This post has been republished via RSS; it originally appeared at: Core Infrastructure and Security Blog articles.
As companies adopt Microsoft Defender, there are certain questions coming from customers in terms of EPP management. These questions are mostly focusing on Microsoft Defender management in Windows Servers. I’d like to touch base on different management options for different customer scenarios.
I have on-premises environment, and I cannot move to cloud
We can use legacy management options such as Active Directory GPOs and Microsoft Endpoint Configuration Manager (aka. System Center Configuration Manager - SCCM) for sure. However, these tools might not be the best possible solutions that would be agile enough - since these two options wait for a certain amount of time before taking requested actions and it would be hard to RBAC on these tools to satisfy Segregation of Duties requirements.

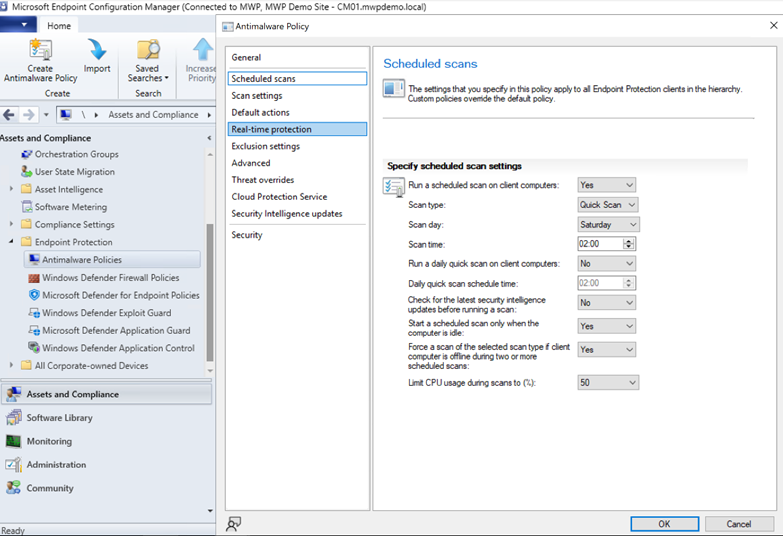
I have on-premises environment and I can extend to cloud
For modern client operating systems such as Windows 10 / Windows 11, we have an option to use Microsoft Intune either on a cloud only configuration or on a co-management setup. Cloud only configuration has nothing fancy, you basically create a policy on the cloud and target that policy to the cloud managed devices. However, co-management configuration is where Intune is integrated with Microsoft Endpoint Configuration Manager. With this integration we can set the endpoint security workload management authority to Intune as shown below:

This change would allow Intune to push endpoint security policies and trigger activities such as AV scanning etc. just like a cloud only scenario while keeping other workloads in Configuration Manager authority allowing security teams to create policies and push them over Intune while infrastructure teams keep doing their job without any interference.
How about managing AV on servers?
For AV management of Servers, we can use Configuration Manager with two different configuration options. For the customers that are working on-premises only, Configuration Manager can be used together with Group policy objects just like they can be used for client management.
For the customers that are using or planning to use cloud services; another integration between Configuration Manager and Intune is available to simplify management, which can be used to manage Microsoft Defender as well. That configuration is called “Tenant Attach”. Tenant Attach helps to “view” the resources that are managed by Configuration Manager via Intune.
