This post has been republished via RSS; it originally appeared at: Azure Database Support Blog articles.
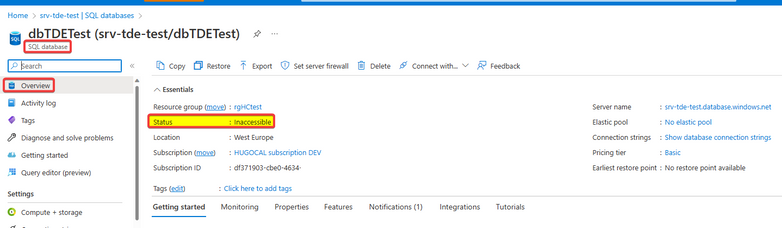
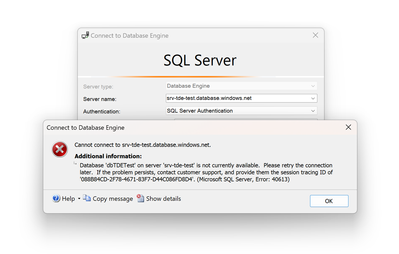
If we have a Customer-managed TDE (Transparent Data Encryption) and we delete by mistake the entire "Azure Key Vault" or just the "Key" object, the database will be inaccessible:
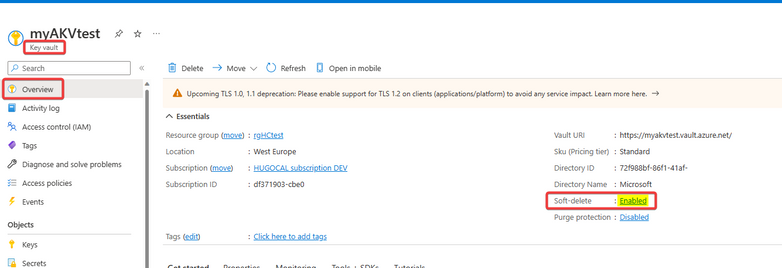
Don't worry, this problem is solvable. Every "Azure Key Vault" or its "keys"/"secrets"/"certificates" objects have the "soft-delete" feature enabled, so if you delete any of these elements, Azure keeps a backup copy of them for 90 days:
Azure Key Vault soft-delete | Microsoft Learn
We need to recover the "Azure Key Vault" (AKV) or the Key object. We can follow these steps in the Azure Portal:
Case 1 - [ Deleted key object]
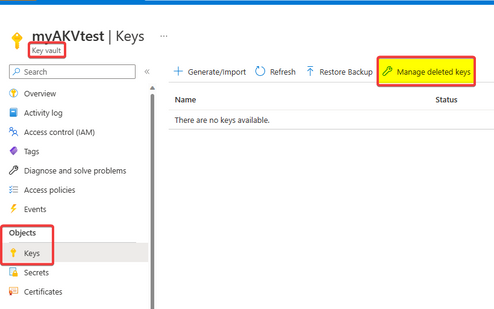
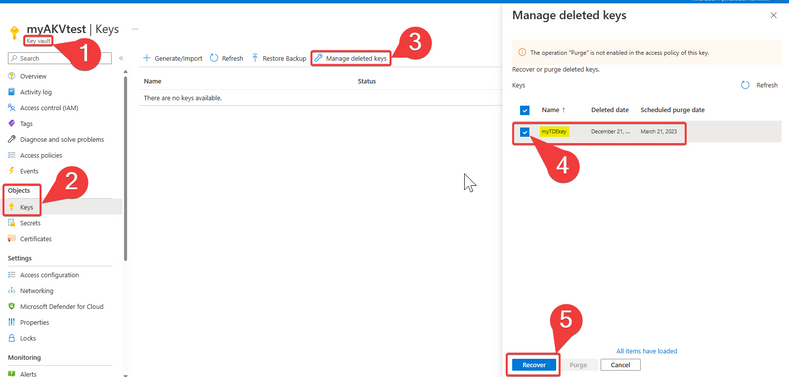
Go to the Azure Key Vault and select "Keys" objects and then click on "Manage deleted Keys":
Select the "key" object that you want to recover and then click on "Recover":
The recovery takes a few seconds:
Once access to the key is restored, taking the database back online requires extra time and steps, which may vary based on the time elapsed without access to the key and the size of the data in the database. If key access is restored within 30 minutes, the database will autoheal within the next hour. If key access is restored after more than 30 minutes, autoheal isn't possible, and bringing back the database requires extra steps on the portal and can take a significant amount of time depending on the size of the database. Once the database is back online, previously configured server-level settings such as failover group configuration, point-in-time-restore history, and tags will be lost.
