This post has been republished via RSS; it originally appeared at: Microsoft Tech Community - Latest Blogs - .
Protect against ransomware and other threats as you build new cloud-based services and migrate or modernize existing apps and services. Get guidance for where to start, with a free new assessment with security recommendations and a prioritized list tailored for your organization, apps, and services.
Azure expert, Matt McSpirit, joins Jeremy Chapman to share how to architect your apps and services for Zero Trust security.
Start a free assessment.
Get actionable guidance to implement policies and rules. Stop attacks in their tracks with a Cloud Adoption Security Review assessment.
Stop an attacker at the front door.
Know your risks. Have a plan. Apply security recommendations. Architect your apps for Zero Trust security.
Strong security foundation for cloud apps.
Manage identity infrastructure and conditional access policies using Microsoft Entra and Azure AD. Click to watch a rundown.
Watch our video here.
QUICK LINKS:
00:00 — Introduction
02:32 — Where to start with security architecture
04:36 — Apply prioritized list to a new app
05:38 — Policies and configurations
07:03 — Improving security strategy
09:59 — Implementing strong authentication
12:21 — Wrap up
Link References:
Take the free assessment at https://aka.ms/microsoftassessments
Check out our show on Zero Trust at https://aka.ms/zerotrustmechanics
How to automate and deploy landing zones at https://aka.ms/LandingZoneMechanics
Manage identity infrastructure in the Microsoft Entra admin center at https://entra.microsoft.com
More on Microsoft Cloud Adoption Framework security at https://aka.ms/CAFsecure
How to implement Azure landing zones at https://aka.ms/ALZ
Unfamiliar with Microsoft Mechanics?
As Microsoft’s official video series for IT, you can watch and share valuable content and demos of current and upcoming tech from the people who build it at Microsoft.
- Subscribe to our YouTube: https://www.youtube.com/c/MicrosoftMechanicsSeries
- Talk with other IT Pros, join us on the Microsoft Tech Community: https://techcommunity.microsoft.com/t5/microsoft-mechanics-blog/bg-p/MicrosoftMechanicsBlog
- Watch or listen from anywhere, subscribe to our podcast: https://microsoftmechanics.libsyn.com/website
Keep getting this insider knowledge, join us on social:
- Follow us on Twitter: https://twitter.com/MSFTMechanics
- Share knowledge on LinkedIn: https://www.linkedin.com/company/microsoft-mechanics/
- Enjoy us on Instagram: https://www.instagram.com/msftmechanics/
- Loosen up with us on TikTok: https://www.tiktok.com/@msftmechanics
Video Transcript:
Jeremy Chapman (00:02):
Up next, we’ll go deep on how you can architect your apps and services for Zero Trust security to protect against ransomware and other threats as you build new cloud-based services and also migrate or modernize what you have, including a free new assessment to help you know where to start with security recommendations and priorities tailored for your organization, apps, and services. And to walk us through architecting for security, I’m joined once again by Azure expert, Matt McSpirit, welcome back to the show.
Matt McSpirit (00:29):
Great. Thanks for having me.
Jeremy Chapman (00:30):
Now, security is one of those topics that never goes out of fashion. And as we deploy in today’s age of cloud and more sophisticated cyber attacks, you really need to think about the attack vectors and measures that you put in place to prevent, detect, and also respond to attacks.
Matt McSpirit (00:44):
Yeah, exactly right. And this is about making sure that security is a top priority in consideration as you’re setting up your workloads to run in the cloud. And at the core, this boils down to a Zero Trust approach in ensuring that not only your protection is comprehensive and proactive, but it also expands on the idea of assume breach, so that even if something does make it through your defenses, you’re able to discover and evict bad actors as well as recover from any damage once it’s done. Now, security can’t be an afterthought if you don’t build security into your apps from the beginning. It’s much more expensive and difficult to clean up or add what you need later.
Jeremy Chapman (01:19):
Right. And by the way, zero trust is the topic we’ve covered extensively on mechanics, which you can check out at aka.ms/zero trusts mechanics to break it down, it’s all about verifying the identity of any person or entity as well as any endpoint device, application or service network connection infrastructure component along with applying protections to the data itself. And on the surface, this does sound pretty comprehensive, but what are some of the other considerations that we might have in terms of architecting, building, or migrating a workload to the cloud?
Matt McSpirit (01:48):
Well, across all of those areas, you have to factor in the right processes and operations. And when you’re building cloud hosted apps, these are shared responsibilities between your organization and your cloud provider. And it’s even more important than you work together within your organization as a team so that your developers, security team identity and network admins are all in sync. So for example, you’ll need to put in place processes for change management as you iteratively build and deploy new apps. And if your workload is compromised, your architecture design needs to be able to contain the threat so that it doesn’t take down other workloads sharing the same network and services. And it’s important to factor in the right attack response capabilities for your SecOps teams to respond through, for example, integration with their XDR system.
