This post has been republished via RSS; it originally appeared at: Microsoft Tech Community - Latest Blogs - .
Microsoft Defender for DevOps shows the security posture of pre-production application code and resource configurations. Security teams can use the service to enable security checks for their templates and container images designed to minimize the chance that cloud misconfigurations reach production environments. Leveraging [insights] within Microsoft Defender for Cloud, security admins can help developers prioritize critical code fixes with actionable remediation and assign developer ownership by triggering custom workflows.
Defender for DevOps uses a central console to empower security teams with the ability to protect applications and resources from code to cloud across multi-pipeline environments, such as GitHub, Azure DevOps and more to come.
With an intent to help Security admins and developers, Azure DevOps provides two ways of configuration today. In this article we want to walk you through the configuration of Azure DevOps pipelines via the classic UI and YAML.
Option 1: Configure using Azure DevOps Pipeline Classic Editor:
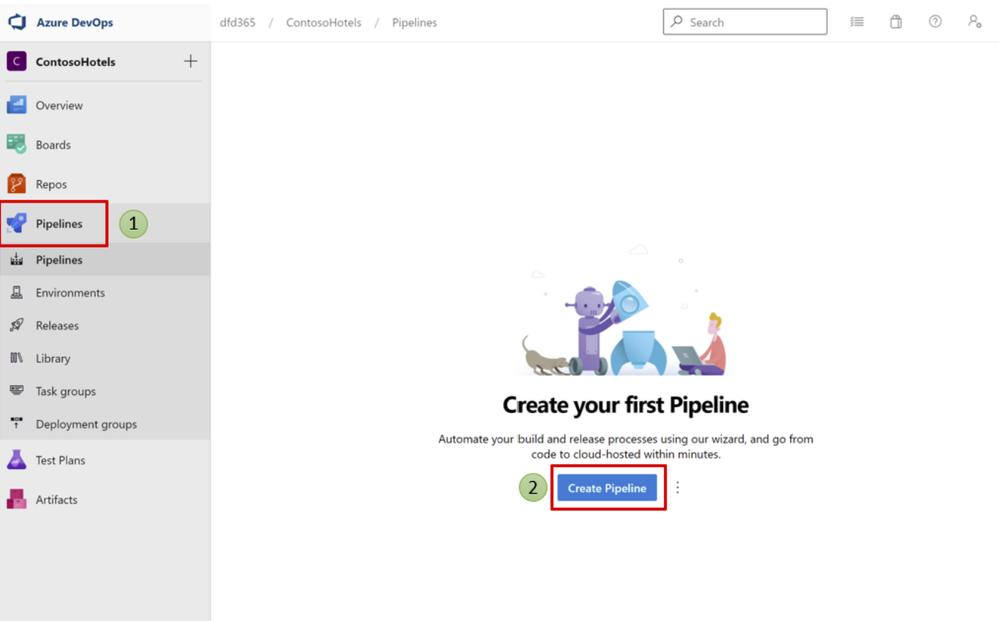
- Select a Project
- Click Pipelines > Click Create Pipeline
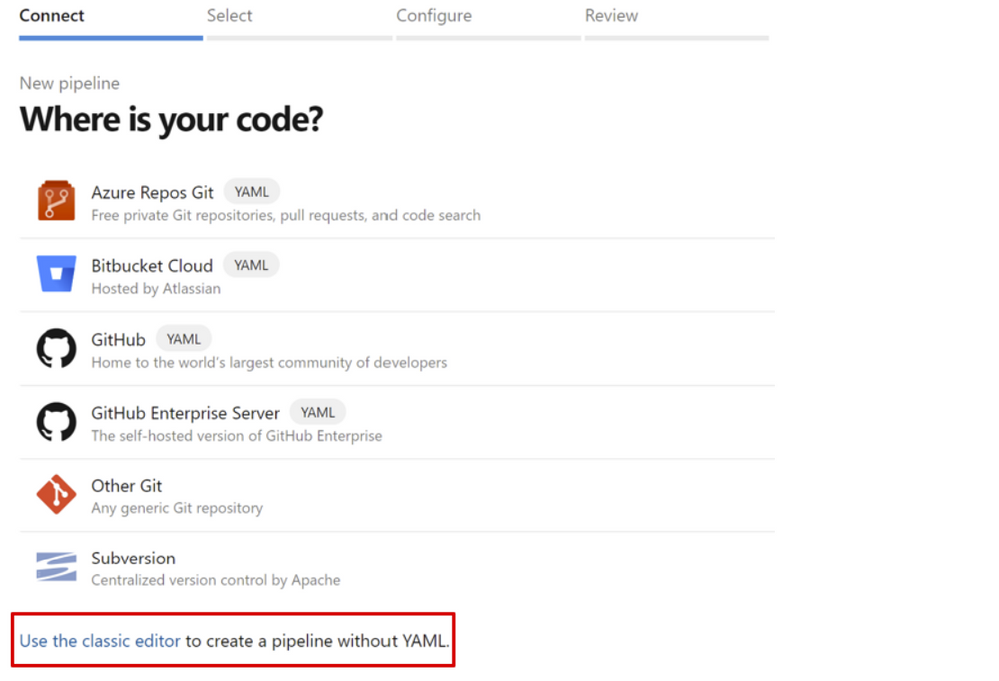
3. Click Use the classic editor to create a pipeline without YAML
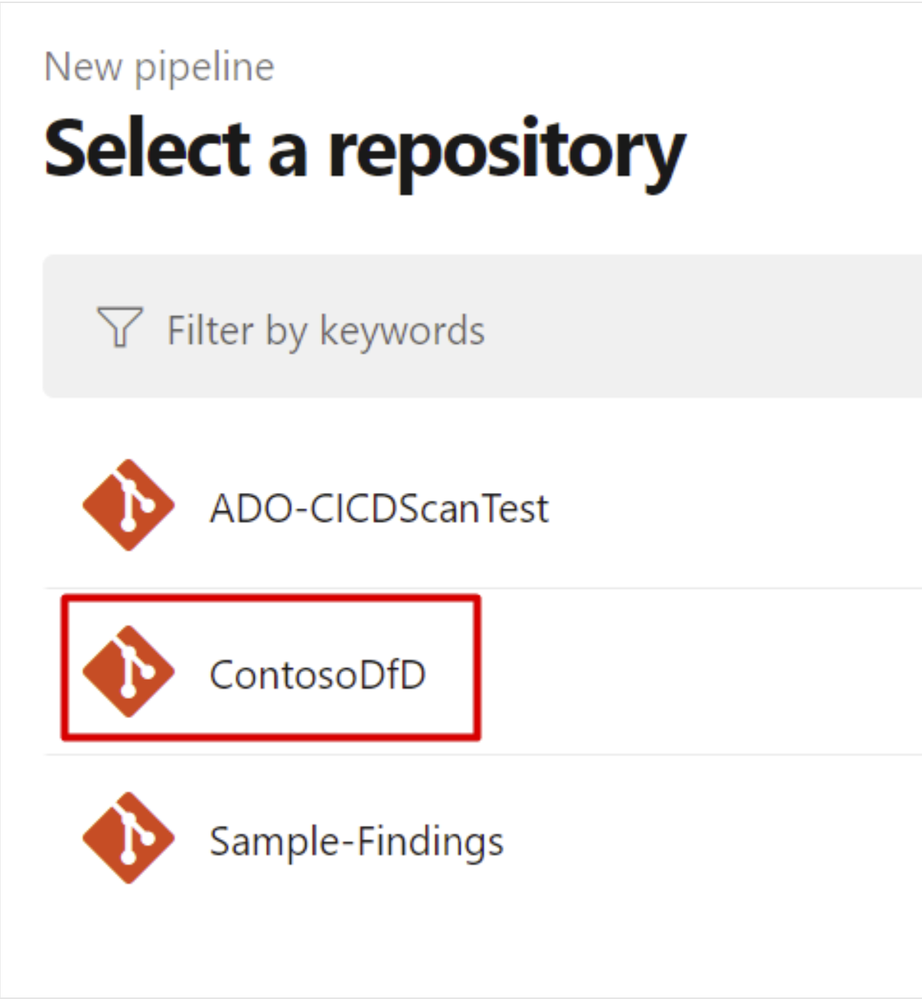
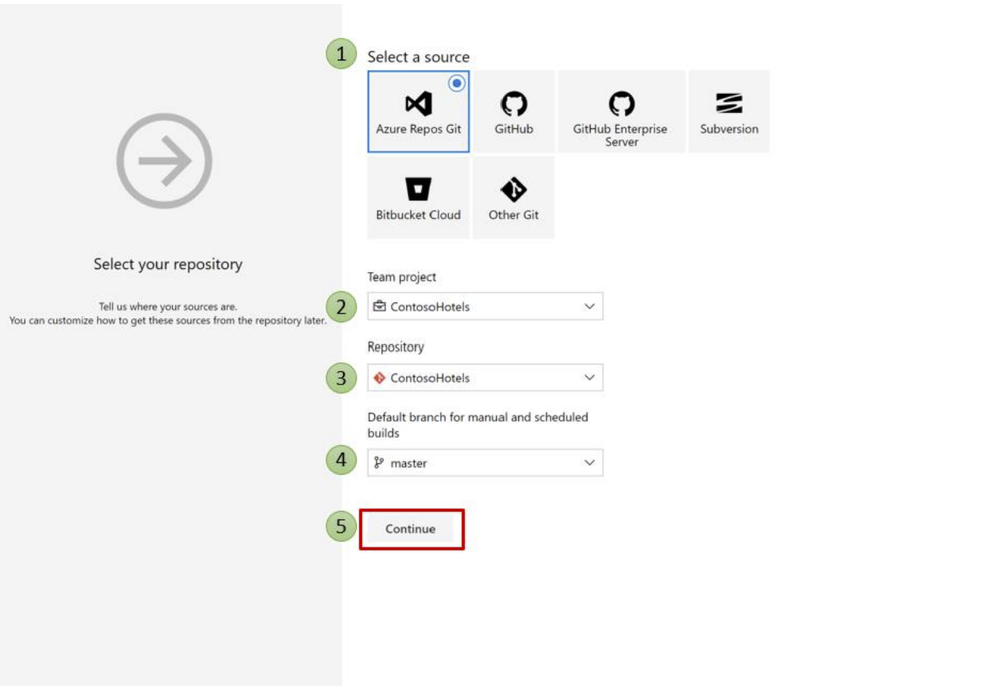
4. Select a source, Team project, Repository, and Default branch from the dropdown menus Click Continue
