Overview & Use Case
Thanks to Ivan Ovchinnikov, Lead integration developer at Group-IB, Rijuta Kapoor from Microsoft Azure Sentinel Threat Intelligence team, Sreedhar Ande from Microsoft Azure Sentinel PG, the whole Group-IB Threat Intelligence and Azure Sentinel Threat Intelligence Product Group teams for the technical brainstorming, contributing and proof reading!
Group-IB Threat Intelligence & Attribution (TI&A) is a system for analyzing and attributing cyberattacks, threat hunting, and protecting network infrastructure based on data relating to adversary tactics, tools and activity. TI&A combines unique data sources and experience in investigating high-tech crimes and responding to complex multi-stage attacks worldwide. The system stores data on threat actors, domains, IPs, and infrastructures collected over the last 15 years, including those that criminals attempted to wipe out. The functionality of the system helps customize it to the threat landscape not only relevant to a particular industry, but also to a specific company in a certain country. Below is the high-level architecture of Group-IB TI&A:
SOC team requirement is to ingest Group-IB TI&A feeds & indicators based on multiple TI collections to Azure Sentinel (and writes them to Microsoft Security Graph API to be listed under Azure Sentinel ThreatIntelligenceIndicators table and custom log tables as well) for automatic scanning and detecting matched TI feeds/indicators across their organizational data sources logs for further investigation and analysis.
Implementation
First let’s understand and get more technical details on the Group-IB TI&A collections to see how we can ingest and map these feeds/indicators to the Azure Sentinel Threat Intelligence data types via TI&A APIs and Azure Sentinel Automation (Playbooks):
gib-tia | Collection | Has Indicators | Indicators Content | Description |