Jeremy Chapman (02:31):
Got it. That said, though, you’re often only as secure as your weakest link. So if I wanted to build out a new app and needed to know where to start for security, where would I even begin?
Matt McSpirit (02:41):
Well, every organization’s different, and based on your industry, location, or other factors, your security priorities will also vary. So to help you identify opportunities to improve your security architectures and the services around them, we’ve created a free assessment that you can find at aka.ms/microsoft assessments. And like other assessments here, you can log in and track your progress over time. So when I select this security assessment, you can see it enters a default name and I’ll go ahead and keep that. And on the left you can see all of the categories and questions. And to save time here, I’ve already inputted my answers to most of these. And on the final question, I’ll mark my answer and hit view guidance, and you can see my overall results and score along with a breakdown of scores by category. Here you can see our biggest opportunity is to improve the categories for security strategy, access control, and infrastructure security.
(03:32):
When I scroll down, I see quick links to recommended resources like the Azure Fundamentals, security guidance in the Cloud Adoption Framework and the CISO workshop. And under improve my results, if I drill into this one for infrastructure security that I want to improve, it provides dozens of recommended actions tailored to me and each links directly to the best resources to improve. In my case, I know I want to improve access controls and infrastructure security as priorities. At a high level, you can see recommendations for improving things like network segmentation, ensuring I’ve got the right Azure policy controls in place, as well as several detailed networking recommendations. This one goes to the web app firewall recommendations, and you’ll see it explains what it is and how it works, along with the types of attacks it protects against. And it provides actionable guidance to implement policies and rules for stopping common attacks. And that’s just one example. Importantly, I have a few prioritized areas to start with. So now I can start making improvements on our security foundation and set ourselves up for success as we build, evaluate, and deploy new apps.
Jeremy Chapman (04:36):
Okay, so now you’ve got this great prioritized list of what to do, but can we make this real by applying that to a new app that you’re building or architecting?
Matt McSpirit (04:44):
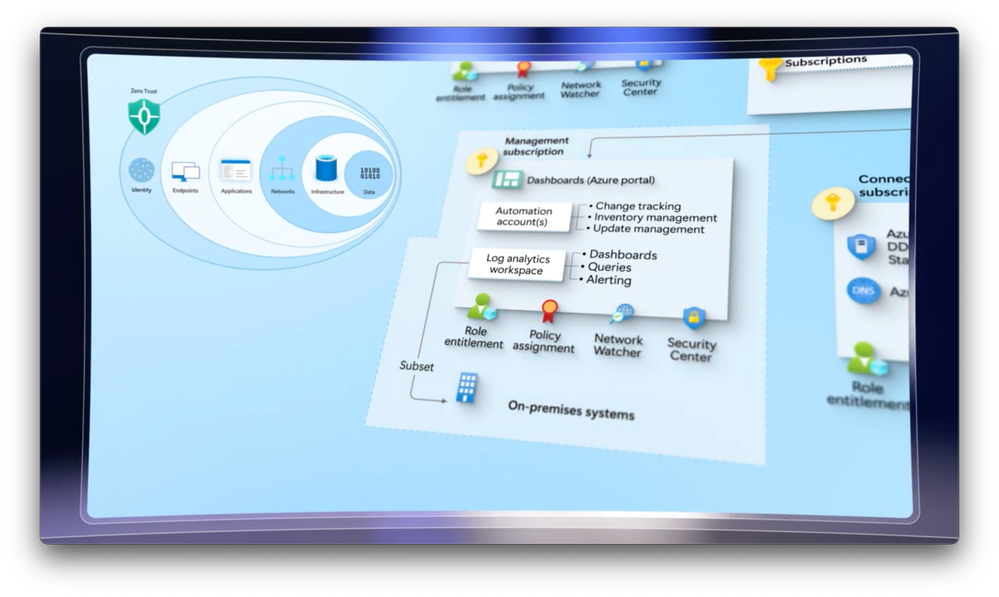
Yeah. Let’s apply the areas we’ve prioritized based on our assessment to a new app. So for the sake of an example, imagine we’re building a human resources wellness application where there’s a lot of highly sensitive information at the center. It’s going to need highly differentiated access controls depending on who’s accessing it, for example, between your HR team, your employees, and their family members, that should get differentiated views. We need to think about integrating innovation security to support the SecOps process throughout the application life cycle. Now, if you watched our last show, you might remember that any app needs to start with a landing zone. And this is really one of the first steps towards having infrastructure security and access controls in place, and it ensures the right level of separation with its own subscription and dedicated Azure policies.
