This post has been republished via RSS; it originally appeared at: Microsoft Tech Community - Latest Blogs - .
Overview
Threat intelligence is the data organizations need to map threats to the enterprise and enable the best possible decision-making related to risk. Microsoft Defender Threat Intelligence (Defender TI) serves as a valuable source of attack surface threat intelligence on global, industry, and local threats, with content from hundreds of OSINT sources complementing original research, shared from Microsoft's own Defender, MSTIC, and Section52 research groups. As an analyst working with threat intelligence, it's easy to become overwhelmed by the volume of data out there. Still, within the Defender TI portal, the ability to quickly find data relevant to your needs is kept top of mind.
Before we drill into the Defender TI Threat Intelligence portal, take a look at this blog post for a deep dive into the types and benefits of threat intelligence and the threat intelligence lifecycle.
Disclaimer
Defender TI may include live, real-time observations and threat indicators, including malicious infrastructure and adversary-threat tooling. Any IP, domain, and host searches within our Defender TI platform are safe to search. Microsoft will share online resources (e.g., IP addresses, domain names) that should be considered real threats posing a clear and present danger. We ask that users use their best judgment and minimize unnecessary risk while interacting with malicious systems when performing exercises provided in this module. Please note that Microsoft has worked to reduce risk by defanging malicious IP addresses, hosts, and domains.
Articles
The content in the Defender TI portal sources hundreds of OSINT as well as original Microsoft Defender Threat Intelligence research articles enriched with indicators from the Defender TI global collection network. For more information, see What is Microsoft Defender Threat Intelligence (Defender TI)? and review the Articles sections.
Figure 1 – Defender TI Articles
Finding New Connections from Previously Published Articles
Original research published by Microsoft's internal research teams is especially valuable to review to better understand how the various datasets within Defender TI can be woven together to profile complex threat actor activity.
As an example, review the article ToddyCat: A Guided Journey through the Attacker's Infrastructure to observe how Microsoft Defender Threat Intelligence researchers were able to start with work performed by other community researchers and build upon it to illuminate threat actor infrastructure even further by pivoting through Defender TI.
Suppose you spot a detection linked to a Defender TI article. In that case, it's important to understand when it was published to then identify new infrastructure you may want to block and monitor across your network. That's a massive value-add of our Defender TI platform – the ability to identify previously recognized threats and new infrastructure related to those threats. Threat actor infrastructure changes over time, especially when it's been published. They know they need to change their infrastructure to try and mitigate being detected in future campaigns.
As of the time of writing this module, the ToddyCat article had been published for two months. Here are some techniques I took to identify new infrastructure associated with the already published Public indicators related to the article.
- Searched SSL Certificate, 94130bf60597277fec30b3d25d65199ad329015a.
Are there any new IP addresses that have observed this SSL Certificate Sha-1?
Findings:
- No new IPs were identified observing this SSL Certificate.
- Observed what SSL Certificate components, such as '"Internet Widget Pty Ltd"' as the certificate's organization subject and issuer names, were used to identify if related IPs observed new SSL Certificates with similar components.
- Searched those IPs that had observed the SSL Certificate in step 1.
Are there any new A record resolutions associated with these IP addresses?
Findings:
- 5/14 IP addresses that observed SSL Certificate, ‘94130bf60597277fec30b3d25d65199ad329015a’, observed new A record resolutions. The hosts in the gold text below, time.pornhumen[.]com and ca3jfa.whatsupman[.]net, follow the TTPs associated with ToddyCat, so we will investigate those next.
