This installment is part of a broader series to keep you up to date with the latest features in Azure Sentinel. The installments will be bite-sized to enable you to easily digest the new content.
In the today’s landscape, Security operations center (SOC) analysts constantly face the challenge of prioritization due to the overwhelming number of notifications they must triage and investigate. With a never-ending stream of security alerts, reports and a widening array of security tools designed to help safeguard their critical assets, an average of 44% of security alerts fall through the crack and are never investigated.
To help alleviate the alert fatigue, we are delighted to announce that the incident settings and alert grouping tab is now in public preview. This feature is designed to help reduce the noise in your Azure Sentinel incidents queue.
Today, each alert generated from a scheduled Analytics rule creates a new Azure Sentinel incident.
With the new aggregation capabilities, we can reduce the number of alerts your SOC analysts consume when the same entities match.
Walkthrough
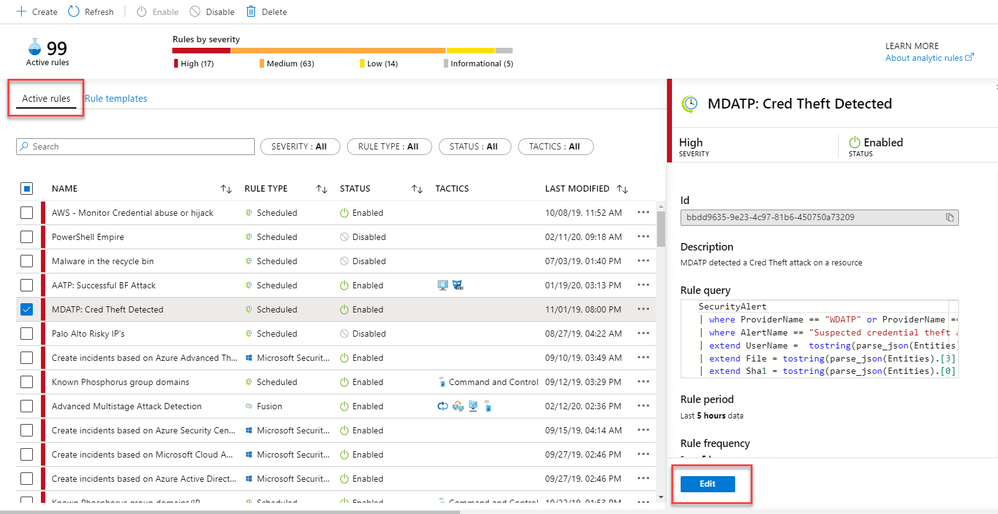
- In Azure Sentinel, select Analytics
- Edit an active scheduled analytic
3. Click on the new “Incident Settings” tab in the Analytics rule wizard to configure how alerts generated by that analytic rule are aggregated into incidents.
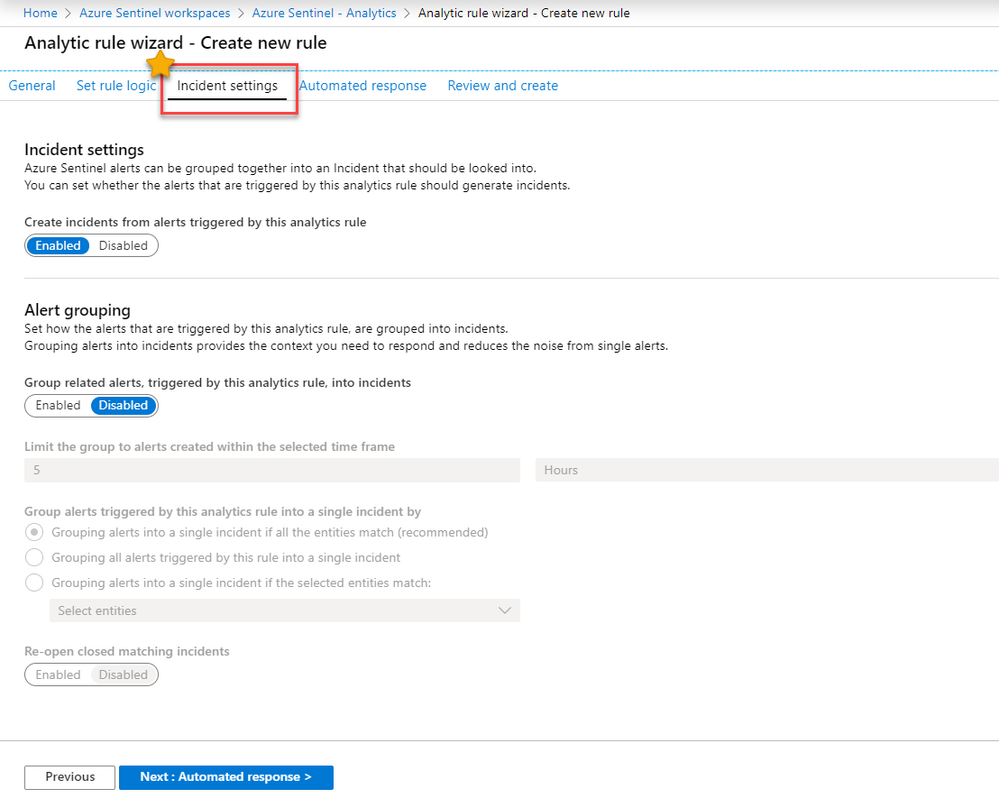
The new incident settings tab is segmented into two areas: “Incident Settings” and “Alert Grouping”.
