This post has been republished via RSS; it originally appeared at: Core Infrastructure and Security Blog articles.
In the last blog we discussed how to deploy AKS fully integrated with AAD. Also we discussed deploying add-on for Azure Pod Identity and Azure CSI driver. In the article we will discuss how to create an application that using Pod Identity to access Azure Resources.
What is Pod Identity?
Pod Identity is a feature allows applications deployed to communicate with AAD, request a token then use the token to access Azure resources. The simplified workflow for pod managed identity is shown in the following diagram:
You can review Microsoft docs about pod identity best practice here
How to Create an application using Pod Identity?
In order to use pod identity in our code we will need AKS cluster to be configured with Azure AAD and Pod Identity deployed as we discussed in our pervious post.
Depending on the application, we will need to use an authentication MSI library to request a token from AAD. You can review example here
In our previous post we show after deploying Pod Identity addon, terraform script deployed a managed Identity to namespace “demo” and updated the Key Vault access policy to include this managed identity.
In our demo today, we will show how to build application access Azure Key Vault to retrieve secrets using Pod Identity. Sample code exists here. The repo contains sample codes using C#, Java and Python.
Before staring we need to double check out environment to make sure all necessary deployment are deployed
- AAD Azure Identity Pods under Kube-System namespace:
kubectl get pods -n kube-system| grep aad” - Azure Identity resource under target namespace
kubectl get azureIdentity -n demo - Azure Identity Binding resource under target namespace
kubectl get azureIdentity -n demo
Once we confirm the resources then we are ready to start coding.
Java Demo
Source Code Review
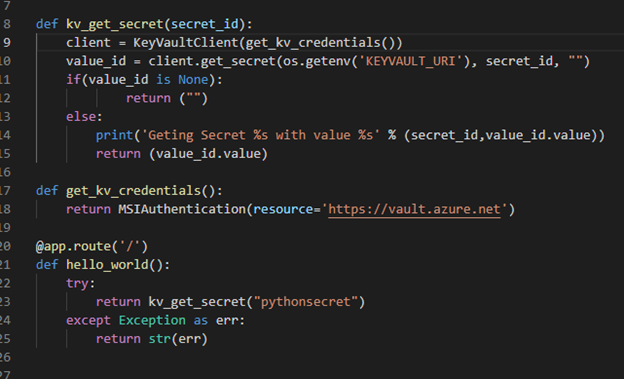
The Java demo is a sample java spring boot RestAPI application. Here are few points about the code
- Add Azure Key vault to pom.xml file
<dependency> <groupId>com.azure.spring</groupId> <artifactId>azure-spring-boot-starter-keyvault-secrets</artifactId> </dependency> - Under application.properties set key vault properties to managed Identity mode
- main class shows how we retrieve the secrets using annotation
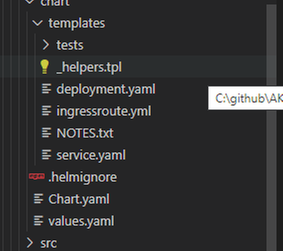
Helm Chart Review
The helm chart will be the same chart for all demos (java/C#/Python) we will override the values.yaml during the pipeline run to fit every demo needs. The chart will deploy the following:
- Applications pods deployment: we can control how many replica from values.yaml
- Service deployment:
- Ingress deployment: map incoming request to app services
The main area we point here will be the metadata label aadpodbinding. The pod deployment file MUST have this label. In our environment we deployed the AzureIdentity and AzureIdentityBinding with same name like environment namespace hence we passing the namespace as value for aadpodbinding
