This post has been republished via RSS; it originally appeared at: Microsoft Tech Community - Latest Blogs - .
Overview
Microsoft Sentinel’s REST – API based data connectors a lot of times use secrets and keys that customers would prefer to keep secured in a vault from where they can effectively manage (retrieve, update, delete, manage access, etc.) these secrets and keys. In this article, we’ll talk about securing API secrets and keys using an Azure Key Vault.
Content Hub solution when deployed may not necessarily deploy the Azure Key Vault resources as a part of the solution deployment to account for varied usage of Azure Key Vaults. However, Azure Function apps can use keys stored in AKV using AKV references without any changes in the Azure Function App code.
Integrating with AKV is a three – step process:
- Ensure the Function App & Key Vault have the right permissions
- Create the secrets in the Key Vault
- Add Key Vault References in the Function App
Let’s talk about each of these in more detail.
Ensure the Function App & Key Vault have the right permissions
You could choose to create a new or use an existing Key Vault to store and manage your API keys and/secrets. To create a new Azure Key Vault, follow the steps documented on the official documentation.
Manage Permissions
Once created, you need to ensure that sufficient permissions have been assigned for the Function App to read the secrets from the Key Vault. Your Function App must have managed identity enabled. This could either be system-generated or user-generated. For the purpose of this article, we’ll continue to use a system generated managed identity.
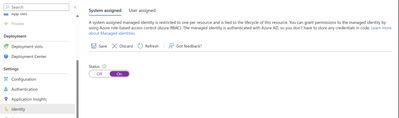
To enable system assigned managed – identity on the Function App,
- Navigate to the Function App in the Azure Portal and click on Identity.
- Still under the System assigned tab, switch the Status to On if its currently set to Off. Click Save.
3. On saving, it should auto generate an Object with an Object ID. Copy the Object ID to keep it handy, you’ll need it in some time.
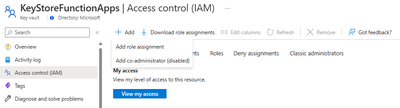
To provide access to the Function App’s managed – identity to read secrets from the Azure Key Vault,
- Navigate to the Key Vault on the Azure Portal.
- Click on Access Control (IAM).
- Next, click on Add and then on Add role assignment.
4. Select the Key Vault Secrets User role from the list of roles and then click Next.
5. On the Members tab, for Assign access to, select Managed identity and then click on ‘+ Select members’.
On the configuration pane that opens on the right, make the following selections:
- Subscription – The subscription in which your Function App resides.
- Managed identity – Function App
- Select – From the dropdown, select the name of the Function App.
When the selections are complete, click on Select.
6. The Members should now have the name of the Azure Function app along with the Object ID of the Managed identity populated.
7. Optionally, add a Description.
8. Click on Review + assign.
Create the Secrets in the Key Vault
You can manually create Secrets in the Key Vault.
- On the Azure Portal, navigate to Azure Key vault and select the Key vault that was created earlier.
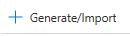
- On the left-hand pane, click on Secrets.
- Next, click on + Generate/Import.
- Make the following selections on the Create a secret page:
- Upload options: Manual
- Name: <Name/Identifier of the Secret>
- Secret value: <Value of the Secret>. (This will be the actual string that the Function App will need to connect to the API)
- Enabled: Yes
The other value can be left default.
5. Click Create.
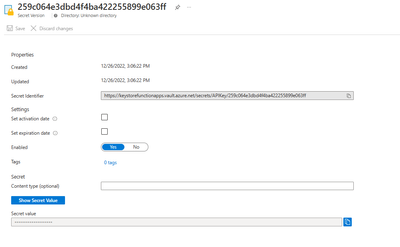
6. Now, to extract the SecretUri,
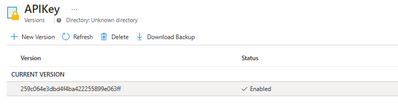
a. Select the Secret that was created in the previous step
b. Click on the Current Version
c. Copy the Secret Identifier.
Add Key Vault References in the Function App
Azure Function Apps will now need to be re-configured to extract the secrets from the Key Vault instead of using the plain – text strings. To do that,
- On the Azure Portal, navigate to Function Apps and select your Function App.
- On the left-hand pane, click on Configuration.
- Click on Advanced Edit and you’ll notice a configuration pane open on the right with all the configuration parameters in json format.
- Look for the name of the configuration setting you wish to edit and for the setting, edit the value as:
@microsoft.KeyVault(SecretUri=https://<key-vault-name>.vault.azure.net/secrets/<secret-name>/<secret-version>)
Note: The value of the SecretUri was the secret identifier copied from the Secret created in the previous section.
5. Click Ok.
6. Back on the Function App settings, click Save and then Continue. This will apply the changes to the Function App.
7. Now, back on the Function App settings, click on Refresh and click Continue.
You will now also notice that the Source in the Configuration Setting that was just modified changes to Key vault Reference from App Service.
The Function App is now configured to extract the Secret values from Key Vaults instead of reading plain-text values from the Configuration Settings.