This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Tech Community.
Protecting sensitive data from risky or inappropriate copying, sharing, transfer, or use is a top priority for government organizations. Remote delivery of public services and data sharing across devices have created renewed emphasis on providing strong and coordinated protection on the endpoints government employees use every day. To help government organizations accelerate their deployment of a comprehensive information protection strategy, we are announcing the public preview of Microsoft Endpoint Data Loss Prevention (DLP) to GCC, GCC High and DoD customers.
At Microsoft, we have long invested in developing cutting-edge information protection solutions for our customers. Microsoft Information Protection (MIP) is a built-in, intelligent, unified, and extensible solution that understands and classifies data, keeps it protected, and prevents data loss across Microsoft 365 apps (e.g., Word, PowerPoint, Excel, Outlook), services (e.g., Microsoft Teams, SharePoint, Exchange), third-party SaaS applications, and more – on premises or in the cloud. Endpoint DLP now extends MIP classification and protection to devices.
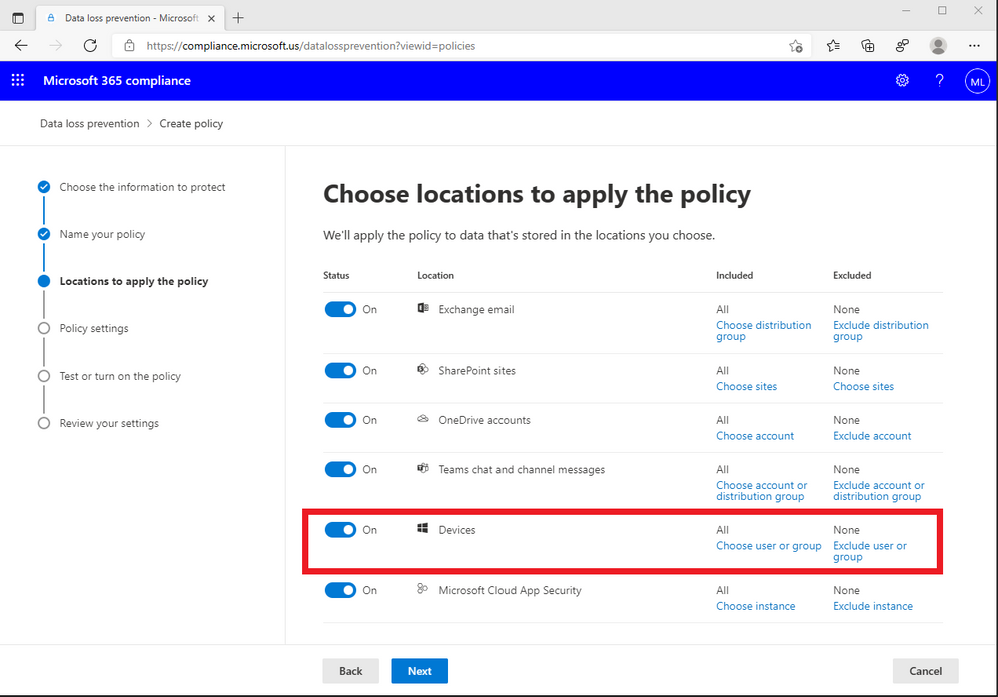
With Endpoint DLP, Microsoft 365 GCC, GCC High and DoD customers only need to create DLP policies once in the Microsoft 365 compliance center. They can then apply the policies to Exchange, Teams, SharePoint, OneDrive for Business, and now – to endpoints as well. All that is required is for the endpoint to be onboarded in their specific cloud environment using their established device management onboarding process.
Figure 1: DLP policy location choices (including ‘Devices’) in the Microsoft 365 compliance center
Endpoint DLP identifies and protects information on endpoints. Endpoint DLP does not restrict or limit the use of applications, web browsers, or other services when sensitive data is not present. It delivers three core capabilities: Native protection, seamless deployment, and integrated insights.
Native protection
Endpoint DLP is native to Windows 10 and the new Microsoft Edge browser. There is no need to install or manage additional DLP software on Windows 10 machines anymore. Providing DLP experiences natively on the endpoint has many benefits.
A familiar look and feel users are already accustomed to from applications and services they use every day is just the beginning. Endpoint DLP also reduces end-user training time and alert confusion, increases user confidence in prescribed guidance and remediations, and improves policy compliance – without reducing productivity.
Users are automatically alerted when they take an inappropriate or risky action with sensitive data and are provided with actionable policy tips and guidance to remediate properly. For example, in Figure 2, a user attempts to copy sensitive data from the Word document – Project Obsidian Spec.docx – which contains sensitive information about an updated engine chip design. In this example, the policy is set as ‘Block’ without the option to Override. When the user performs the activity – in this case, copying sensitive data, the event is recorded, and the user is notified that this action is being blocked because copying this data is not allowed, per the DLP policy.