- 207.148.8[.]47
- 149.28.220[.]70
- cusdis.961996[.]xyz
- www.961996[.]xyz
- sub.961996[.]xyz
- gitlab.961996[.]xyz
- display.961996[.]xyz
- dns-acme.961996[.]xyz
- jamdict.961996[.]xyz
- minio.961996[.]xyz
- vnc.961996[.]xyz
- rss.961996[.]xyz
- favicon.961996[.]xyz
- jd-quit.961996[.]xyz
- www.dns-acmess.961996[.]xyz
- dns-acmess.961996[.]xyz
- http-acmes.961996[.]xyz
- kpi.961996[.]xyz
- qbit.961996[.]xyz
- vps.961996[.]xyz
- jd-login.961996[.]xyz
- pma-dev.961996[.]xyz
- emby.961996[.]xyz
- www.dashboard.961996[.]xyz
- dashboard.961996[.]xyz
- www.sub.961996[.]xyz
- www.speedtest.961996[.]xyz
- www.vnc.961996[.]xyz
- www.cusdis.961996[.]xyz
- www.jd-admin.961996[.]xyz
- www.kpi.961996[.]xyz
- www.gitlab.961996[.]xyz
- www.qbit.961996[.]xyz
- www.display.961996[.]xyz
- www.rss.961996[.]xyz
- www.pma.961996[.]xyz
- radarr.961996[.]xyz
- sonarr.961996[.]xyz
- speedtest.961996[.]xyz
- jd-admin.961996[.]xyz
- proxy.961996[.]xyz
- fbs.961996[.]xyz
- ecdict.961996[.]xyz
- staging.961996[.]xyz
- api.961996[.]xyz
- remote.961996[.]xyz
- pma.961996[.]xyz
- netdata.961996[.]xyz
- http-acme.961996[.]xyz
- metube.961996[.]xyz
- www.sonarr.961996[.]xyz
- www.radarr.961996[.]xyz
- www.favicon.961996[.]xyz
- jd.961996[.]xyz
- jackett.961996[.]xyz
- win7.961996[.]xyz
- torrent.961996[.]xyz
- blog.k1.karahoi[.]com
- dos-game.karahoi[.]com
- www.dos-game.karahoi[.]com
- jellyfin.karahoi[.]com
- emby.karahoi[.]com
- k4.karahoi[.]com
- wp-admin.k4.karahoi[.]com
- jd-login.karahoi[.]com
- 45.32.84[.]73
- 45.76.99[.]225
- 207.148.123[.]125
3. Reviewed time.pornhumen[.]com and ca3jfa.whatsupman[.]net.
What IP addresses are these hosts actively resolving to?
What components are running on these IP addresses?
Findings:
- time.pornhumen[.]com is actively resolving to 207.148.8[.]47.
- 207.148.8[.]47 is currently observing the following components
- nginx (v1.20.1)
- OpenSSH (v7.4)
- SSH (v2.0)
- Pivoting off each of these components allows users to identify other hosts and IPs that also may be tied to ToddyCat infrastructure.
4. Reviewed pornhumen[.]com and whatsupman[.]net subdomains (other than the ones noted in step 3).
What IP addresses are these subdomain hosts resolving to?
Findings:
- pornhumen[.]com
- Defender TI has not observed pornhumen[.]com resolve to an IP address
- register.pornhumen.com
- Still resolving to previously reported ToddyCat IP, 149.28.220[.]70
- whatsupman[.]net
- Not actively resolving to an IP
- _dmarc.whatsupman[.]net
- Defender TI has not observed this host resolve to an IP address yet. This could be new infrastructure that has not been operationalized by ToddyCat yet.
5. Reviewed the rest of the domains and hosts identified previously in the ToddyCat article.
Do any of them have new subdomains that follow ToddyCat TTPs and are actively or not actively resolving to IPs?
Findings:
- fopingu[.]com – No A record observations
- ad.fopingu[.]com – Still actively resolving to 45.77.28[.]33
- facebuk[.]org – Multiple historical A record observations. No active A record observations.
- am6l7h.facebuk[.]org
- Still actively resolving to 45.32.29[.]96
- www.facebuk[.]org
- One historical A record observation. No active A record observations.
- am6l7h.facebuk[.]org
- rtmcsync[.]com – New active A record observation, 58.158.177[.]102. This IP is located in Japan, and the ASN is AS17506 – UCOM, which isn't associated with the previously reported ToddyCat TTPs.
