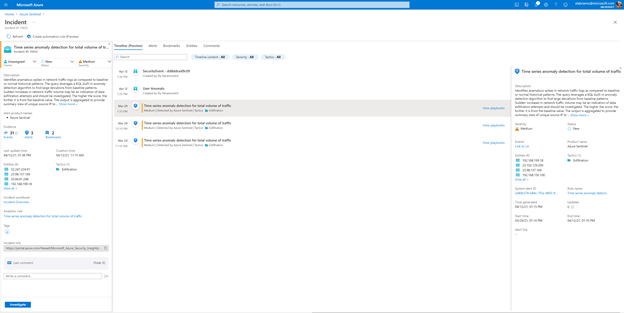
Building a timeline of a cyber security incident is one of the most critical parts of affective incident investigation and response. It is essential in order to understand the path of the attack, its scope and to determine appropriate response measures.
Now in public preview, we are redesigning the Azure Sentinel full incident page to display the alerts and bookmarks that are part of the incident in a chronological order. As more alerts are added to the incident, and as more bookmarks are added by analysts, the timeline will update to reflect the information known on the incidents.
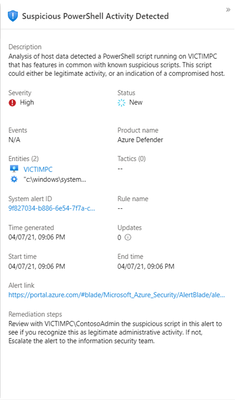
For each alert and bookmark, a side panel will be displayed to show details such as the entities involved, the status, the MITRE tactics used, custom details defined and many other details. Having these details available without further navigation can help with incident trigate and can reduce the overall investigation time.

We plan to extend this offering by adding additional elements to the timeline such as anomalies or activities and including elements from the incident response world such as analyst or automation actions. We will appreciate your feedback as to what will help with you procceses.
For further reading:
- Investigating incident in Azure Sentinel – https://docs.microsoft.com/en-us/azure/sentinel/tutorial-investigate-cases
- On using bookmarks in azure Sentinel – https://docs.microsoft.com/en-us/azure/sentinel/bookmarks