This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Tech Community.
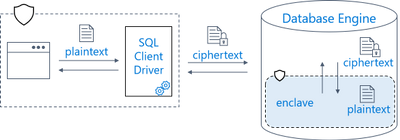
Always Encrypted helps prevent the exfiltration of sensitive data by rogue DBAs, admins, and cloud operators. Your data gets transparently encrypted and decrypted on the client side and it is never revealed in plaintext in the database system.
Always Encrypted with secure enclaves extends Always Encrypted by allowing sensitive data to be decrypted within a server-side trusted execution environment, called a secure enclave - a protected region of memory within the database system process, which appears as a black box to the database system and other processes on the hosting machine. There is no way to view any data or code inside the enclave from the outside. Thus, the enclave can safely perform computations on plaintext data within the database system.
Always Encrypted with secure enclaves, now generally available in Azure SQL Database, provides two main benefits: in-place encryption and rich confidential queries.
In-place encryption
Without secure enclaves, setting up Always Encrypted can be challenging – since the database system has, by design, no access to cryptographic keys, encrypting a column requires data to be moved and encrypted outside of the database. As a result, the encryption process can take a long time and is prone to network errors. And, if you need to re-encrypt your column later, for example to rotate the column encryption key or to change the type of encryption, you will face the same challenges again.
With a secure enclave available inside your database system, there is no need to move your data for cryptographic operations. Since the enclave is trusted, a client driver within your application or a tool, such as Azure Data Studio or SQL Server Management Studio, can securely share the keys with the enclave for the duration of cryptographic operations. The enclave can encrypt or re-encrypt columns in-place. This typically results in a dramatic reduction of time needed to perform such operations. One of the customers reported encrypting a column in a table with a few hundred million rows used to take a few days - now, with secure enclaves, in-place encryption completes in only 5 hours.
Rich confidential queries
Most client-side encryption technologies allow no operations on protected data within a database server. Always Encrypted (without secure enclaves) supports only one operation on encrypted columns: equality comparison. Many applications, however, require richer data processing. For example, personally identifiable information (PII), such as people names, addresses, national identification numbers, or credit card numbers often require pattern matching or sorting. If you want to protect your data from malicious admins and perform such computations without enclaves, the only option is to move the data to the client-side and process it within your application. However, this approach does not scale to large data sets and requires extensive application changes.
Always Encrypted with secure enclaves enables pattern matching, range comparisons, sorting, and more on encrypted columns, allowing you to use the database system for what it’s designed for: querying your data. There is no need for refactor your apps and expensive data movement.
Royal Bank of Canada is an example of a customer who is already leveraging the power of rich confidential computations provided by Always Encrypted with secure enclaves:
Our project focuses on working with different partners to bring more value to respective customers by exchanging encrypted data wherein no person, process or system can see each other’s data. Always Encrypted with secure enclaves in Azure SQL Database provides us the framework for managing encrypted data and running queries on top of them, while minimizing work on our end. By leveraging Always Encrypted that helps ensure that RBC and Microsoft don’t have access to customer data, we can create a new platform to provide services that we couldn’t offer before. — Eddy Ortiz, VP of Solution Acceleration and Innovation, Royal Bank of Canada
You can learn more about RBC’s application here.
Next steps
For more information and to get started with Always Encrypted with secure enclaves in Azure SQL Database, see:
- Always Encrypted with secure enclaves - documentation
- Tutorial: Getting started with Always Encrypted with secure enclaves in Azure SQL Database
- GitHub demo/sample
- Inside Azure Datacenter Architecture with Mark Russinovich (video)
- Data Exposed episode (video)
To learn about other confidential computing technologies and services in Azure, see Azure confidential computing documentation.