Jeremy Chapman (05:28):
Right. And by the way, if you missed it, our last show on this concept covered how to automate and deploy landing zones. So check that out at aka.ms/LandingZoneMechanics. So what are some of the policies and configurations we might make in our case for our app that’s sitting in its own landing zone?
Matt McSpirit (05:44):
So the nice thing about this is that the structure and top level management groups put the right guardrail policies in place for all apps in the organization, including ours in the corp management group. And as part of this architecture, it will have access to managed shared services, many of which align to the areas highlighted in Zero Trust, like identity and access management for authentication, endpoints, cloud apps, and infrastructure that are governed through the management subscription, network controls are part of the connectivity subscription, and the data for our HR system in this case will reside within the landing zone for our app. And all of this means we don’t have to reinvent the wheel, and it also means that we’re working across our identity, networking, security, and dev teams each time we build out a new app. And because we’re using their services, this drives us to collaborate together on design, policy, controls and operations. And this logical separation of resources and services, will often lead to more business resilience. So even if your new app is compromised, it won’t necessarily impact other apps and services ensuring other areas of the business continue to function.
Jeremy Chapman (06:45):
And this is really one of those cases, you know, where the upfront work in getting the management group and subscription structure in place is going to save you time in the long run. So now you have a set of base services in place, what’s the next step?
Matt McSpirit (06:56):
Now, before you start any project, whether it’s an HR solution integrated with sensitive information or something like a marketing site without sensitive information, remember from our assessment security strategy was another area to improve for us. So let’s address that. So first, as a workload owner, you’ll want to pull in your security architects and engineers to understand the risks for any app or service you plan to build or deploy. And here you’ll need to think like an attacker — which aspects of the service are valuable, and what are the potential targets that could be exploited? What’s the potential damage an attacker can cause, whether it’s destruction of assets via ransomware, impacts on revenue, by stealing money, data, or preventing your company from doing business, as well as what the risks are for your reputation. These motivations will help you inform decision makers and how you implement and integrate security across your solutions. And it means getting your security operations involved early so they’re ready to rapidly respond to security incidents.
Jeremy Chapman (07:51):
Okay, so once we know our risks and we have a plan in place to be able to respond to any attacks, then what’s the next step?
Matt McSpirit (07:56):
Well, now it’s time to apply the infrastructure security recommendations. So prevention beats remediation. It’s a lot easier to stop an attacker at the front door than it is to find them, evict them, and clean up afterwards. The assessment pointed me to the web app firewall, and among other attack vectors, this protects against common web hacking techniques like SQL injection and cross site scripting. So let me give you a few more details. So I’m in the Azure portal on the app firewall policies page, and I’ll open this one called contosowafpolicy. Now here in managed rules, you’ll see I’ve got 127 rules preconfigured, and these are all defaults in the service and based on the Open Web App Security Project, or OWASP, the top 10 risk categories to prevent common attacks.
Jeremy Chapman (08:39):
And by the way, if you’re not familiar with OWASP, it’s a non-profit organization of security experts really around the world that’s dedicated to improving web application security.
Matt McSpirit (08:48):
That’s right. Now, the OWASP contributors know that it’s a mess out there and it’s not easy to keep up with the trending risks and vulnerabilities. Now, as I scroll down this list of rules, pay attention to the description column to see the types of attacks. The main thing here is to point out again, that everything here is preconfigured. So you don’t need to research trending threats and translate them manually into policies. It’s all done for you by the Azure WAF service. Now, additionally, in custom rules, you can optionally add your own rules with conditions based on geolocation, IP address or range, size, and strings. But even if you just stick with defaults based on OWASP top 10, your app will be much more secure. Then all you need to do is configure the application gateway associated in our case with our HR app to our app firewall policy. And all enable protections will be in place for our HR app. And while I showed everything from the Azure portal, everything I just did can be implemented using Azure infrastructure as code. As you can see here with this Bicep example. It makes it easily repeatable in dev, test, and production as well as when you build new apps in the future.
Jeremy Chapman (09:52):
And this is really one of those great examples where you can invest a little bit of time, but the protection from it is going to really pay off. So what do we do next?
Matt McSpirit (09:59):
Well implement strong authentication. Now, we needed to address access control based on our assessment and basic password only auth isn’t enough, but unfortunately it’s still incredibly common. So your app should factor in the access control plane and management plane. And these are baked into our landing zone architecture, secure user access pathways using multifactor authentication required to reach your apps, secure application access pathways with anything connecting using APIs to your apps, as well as privileged access controls to protect IT and service admin accounts.