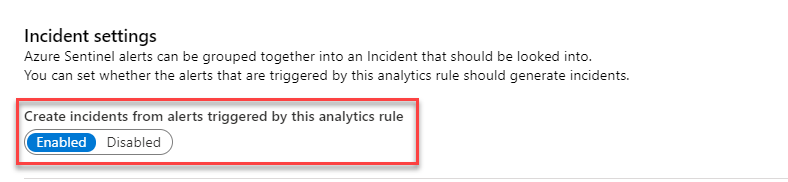
Incident Settings
4. Enable the following button to elevate the alerts triggered by the analytic rule to incidents
Note: You can also decide to run scheduled alerts that do not generate an incident at all, they will be saved in the SecurityAlert table in your Azure Sentinel workspace.
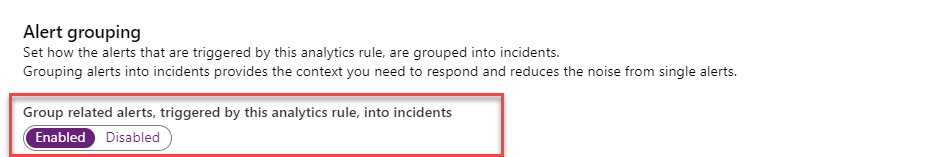
Alert Grouping
Alert grouping is where the magic happens. You have the flexibility to group alerts triggered by an analytic rule into actionable incidents. Grouping alerts into incidents provides the context you need to respond and reduces the noise from hundreds of single alerts.
5. Enable the following button to group related alert into incidents
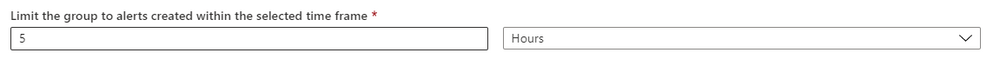
6. Then, Specify a time frame to limit the group to alerts created
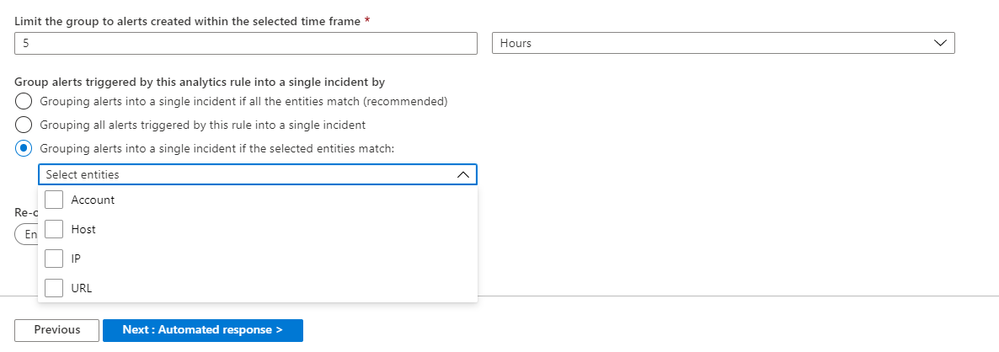
7. You have the flexibility to group alerts into a single incident per the following logic:
- Grouping alerts into a single incident if all the entities match (recommended)
- Grouping all alerts triggered by this rule into a single incident
- Grouping alerts into a single incident if the selected entities match (Account, Host, IP, URL)
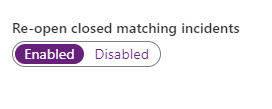
8. Below you have the control you re-open closed matching incidents and kick start an investigation.
Get started today!
We encourage you to use the new alert grouping feature to reduce the alert noise and improve prioritization in your environment.
Note – The Incident Settings and Alert Grouping documentation will be available in 1-2 weeks.
Try it out, and let us know what you think!