This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Community Hub.
Secure Communication to Fetch SAP NetWeaver SAP Control and SAP RFC (Remote Function Call) Metric Data in Azure Monitor for SAP solution (AMS).
Introduction:
In the previous blog series Part 1 - SAP NetWeaver SOAP & RFC deep dive in Azure Monitor for SAP solutions and Part 2 - Configuring NetWeaver Provider, we have understood the architecture and successfully configured NetWeaver provider as part of AMS (Azure Monitor for SAP) , using HTTP port.
This blog provides an overview of enabling secure communication over HTTPS using TLS 1.2 (or higher) certificate.
AMS (secure communication):
The following diagram shows Azure Monitor for SAP Solutions service with all the available providers and a secure communication layer with TLS 1.2 encryption to collect telemetry from the AMS providers:
Review this document to learn about enabling TLS 1.2 (or higher) in AMS.
Configure SAP NetWeaver for secure communication
The following documentation from SAP explains how to configure X.509 encryption certificates in an SAP ABAP system to enable secure communication.
Configure TLS 1.2 (or higher) in the SAP DEFAULT profile
Check if the SAP system is configured for secure communication using TLS 1.2 (or higher).
- Go to transaction RZ10.
- Open the DEFAULT profile, select Extended Maintenance and click change.
- Below configuration is for TLS1.2, the bit mask will be 544: PFS. If the system is configured with TLS version > 1.2, then bit mask will be greater than 544.
Check the HTTPS port, that will be specified in the AMS configuration, during the create Provider process.
- Go to transaction SMICM.
- Choose from the menu GOTO -> Services.
- Verify if HTTPS protocol is in Active status.
Note: certificate must be from a trusted root authority and cannot be a self-signed.
Secure communication between the AMS NetWeaver Provider and SAP
Review Configure SAP NetWeaver for Azure Monitor for SAP solutions (preview) - Azure Virtual Machines | Microsoft Learn and Part 2 - Configuring NetWeaver Provider to understand how to configure SAP NetWeaver SAP Control and SAP RFC metrics and how telemetry data are fetched through web service-enabled Zeep SOAP client in Python programming.
SAP Control
Metric collection via sapcontrol web methods is done through SOAP URL via HTTPS on port 5xx14, and HTTP on port 5xx13 when HTTPS connection is unavailable as explained in the section SOAP URL in the blog series. When secure communication is enabled, the data transfer from SAP system to AMS landscape is established only through HTTPS connection on port 5xx14.
SAP Remote Function Call (RFC)
Remote-enabled function module is processed through SOAP based HTTP request-response model for metric collection call.
The default protocol for RFC metric data collection is through HTTP with basic user ID and password authentication. When secure communication is enabled, it is defaulted to HTTPS connection and the encryption of data is facilitated by X.509 public-key certificate published by Certificate Authorities (CA).
Configuring NetWeaver via Root Certificate
SAP system configured with TLS1.2 (or higher) certificate, that is part of Microsoft certified trusted authority root available in the list here.
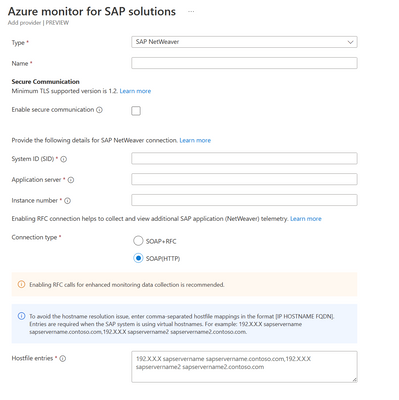
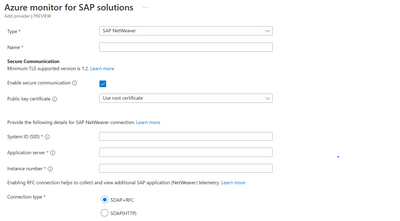
The user needs to check “Enable secure communication” and choose the public key certificate as “Use root certificate” as shown below in the screen shot.
Configuring NetWeaver via Server Certificate:(Azure Storage Blob Container Approach)
If the SAP system is configured with certificates, that are not part of trusted root program from Microsoft, the user needs to prepare a CA_BUNDLE by combining issuer certificate (server certificate), intermediate certificate (1. *) and root certificate into one certificate with .crt or. pem extension.
Note: Open SSL (Secure Sockets Layer) commands can be used to bundle the certificates (OpenSSL create certificate chain with Root & Intermediate CA | GoLinuxCloud)
1. The user needs to check “Enable secure communication” and choose the public key certificate as “Use server certificate” as shown in the screen shot below.
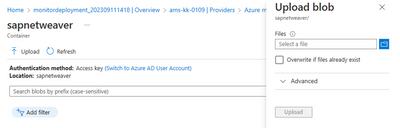
2. Click on the upload button in the "Upload certificate" option to upload the certificate can from the local file folder to the “sapnetweaver” container, that is available in the storage account of managed-resource group in the AMS service
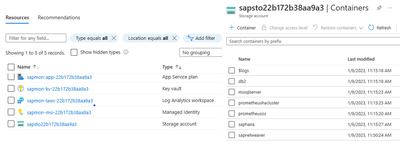
3. In the picture below, on the left are represented the storage account and all other resources available in the AMS managed resource-group. On the right, you see the containers, available for file upload , listed by provider names.
Programmatic representation for server certificate verification
In AMS, Zeep python SOAP client is programmatically implemented for metric collection, and secure communication is established for the WSDL (Web Services Description Language) client on the default port (443) unless specified by the user with a different port.
When server certificate is selected in the UI, WSDL session object “verify” property is initialized with the URL of certificate location or file location path of the certificate. In the AMS service the URL of the storage account container blob(certificate) path is applied as mentioned above in #3 of "Configuring NetWeaver via Server Certificate:(Azure Storage Blob Container Approach)"
Sample code snippet:
|
wsdl_url = "https://sapservername.contoso.com:443/sap/bc/soap/wsdl?sap-client=001&services=/SAPDS/RFC_READ_TABLE" session = Session () session.auth = HTTPBasicAuth(‘XXXX, ‘XXXX’) session.verify =https://sapsto22b172b38aa9a3.blob.core.windows.net/sapnetweaver/chain_cert.crt client = Client( wsdl=wsdl_url, transport=Transport(session=session)) rfcname = rfcname.replace('/', '_-') method = getattr(client.service, rfcname) failed_update_result = method (DATA = data_value, DELIMITER=';', FIELDS=rfc_fld, NO_DATA='', OPTIONS='', QUERY_TABLE='VBHDR', ROWCOUNT = 0, ROWSKIPS = 0 ) |
References:
- To learn more read our documentation and watch video in SAP on Azure YouTube channel.
- Public documentation: Configure SAP NetWeaver for Azure Monitor for SAP solutions (preview) - Azure Virtual Machines | Microsoft Learn
- Maximizing Observability for SAP on Azure with Azure Monitor for SAP solution
- Part 1 - SAP NetWeaver SOAP & RFC deep dive in Azure Monitor for SAP solutions
- Part 3 - Visualizing SAP NetWeaver data in AMS through Azure Workbook