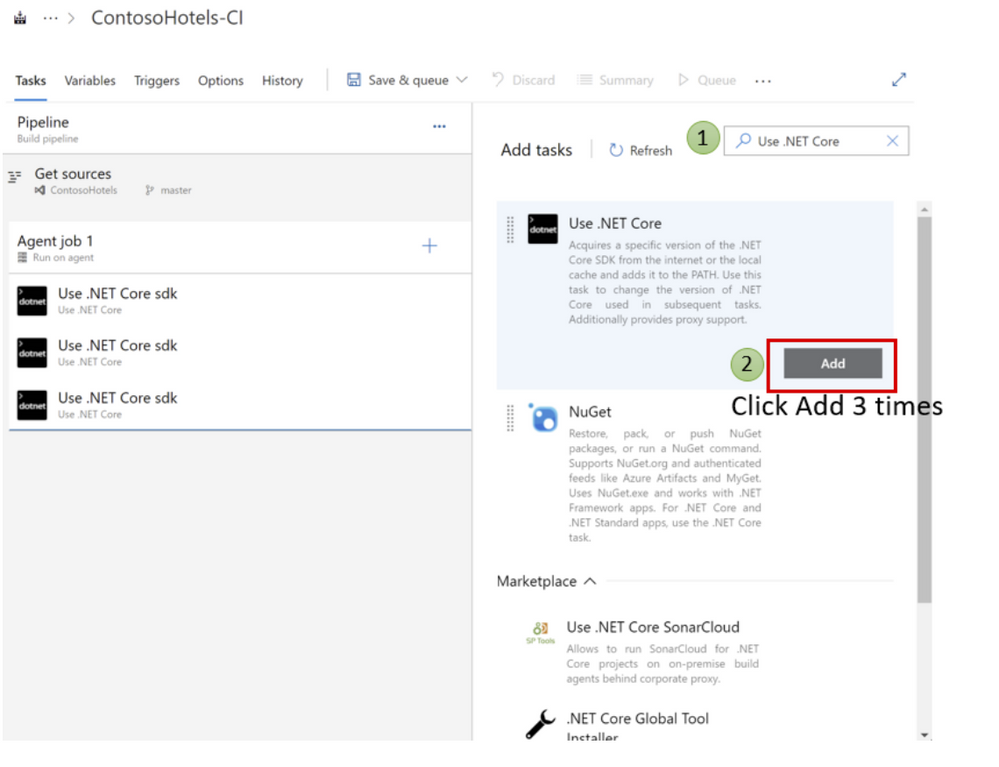
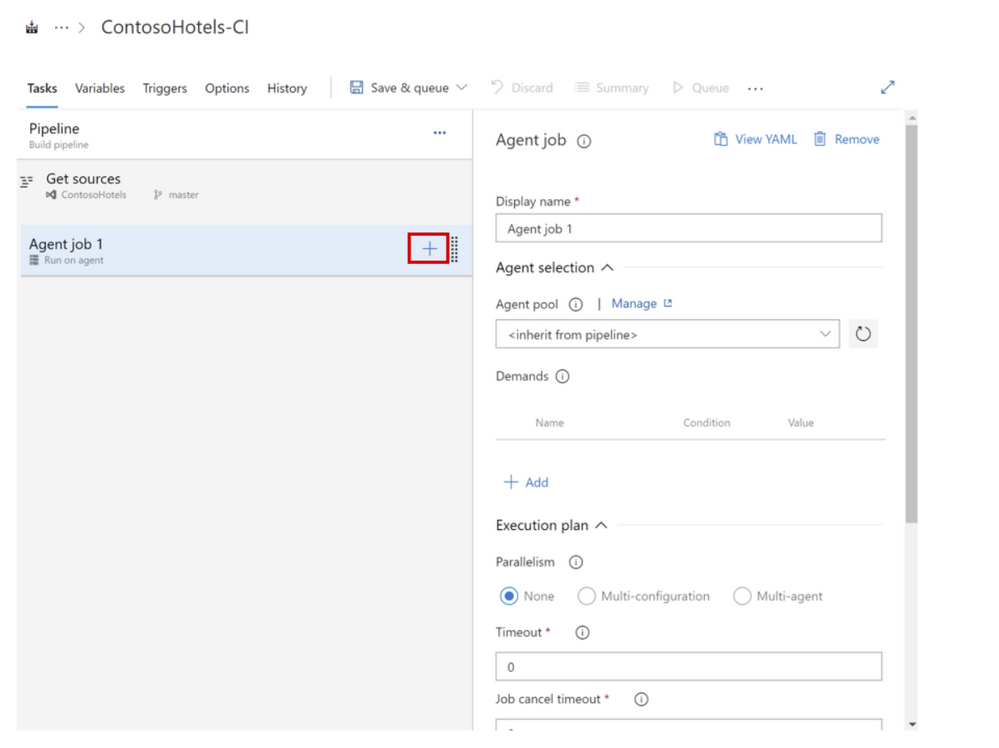
6. On the Agent job 1, click the + to add a step
7. In the search box type Use .NET Core
Click Add 3 times
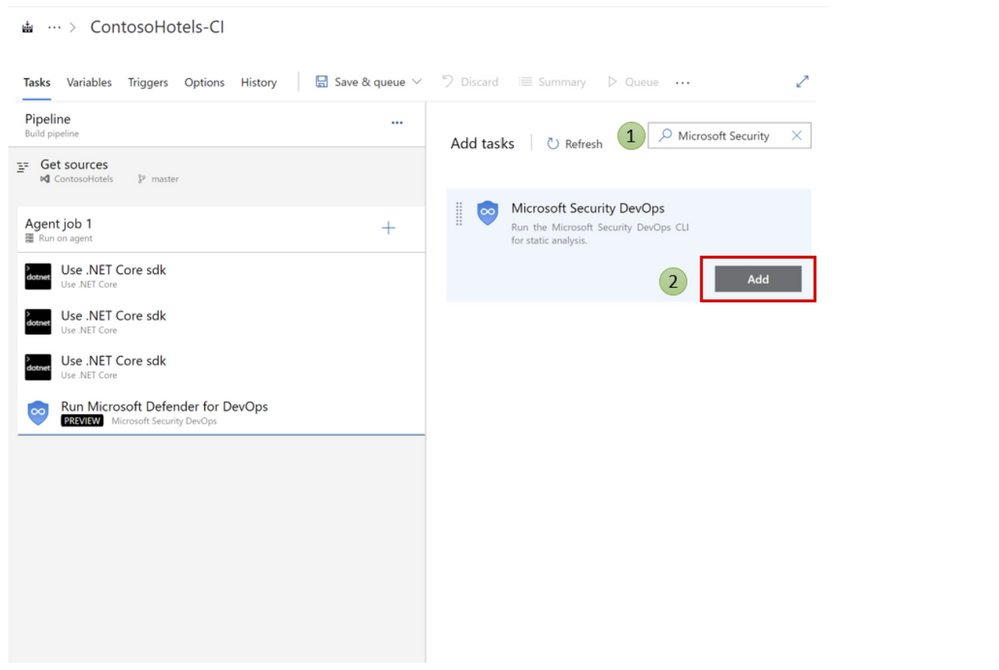
8. Type Microsoft Security in the search box
Click Add on Microsoft Security DevOps to add it to the Agent job 1
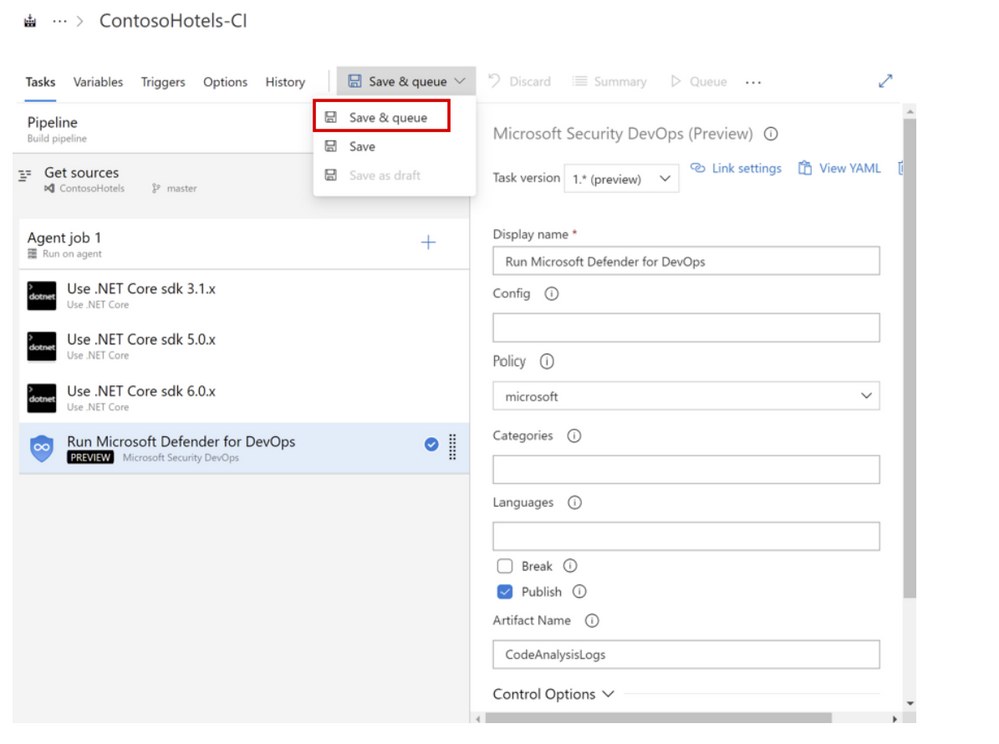
9. Click on each of the Use .NET Core sdk tasks and set the versions as 3.1.x, 5.0.x, 6.0.x
10. Click Save & queue to open the dropdown menu
Click Save & queue
11. Type a Save comment (example: Microsoft Security DevOps added) > Click Save and run
NOTE: It will take a few minutes to run pipelines and save the results. To make viewing the scan results easier, you can install this free extension in your Azure DevOps organization: SARIF SAST Scans Tab - Visual Studio Marketplace
Option 2: Configure your pipelines using YAML
To configure your pipeline using YAML:
- Sign in to Azure DevOps
- Select your project.