- rtmcsync[.]com
- backend.rtmcsync[.]com
- backend.backend.rtmcsync[.]com
- pic.backend.rtmcsync[.]com
- proxy.backend.rtmcsync[.]com
- upload.backend.rtmcsync[.]com
- pic.rtmcsync[.]com
- backend.pic.rtmcsync[.]com
- pic.pic.rtmcsync[.]com
- proxy.pic.rtmcsync[.]com
- upload.pic.rtmcsync[.]com
- proxy.rtmcsync[.]com
- backend.proxy.rtmcsync[.]com
- pic.proxy.rtmcsync[.]com
- proxy.proxy.rtmcsync[.]com
- upload.proxy.rtmcsync[.]com
- upload.rtmcsync[.]com
- backend.upload.rtmcsync[.]com
- pic.upload.rtmcsync[.]com
- proxy.upload.rtmcsync[.]com
- upload.upload.rtmcsync[.]com
- All hosts above also observed actively resolving to – Also observed actively resolving to 58.158.177[.]102
- windowshost[.]us - A few historical A record observations. No active A record observations
- f83t6jurwdaq.windowshost[.]us – New active A record observation, 149.28.147[.]105. This IP is located in Singapore and the ASN was the previous ASN observed used by ToddyCat, AS20473 – AS-CHOOPA.
- 2ml0mjiob6.windowshost[.]us
- Still actively resolving to 141.164.38[.]11.
- bb9sh2gczdzm.windowshost[.]us
- Still actively resolving to 202.182.133[.]23.
- blogs.windowshost[.]us
- Still actively resolving to 149.248.18[.]145
- eohsdnsaaojrhnqo.windowshost[.]us
- Various historical A record observations.
- Still actively resolving to 207.148.73[.]146
- g5lwvvqe1u.windowshost[.]us
- Still actively resolving to 45.76.103[.]70
- ohs7usetnd.windowshost[.]us
- Still actively resolving to 45.32.58[.]62
- poapkvlr.windowshost[.]us
- Still actively resolving to 66.42.40[.]114
- q9gebl9hff.windowshost[.]us
- Still actively resolving to 45.76.103[.]70
- time.windowshost[.]us
- Still actively resolving to 207.148.73[.]146
- youtubuy[.]org - Multiple historical A record observations. No active A record observations.
- lhqkns.youtubuy[.]org
- Still actively resolving to 78.141.233[.]106.
- ww1.youtubuy[.]org
- 1 historical A record observation. No active A record observations.
- ww41.youtubuy[.]org
- 1 historical A record observation. No active A record observations.
- www.youtubuy[.]org
- Multiple historical A record observations. No active A record observations.
- lhqkns.youtubuy[.]org
- ns247[.]one – Still actively resolving to 185.224.129[.]13. 1 historical A record observation.
- mail.ns247[.]one
- Still actively resolving to 185.224.129[.]13.
- smtp.ns247[.]one
- No active A record observations. 1 historical A record observation.
- www.ns247[.]one
- Still actively resolving to 185.224.129[.]13.
- mail.ns247[.]one
- ns247[.]top – No active or historical A record observations. No subdomains.
- wikipedi[.]net - No active A record observations. Multiple historical A record observations.
- rgyurv.wikipedi[.]net
- Still actively resolving to 208.72.154[.]135.
- _dmarc.wikipedi[.]net
- No active or historical A record observations.
- en.wikipedi[.]net
- No active or historical A record observations.
- forum.wikipedi[.]net
- No active A record observations. 2 historical A record observations.
- ww1.forum.wikipedi[.]net
- No active or historical A record observations.
- ftp.wikipedi[.]net
- No active A record observations. 1 historical A record observation.
- imap.wikipedi[.]net
- No active or historical A record observations.
- l3eiph.wikipedi[.]net
- Still resolving to 149.28.118[.]97.
- mail.wikipedi[.]net
- No active A record observations. 1 historical A record observation.
- pop.wikipedi[.]net
- No active or historical A record observations.
- pop3.wikipedi[.]net
- No active or historical A record observations.
- rgyurv.wikipedi[.]net
- Still resolving to 208.72.154[.]135.
- smtp.wikipedi[.]net
- No active A record observations. 1 historical A record observation.
- vfmpde.wikipedi[.]net
- Still resolving to 149.28.118[.]97.
- ww1.wikipedi[.]net
- No active A record observations. 1 historical A record observation.
- ww15.wikipedi[.]net
- No active A record observations. 1 historical A record observation.
- ww2.wikipedi[.]net
- No active A record observations. 2 historical A record observations.