GIBTIA_APT_Threats | apt/threat | Yes | GIB APT Threat Indicator(IPv4)
| Group-IB continuously monitors activities undertaken by hacker groups, investigate, collect, and analyze information about all emerging and ongoing attacks. Based on this information, we provide IOC’s related to APT Groups Attacks |
GIBTIA_APT_ThreatActor | apt/threat_actor | No | N/A | This collection contains APT groups’ info, with detailed descriptions |
GIBTIA_Attacks_ddos | attacks/ddos | Yes | GIB DDoS Attack(IPv4) | The “DDoS attacks” collection contains a DDoS Attacks targets and C2 indicators |
GIBTIA_Attacks_deface | attacks/deface | Yes | GIB Attack Deface(url) | The “Deface” collection contains information about online resources that have become subject to defacement attacks (the visual content of a website being substituted or modified) |
GIBTIA_Attacks_phishing | attacks/phishing | Yes | GIB Phishing Domain(domain)
| The “Attacks Phishing” collection provides information about various phishing resources (including URLs, Domains and IPs.) |
GIBTIA_Attacks_phishing_kit | attacks/phishing_kit | Yes | GIB Phishing Kit Email(email) | The “Atacks Phishing Kits” collection contains information about the archives of phishing kits. Emails gotten from kits can be obtained as indicators |
GIBTIA_BP_phishing | bp/phishing | Yes | GIB Phishing Domain(domain)
| The “BP Phishing” collection provides events related to clients company |
GIBTIA_BP_phishing_kit | bp/phishing_kit | Yes | GIB Phishing Kit Email(email) | The “BP Phishing Kit” collection provides phishing kits related to clients company |
GIBTIA_Compromised_account | compromised/account | Yes | GIB Compromised Account CNC(url)
| This collection contains credentials collected from various phishing resources, botnets, command-and-control (C&C) servers used by hackers |
GIBTIA_Compromised_card | compromised/card | Yes | GIB Compromised Card CNC URL(url)