- Navigate to Pipelines
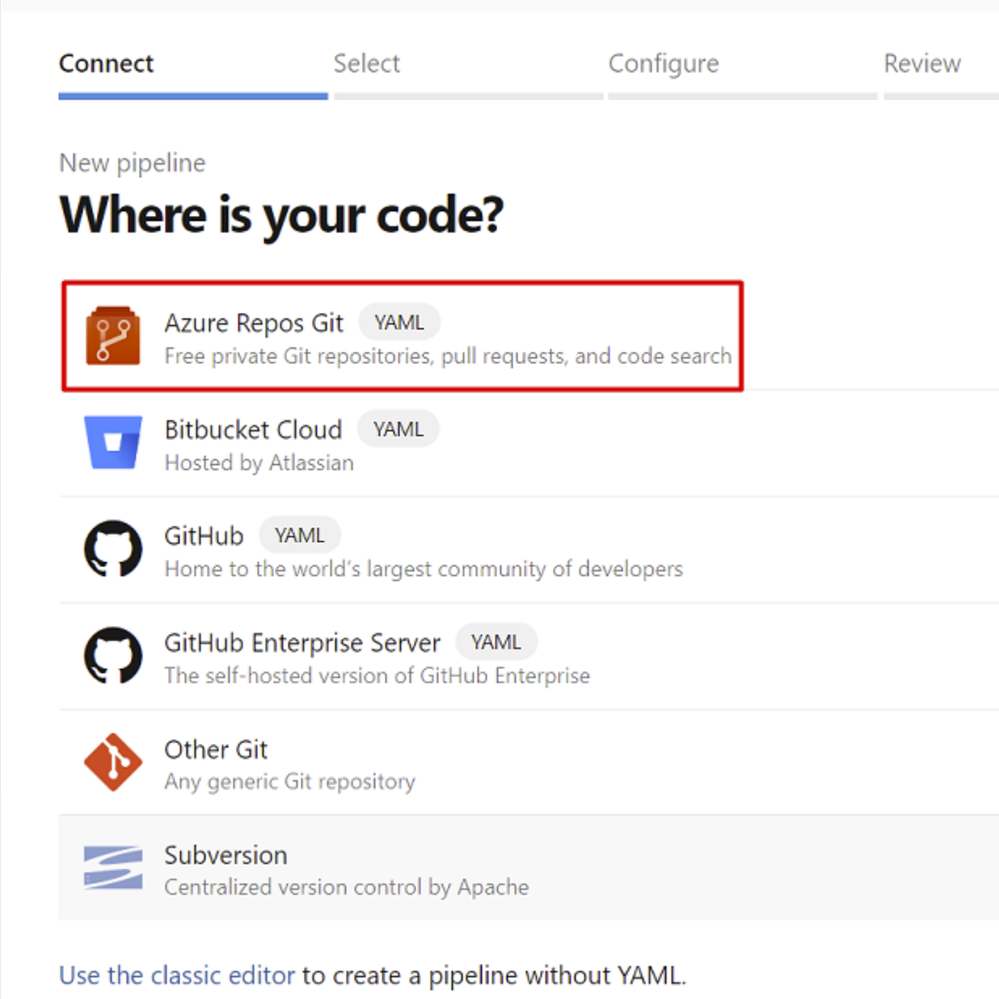
- Select New pipeline.

