This post has been republished via RSS; it originally appeared at: Microsoft Tech Community - Latest Blogs - .
Introduction
Microsoft Defender for APIs, a new plan in Defender for Cloud, offers full lifecycle protection, detection, and response coverage for APIs published in Azure API Management. One of the main capabilities is the ability to detect exploits of the OWASP API Top 10 vulnerabilities through runtime observations of anomalies using machine learning-based and rule-based detections.
This blog will outline the steps for simulating an action that will trigger an alert for one of your API endpoints through Defender for APIs. In this scenario, the alert will be for the detection of a suspicious user agent.
Validation Steps
- If you don’t have an API Endpoint in Azure API Management Service created yet, make sure to create one following the steps from this article and this article.
- If you haven’t enabled Defender for APIs and onboarded API endpoints, refer to this document for guidance before moving to step 3.
- Once you have completed steps 1 and 2, access the API Management page through the Azure Portal and navigate to the APIs blade.
- Select an API Endpoint (e.g., Echo API).
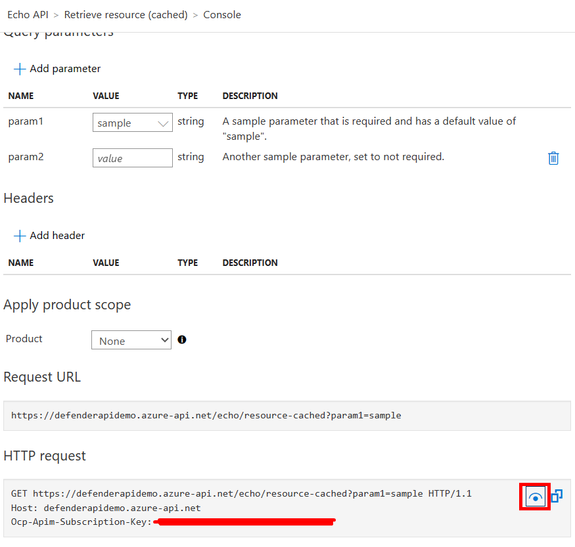
- Select an API Operation (e.g., Retrieve Resource) and then open the “Test” tab.
- Scroll down to the HTTP request section and click on the see more icon to retrieve the full request URL and the APIM subscription key that will be required later. Be sure to copy this information and store it in a secure location. Alternatively, for testing purposes in a non-production environment, you can disable the subscription requirement following the steps here.
- Navigate to Postman and sign up for a new account or login to your existing account.
- In Postman, select “My Workspace” or any other workspace that you already have.
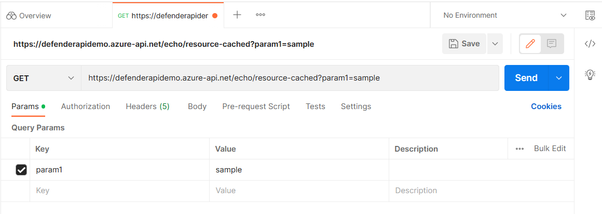
- Select the "+" icon to start a new request. 
- Using the HTTP request information that you copied in Step 6, enter the URL (e.g., GET https://apidemo.azure-api.net/echo/resource-cached?param1=sample) into Postman. Do not send the request yet.
- Select the “Headers” tab.
- Enter the APIM subscription key as a header. The key is Ocp-Apim-Subscription-Key and the value will be the unique value that you copied in Step 6.
- Enter another header for the user agent value. For this step, enter User-Agent as the key and jvascript: as the value. The user agent javascript; contains distinct patterns typical of script code and is rarely used by legitimate user agents. 
- Send the request. You will get a “200 OK” status if the request went through.
Conclusion
After some time, Defender for APIs will trigger an alert with detailed information about this suspicious activity, as shown below:
For a complete list of potential alerts that could be triggered by Defender for APIs, access this reference guide.
Written in collaboration with Liana Tomescu and Yuri Diogenes.