: designing SaaS service implementations to meet federal policy.
9) Audit Access to Resources
Auditing access to resources is another central tenant to both information security and supply chain risk management. It’s important to log all access to your resources including connections from partners, contractors, and suppliers. It’s also important to maintain these logs for formal auditing to attest to organizational compliance requirements. Azure Monitor maximizes the availability and performance of your applications and services by delivering a comprehensive solution for collecting, analyzing, and acting on telemetry from your cloud and on-premises environments. It helps you understand how your applications are performing and proactively identifies issues affecting them and the resources they depend on. Azure Monitor provides the following capabilities to support audit and logging requirements:
For more information, see Adaptive application controls.
8) Enable Malicious Code Protections
Malware detection is critical to identify threats to your organization and your suppliers. Rapid detection and remediation are key to maintaining operations and reducing downtime. Azure Sentinel has several built-in rules for monitoring files for suspicious actions and malware. Azure Sentinel can connect an endpoint security solution such as Microsoft Defender ATP for malware alerting via Azure Sentinel connectors. By using Fusion technology that’s based on machine learning, Azure Sentinel can automatically detect multistage attacks by combining anomalous behaviors and suspicious activities that are observed at various stages of the kill-chain. Azure Sentinel then generates incidents that would otherwise be very difficult to catch. These incidents encase two or more alerts or activities. By design, these incidents are low volume, high fidelity, and high severity. Customized for your environment, this detection not only reduces false positive rates but can also detect attacks with limited or missing information. For more information on defending against malware with endpoint security in federal information systems, see Securing the endpoint: designing SaaS service implementations to meet federal policy.
9) Audit Access to Resources
Auditing access to resources is another central tenant to both information security and supply chain risk management. It’s important to log all access to your resources including connections from partners, contractors, and suppliers. It’s also important to maintain these logs for formal auditing to attest to organizational compliance requirements. Azure Monitor maximizes the availability and performance of your applications and services by delivering a comprehensive solution for collecting, analyzing, and acting on telemetry from your cloud and on-premises environments. It helps you understand how your applications are performing and proactively identifies issues affecting them and the resources they depend on. Azure Monitor provides the following capabilities to support audit and logging requirements:
- Detect and diagnose issues across applications and dependencies with Application Insights.
- Correlate infrastructure issues with Azure Monitor for VMs and Azure Monitor for Containers.
- Drill into your monitoring data with Log Analytics for troubleshooting and deep diagnostics.
- Support operations at scale with smart alerts and automated actions.
- Create visualizations with Azure dashboards and workbooks.
- Reach the Optimal State in your Zero Trust Journey
- The Zero Trust Maturity Model
- Zero Trust: A New Era of Security
- Implementing a Zero Trust Security Model at Microsoft
- Zero Trust Strategy: What Good Looks Like
- Securing Mobile: Designing SaaS Service Implementations to Meet Federal TIC Policy
- Implementing Zero Trust with Microsoft Azure: Identity and Access Management
- Protecting Cloud Workloads for Zero Trust with Azure Security Center
- Monitoring Cloud Security for Zero Trust with Azure Sentinel
- Enforcing Policy for Zero Trust with Azure Policy
- Insider Threat Monitoring for Zero Trust with Microsoft Azure
[i] National Institute of Standards and Technology. (2019, September 1). Draft NIST Special Publication 800-207: Zero Trust Architecture. Retrieved January 25, 2020, from https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-207-draft.pdf [ii] Cybersecurity and Infrastructure Security Agency. (2019, December 1). Trusted Internet Connections 3.0: Volume 3 Security Capabilities Handbook. Retrieved January 22, 2020, from https://www.cisa.gov/sites/default/files/publications/Draft%20TIC%203.0%20Vol.%203%20Security%20Capabilities%20Handbook.pdf [iii] National Institute of Standards and Technology. (2018, April 16). Framework for Improving Critical Infrastructure Cybersecurity. Retrieved January 22, 2020, from https://nvlpubs.nist.gov/nistpubs/CSWP/NIST.CSWP.04162018.pdf [iv] National Institute of Standards and Technology. (2015, April 1). NIST Special Publication 800-161: Supply Chain Risk Management Practices for Federal Information Systems and Organization. Retrieved January 26, 2020, from https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-161.pdf