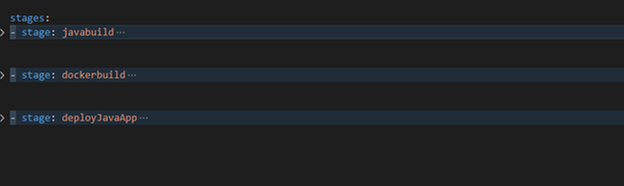
Pipeline Review
The pipeline “azure-pipelines-java-kv.yml” has 3 stages as shows in the following figure:
- Java Build: using Maven will package the app and publish it with chart
- Docker Build: using docker will build an image and publish it to ACR
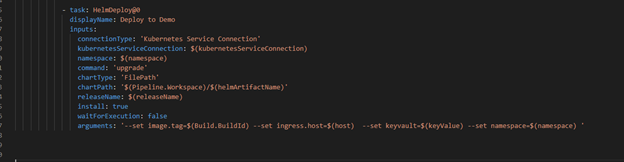
- Helm Deployment: using helm will connect to AKS then install helm chart under namespace “demo”. Please notice how we passing new chart values as argument
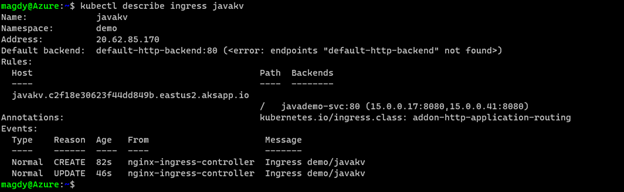
Once it runs, we should see the following:
Check our work:
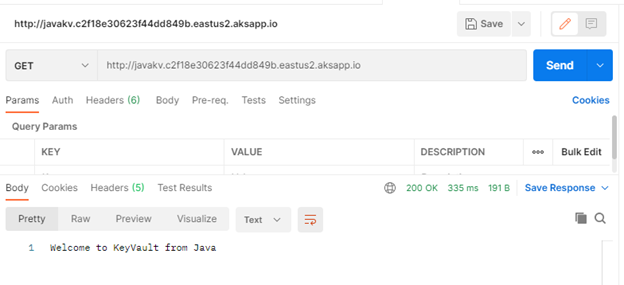
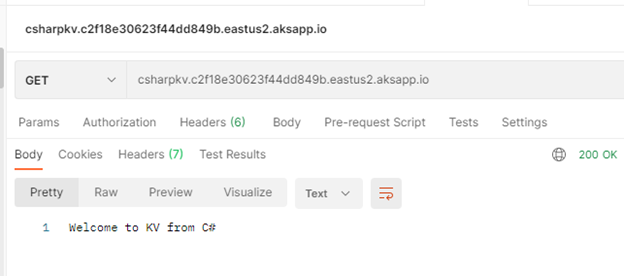
Finally Use Postman and query the Java app.
C# Demo
Source Code Review
Demo is identical to Java code. Rest API service that shows secret from KV. The API class is under controller folder and it expect KV URL to pass as environment variable exactly like Java example.
The pipeline for “azure-pipelines-csharp-kv.yml” is follow same structure of 3 stages
- CSharp Build: using dotnet will package the app and publish it with chart
- Docker Build: using docker will build an image and publish it to ACR
- Helm Deployment: using helm will connect to AKS then install helm chart under namespace “demo”. Please notice how we are passing new chart values as arguments
Python Demo
Source Code Review
Python code is a FlaskRest API example.
The pipeline for “azure-pipelines-python-kv.yml” is follow same structure of 2 stages.
- Docker Build: using docker will build an image and publish it to ACR
- Helm Deployment: using helm will connect to AKS then install helm chart under namespace “demo”. Please notice how we are passing new chart values as arguments.
Check our work:
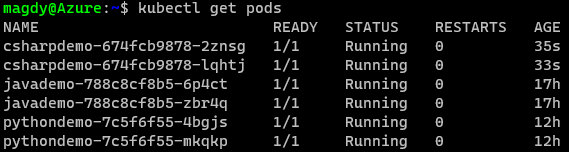
Once we get pipelines deployed for all application, we can review the deployed resources.
Use Postman to call apps using ingress host.
Java Demo
Python Demo
C# Demo
Summary
We discussed in detail how to setup and configure your application to use Pod Identity. It is great feature to utilize Azure Managed Identity to access Azure resources. In our next blog will discuss Azure secret store provider for csi driver
Disclaimer
The sample scripts are not supported under any Microsoft standard support program or service. The sample scripts are provided AS IS without warranty of any kind. Microsoft further disclaims all implied warranties including, without limitation, any implied warranties of merchantability or of fitness for a particular purpose. The entire risk arising out of the use or performance of the sample scripts and documentation remains with you. In no event shall Microsoft, its authors, or anyone else involved in the creation, production, or delivery of the scripts be liable for any damages whatsoever (including, without limitation, damages for loss of business profits, business interruption, loss of business information, or other pecuniary loss) arising out of the use of or inability to use the sample scripts or documentation, even if Microsoft has been advised of the possibility of such damages.