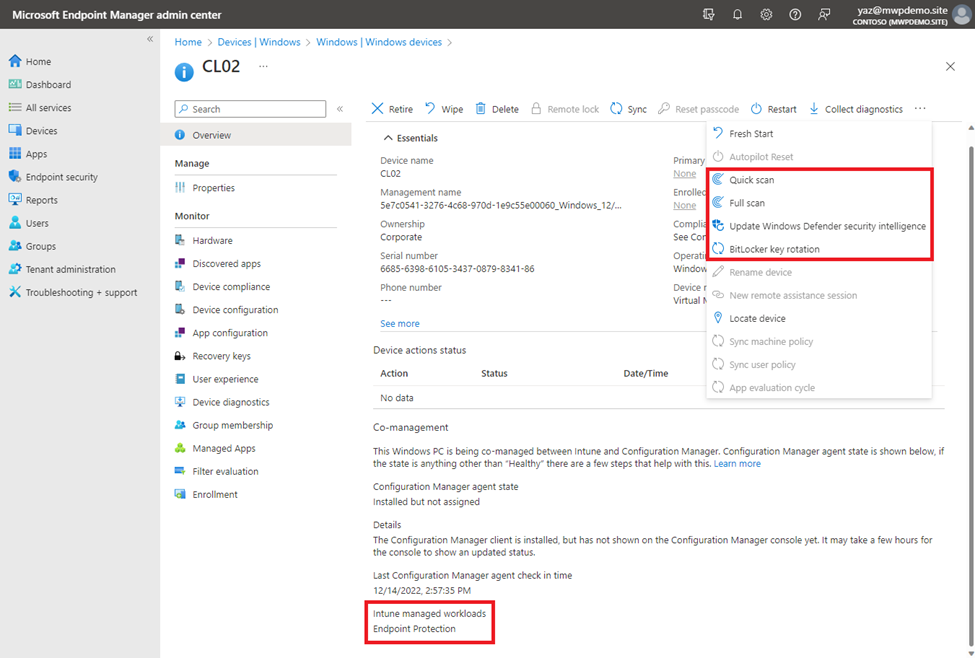
After configuring tenant-attach, we will start seeing devices that are uploaded to Microsoft Endpoint Manager Admin Center as “Managed by: ConfigMgr”

When creating an AV policy via Intune, there is now an option for devices being managed by Configuration Manager.
To be able to do that, we will need to have collections that we would target AV policies synced to Intune. Let’s look at how it is done.
First, we need to decide which collection memberships will be sync to Intune. Since I will be using this feature for on-prem managed servers only, I am doing a search on my server collections. This is possible for on-prem managed clients as well.
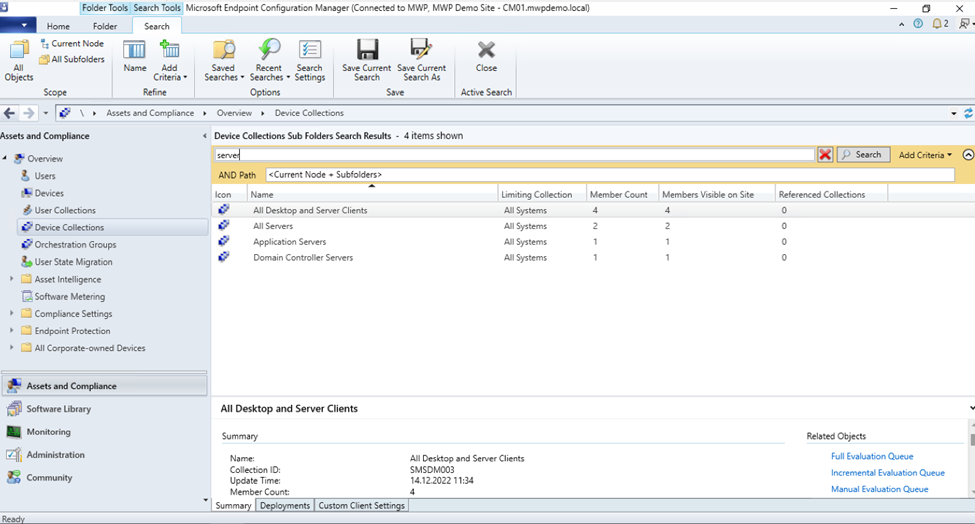
I see that I have 4 collections that have the word “server” in it. But I want to sync only 3 of them: All Servers, Application Server and Domain Controller Servers.