Jeremy Chapman (10:31):
Yeah, and this is where Microsoft Entra and Azure Active Directory come in.
Matt McSpirit (10:34):
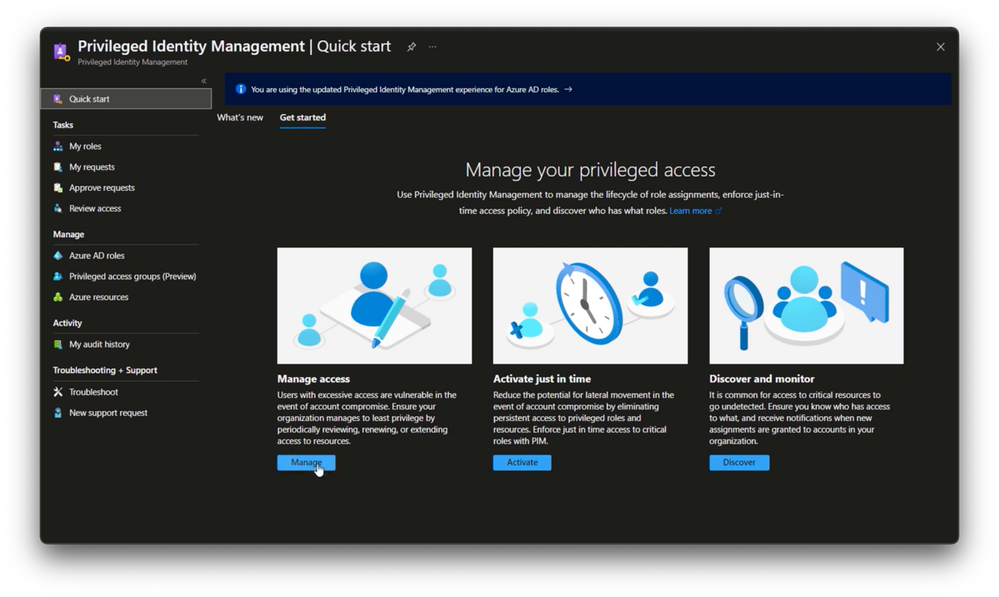
That’s right. And if you haven’t checked out the Microsoft Entra admin center for managing identity infrastructure, it’s the central place where you’ll configure everything. And you can get to it by going to entra.microsoft.com. So here, for example, in privileged identity management, I can manage the lifecycle of role assignments, enforce just-in-time access policy, and discover who has what roles. For example, if I drill into managed access and then into alerts, I can use this information to assess the risk roles without MFA set up, having too many global admins, or potential stale accounts with privileged access. These are prime targets for attackers to operate under the radar. Now, for example here, if I drill into my stale accounts, I see eight accounts that haven’t been used in a while. I can select the stale accounts and fix that up right from here.
(11:20):
And this also works for conditional access policies where the system determines risk automatically at the time of sign in and can take action. So here you can see we have conditional access policies set up for our HR app. If I look at the conditions, you’ll see we’ve configured user and sign in risk. Trusted locations are enabled where we can make the determination at log on if the user is in an expected location. Now, for client apps, we’re only allowing modern authentication clients. And in grant, you’ll see that if any of the above conditions are flagged, it’ll require another MFA pass for access. Then because our HR app allows family members to access it without an Azure AD account, you can configure what’s required for secure access in external identities. So here we’ve enabled B2C access either using email based one time passcodes and consumer Microsoft accounts like Outlook.com, and I can also configure Google or Facebook identity providers for secure access as well.
Jeremy Chapman (12:14):
And these considerations and really how you incorporate everything into your apps will ensure that you’ve set a strong security foundation. So now you’re ready to architect and build your app with Zero Trust security considerations in mind. So for anyone who’s watching right now, what do you recommend they do to get started?
Matt McSpirit (12:30):
Well, firstly, everything I showed you today is available now, and while I only highlighted a few recommendations and controls, the tools and guidance for this will go a lot deeper, and you can get started today. Now, key points to remember, integrate security as early as possible when you’re architecting your app. Put controls in to protect infrastructure and the app itself, and importantly, implement the right controls and policies around your app. Now all of the security guidance is part of the cloud adoption framework. You can find everything you need to learn more at aka.ms/CAFsecure. You can learn more about the Azure landing zones and how to implement them at aka.ms/ALZ. And of course, take the free assessment now available for security at aka.ms/microsoftassessments.
Jeremy Chapman (13:13):
Thanks so much, Matt, for joining us today and also sharing how you can bake security into every aspect as you architect your new apps. Of course, keep checking back to Microsoft Mechanics for all the latest updates. Subscribe to our channel if you haven’t already. And as always, thank you for watching.