This post has been republished via RSS; it originally appeared at: Configuration Manager Blog articles.
The global health crisis has dramatically changed life for all of us. We are working to get you the information and guidance you need to keep your people productive and secure. Two weeks from today is Patch Tuesday, which will provide the April 2020 security update for supported versions of Windows.
A couple of weeks ago I published a blog detailing the options and configuration available in Microsoft Endpoint Configuration Manager to allow a remotely managed PC to intelligently leverage the broadband connection without adding traffic load on the VPN connection back to corporate network.
A common theme in the questions we’ve seen after that post is customers asking how they can continue to patch based on their specific configuration and environment. Two weeks from today (April 14, 2020) is the April Patch Tuesday, so this article is designed to help you successfully deliver patches to your managed PCs that are no longer on-premises and connecting via VPN using home broadband networks. We will take you through a decision tree of options available to your organization when it comes to managing your upcoming patch deployments as we approach the April 2020 security update.
We know that every enterprise and small business is different, with different scenarios across their organizations. This article will help you use your existing patch strategy to update your remote machines. In some of your organizations, more than one of these VPN scenarios may apply, so please follow the appropriate guidance for that part of your organization. In some companies, more than one of the scenarios may be implemented.
VPN Guidance
The Microsoft recommended approach is to configure the VPN client to only send traffic bound for corporate resources located on-premises via the VPN connection, allowing all other traffic to go directly to the Internet and to be routed accordingly. This is how the VPN is configured internally at Microsoft. This also aligns to how we are securing our internal network through zero trust.
There has already been some great content published on VPN and configuration, I won’t go into that in too much detail here, so if you’re looking for guidance on how to start deploying a VPN, or you want more information on the best practices for configuring split tunnel, here some resources on how to position the value of split tunnel VPN and zero trust IT:
- Microsoft Security blog: https://www.microsoft.com/security/blog/2020/03/26/alternative-security-professionals-it-achieve-modern-security-controls-todays-unique-remote-work-scenarios/
- Office 365: VPN Implement Split Tunnel: https://docs.microsoft.com/office365/enterprise/office-365-vpn-implement-split-tunnel
- Zero Trust: https://www.microsoft.com/security/business/zero-trust
Common VPN scenarios
I’ll start by borrowing from one of those articles and describe the broad buckets customers typically fall into when it comes to VPN configuration:
- No VPN
- VPN forced tunnel: 100% of traffic goes into the VPN tunnel, including on-premise, management, Internet and all Office 365 or Microsoft 365 traffic
- VPN Selective Tunnel: VPN tunnel is used only for corpnet-based services. Default route (Internet and all Internet based services) goes direct
- VPN Forced Tunnel with few exceptions: VPN tunnel is used by default (default route points to VPN), with few, most important exempt scenarios that are allowed to go direct
- VPN Forced Tunnel with broad exceptions: VPN tunnel is used by default (default route points to VPN), with broad exceptions that are allowed to go direct (such as all Office 365 or Azure-routed traffic, etc.)
I don’t have a (split tunnel) VPN
If you don’t have a VPN, then it’s possible to configure ConfigMgr to leverage cloud services by default, and you should consider using Intune to manage your Windows Updates deployments without the need for any on-prem infrastructure.
If you do have a VPN but it routes all traffic back on premises, then unfortunately you cannot direct ConfigMgr traffic away from the VPN, and all update traffic will flow from the on-premises servers. This can be problematic for normal day-to-day operations, but the impact is likely exacerbated when faced with a patch deployment to remote machines.
Split tunnel defaults to Internet
If this is your configuration, happy days. To leverage the split tunnel, in the Configuration Manager console you’ll need to:
- Configure a boundary that encompasses your VPN clients
- Create a boundary group to control your VPN clients and assign the VPN boundary(s)
- Associate the boundary with the Cloud Distribution Point (CMG) and / or Cloud Distribution Point (CDP)
- Configure the boundary group to leverage cloud sources
- Configure your update deployments to use Microsoft Updates
This will allow your clients to directly receive the Patch Tuesday updates from the Internet, without adding congestion traffic on your corporate VPN.
Configuring split tunnel with known FQDNs.
We know that a number of customers aren’t quite ready to adopt split tunneling to the Internet because of current security or networking policies. If you’re in that position, then you can configure the split tunnel to direct known traffic to cloud services.
In this context, cloud services mean a combination of CMG, CDP, and Microsoft Update.
The FQDN of your CMG / CDP should be known to you already. Depending on your configuration, this will be either CMGhostname.cloudapp.net or CMGHostname.domainnameFQDN e.g. ContosoCMG.Contoso.com.
If you have a CDP or a content enabled CMG then, in addition to the service FQDN, the client will also need to retrieve content from *.blob.core.windows.net and also access *. table.core.windows.net to enable cloud-based content lookup.
For Microsoft Update, you will need to whitelist the endpoints in this article
- https://*.prod.do.dsp.mp.microsoft.com
- http://emdl.ws.microsoft.com
- http://*.dl.delivery.mp.microsoft.com
- http://*.windowsupdate.com
- https://*.delivery.mp.microsoft.com
- https://*.update.microsoft.com
- https://tsfe.trafficshaping.dsp.mp.microsoft.com
If this applies to you, you can follow all the steps in my last blog. To leverage the split tunnel, in the Configuration Manager console you need to:
- Configure a boundary that encompasses your VPN clients
- Create a boundary group to control your VPN clients and assign the VPN boundary(s)
- Associate the boundary with the Cloud Distribution Point (CMG) and / or Cloud Distribution Point (CDP)
- Configure the boundary group to leverage cloud sources
- Configure your update deployments to use Microsoft Updates
This will allow your clients to directly receive the Patch Tuesday updates from the Internet, without adding congestion traffic on your corporate VPN.