Figure 2: User alerted not to copy sensitive data from a Word document
The user experience for third-party applications is similar. In Figure 3 below, a user tries to copy a document with sensitive data – Project Obsidian.pdf – to a personal Dropbox account using Microsoft Edge. In this example, the DLP policy is set as ‘Block with Override.’ The user is notified this action is blocked because copying the file to that specific cloud application is not allowed, and the event is recorded and available for review and analysis in the Microsoft 365 compliance center console.
Figure 3: User alerted in Microsoft Edge to not copy a file containing sensitive data to a cloud file service
Seamless deployment
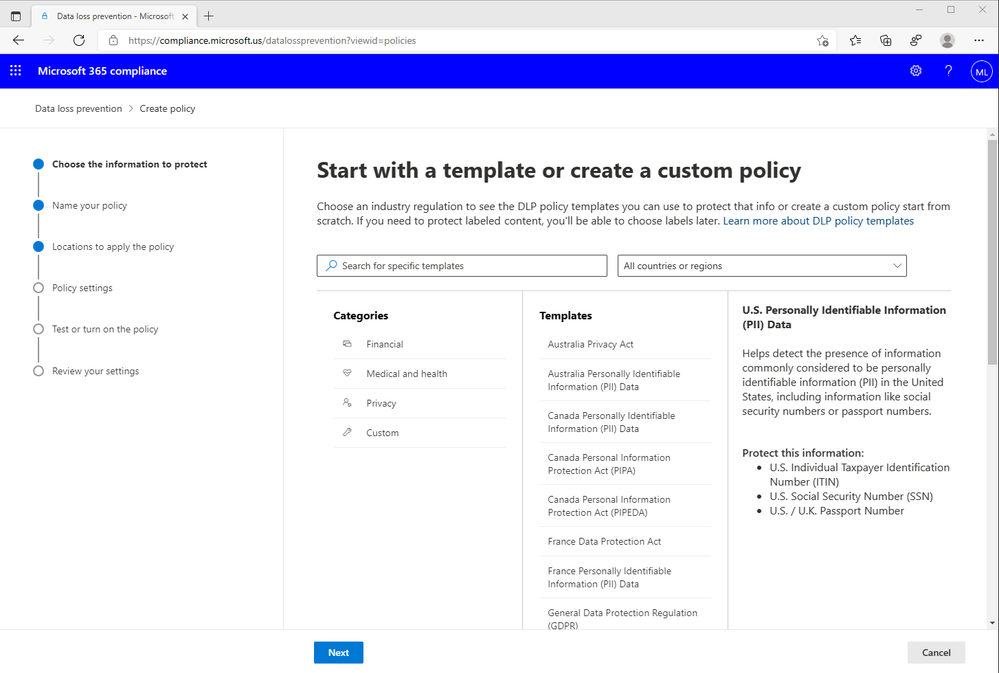
Endpoint DLP is managed via the cloud and the Microsoft 365 compliance center, eliminating the need to deploy and operate additional consoles, event management systems, databases, and hardware on premises. As an integral part of MIP, Endpoint DLP leverages the same robust classification system to identify sensitive data accurately and consistently. It is easy to get started with data protection using our 100+ built-in sensitive data types and over 40 templates for common industry regulations. MIP policies can be deployed to Endpoint DLP without additional reconfiguration. Organizations that use MIP’s intuitive interface to create custom sensitive content identifiers and policies can deploy these to Endpoint DLP without any reconfiguration as well.