| This collection contains information about compromised bank cards. This includes data collected from card shops, specialized forums, and public sources |
GIBTIA_Compromised_imei | compromised/imei | Yes | GIB Compromised IMEI CNC Domain(domain)
| The section contains data on infected mobile devices, which is obtained by analyzing mobile botnets. It does not contain personal data and is available to all system users |
GIBTIA_Compromised_mule | compromised/mule | Yes | GIB Compromised Mule CNC Domain(domain)
| This section contains information about bank accounts to which threat actors have transferred or plan to transfer stolen money. Man-in-the-Browser (MITB) attacks, mobile Trojans, and phishing kits allow fraudsters to make money transfers automatically. Playbook provides C2 data related to compromitation |
GIBTIA_HI_Threats | hi/threat | Yes | GIB HI Threat Indicator(domain) | Group-IB continuously monitors activities undertaken by hacker groups, investigate, collect, and analyze information about all emerging and ongoing attacks. Based on this information, we provide IOC’s related to Hackers Attacks |
GIBTIA_HI_ThreatActor | hi/threat_actor | No | N/A | This collection contains non-APT groups’ and Individual hackers info, with detailed descriptions |
GIBTIA_Malware_cnc | malware/cnc | Yes | GIB Malware CNC Domain(domain)
| The “Malware” collection contains Malwares C2 detected by group IB |
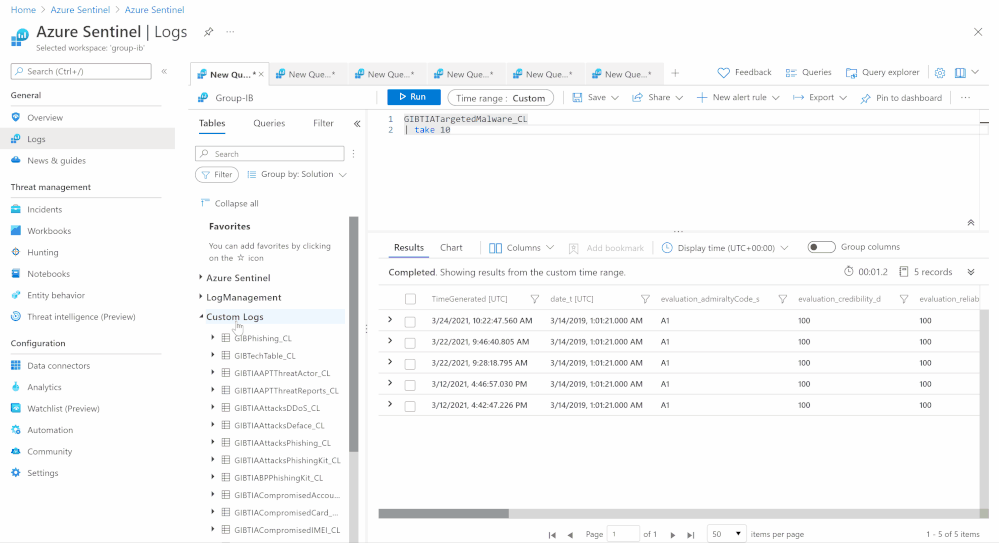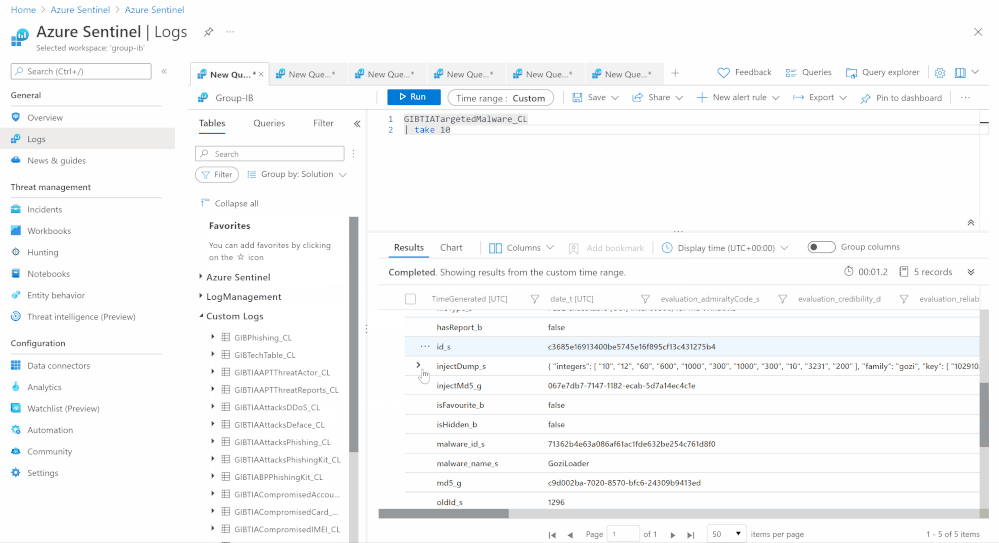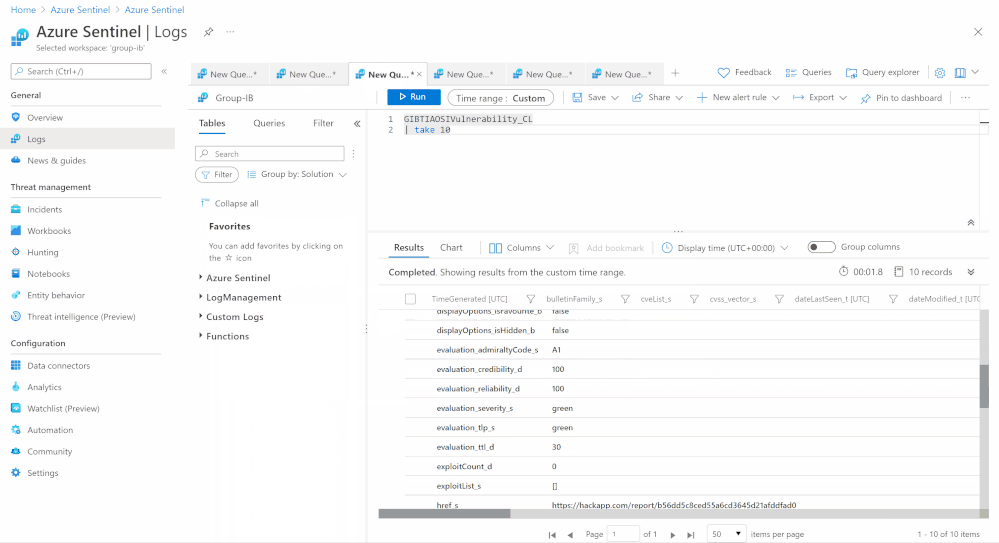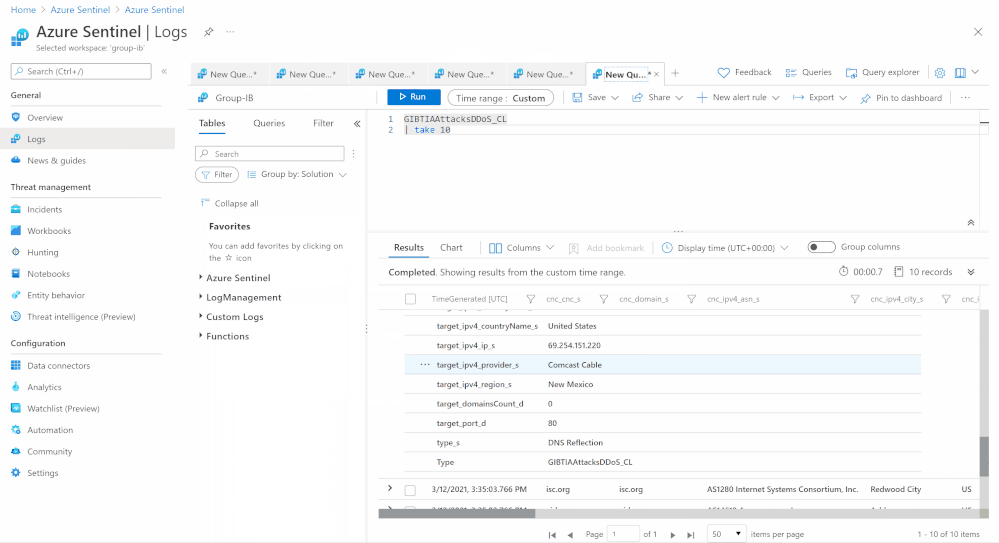
GIBTIA_Malware_Targeted_Malware | malware/targeted_malware | Yes | GIB Malware Targeted Malware(md5)
| The “Targeted Trojans” section contains information about malicious programs targeting the client’s infrastructure. Information is collected by examining a multitude of malicious files and investigating various incidents |