Configuring split tunnel with known IP ranges.
We’ve also heard from customers that some VPN client configurations do not allow FQDN for configuring split tunnel whitelisting. If you fall into this category, then you can use the documented Microsoft addressable space in the following article: https://www.microsoft.com/download/details.aspx?id=53602. This will cover your CMG and CDP services, but does not cover Microsoft Update, so you need to keep reading.
Cannot configure split tunnel VPN to whitelist Microsoft Update
If you’re in this situation, the tradeoff you now face is to either deliver content from an on-prem distribution point over the VPN, or by using a CDP to deliver directly from the Internet and reduce the load on the VPN.
Normally, the Configuration Manager client will prefer Microsoft Update over Cloud Distribution Point, because we don’t want you to pay for content from a Microsoft cloud service that is available for free on a different Microsoft cloud service. For the April 2020 updates cycle specifically, the estimated cost is going to range anywhere between $0.01 and $0.10 per client based on a number of factors, including but not limited to:
- The OS being patched
- Major version
- Current patch level
- The type of updates being deployed
- The pricing tier of Azure you are on
- Your organization’s existing usage of Azure
There are actions you can take to minimize the payload size for updates and ultimately reduce the necessary transfer from the CDP.
Now, at this point I fully expect that a multi-way discussion between networks, security, client management, and potentially procurement teams need to take place to determine the acceptable trade off in network savings versus cost.
I’ll skip forward to the point where the tradeoff has been decided. If the decision is to configure split tunneling, great…. Go back 3 places and start the decision tree again to find the guidance that applies for your newly applicable split tunnel configuration.
If you’ve decided to use Cloud Distribution Point in order to leverage the split tunnel configuration then… in the event the client fails to retrieve content from Microsoft Update, it will automatically fallback to CDP. But there are steps you can take in the Configuration Manager console to ensure the client automatically retrieves content from CDP:
- Configure a boundary that encompasses your VPN clients
- Create a boundary group to control your VPN clients and assign the VPN boundary(s)
- Associate the boundary with the CMG and / or CDP
- Distribute the updates packages to the content enabled CMG / CDP
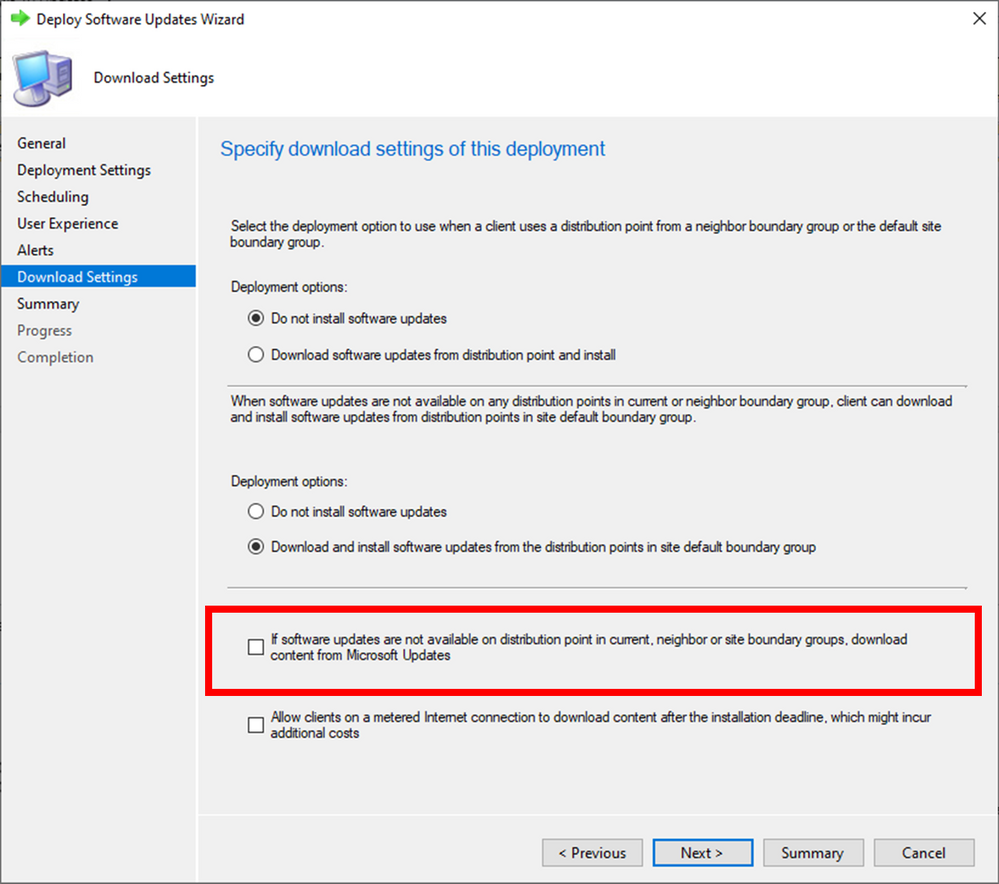
- DISABLE the “If software updates are not available on distribution point in current, neighbor or site boundary groups, download content from Microsoft Updates” check box on the updates deployment
These are unprecedented times and we are here to help and share guidance so you can keep your employees connected. We continue to update our Microsoft COVID-19 Response resources with guidance and learnings, please check frequently for more ideas and information: https://news.microsoft.com/covid-19-response.
As always, we would love to hear your experiences and feedback. Either use the comments below or join the conversation in our Remote Work Tech Community to share, engage and learn from experts.
Rob York
Program Manager
Microsoft Endpoint Manager