Use case example: I want to deploy a policy to all servers, and different exclusions for application servers and domain controllers.
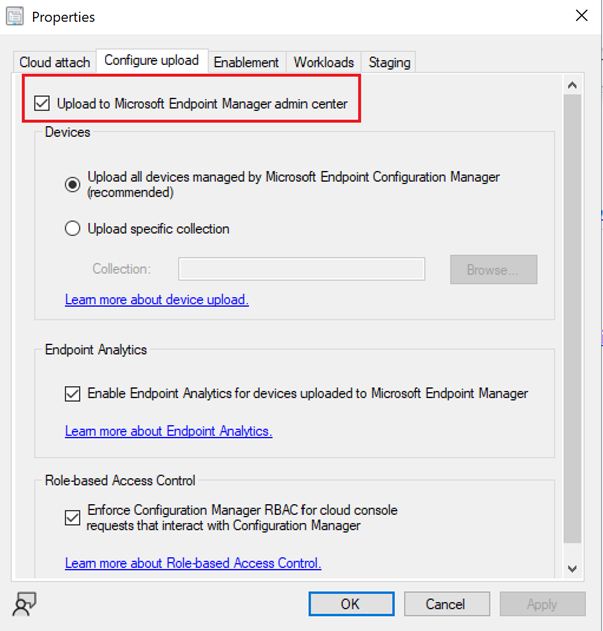
Let’s click on properties of every collection we want to Sync to Intune service, and check “Make this collection available to assign Endpoint security policies from Microsoft Endpoint Manager admin center” checkbox that is available in Cloud Sync tab.

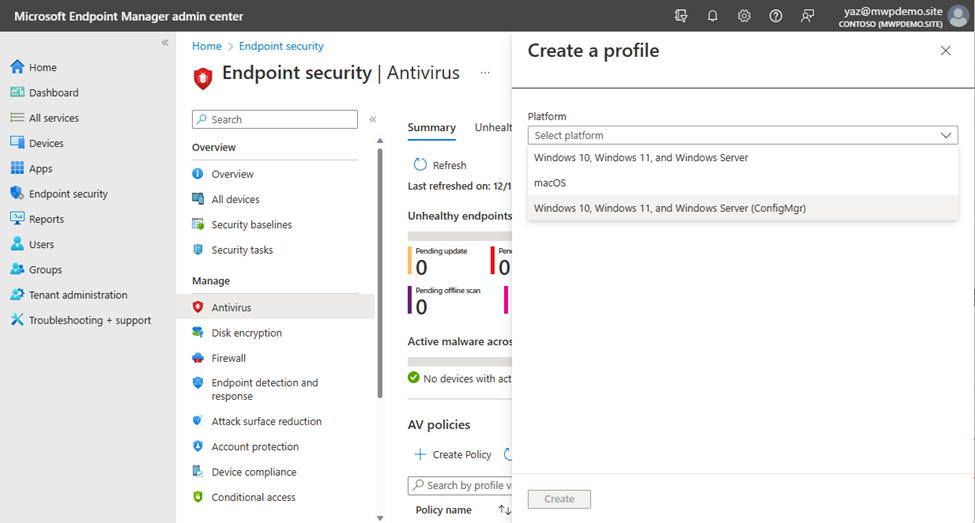
Then, let’s create an AV policy to target those devices:
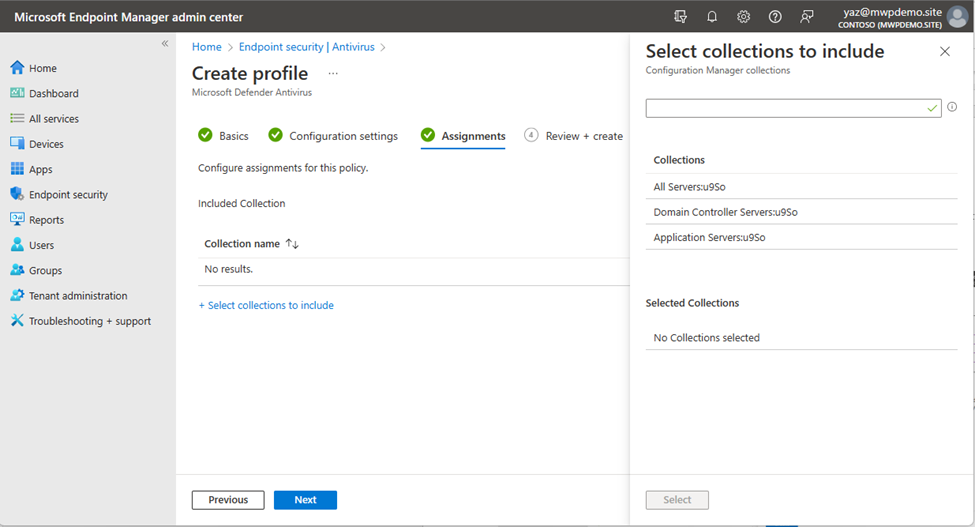
