This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Community Hub.
Threat Hunting is the use of tactics, techniques, and processes to detect cyber adversaries that have bypassed an organization’s layered security strategy and are now inside their network. Threat hunters must find, contain, and remove those adversaries before they can cause significant damage. To succeed in this mission, they need access to current, relevant, and actionable Threat Intelligence (TI) organized to reduce the mean time to remediation and their overall workload.
For this reason, Microsoft Defender Threat Intelligence (MDTI) is powerful in the hands of a threat hunter. In this blog, we’ll show how threat intelligence MDTI, collected, mapped, assembled, and identified connections across the internet, creates a continuous graph that security teams can use to understand threats quickly and act decisively.
Building an Advanced Investigation From a Single IP Address
MDTI’s ability to add immediate context to an indicator of compromise (IOC) can initiate a threat investigation when time is of the essence. Think of it as an instant encyclopedia for threat infrastructure.
Let’s say a threat hunter analyzes outbound connections from the organization’s network via a technique known as ‘Top Talkers,’ which enables them to identify machines using the most bandwidth. During that analysis, the hunter noticed a host within the network connecting to an IP address, 144.76.6[.]34, approximately four times an hour in a pattern that appears to be malware command and control (C2) beaconing behavior. While this behavior seems odd, a single IP address without any context will be of limited value to the threat hunter. To enhance and enrich the IP address, they can enter the IP address utilizing the MDTI home page.
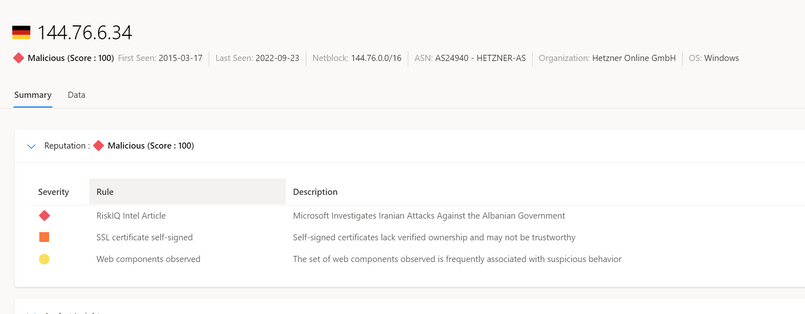
The results of this query allow the threat hunter to quickly decern the IP’s reputation. In this case, MDTI scores the reputation as 100 and rates it Malicious. With this knowledge, the threat hunter can now take immediate action to prevent communications to that IP address from anywhere on the organization’s network.
However, if the attacker is part of a threat group with advanced capabilities, only blocking one IP address will not be sufficient. Threat hunters know that by blocking C2 communication, the threat group will know they have been detected and could switch to an alternate C2 channel. To combat this evasion tactic, threat hunters must have a complete picture of the threat group’s infrastructure. MDTI enables this crucial drill-down into a threat group with continuously updated Threat Intelligence Articles.
Unmask and get to know your attacker
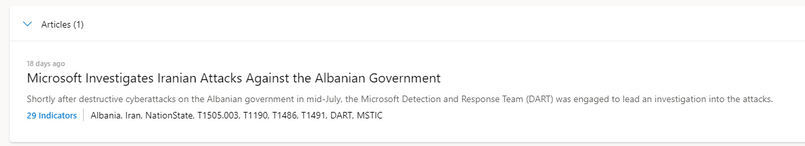
In addition to the malicious reputation score, the threat hunter using MDTI can see that there is a Microsoft Intelligence Article associated with this IP address inside the MDTI Portal.
When the threat hunter selects the article, they can read a comprehensive report on the threat group associated with that IP address, including the threat group’s known tactics, techniques, and procedures (TTPs) and additional reference materials for the analyst to consider. More importantly, the article provides the hunter with additional IOCs that can be used to search for activity on the organization’s network and harden their layered defense strategies.
Utilizing relevant and actionable threat intelligence like that found in MDTI, a threat hunter can quickly triage and action an alert, event, or incident with the organization’s network. In this case, Threat Intelligence would have significantly reduced the workload on the analyst and allowed that analyst to move on to another event or investigation, reducing time and increasing efficiency.
We’re excited to keep innovating and sharing our enhancements with you and encourage your feedback and conversations in the chat. Don’t hesitate to get in touch with us through the community.