Introduction
We are pleased to announce the “Unusual Mass Downgrade AIP Label” anomaly simulator, the first in a series of simulators for Azure Sentinel Anomalies. This simulator will populate the table in Azure Sentinel monitored by the relevant anomaly rule with simulated data. This simulated data will trigger an anomaly. You can review the anomaly by querying the Anomalies table for the anomaly rule’s name. These simulators will enable users to validate that an anomaly rule works in their Sentinel workspace.
What is the Unusual Mass Downgrade AIP rule?
The anomaly rule “Unusual Mass Downgrade AIP Label” detects unusual high volume of downgrade label activity in Azure Information Protection (AIP) logs. It considers “AIP” workload records for a given number of days and determines the sequence of activity performed on documents along with the label applied to classify unusual volume of downgrade activity. Anomalies are saved to the Anomalies table in your Azure Sentinel workspace. No alerts or incidents are generated by these anomalies. You can use anomalies to correlate with other signals to build threat detections, investigate an incident, or hunt for malicious actors.
Value for your Organization
End to End visibility – Enables analysts to gain a deeper understanding of the anomaly rules by injecting simulated data while limiting impacts to production security operations. Familiarization with signals such as those identified in an anomaly rule can assist in production detection and deepen skills necessary to effectively identify malicious behaviors .
Training, Building SOPs, Workflows, Playbooks – SOC operations rely on standardized responses, new rules require periods of observation by analysts to become familiar with the signals and indicators. The anomaly simulator provides a mechanism whereby analysts can preview the associated anomaly information broadly without compromising normal production analysis. Subsequent development of SOPs, Workflows and playbooks can complement training programs and overall knowledge enhancement.
Configuration Steps:
Source code for the anomalies simulator is available on the Azure Sentinel Tools Simulators GitHub space.
Configure the Script
- Edit the writetoLA-AIPMassDowngrade.txt file found on GitHub, save as PowerShell script (PS)
**Ensure your Log Analytics ID, Workspace ID and Tenant ID are correctly entered into the script
Execute the Script