I will not go deep on details of AV configuration, however when we move forward to assignment page in Intune, we are able to see the collections that are available to assign Endpoint security policies from Microsoft Endpoint Manager admin center. We can deploy the AV policy to these collections.
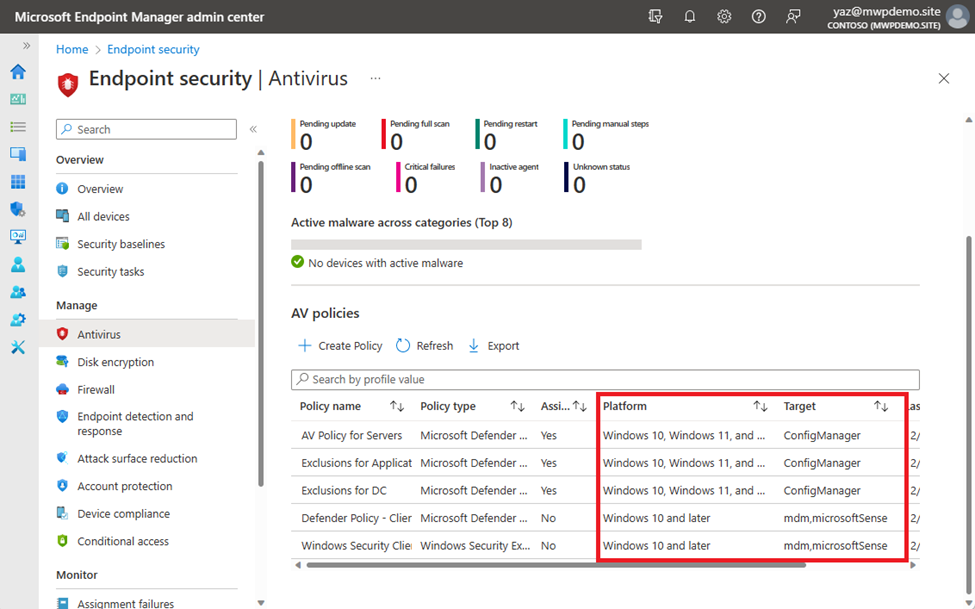
After creating the policy and exclusions as necessary, we will be able to see the policies on intune console, with the platform information and target. Note that target of these policies are listed as “ConfigManager” while other policies are targeted to “mdm,microsoftSense”.
Those targeted policies can be seen under the “deployments” tab of respective collections.