5. Select Azure Repos Git.
6. Select the relevant repository
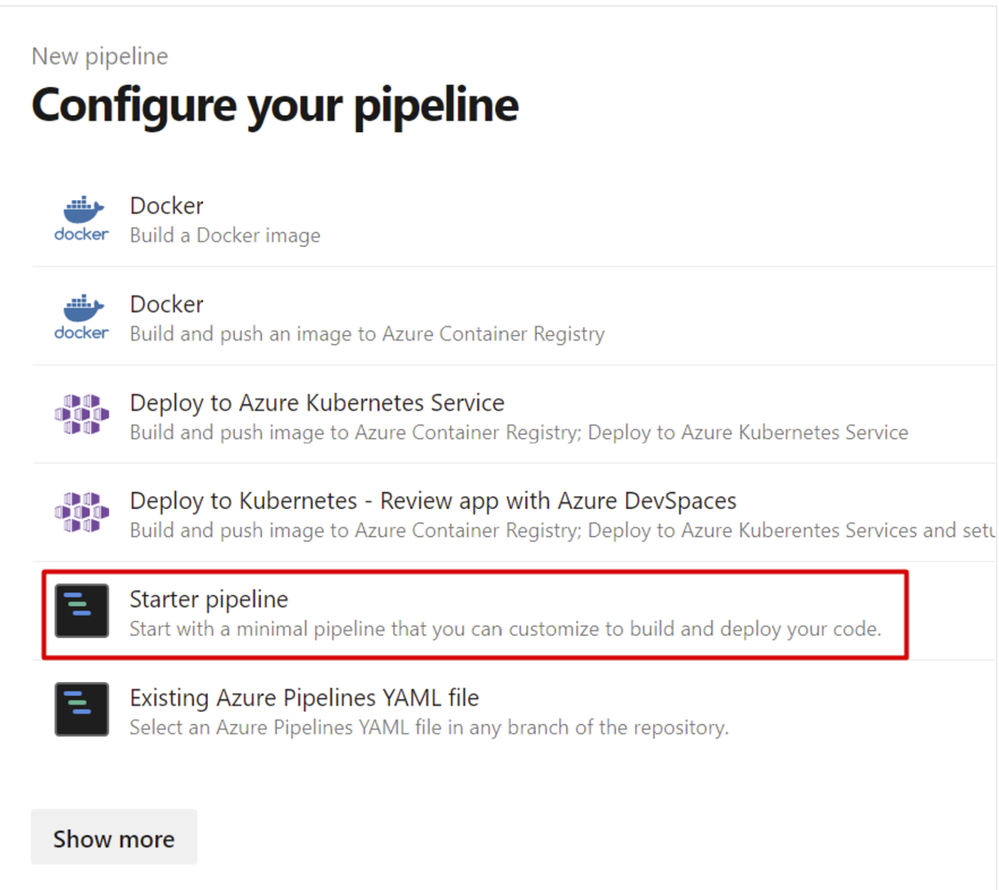
7. Select Starter Pipeline
8. Paste the following YAML into the pipeline:
# Starter pipeline
# Start with a minimal pipeline that you can customize to build and deploy your code.
# Add steps that build, run tests, deploy, and more:
trigger: none
pool:
vmImage: 'windows-latest'
steps:
- task: UseDotNet@2
displayName: 'Use dotnet'
inputs:
version: 3.1.x
- task: UseDotNet@2
displayName: 'Use dotnet'
inputs:
version: 5.0.x
- task: UseDotNet@2
displayName: 'Use dotnet'
inputs:
version: 6.0.x
- task: MicrosoftSecurityDevOps@1
displayName: 'Microsoft Security DevOps'
9. Select Save and run
10. To commit the pipeline, select Save and Run.
The pipeline will run for a few minutes and save the results.
Note:
Install the SARIF SAST Scans Tab extension on the Azure DevOps organization in order to ensure that the generated analysis results will be displayed automatically under the Scans tab.
What Next?
- Learn how to create your first pipeline.
- Learn how to deploy pipelines to Azure.
Additional Resources:
- To learn more about Defender for DevOps capabilities please visit our documentation here
- Would like to try the capabilities in a lab environment? Follow along with our MDC labs here specifically Modules 14 & 15
- Check out our Defender for DevOps Interactive Guide here
- Check out Defender for Cloud in the field features Defender for DevOps here
- To connect your GitHub repositories to Microsoft Defender for Cloud, refer this
- To connect your Azure DevOps repositories to Microsoft Defender for Cloud, refer this
Acknowledgements:
- Special thanks to @Sukhandeep Singh, Senior Program Manager, for the partnership in reviewing and providing feedbacks on the article.