- ww25.wikipedi[.]net
- No active A record observations. 1 historical A record observation.
- ww35.wikipedi[.]net
- No active A record observations. 1 historical A record observation.
- ww38.wikipedi[.]net
- No active or historical A record observations.
- ww41.wikipedi[.]net
- No active A record observations. 1 historical A record observation.
- www.wikipedi[.]net
- No active A record observations. Multiple historical A record observations.
- rgyurv.wikipedi[.]net
- temdiever[.]com - No active A record observations. 1 historical A record observation. No subdomains.
- tiktocek[.]net - No active or historical A record observations.
- logs.tiktocek[.]net
- Host observed actively resolving to new IP address, 141.164.44[.]49. This IP is located in South Korea and the ASN was the previous ASN observed used by ToddyCat, AS20473 – AS-CHOOPA. However, this IP was not listed as an indicator in the ToddyCat article.
- logs.tiktocek[.]net
- twiteer[.]org - No active A record observations. 2 historical A record observations. No subdomains.
6. Reviewed IPs, 58.158.177[.]102 and 141.164.44[.]49 in gold text in step 5.
What is the reputation for each of these IPs?
Findings:
- 58.158.177[.]102, Suspicious, 71
- 141.164.44[.]49, Suspicious, 74
Are these IPs listed as indicators in any intelligence articles?
Findings:
- 58.158.177[.]102 is listed as a Defender TI indicator in the New Nebulae Backdoor Linked with the NAIKON Group article, which was published over a year ago.
7. Searched hxxp://time.pornhumen[.]com and hxxp://ca3jfa.whatsupman[.]net as URLs in VirusTotal.
Have any security vendors detected that this URL is associated with malware?
Findings:
- time.pornhumen[.]com: Fortinet found that this URL was linked to malware.
What sha-256 hashes are related to these newly discovered hosts?
Findings:
- time.pornhumen[.]com:
- ca3jfa.whatsupman[.]net:
8. Searched both sha-256 hashes discovered in step 7 in Defender TI to see if they appeared in any articles.
Findings:
- These sha-256 hashes do not appear in any existing Defender TI articles.
9. On your own: Review the Data tab and datasets for the two IPs noted in step 6 as well as those that the domains and subdomains were actively resolving to in step 5.
Is there any data overlap in ToddyCat's TTPs previously reported?
Are there any new hosts resolving to these IPs that are associated with ToddyCat that were not previously reported?
10. On your own: Search both sha-256 hashes discovered in step 7 in VirusTotal and review the Relations tab. Search related IPs, hosts, and domains in Defender TI. Review the Summary and Data tab results to identify additional pivot points to find related indicators of compromise.
Are there any related indicators that have overlap with ToddyCat infrastructure?
Do any of these indicators appear in any articles?
What is the reputation for these indicators?
11. On your own: Repeat step 6 for other newly observed subdomains and IPs that have overlap in TTPs. Query those indicators as URLs in VirusTotal.
Have any security vendors flagged this indicator for malware?
12. On your own: Continue to iterate through steps 8 through 11.
What additional related indicators of compromise can you find?
This was a large campaign, and there are more techniques I could have taken to broaden the scope of IOCs identified.
What additional techniques would you have taken?
What was the one initial seed that led to the identification of additional indicators of compromise?
How many additional indicators of compromise were identified at the time of this writing?
What SSL certificate component serves as a pivot point to identify additional actor infrastructure?
What ASN was used by the IP addresses associated with this campaign?
What nameservers were observed by the IP addresses?
Where can server banner response data be found within the Defender TI platform?