GIBTIA_OSI_GitLeak | osi/git_leak | No | N/A | Open-source repositories such as GitHub contain codes that anyone can search for. They are often used by threat actors planning to attack a specific company. The “Git Leaks” section contains the above data in code repositories |
GIBTIA_OSI_PublicLeak | osi/public_leak | No | N/A | The “Public leaks” collection contains the leaked clinets data collected on popular file-sharing resources or text/information exchange websites |
GIBTIA_OSI_Vulnerability | osi/vulnerability | No | N/A | The “Vulnerabilities” collection displays information about vulnerabilities detected in the software by version |
GIBTIA_Suspicious_ip_open_proxy | suspicious_ip/open_proxy | Yes | GIB Open Proxy Address(IPv4) | The “Open proxy” collection proviedes information about lists of proxy servers that are publicly available on various online resources related to anonymity. In addition, proxy servers may be configured as open proxies intentionally or as a result of misconfiguration or breaches |
GIBTIA_Suspicious_ip_socks_proxy | suspicious_ip/socks_proxy | Yes | GIB Socks Proxy Address(IPv4) | The “Socks proxy” collection providess information about addresses where malware that turns infected computers into SOCKS proxies has been installed. Such computers (bots) are rented out and used in various attacks to ensure the attacker as much anonymity as possible |
GIBTIA_Suspicious_ip_tor_node | suspicious_ip/tor_node | Yes | GIB Tor Node Address(IPv4) | The “Tor Node” collection displays information about Tor exit nodes, which are the final Tor relays in the circuit. The nodes act as a medium between a Tor client and public Internet |
#Deployment Steps
The whole custom connectors code & deployment templates with detailed instructions and considerations already been uploaded at Azure Sentinel github Playbooks repo