Figure 4: Easy policy configuration in the Microsoft 365 Compliance Center
Organizations also require flexibility when deploying policies to ensure they minimize disruptions to users and maximize policy effectiveness. Microsoft DLP solutions offer three different modes to monitor and restrict activities in each DLP policy to ensure the intended compliance objectives are achieved:
- Audit: only records policy violation events without impacting end user activity
- Block with Override: records and blocks the activity, but allows the user to override when they have a legitimate business need
- Block: records and blocks the activity without the ability to override
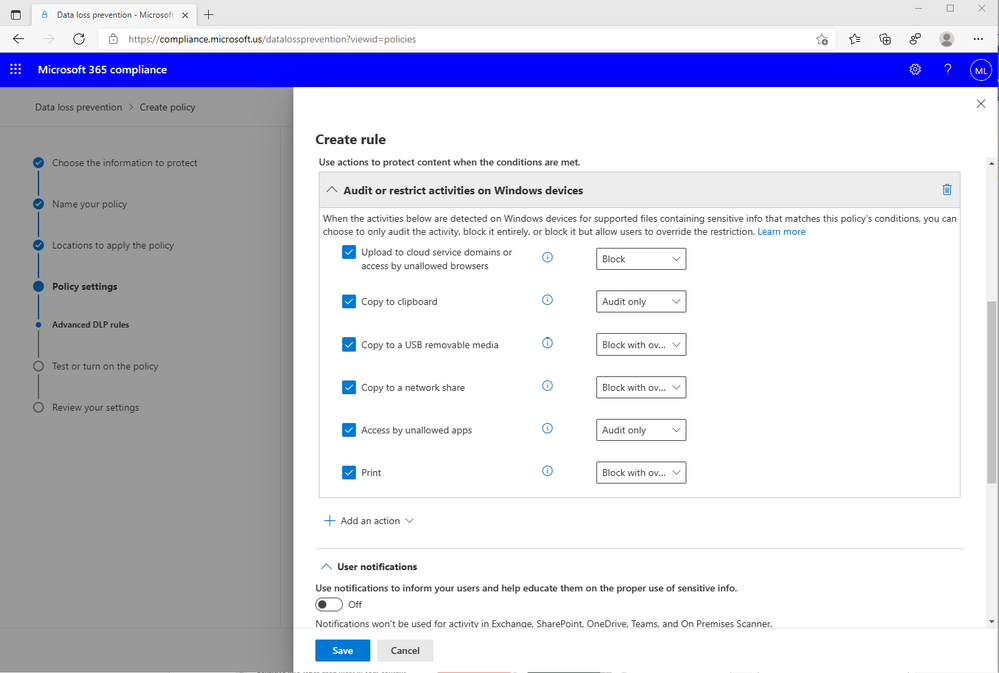
Endpoint DLP can enforce policies for a broad range of activities unique to the endpoint including:
- Copying a sensitive file to an external USB media device
- Copying a sensitive file to a network share
- Uploading a sensitive file to a cloud service
- Printing a sensitive file
- Copying sensitive content to the clipboard
- Accessing a sensitive file by an unallowed app
Figure 5: DLP policy enforcement options
The seamless deployment of Endpoint DLP reduces the strain of incorporating endpoints into existing DLP programs. It increases consistency of compliance across cloud and native workloads and ensures immediate value upon deployment. Device telemetry, for instance, is available in the Microsoft 365 compliance center without having to configure any policies.
Figure 6: Microsoft 365 compliance center view of sensitive data activity including device telemetry
Microsoft 365 compliance center’s Activity Explorer view filters events to identify risky activities and provides details on specific actions, user, and file details. This streamlines responses, and you can quickly remediate potential risks of unintended or intentional data breaches.
Figure 7: Activity Explorer view of sensitive data activity including device telemetry
Integrated insights
Microsoft Endpoint DLP integrates with other Security and Compliance solutions such as MIP, Microsoft 365 Defender, and Insider Risk Management in Microsoft 365. Endpoint DLP enriches the other solutions with precise insights about device activity of sensitive content. This provides comprehensive coverage and visibility of active data protections, device states and user actions required by organizations to meet regulatory and policy compliance.
Insider Risk Management in Microsoft 365 provides organizations with the ability to detect, investigate, and take actions on risky insider activities. Organizations can define a range of acceptable thresholds for a broad set of user and device activities beyond which an alert is generated and displayed in an interactive chart that plots risks and risk level over time for current or past activities. This critical insight can be used in addition to DLP event information to enhance the context of findings and quickly assess the scope of policy violations to help triage intentional versus accidental policy violations.
Endpoint DLP reduces the dependence on individual and uncoordinated solutions from disparate providers to monitor user actions, remediate policy violations, and educate users in context on the correct handling of sensitive data at the endpoint, on-premises and in the cloud.
Get Started
Endpoint DLP is currently available in Public Preview to customers’ tenants with Microsoft 365 G5, Microsoft 365 G5 Compliance, and Microsoft 365 G5 Information Protection and Governance. To learn more about Endpoint DLP, visit our documentation. Endpoint DLP is part of a broad and comprehensive set of capabilities to identify, protect and govern your sensitive data. Get the latest version of Edge Chromium that’s integrated with Endpoint DLP, on the Microsoft Edge page. To learn more about our Information Protection and Governance solutions, on the documentation page.
APPENDIX:
As the advanced compliance specialist for Microsoft 365 compliance solutions, you can connect with me here. Check out other Microsoft 365 compliance resources for US government.
|
Evaluate CMMC posture with Compliance Manager |
|
|
Microsoft CMMC Acceleration Program Update – January 2021 |
|
|
Using Advanced Audit for your forensic investigation capability |
|
|
Advanced eDiscovery demo for Gov cloud (video) |
|
|
Enhanced regulatory, legal and forensic investigation capabilities now in the Government Cloud |
|
|
Microsoft 365 Public Roadmap link to check status on upcoming Microsoft 365 compliance solution features |
Microsoft 365 Roadmap: Microsoft 365 compliance solutions |