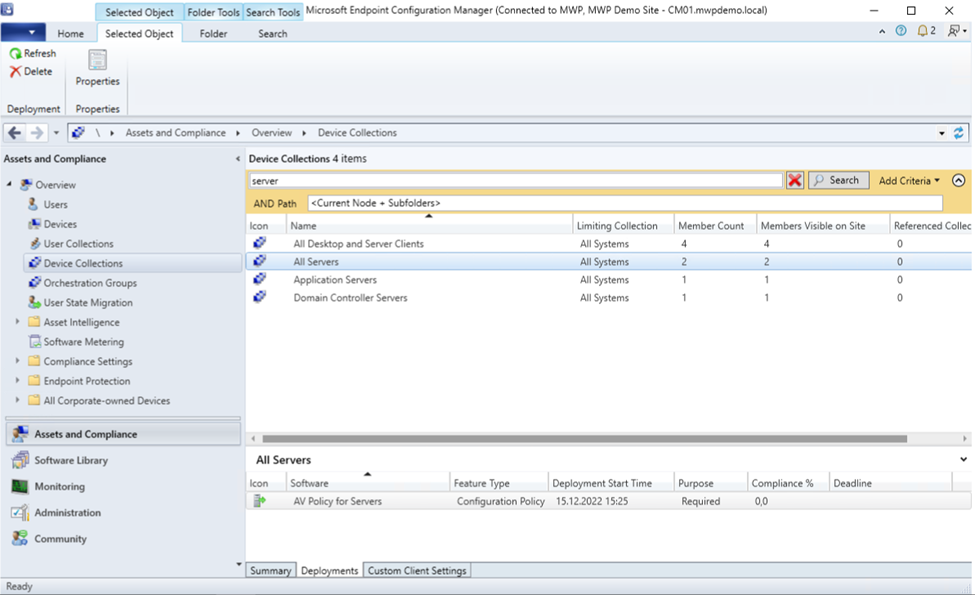
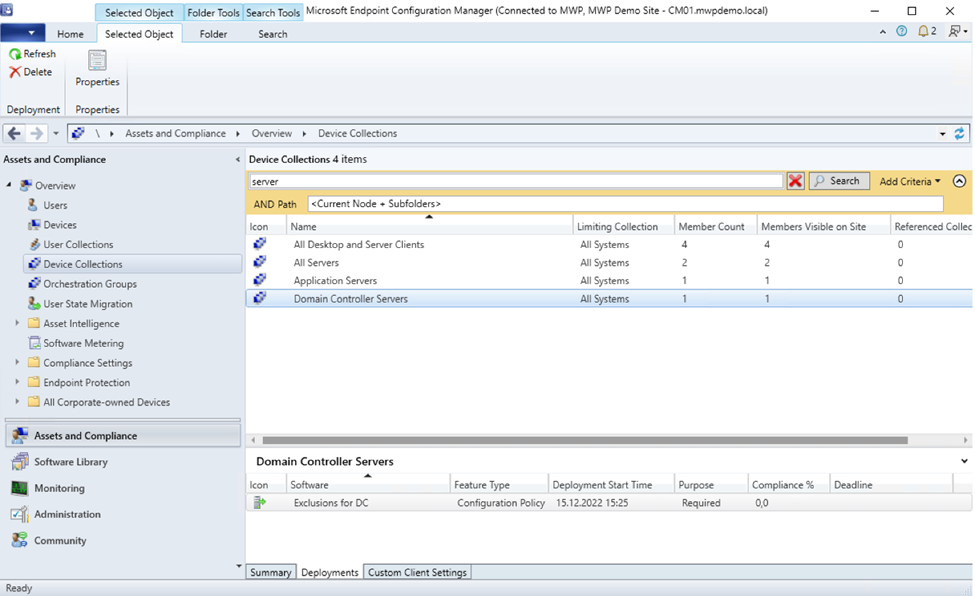
Note that the policies that are affecting an endpoint can be seen on the properties of the endpoint as well. You may see the policy deployment details on Configuration Manager collections and all the policies targeted to the endpoint in the snippet.

Wrap Up
It is possible to use Intune as a single management plane for managing Microsoft Defender Antivirus even in Windows Servers. Managing AV in the servers may require additional integration and configuration between Intune and Configuration Manager, but the results worth the effort.
