This post has been republished via RSS; it originally appeared at: Intune Customer Success articles.
By Pallavi Joshi - Sr. Program Manager | Microsoft Endpoint Manager - Intune
Microsoft Endpoint Manager Role-based access control (RBAC) helps you manage who has access to your organization's resources and what they can do with those resources determine what they can do with those resources. Roles determine what access admins have to which objects. Scope tags determine which objects admins can see.
There are scenarios across organizations, where an organization has various regions or departments, and each region needs to work independently of other regions. For such scenarios, there are regional admins who need to manage devices in their region, but not have visibility over devices of other regions. To achieve this scenario using Endpoint Manager, central IT would use RBAC and scope tags. Once a scope tag is assigned to a device, that device is visible only to regional admins who have the same scope tag assigned to them in the role definition.

For large organizations with thousands or tens of thousands of devices, it is critical that the scope tags get assigned to a device automatically, based on the region the user owning the device belongs to. To achieve this, the following steps need to be performed:
- Admins need to have a clear identification of devices belonging to a region. This step is the focus of this article.
- Based on the above identification, admins create Azure AD device group containing devices belonging to a specific region.
- This Azure AD device group is assigned to the relevant scope tag, which ensures that scope tags automatically get added to all the devices in that group.
To achieve step 1 mentioned above, there are various options, each with its pros and cons listed below:
Option 1 – Assigned groups
If you have the identification of which devices belong to which regions, you can create an Azure AD assigned device group and add the respective devices manually in the group.
Once the Azure AD device group is created, it can then be assigned to the scope tag for that region. The table below lists pros and cons for this option:
Pros
|
Cons
|
Option 2 – Dynamic groups
You can use Azure AD dynamic device groups to automatically add devices in a group based on a device’s attributes. For example, you can use RBAC to provide secure access to your admins based on platforms. The options below list various attributes that can be used for creating Azure AD dynamic device groups.
Option 2a – Device categories
You can use device categories to automatically add devices to groups based on categories that you define. In this scenario, you can create one device category for each region.
When users enroll a device, they must choose a category from the list of categories you configured. You can then create dynamic groups in the Azure portal, based on the device category and device category name, for example: device.deviceCategory -eq "German devices".
Once Azure AD device group is created, it can then be assigned to the scope tag for that region. The table below lists pros and cons for this option:
Pros
|
Cons
|
Option 2b – Enrollment profiles
For specific scenarios, you can create enrollment profiles per region for enrolling devices. If you are using Automated Device Enrollment for iOS, iPadOS and macOS, you would create separate enrollment profiles per region. For Windows devices, you would use group tags as an attribute to create Autopilot device groups. For Android Enterprise dedicated device enrollment and corporate-owned work profile devices, you would create separate enrollment profiles per region as well. You can use the enrollment profile name for creating Azure AD dynamic device group, for example: device.enrollmentProfileName -eq "Spain iOS Kiosk Profile".
Once Azure AD device group is created, it can then be assigned to the scope tag for that region. The table below lists pros and cons for this option:
Pros
|
Cons
|
Option 3 – Scripts
For the scenarios where enrollment profile is not used while performing enrollment, you can use PowerShell scripts. If you have an identification of which users belong to which regions, you can use this information to query devices for each user belonging to a region and add the devices in a group. This would lead to all the devices of users belonging to a region now added to specific device groups. Here’s an example flowchart showing the same:
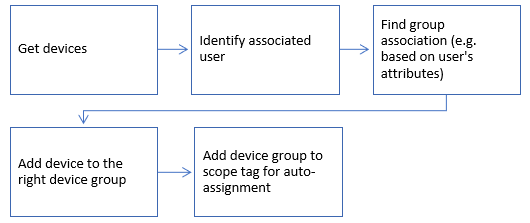
We have various script samples that can be used as examples and run at various frequencies depending on your scenarios, as listed below:
Sample script to enumerate devices, determine primary owner and add devices to a group
Sample script to add managed devices to a group based on associated user’s username
We recommend that you run the script once weekly, and then run a separate version more frequently based on the enrollment time frame since the last run, for optimal performance. Running the script too frequently against a large tenant can impact the performance negatively and might, at times, cause delays while running the script or using Endpoint Manager.
For the cases where employees change regions, you need to ensure that the script is updated with relevant information and maintained for accurate scope tag assignments.
Important: The scripts above are examples. From a support perspective, Microsoft fully supports Intune. However, Microsoft does not support the scripts themselves. They are provided for example only and you are responsible for anything they may do within your environment. Always test!
Once Azure AD device group is created, it can then be assigned to the scope tag for that region. The table below lists pros and cons for this option:
|
Pros
|
Cons
|
Besides the options listed above, you can use various other ways to create Azure AD device groups, for example, if devices in a region start with specific name, that can be used to create Azure AD dynamic device groups. This is dependent on how you identify devices belonging to a region.
We have seen customers using various options listed above. If you can use enrollment profiles for performing enrollment and creating Azure AD dynamic device groups based on the same, then it provides a simplistic solution to creating groups and using them for automatic scope tag assignment. If you have large number of devices, users, and regions then scripts provide a robust way to identify and add devices to a group, equips you with a solid automation model, and provides a lot of flexibility.
We hope this article helps you with progressing in your endpoint management journey and deploy Endpoint Manager at scale, with delegation, across your entire organization.
Let us know if you have any additional questions by replying to this post or reaching out to @IntuneSuppTeam on Twitter.