Step(1): Azure Sentinel gib-tia Playbooks
- Deploy GIBIndicatorsProcessor playbook first
- Deploy required collections Playbooks and configure the following parameters:
- GIB Username – is a login to access Group-IB TI&A Web Interface
- Save only indicators – set to true if only indicators enrichment is required, otherwise, an additional table in Workspace with full event content will be created
- Some collections provide no indicators, so do not have this parameter configurable and add Group-IB TI&A events only in Log Workspace
- GIB Action – This is an action required to set in a particular indicator type provided through the current collection.(The action to apply if the indicator is matched from within the target Product security tool. Possible values are: unknown, allow, block, alert)
- GIB API URL – is an GIB TI&A API URL
- Configure API Key variable. API Key can be generated in the Profile Section in Group-IB TI&A Web Interface
Step(2): Register an Azure AD App for TI Indicators Graph API Write Access
- Go to Azure Active Directory / App Registrations
- Create +New Registration
- Give it a name. Click Register
- Click API Permissions Blade
- Click Add a Permission
- Click Microsoft Graph
- Click Application Permissions
- Check permissions for ThreatIndicators (ThreatIndicators.ReadWrite.OwnedBy). Click Add permissions
- Click grant admin consent for domain.com
- Click Certificates and Secrets
- Click New Client Secret
- Enter a description, select never. Click Add
- IMPORTANT. Click copy next to the new secret and paste it somewhere temporarily. You cannot come back to get the secret once you leave the blade
- Copy the client ID from the application properties and paste it somewhere as you will need it to be added to the Playbooks
- Also copy the tenant ID from the AAD directory properties blade
Detection & Investigation