- Open your Azure Sentinel workspace and the Command Line Interface (CLI),
- Upload PS and .csv files
- Execute the script in the Azure CLI with the following command line; & ‘./WriteToLA – AIPMassDowngrade.ps1’
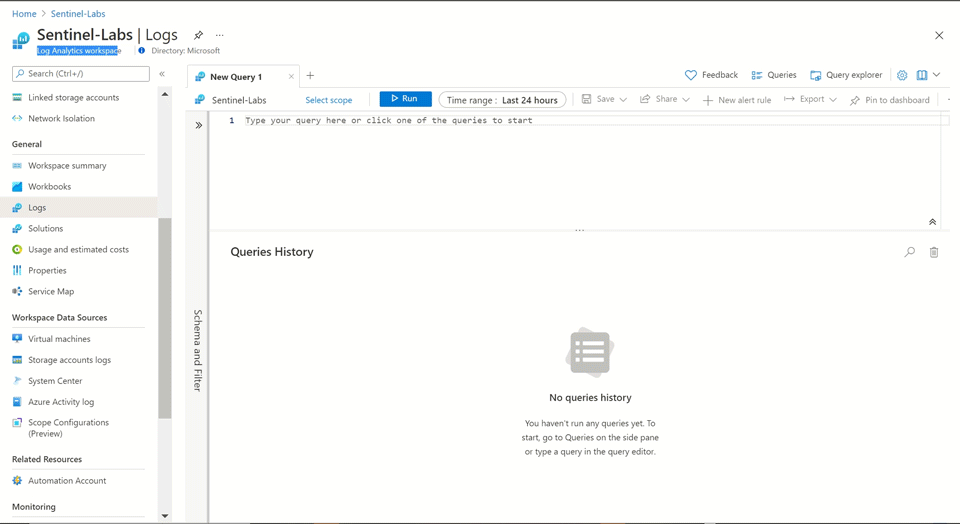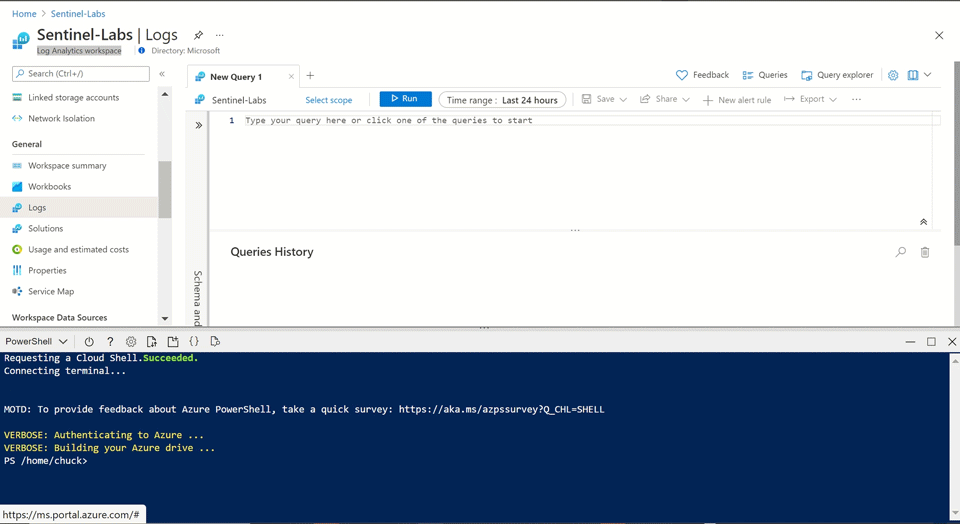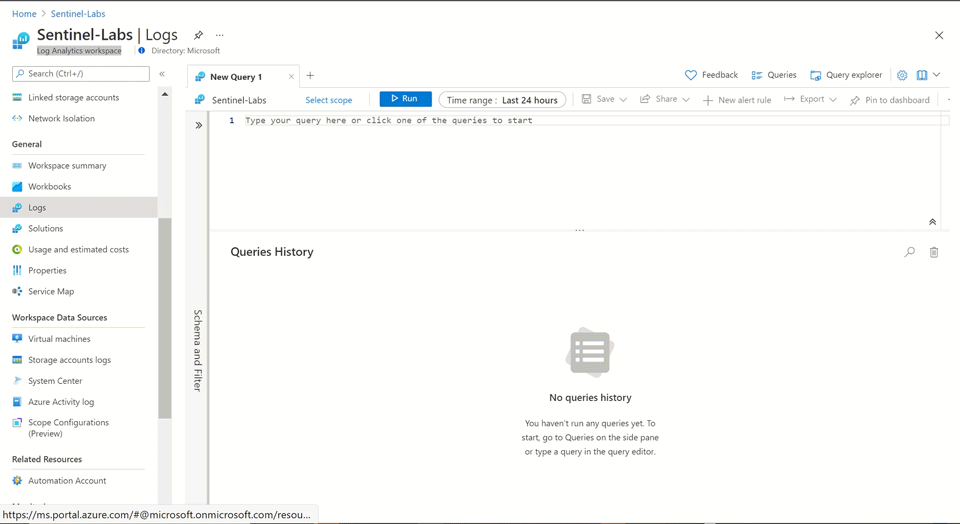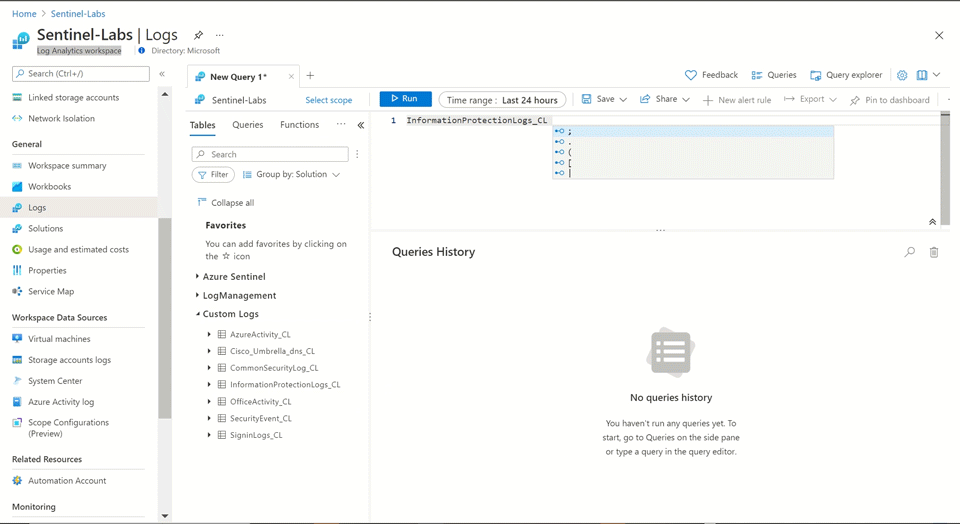
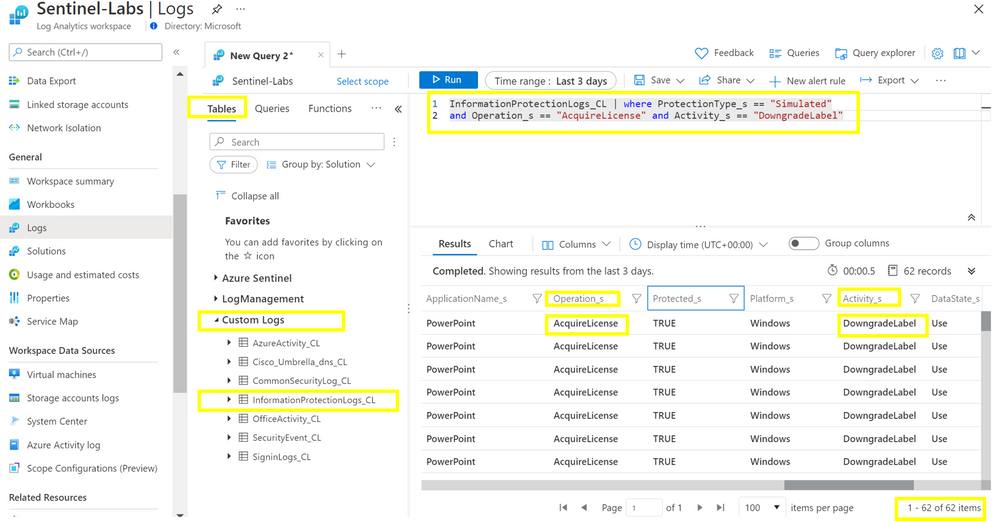
Review the InformationProtection_CL table entries
KQL query:
and Operation_s == “AcquireLicense” and Activity_s == “DowngradeLabel”
Note: 62 simulated entries related to the “Unusual MassDownload AIP Label” have been added.
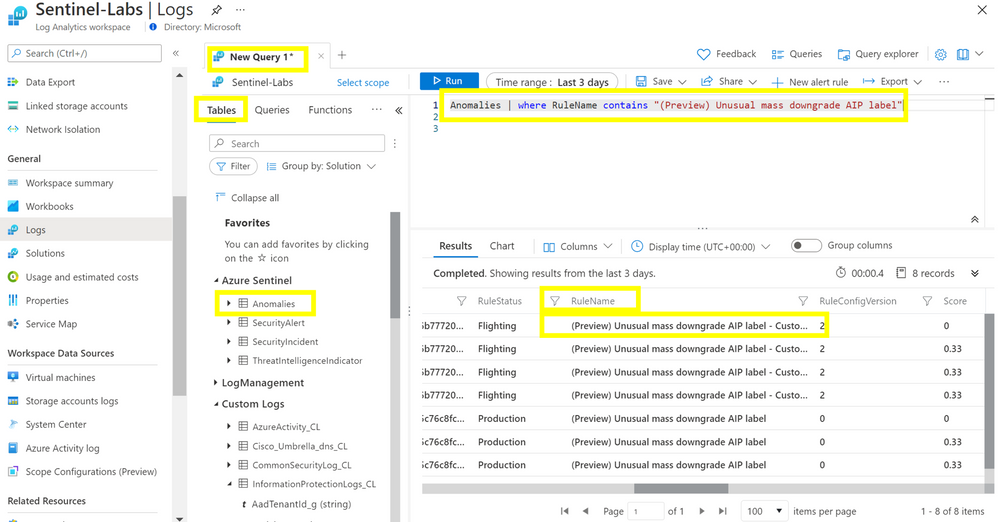
Review the Anomalies table entries
KQL query:
The “contains” operator in the KQL query allows for viewing results in both Flighting and Production status. Results from the script will be immediately visible in the InformationProtection_CL table, but it may take up to 12 hours to show results in the Anomalies table depending on when the data is imported with the PS script.
Reply in the comments section with questions related to this release as well as others anomaly simulators you make like to see.