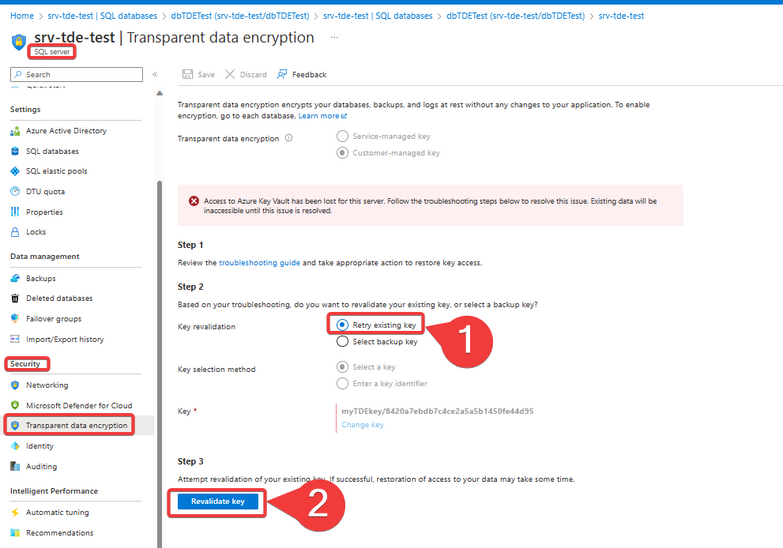
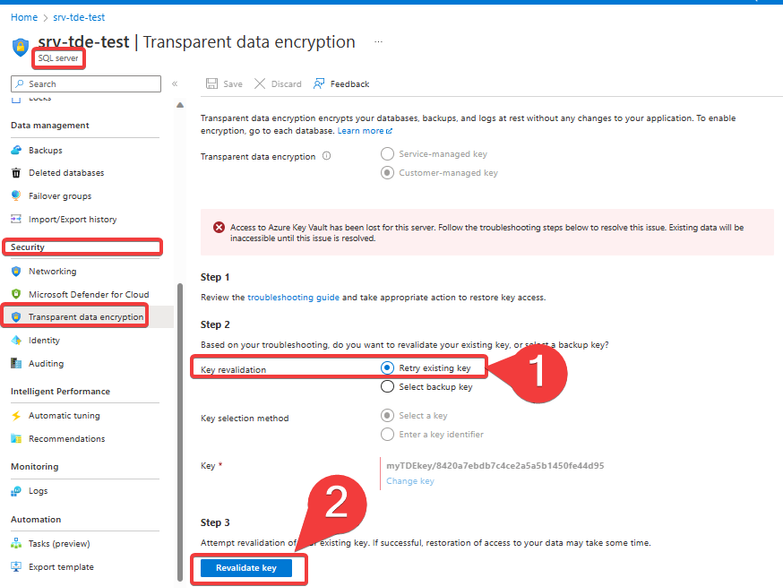
If we restored the "Key" object after 30 minutes, we need to go to the "Transparent Data Encryption" blade from the Azure SQL Server, select the option "Retry existing key" and then click on "Revalidate key":
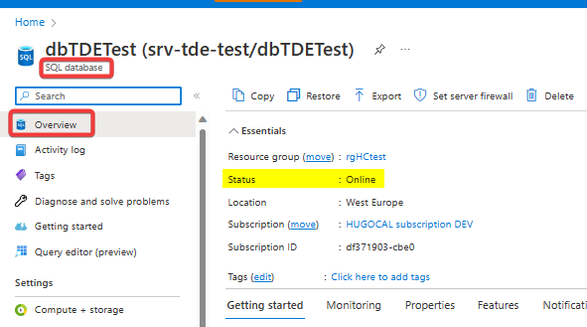
And now the database is online again:
You can also restore the "key" object through PowerShell and CLI:
[PowerShell]
List all deleted keys in a key vault
[CLI]
List all deleted keys in a key vault
Case 2 - [ Deleted Azure Key Vault ]
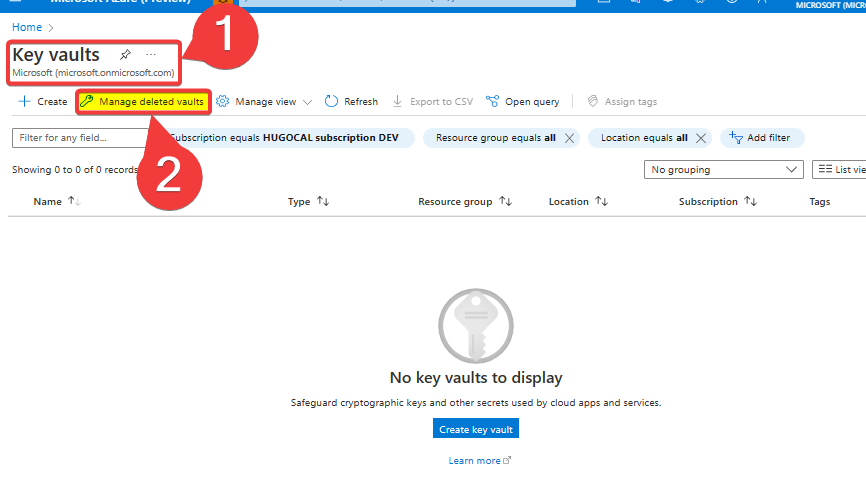
If you have deleted the whole "Azure Key Vault" you can restore it, to do this you have to go to the main blade of the "Azure Key Vault" resources and click on "Manage deleted vaults":
Select the subscription, then the "Azure Key Vault" you want to restore, and click on the button "Recover":
The recovery process takes a few seconds:
If we restored the "Key" object after 30 minutes, we need to go to the "Transparent Data Encryption" blade from the Azure SQL Server, select the option "Retry existing key" and then click on "Revalidate key":
And the TDE is working again:
You can also restore the "Azure Key Vault" resource through PowerShell and CLI:
[PowerShell]
List all soft-deleted key vaults
Recover soft-deleted key-vault
[CLI]
List all soft-deleted key vaults
Recover soft-deleted key-vault
If we deleted the key object or the Azure Key vault more than 30 minutes ago, the only way to revalidate the TDE is through the Azure Portal or Rest API.
I hope this step-by-step guide will be helpful.