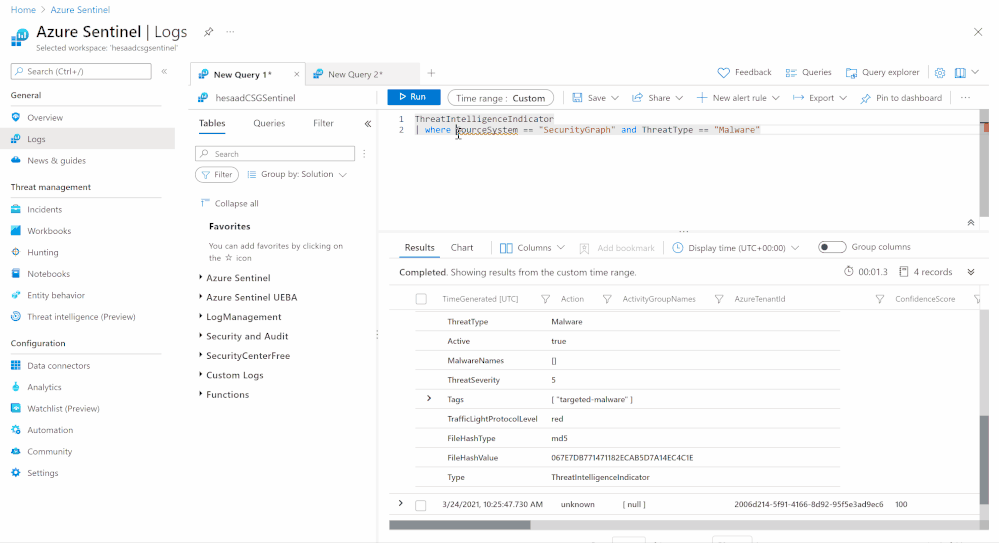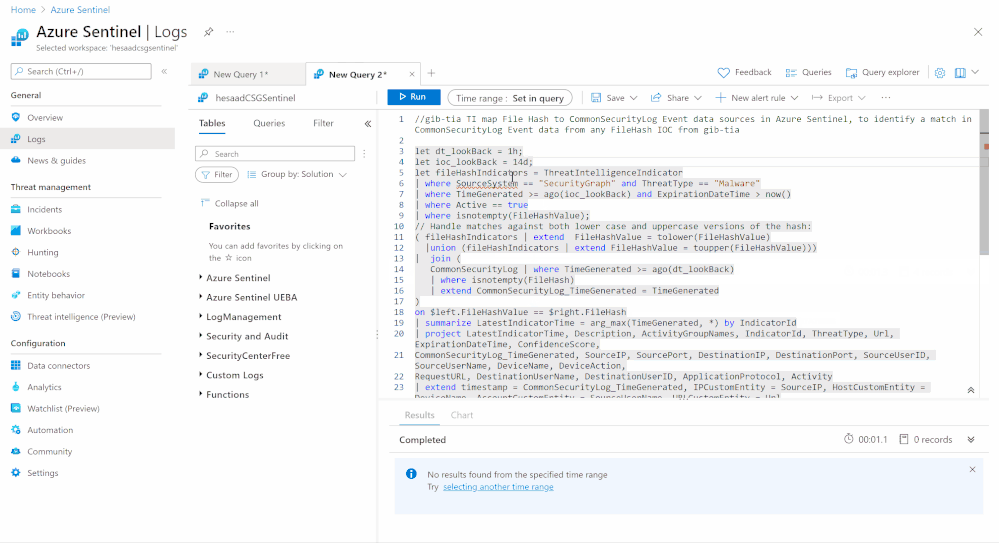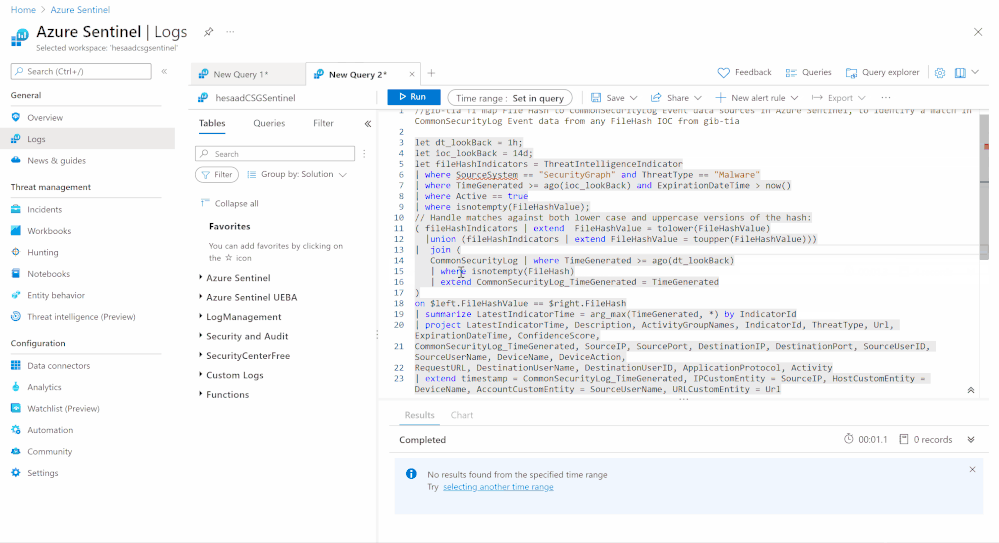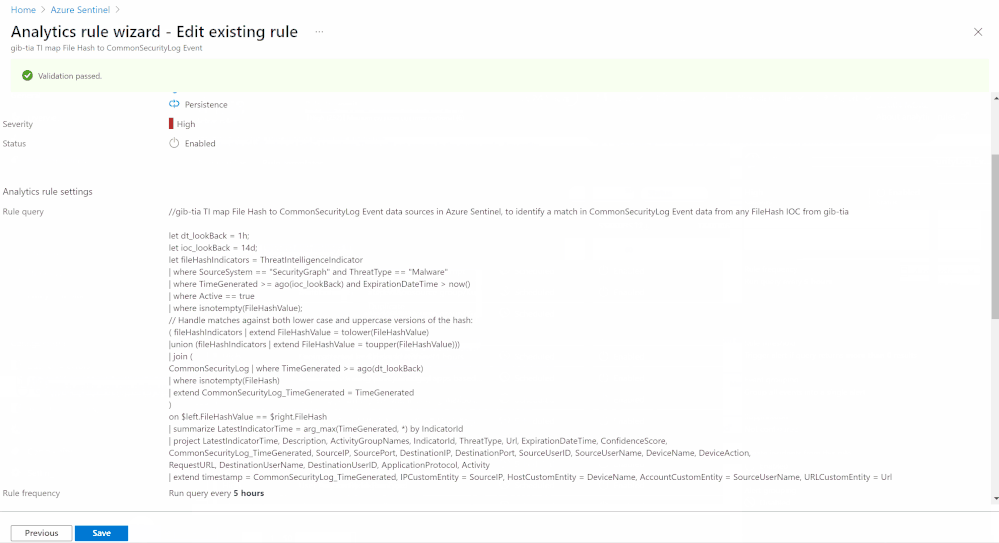
A sample Azure Sentinel Analytics rule to identify a match in CommonSecurityLog Event data from any FileHash IOC from gib-tia, we highly recommend you to check out the list of the Azure Sentinel TI Out of the box TI analytics rules:
let dt_lookBack = 1h;
let ioc_lookBack = 14d;
let fileHashIndicators = ThreatIntelligenceIndicator
| where SourceSystem == “SecurityGraph” and ThreatType == “Malware”
| where TimeGenerated >= ago(ioc_lookBack) and ExpirationDateTime > now()
| where Active == true
| where isnotempty(FileHashValue);
// Handle matches against both lower case and uppercase versions of the hash:
( fileHashIndicators | extend FileHashValue = tolower(FileHashValue)
|union (fileHashIndicators | extend FileHashValue = toupper(FileHashValue)))
| join (
CommonSecurityLog | where TimeGenerated >= ago(dt_lookBack)
| where isnotempty(FileHash)
| extend CommonSecurityLog_TimeGenerated = TimeGenerated
)
on $left.FileHashValue == $right.FileHash
| summarize LatestIndicatorTime = arg_max(TimeGenerated, *) by IndicatorId
| project LatestIndicatorTime, Description, ActivityGroupNames, IndicatorId, ThreatType, Url, ExpirationDateTime, ConfidenceScore,
CommonSecurityLog_TimeGenerated, SourceIP, SourcePort, DestinationIP, DestinationPort, SourceUserID, SourceUserName, DeviceName, DeviceAction,
RequestURL, DestinationUserName, DestinationUserID, ApplicationProtocol, Activity
| extend timestamp = CommonSecurityLog_TimeGenerated, IPCustomEntity = SourceIP, HostCustomEntity = DeviceName, AccountCustomEntity = SourceUserName, URLCustomEntity = Url
Get started today!
We encourage you to try it now!
You can also contribute new connectors, workbooks, analytics and more in Azure Sentinel. Get started now by joining the Azure Sentinel Threat Hunters GitHub community.