This post has been republished via RSS; it originally appeared at: ITOps Talk Blog articles.
In today’s world we must be able to scale our workloads, whether that be dealing with an internal workload or an external workload serving your organisations’ customers. There are lots of options available to you to implement that scale and deal with the traffic to your workload, let’s walk through some of the options within Azure and help you understand their use cases.
Azure Load Balancer
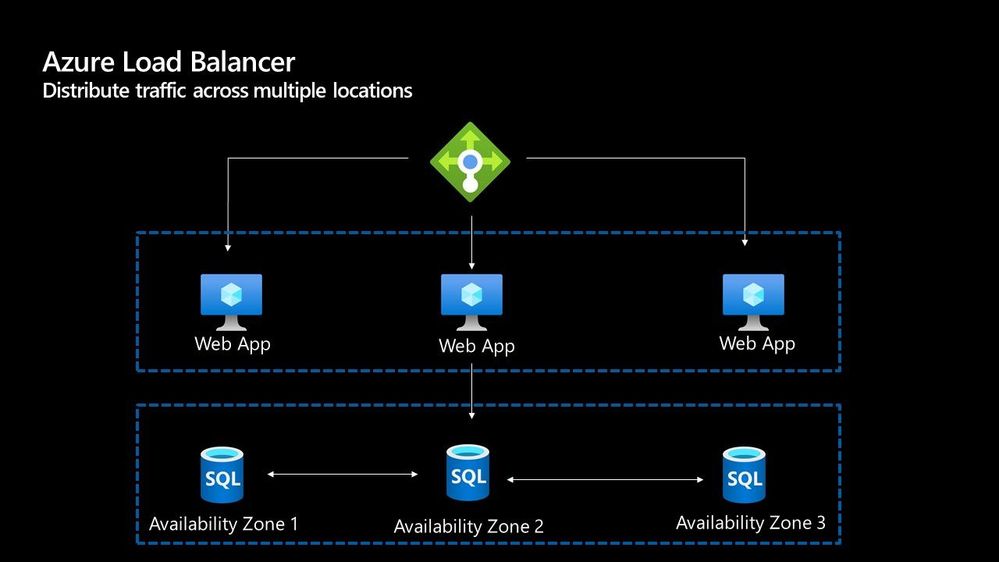
The Azure Load Balancer is one of the first options that you have to help deal with scaling your workload. It supports TCP/UDP based protocols such as HTTP, HTTPS and SMTP and other protocols used within real-time voice and video messaging applications. It helps you distribute traffic to your backend virtual machines and is a fully managed service.
With the load balancer you can distribute traffic either from external traffic or for internal traffic. The Azure Load balancer works on Layer 4 of the OSI model and is a transparent load balancer. Meaning it won’t do anything to the packets that it receives and just sends to them onto the endpoint should depend on the routing algorithm. The Azure Load Balancer has a lot of features, one that I love is the outbound connection feature, which allows you to configure all outbound traffic from your virtual network to the Internet to be displayed as from the frontend IP of the load balancer.
Azure Application Gateway
The Azure Application Gateway is an HTTP or HTTPs load balancer and behaves differently to the networking load balancer. It will take the connection coming into it, terminate and start a new connection to the backend endpoint based on its routing algorithms. This opens new possibilities such as redirections or URL rewrites or header changes.
Two of my favourite features of the Azure Application Gateway are connection draining and autoscaling. Both help give you confidence of running your environment and help save on operational costs.
With connection draining it helps you to gracefully remove backend endpoints to carry out planned maintenance or upgrades. With autoscaling it can start to scale out or in based on the traffic pattern to your Application Gateway. This not only helps to eliminate the guessing game of over provisioning workloads and helps to avoid your operations teams having to manually scale out or in when traffic spikes.
Azure Traffic Manager
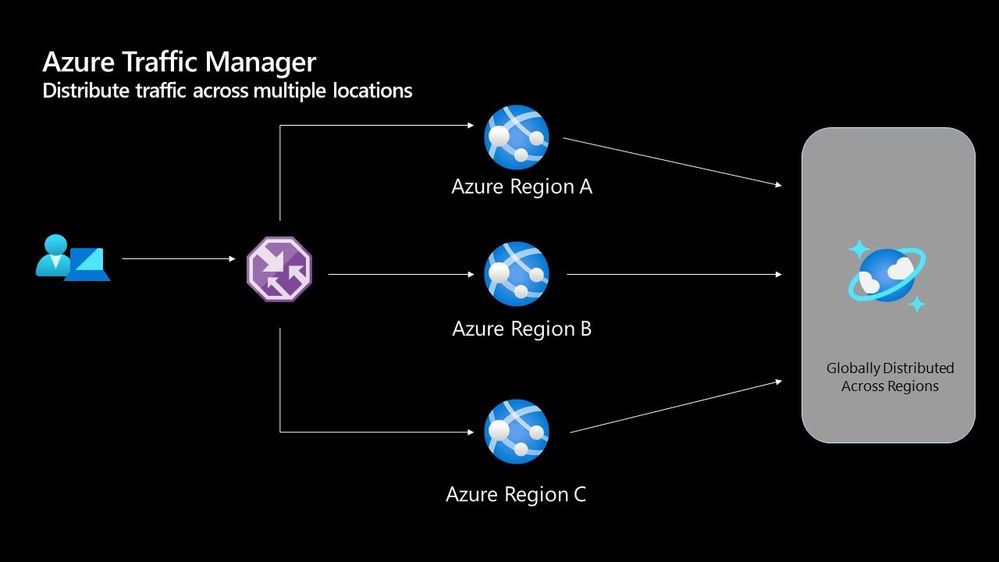
The Azure Traffic Manager is a DNS-based load balancer, it allows you to distribute traffic across your public facing applications. With the traffic manager it will use DNS to direct requests from your users to the appropriate endpoint based on the traffic-routing method that you have configured. Your endpoints can be any Internet-facing service hosted inside OR outside of Azure.
With Traffic Manager you can help to provide great performance to your end users with distributed endpoints through out the globe. The features that I really enjoy is the Real User Measurements and Traffic View features. They can be used to give you a real insight into where your users are based and the performance they are experiencing. And the data that is collected can really help you make informed decisions on how to develop your application in the future.
Azure Front Door
Azure Front Door works at Layer 7 of the OSI model and based on your routing method you can ensure that your customer is routed to the fastest and most available endpoint on offer. Like Traffic Manager, Front Door is resilient to failures, including failures to an entire Azure region. With Front Door you can offload SSL and certificate management, define a custom domain, and provide application security with integrated Web Application Firewall (WAF), with a ton of other features as well.
Your end points can be based within Azure or elsewhere. No matter where or what your endpoints are Front Door will help provide the best experience for your end user.
Azure DDoS Protection Basic is integrated into the Front Door platform by default and helps to defend against the most common and frequently occurring Layer 7 DNS query floods and layer 3 and 4 volumetric attacks that target public endpoints.
Azure Web Application Firewall
Azure Web Application Firewall (WAF) can also be used to protect your Front Door and Application Gateway implementations. Because the WAF policies are “global resources” you can apply the same policy to your Front Door and Application Gateway implementations and have a consistent approach to prevention and detection.
Which one?
There are times when it’s not a question of which one should I use, as there are scenarios when you would use two of these options together to provide the best experience all round. In preview there is a feature within the Azure Portal where it will walk you through some questions and give some advice on the best options for you – Load Balancing – help me choose.
Each of the load balancer have unique features and unique use cases, and as I said can often be used in combination together. For examples of how to use them in different scenarios be sure to check out the Azure Architecture Centre for reference architecture diagrams to get your imagination sparked!