This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Community Hub.
Attack Simulation Training is an intelligent phish risk reduction tool that measures behavior change and automates the deployment of an integrated security awareness training program across an organization. It allows security teams to run intelligent simulations and measure users for a baseline awareness of phishing risk, provide actionable insights and recommendations to remediate risk with hyper-targeted training designed to change behavior, and then measure behavioral progress against that benchmark through repeated simulation.
Today we are excited to announce that Attack Simulation Training now provides enhanced user telemetry in the simulation reports! This is an impactful update as we empower our customers to better understand the behavior of targeted users in their organization.
As an admin, have you ever wondered what your users that are being targeted by a phishing campaign are doing outside of traditionally captured telemetry of compromise and report rates?
As part of our enhanced user telemetry, administrators can now view additional details on how their targeted users are interacting with the phishing payload from phishing simulation campaigns. The enhanced telemetry is now included directly with your phishing simulation campaign reports, so no additional configuration is needed to enable this functionality. The information can also be exported as a CSV through the simulation reports.
In addition to our existing end user telemetry: Reported Email, Email Link Clicked, Credentials Supplied - we are now adding:
- Read message: if a targeted end user read the phishing simulation message
- Deleted message: if a targeted end user deleted the phishing simulation message
- Forwarded message: if a targeted end user forwarded the phishing simulation message
- Replied to message: if a targeted end user replied to the phishing simulation message
- Out of office: if a targeted end user has set up automatic out of office responses when the phishing simulation campaign was delivered
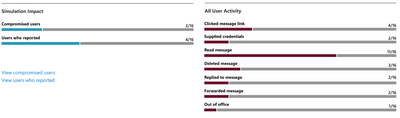
This information is provided in the phishing reporting page under "All User Activity" and will be available as columns in the exportable Users Report.
|

Screenshot: Simulation report “All User Activity Section ” |
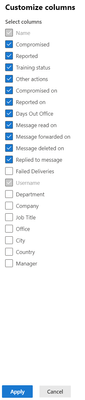
Screenshot: All User report available columns |
These additional data points can help organizations gauge areas of opportunities and target training for their end users. With detailed telemetry, administrators can get richer insights on the targeted users' behaviors outside of compromise and reporting the phishing simulation.
Let’s see what additional insights you can gain with these new data points!
Example Analysis
In this example, we have 16 users within a single simulation.
Of these 16 users, we see the following breakdown:
- 4 users who clicked on the message
- 2 users who had supplied their credentials
- 11 users who read the message
- 3 users who deleted the message
- 2 users who replied to the message
- 2 users who forwarded the message
- 1 user who was out of office
- 4 users who have not yet interacted with the payload and are not out of office
In conjunction with the data from Simulation Impact section, we also see that there were:
- 4 users who reported message as phishing
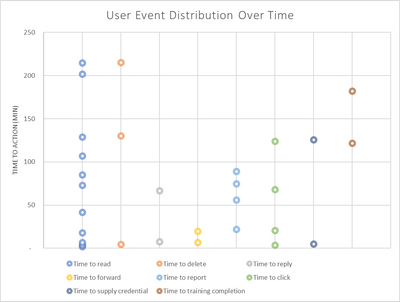
We can use the data from the detailed user report to construct each individual user’s timeline of actions and to create a report to see what the time distribution looks like across each event action.
In this visualization, we can see different types of behavior amongst the individual users. In this example, users who reported the phishing simulation tend to do it very quickly after reading the message. We also see that there are users who run through various interactions such as clicked, forwarded, and reported all in quick succession after receiving the message. From this sample, most of the users did read the phishing simulation message and there were two users that deleted the message but did not report. There was also one user who read the message and did not engage with it further. This provides some additional insights about users who were neither phished nor reported phishing and opens the opportunities to provide encouragement and reminders on the importance of reporting phishing messages.
This is another visualization with the same data set. In this view, we can see that most of the messages were read within 150 minutes of message delivery and most of the messages were reported between 50 to 100 minutes after message delivery. With this visualization, we can gain insights on the distribution of user actions within the organization when a real phishing attack occurs. Given that there may not be any reported phishing message until 100 minutes after an initial attack, there is an opportunity to provide end users training and encouragement to report messages even quicker given that there are several individuals who had read the message in the first 30 minutes of receiving it but had not report or clicked the message.
We hope these visualizations provide new inspiration into what you can do with this new set of data and how it can inform your security culture and investments.
Want to learn more about Attack Simulation Training?
Get started with the available documentation today and you can read more details about new features in Attack Simulation Training.