Vulnerability Articles
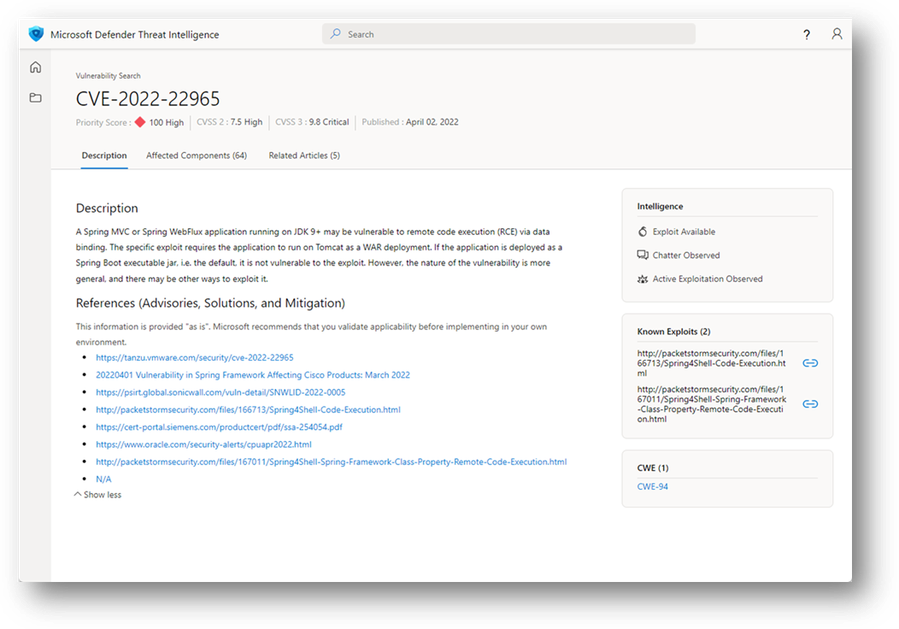
Defender TI offers CVE-ID searches to help users identify critical information about the CVE. CVE-ID searches result in Vulnerability Articles.
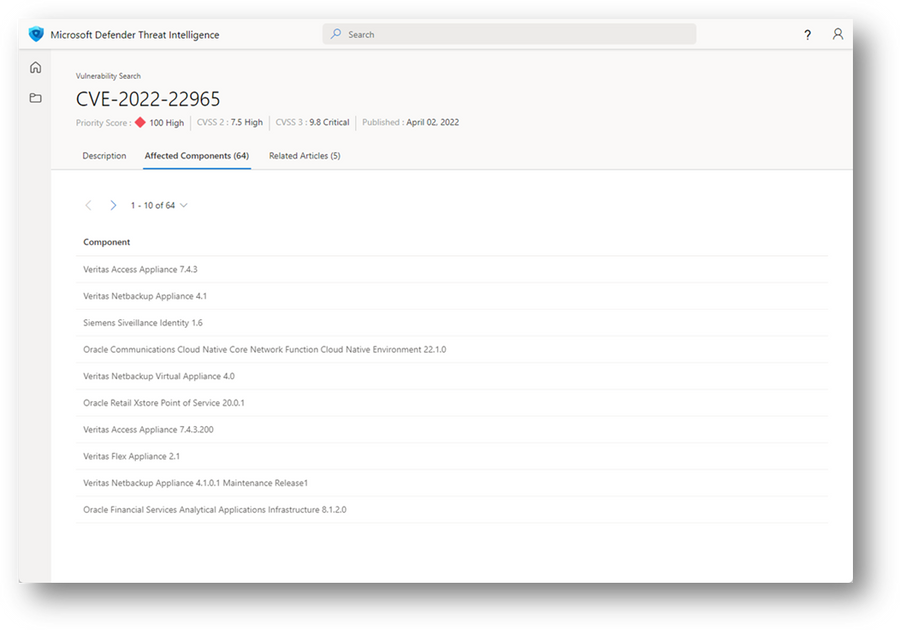
Vulnerability Articles provide critical context behind CVEs of interest. Each article contains a description of the CVE, a list of affected components, tailored mitigation procedures and strategies, related intelligence articles, references in Deep & Dark Web chatter, and other key observations. These articles provide deeper context and actionable insights behind each CVE, enabling users to understand these vulnerabilities more quickly and quickly mitigate them. For more information, see What is Microsoft Defender Threat Intelligence (Defender TI)? and reference the Vulnerability Articles section.
Figure 2 – Vulnerability Article Description
Figure 3 – Vulnerability Article Affected Components
Figure 4 – Vulnerability Article Related Articles
Tutorials
For tutorials referencing our articles, vulnerability articles, search, and dataset features see Gathering threat intelligence and infrastructure chaining and Gathering vulnerability intelligence tutorial articles.